Escolar Documentos
Profissional Documentos
Cultura Documentos
IEEE 2012 (1) Java, Netdh
Enviado por
Saidi ReddyTítulo original
Direitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
IEEE 2012 (1) Java, Netdh
Enviado por
Saidi ReddyDireitos autorais:
Formatos disponíveis
IEEE 2012 PROJECTS
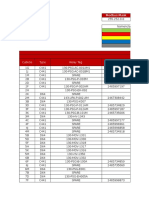
S.NO. LSJ120 1 LSJ120 2 LSJ120 3 LSJ120 4 LSJ120 5 LSJ120 6 LSJ120 7 LSJ120 8 LSJ120 9 LSJ121 0 LSJ121 1 LSJ121 2 LSJ121 3 LSJ121 4 LSJ121 5 LSJ121 6 LSJ121 7 LSJ121 8 LSJ121 9 LSJ122 0 Project Title A Network Coding Equivalent Content Distribution Scheme For Efficient Peer To Peer Interactive Vod Streaming An Optimizing Overlay Topologies For Search In Unstructed Peer To Peer Networks Automatic Discovery of Association Orders between Name and Aliases from the Web using Anchor Texts-based Co-occurrences Cloud Data Production for Masses Clustering With Multi View Point Based Similarity Measure Cooperative Provable Data Possession for Integrity Verification in Multi-Cloud Storage Distributed Packet Buffers For High Band Width Switches & Routers Efficient Fuzzy Type A Head Search In Xml Data Fast Data Collection in Tree-Based Wireless Sensor Networks. Foot Print Detecting Sybil Attacks In Urban Vehicular Networks Game-Theoretic Pricing for Video Streaming in Mobile Networks Hand Written Chinese Text Recognition By Integrating Multiple Contexts In Tags We Trust: Trust modeling in social tagging of multimedia content Learn to Personalized Image Search from the Photo Sharing Websites
MULTIPARTY ACCESS CONTROL FOR ONLINE SOCIAL NETWORKS: MODEL AND MECHANISMS
DOMINE Parallel & Distributed Systems Parallel & Distributed Systems Knowledge & Data Engineering Cloud Computing Knowledge & Data Engineering Parallel & Distributed Systems Parallel & Distributed Systems Knowledge & Data Engineering Mobile Computing Parallel & Distributed Systems Mobile Computing Pattern Analysis & Machine Intelligence Signal Processing Multimedia Knowledge & Data Engineering Secure Computing Knowledge & Data Engineering Networking Secure Computing Knowledge & Data Engineering
TEC H JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA
Online Modeling of Proactive Moderation System for Auction Fraud Detection Organizing User Search Histories Packet Loss Control Using Tokens at the Network Edge Packet-Hiding Methods for Preventing Selective Jamming Attacks Ranking Model Adaptation for Domain-Specific Search
IEEE 2012 PROJECTS
LSJ122 1 LSJ122 2 LSJ122 3 LSJ122 4 LSJ122 5 LSJ122 6 LSJ122 7 LSJ122 8 LSJ122 9 Risk-Aware Mitigation for MANET Routing Attacks Self Adaptive Contention Aware Routing Protocol For Intermittently Connected Mobile Networks Slicing: A New Approach to Privacy Preserving Data Publishing Ensuring Distributed Accountability For Data Sharing In The Cloud. Adaptive Opportunistic Routing for Wireless Ad Hoc Networks Vehicle Detection in Aerial Surveillance Using Dynamic Bayesian Networks Catching Packet Droppers and Modifiers in Wireless Sensor Networks Energy-Efficient Cooperative Distribution with Statistical QoS Provisions Video Over Wireless Networks CCD A Distributed Publish Subscribe Framework for Rich Content Format Secure Computing Mobile Computing Knowledge & Data Engineering Secure Computing Networking Networking Parallel & Distributed Systems Networks Parallel & Distributed Systems JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA JAVA
IEEE 2012 PROJECTS
S.No. LSD120 1 LSD120 2 LSD120 3 LSD120 4 LSD120 5 LSD120 6 LSD120 7 LSD120 8 LSD120 9 LSD121 0 LSD121 1 LSD121 2 LSD121 3 LSD121 4 LSD121 5 LSD121 6 LSD121 7 Project Title A New Cell Counting Based Attack Against Tor. AMPLE: An Adaptive Traffic Engineering System Based on Virtual Routing Topologies. Compressed-Sensing-Enabled Video Streaming for Wireless Multimedia Sensor Networks. Defenses Against Large Scale Online Password Guessing Attacks by using Persuasive click Points. Design and Implementation of TARF: A TrustAware Routing Framework for WSNs. Query Planning for Continuous Aggregation Queries Optimal Power Allocation in Multi-Relay MIMO Cooperative Networks: Theory and Algorithms. Robust Face-Name Graph Matching for Movie Character Identify. Scalable and Secure Sharing of Personal Health Records in Cloud Computing using Attributebased Encryption Securing Node Capture Attacks for Hierarchical Data Aggregation in Wireless Sensor Networks Semi supervised Biased Maximum Margin Analysis for Interactive Image Retrieval SPOC: A Secure and Privacy-preserving Opportunistic Computing Framework for MobileHealthcare Emergency Topology control in mobile ad hoc networks with cooperative communications Secure And Efficient Handover Authentication Based On Bilinear Pairing Functions Grouping-Enhanced Resilient Probabilistic En-Route Filtering of Injected False Data in WSNs Latency Equalization as a New Network Service Primitive Fair Torrent A Deficit Based Distributed Algorithm to Ensure Fairness in peer to peer Systems DOMINE Networking Wireless Communications Image Processing Image processing Secure Computing Data Mining Networking Image Processing Cloud computing International Conference Image processing Parallel & Distributed Systems Mobile Computing Secure Computing Parallel & Distributed Systems Networking Networking TEC H .NET .NET .NET .NET .NET .NET .NET .NET .NET .NET .NET .NET .NET .NET .NET .NET .NET
IEEE 2012 PROJECTS
Você também pode gostar
- Data Analysis 15 QuefghfstionsDocumento35 páginasData Analysis 15 QuefghfstionsSaidi ReddyAinda não há avaliações
- Synopsis Capital Budgeting Reddy's LabshjklhjlDocumento10 páginasSynopsis Capital Budgeting Reddy's LabshjklhjlSaidi ReddyAinda não há avaliações
- Knowledge Management - Edlogix Synopsis (1) HJKHDocumento102 páginasKnowledge Management - Edlogix Synopsis (1) HJKHSaidi ReddyAinda não há avaliações
- Saidi BiodataTJTJDocumento2 páginasSaidi BiodataTJTJSaidi ReddyAinda não há avaliações
- AWS Course Content MindQfghfgDocumento8 páginasAWS Course Content MindQfghfgSaidi Reddy100% (1)
- Guidelines For Filling Multisource Procedures of Pharmaceutical DrugyitfitygfouyDocumento7 páginasGuidelines For Filling Multisource Procedures of Pharmaceutical DrugyitfitygfouySaidi ReddyAinda não há avaliações
- 3 Axix CNC DrillinghjgjDocumento1 página3 Axix CNC DrillinghjgjSaidi ReddyAinda não há avaliações
- Synopsis Taxfghfh Saving Mutual FundsDocumento8 páginasSynopsis Taxfghfh Saving Mutual FundsSaidi ReddyAinda não há avaliações
- Karvy Arada CompletionghjDocumento1 páginaKarvy Arada CompletionghjSaidi ReddyAinda não há avaliações
- A Project Report On "Asset & Liability Management" AT Icici BankDocumento5 páginasA Project Report On "Asset & Liability Management" AT Icici BankSaidi ReddyAinda não há avaliações
- Industry Profile: CommodityDocumento12 páginasIndustry Profile: CommoditySaidi ReddyAinda não há avaliações
- Movable Watering RobotsyutyDocumento1 páginaMovable Watering RobotsyutySaidi ReddyAinda não há avaliações
- Bootyijtyklet WindDocumento64 páginasBootyijtyklet WindSaidi ReddyAinda não há avaliações
- Companies List (2pDocumento1 páginaCompanies List (2pSaidi ReddyAinda não há avaliações
- S.No Hall Ticket No Name of The Candidate 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 Specializatio NDocumento8 páginasS.No Hall Ticket No Name of The Candidate 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 Specializatio NSaidi ReddyAinda não há avaliações
- India Infoline Vidya RadfgdDocumento1 páginaIndia Infoline Vidya RadfgdSaidi ReddyAinda não há avaliações
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNo EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNota: 4 de 5 estrelas4/5 (5794)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNo EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNota: 4 de 5 estrelas4/5 (895)
- The Yellow House: A Memoir (2019 National Book Award Winner)No EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Nota: 4 de 5 estrelas4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingNo EverandThe Little Book of Hygge: Danish Secrets to Happy LivingNota: 3.5 de 5 estrelas3.5/5 (400)
- The Emperor of All Maladies: A Biography of CancerNo EverandThe Emperor of All Maladies: A Biography of CancerNota: 4.5 de 5 estrelas4.5/5 (271)
- Never Split the Difference: Negotiating As If Your Life Depended On ItNo EverandNever Split the Difference: Negotiating As If Your Life Depended On ItNota: 4.5 de 5 estrelas4.5/5 (838)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyNo EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyNota: 3.5 de 5 estrelas3.5/5 (2259)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNo EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNota: 4.5 de 5 estrelas4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNo EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNota: 3.5 de 5 estrelas3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnNo EverandTeam of Rivals: The Political Genius of Abraham LincolnNota: 4.5 de 5 estrelas4.5/5 (234)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNo EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNota: 4.5 de 5 estrelas4.5/5 (266)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNo EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNota: 4.5 de 5 estrelas4.5/5 (345)
- The Unwinding: An Inner History of the New AmericaNo EverandThe Unwinding: An Inner History of the New AmericaNota: 4 de 5 estrelas4/5 (45)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNo EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNota: 4 de 5 estrelas4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)No EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Nota: 4.5 de 5 estrelas4.5/5 (121)
- Position PaperDocumento7 páginasPosition PaperClem CollantesAinda não há avaliações
- REST Society For Research International: Rsri Membership Application FormDocumento1 páginaREST Society For Research International: Rsri Membership Application FormmeenasarathaAinda não há avaliações
- EMT Tooth Saver Data SheetDocumento5 páginasEMT Tooth Saver Data SheetTerry FarmakisAinda não há avaliações
- Impact of Computer On SocietyDocumento4 páginasImpact of Computer On SocietyraheelAinda não há avaliações
- Usability Engineering (Human Computer Intreraction)Documento31 páginasUsability Engineering (Human Computer Intreraction)Muhammad Usama NadeemAinda não há avaliações
- All C PG and CPP Service ManualDocumento60 páginasAll C PG and CPP Service Manualhurantia100% (1)
- Roland Mdx-650 Milling TutorialDocumento28 páginasRoland Mdx-650 Milling TutorialRavelly TelloAinda não há avaliações
- Esu Tester WhoDocumento5 páginasEsu Tester WhoquezonAinda não há avaliações
- NGO-CSR Internship Report TemplateDocumento4 páginasNGO-CSR Internship Report TemplatePriyanka Singh100% (1)
- Samtec ASP 134488 01 DatasheetDocumento4 páginasSamtec ASP 134488 01 DatasheetamiteshtripathiAinda não há avaliações
- Simatic Wincc: Answers For IndustryDocumento8 páginasSimatic Wincc: Answers For IndustryAlina MirelaAinda não há avaliações
- Lecture 3. Growth of Functions Asymptotic NotationDocumento9 páginasLecture 3. Growth of Functions Asymptotic NotationJasdeep Singh Pardeep SinghAinda não há avaliações
- Literature Study Nift ChennaiDocumento5 páginasLiterature Study Nift ChennaiAnkur SrivastavaAinda não há avaliações
- Informatics in Logistics ManagementDocumento26 páginasInformatics in Logistics ManagementNazareth0% (1)
- Manual Cmp-Smartrw10 CompDocumento66 páginasManual Cmp-Smartrw10 CompAllegra AmiciAinda não há avaliações
- Item 3 Ips C441u c441r Ieb Main ListDocumento488 páginasItem 3 Ips C441u c441r Ieb Main Listcristian De la OssaAinda não há avaliações
- Technology A Way of RevealingDocumento24 páginasTechnology A Way of RevealingSheena jhane Magana100% (1)
- Effect of Cryogenic Treatment On CompositesDocumento14 páginasEffect of Cryogenic Treatment On CompositesGauthamAinda não há avaliações
- Kumar Saurabh Resume (SAP IBP)Documento6 páginasKumar Saurabh Resume (SAP IBP)SaurabhSinhaAinda não há avaliações
- ACC Flow Chart (Whole Plan) - Rev00Documento20 páginasACC Flow Chart (Whole Plan) - Rev00amandeep12345Ainda não há avaliações
- R Values For Z PurlinsDocumento71 páginasR Values For Z PurlinsJohn TreffAinda não há avaliações
- 563000-1 Web Chapter 4Documento22 páginas563000-1 Web Chapter 4Engr Ahmad MarwatAinda não há avaliações
- Differences Between Huawei ATCA-Based and CPCI-Based SoftSwitches ISSUE2.0Documento46 páginasDifferences Between Huawei ATCA-Based and CPCI-Based SoftSwitches ISSUE2.0Syed Tassadaq100% (3)
- III Sem Jan 2010 Examination Results SwatisDocumento21 páginasIII Sem Jan 2010 Examination Results SwatisAvinash HegdeAinda não há avaliações
- PEC 2019 Design GuidelinesDocumento9 páginasPEC 2019 Design GuidelinesHendrix LevaAinda não há avaliações
- Risk Solver Platform ReferenceDocumento247 páginasRisk Solver Platform Referencemj_davis04Ainda não há avaliações
- Acord and IAADocumento4 páginasAcord and IAABHASKARA_20080% (1)
- 26-789 Eng Manual Pcd3Documento133 páginas26-789 Eng Manual Pcd3Antun KoricAinda não há avaliações
- Decline Curve AnalysisDocumento37 páginasDecline Curve AnalysisAshwin VelAinda não há avaliações
- Scan 0001Documento1 páginaScan 0001ochiroowitsAinda não há avaliações