Escolar Documentos
Profissional Documentos
Cultura Documentos
Payment Billing System Document
Enviado por
Parveen KumarDescrição original:
Direitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
Payment Billing System Document
Enviado por
Parveen KumarDireitos autorais:
Formatos disponíveis
CHAPTER-1
COMPANY PROFILE
The quest for knowledge can never end .The deeper you dig the greater the unexplored
seems to be. No man can honestly say that he has learned all that this world has to offer
we cant achieve anything worthwhile in any field only on basis of theoretical knowledge
from book ,programming knowledge obtain through working at zero level and gaining
experience, in my view. n order to tangible positive and concert result, the classroom
knowledge needs to be effective wedded to the realities of the situation outside the
classroom.
!uring my pro"ect, as a part of it, "oined #GORAL TECHNOLOGY PVT
LTD$ of YAMUNA NAGAR as a trainee in %
rd
year. &y assignment could be defined as
a development of #Payment billing ytem$. This report covers the small introduction of
'()*+ T,-.N(+('/ 01T +T! and complete description of my pro"ect.
C!"#e $#!%i&e& in GORAL te'(n!l!gy)
2ava 3
23,, web development
0.0 web development
*ndroid system development
--N*
4
CHAPTER-*
PRO+ECT,-OR. DONE
*/1 Int#!&"'ti!n t! $#!0e't
The pro"ect titled as #0*/&,NT 5++N' 6/6T,& #is a web based application.
nstitutes have different branches at different locations want to control and maintain the
accountant salary and student personal and payment details. 6oftware provides facility for
reporting, new student details, payment details, and modifies details of student and salary
of the accountant.
*/* M!&"le
*dmin of institute
*ccountant of each branch
*/1 F"n'ti!nal Re2"i#ement)
A&min !3 t(e intit"te)
-reate update and delete accountant details after login
-an search branch wise accountant
-an search all candidates studying in various branches and can update and delete
them
A''!"ntant &etail)
-an search the student personal and payment details as per requirement after
login
-an update the old student record
-an save new student informations
*/4 N!n5F"n'ti!nal Re2"i#ement)
6ecure access of confidential data
3789 availability
3
5rowse testing and support for ,,NN,&ozila and :irefox
*/6 7!3t8a#e an& Ha#&8a#e 7$e'i3i'ati!n
Ha#&8a#e 7$e'i3i'ati!n
0rocessor ; 0entium <*&! *thlone 80
)*& ; 43= &5
.ard disk ; 3> '5
:!! ; 4.77&5
&onitor ; 47 inch
&ouse ; % 5utton scroll
-! !rive ; ?3 8
@eyboard ; 4>= keys
7!3t8a#e 7$e'i3i'ati!n
(perating 6ystem ; Aindows 3>>><80 <9
+anguages ; "ava B*"ax, 2!5-, 260, 6ervlet, C
:ront ,nd ; .T&+, 2ava6cript
0latform ; Net 5eans
Aeb 6ervers ; Aeb +ogic=.4<Tomcat ?.>
5ackend ; &y 6D+ using wamp server
5rowser 0rogram ; nternet explorer<&ozilla :ireworks
%
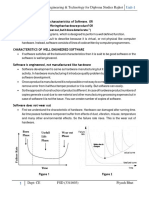
*/9 7!3t8a#e &e%el!$ment li3e 'y'le :7DLC;
The systems development life cycle B6!+-C, or software development process in systems
engineering, information systems and software engineering, is a process of creating or
altering information systems, and the models and methodologies that people use to
develop these systems. n software engineering, the 6!+- concept underpins many kinds
of software development methodologies. These methodologies form the framework for
planning and controlling the creation of an information system; the software development
process.
Fig 1 7DLC
7
* 6ystems !evelopment +ife -ycle B6!+-C adheres to important phases that are
essential for developers, such as planning, analysis, design, and implementation, and are
explained in the section below. t includes evaluation of present system, information
gathering, and feasibility study and request approval. * number of system development
life cycle B6!+-C models have been created; waterfall, fountain, and spiral build and fix,
rapid prototyping, incremental, and synchronize and stabilize. The oldest of these, and the
best known, is the waterfall model; a sequence of stages in which the output of each stage
becomes the input for the next. These stages can be characterized and divided up in
different ways, including the following;
7ytem analyi< #e2"i#ement &e3initi!n; !efines pro"ect goals into defined
functions and operation of the intended application. *nalyzes endEuser
information needs.
7ytem &eign; !escribes desired features and operations in detail, including
screen layouts, business rules, process diagrams, pseudo code and other
documentation.
De%el!$ment; The real code is written here.
Integ#ati!n an& teting; 5rings all the pieces together into a special testing
environment, then checks for errors, bugs and interoperability.
A''e$tan'e< intallati!n< &e$l!yment; The final stage of initial development,
where the software is put into production and runs actual business.
Maintenan'e; Ahat happens during the rest of the softwareFs life; changes,
correction, additions, and moves to a different computing platform and more. This
is often the longest of the stages.
?
*/= FEA7I>ILITY 7TUDY)
:easibility study is made to see if the pro"ect on completion will serve the purpose of the
organization for the amount of work, effort and the time that spend on it. :easibility study
lets the developer foresee the future of the pro"ect and the usefulness. * feasibility study
of a system proposal is according to its workability, which is the impact on the
organization, ability to meet their user needs and effective use of resources. Thus when a
new application is proposed it normally goes through a feasibility study before it is
approved for development. The document provide the feasibility of the pro"ect that is
being designed and lists various areas that were considered very carefully during the
feasibility study of this pro"ect such as Technical, ,conomic and (perational
feasibilities. The following are its features;
1/ TECHNICAL FEA7I>ILITY)
The system must be evaluated from the technical point of view first. The
assessment of this feasibility must be based on an outline design of the system
requirement in the terms of input, output, programs and procedures. .aving
identified an outline system, the investigation must go on to suggest the type of
equipment, required method developing the system, of running the system once it
has been designed. Technical issues raised during the investigation are;
!oes the existing technology sufficient for the suggested oneG
-an the system expand if developedG
The pro"ect should be developed such that the necessary functions and
performance are achieved within the constraints. The pro"ect is developed within
latest technology. Through the technology may become obsolete after some period
of time, due to the fact that never version of same software supports older
versions, the system may still be used. 6o there are minimal constraints involved
with this pro"ect. The system has been developed using 2ava the pro"ect is
technically feasible for development.
*/ ECONOMIC FEA7I>ILITY)
The developing system must be "ustified by cost and benefit. -riteria to ensure
that effort is concentrated on pro"ect, which will give best, return at the earliest.
(ne of the factors, which affect the development of a new system, is the cost it
H
would require. The following are some of the important financial questions asked
during preliminary investigation;
The costs conduct a full system investigation.
The cost of the hardware and software.
The benefits in the form of reduced costs or fewer costly errors.
6ince the system is developed as part of pro"ect work, there is no manual cost to
spend for the proposed system. *lso all the resources are already available, it give
an indication of the system is economically possible for development.
1/ >EHAVIORAL FEA7I>ILITY)
This includes the following questions;
s there sufficient support for the usersG
Aill the proposed system cause harmG
The pro"ect would be beneficial because it satisfies the ob"ectives when developed
and installed. *ll behavioral aspects are considered carefully and conclude that the
pro"ect is behaviorally feasible.
9
*/? DE7IGN)
!esign is the first step into the development phase for any engineered product or system.
!esign is a creative process. * good design is the key to effective system. The term
#design$ is defined as #the process of applying various techniques and principles for the
purpose of defining a process or a system in sufficient detail to permit its physical
realization$. t may be defined as a process of applying various techniques and principles
for the purpose of defining a device, a process or a system in sufficient detail to permit its
physical realization. 6oftware design sits at the technical kernel of the software
engineering process and is applied regardless of the development paradigm that is used.
The system design develops the architectural detail required to build a system or product.
*s in the case of any systematic approach, this software too has undergone the best
possible design phase fine tuning all efficiency, performance and accuracy levels. The
design phase is a transition from a user oriented document to a document to the
programmers or database personnel. 6ystem design goes through two phases of
development; +ogical and 0hysical !esign.
1/ LOGICAL DE7IGN)
The logical flow of a system and define the boundaries of a system. t includes the
following steps;
)eviews the current physical system I its data flows, file content, volumes,
:requencies etc.
0repares output specifications I that is, determines the format, content and
:requency of reports.
0repares input specifications I format, content and most of the input
functions.
0repares edit, security and control specifications.
6pecifies the implementation plan.
0repares a logical design walk through of the information flow, output,
input, -ontrols and implementation plan.
)eviews benefits, costs, target dates and system constraints.
*/ PHY7ICAL DE7IGN)
=
0hysical system produces the working systems by define the design specifications
that tell the programmers exactly what the candidate system must do. t includes
the following steps.
!esign the physical system.
6pecify input and output media.
!esign the database and specify backup procedures.
!esign physical information flow through the system and a physical
design
0lan system implementation.
0repare a conversion schedule and target date.
!etermine training procedures, courses and timetable.
!evise a test and implementation plan and specify any new
hardware<software.
Jpdate benefits , costs , conversion date and system constraints
Deign,7$e'i3i'ati!n a'ti%itie)
-oncept formulation.
0roblem understanding.
.igh level requirements proposals.
:easibility study.
)equirements engineering.
*rchitectural design.
1/ MODULE DE7IGN
*dmin institute
*ccountant of each branch
a; A&min !3 t(e intit"te)
-reate update and delete accountant details after login
-an search branch wise accountant
-an search all candidates studying in various branches and can
update and delete them
b; A''!"ntant &etail)
-an search the student personal and payment details as per
requirement after login
-an update the old student record
-an save new student information
K
4/ INPUT DE7IGN)
The input design is the link between the information system and the user. t
comprises the developing specification and procedures for data preparation and
those steps are necessary to put transaction data in to a usable form for processing
can be achieved by inspecting the computer to read data from a written or printed
document or it can occur by having people keying the data directly into the
system. The design of input focuses on controlling the amount of input required,
controlling the errors, avoiding delay, avoiding extra steps and keeping the
process simple. The input is designed in such a way so that it provides security
and ease of use with retaining the privacy. nput !esign considered the following
things;
Ahat data should be given as inputG
.ow the data should be arranged or codedG
The dialog to guide the operating personnel in providing input.
ðods for preparing input validations and steps to follow when error
occur.
O>+ECTIVE7)
nput !esign is the process of converting a userEoriented description of the input
into a computerEbased system. This design is important to avoid errors in the data
input process and show the correct direction to the management for getting correct
information from the computerized system.
t is achieved by creating userEfriendly screens for the data entry to handle
large volume of data. The goal of designing input is to make data entry
easier and to be free from errors. The data entry screen is designed in such
a way that all the data manipulates can be performed. t also provides
record viewing facilities.
Ahen the data is entered it will check for its validity. !ata can be entered
with the help of screens. *ppropriate messages are provided as when
needed so that the user will not be in maize of instant. Thus the ob"ective
of input design is to create an input layout that is easy to follow
6/ OUTPUT DE7IGN)
4>
* quality output is one, which meets the requirements of the end user and presents
the information clearly. n any system results of processing are communicated to
the users and to other system through outputs. n output design it is determined
how the information is to be displaced for immediate need and also the hard copy
output. t is the most important and direct source information to the user. ,fficient
and intelligent output design improves the systems relationship to help user
decisionEmaking.
!esigning computer output should proceed in an organized, well thought
out mannerL the right output must be developed while ensuring that each
output element is designed so that people will find the system can use
easily and effectively. Ahen analysis design computer output, they should
dentify the specific output that is needed to meet the requirements.
6elect methods for presenting information.
-reate document, report, or other formats that contain information
produced by the system.
The output form of an information system should accomplish one or more of the
following ob"ectives.
-onvey information about past activities, current status or pro"ections of
the :uture.
6ignal important events, opportunities, problems, or warnings.
Trigger an action.
-onfirm an action.
*/@ Data Fl!8 Diag#am
44
* &ata 3l!8 &iag#am BDFDC is a graphical representation of the MflowM of data through
an information system, modeling its process aspects. (ften they are a preliminary step
used to create an overview of the system which can later be elaborated. !:!s can also be
used for the visualization of data processing Bstructured designC.
* !:! shows what kinds of information will be input to and output from the system,
where the data will come from and go to, and where the data will be stored. t does not
show information about the timing of processes, or information about whether processes
will operate in sequence or in parallel Bwhich is shown on a flowchartC.the basic notation
used to create a !:!s are as follows;
1/ Data3l!8; data moves in a specific from an origin to a destination.
*/ P#!'e) People, procedures or device that use or produce data. The physical
components not identified.
1/ 7!"#'e; external source or destination of data, which may be people programs,
organizations or other entities.
4/ Data !"#'e) here data are store and referenced by a process in the system.
LEVEL-1 DFD
43
F!# T(e A&min)
F!# t(e A''!"ntant)
Fig * le%el A DFD
Le%el 1 DFD- A&minit#at!#
4%
0ayment billing
6ystem
*dmin
*ccountant
Jser!, pwd
!etails
*dd ,delete
0ayment billing
6ystem
*ccountant
6tudents
Jser!, pwd
!etails
*dd, modify
Le%el 1 DFD- A''!"ntant
47
1iew details
1iew user details
Jsername, 0assword
0ayment
billing
6ystem
*dministrator
)egistration details
6alary
:eedback
+ogin
Add Solutions
1erify
&odify
Jsername<0assword
)egistration
)egistration
+ogin
+ogin
&odify
details
&odified
Jsername<0assword
Jser
Fig 1 le%el 1 DFD
E- R DIGRAM
4?
*dmin login
+ogi
n
0roc
ess
adm
in
*ccountant
category
5ranc
h
Name
0wd
5ranch
Name
!escriptio
n
*ccountant
login
6tudent
category
Name
0aymen
t details
information
+ogin
proce
ss
6tudent category
Name
0aymen
t details
&odifie
d details
*dd<delete
*dd<delet
e
6dnt id
6dnt id
Fig 4 ER &iag#am
*/1A DATA>A7E DE7IGN
* database is an organized mechanism that has the capability of storing information
through which a user can retrieve stored information in an effective and efficient manner.
The data is the purpose of any database and must be protected.
The database design is a two level process. n the first step, user requirements are
gathered together and a database is designed which will meet these requirements as
clearly as possible. This step is called nformation +evel !esign and it is taken
independent of any individual !5&6. n the second step, this nformation level design is
transferred into a design for the specific !5&6 that will be used to implement the system
in question. This step is called 0hysical +evel !esign, concerned with the characteristics
of the specific !5&6 that will be used. * database design runs parallel with the system
design. The organization of the data in the database is aimed to achieve the following two
ma"or ob"ectives.
!ata ntegrity
!ata independence
Normalization is the process of decomposing the attributes in an application, which
results in a set of tables with very simple structure. The purpose of normalization is to
make tables as simple as possible. Normalization is carried out in this system for the
following reasons.
To structure the data so that there is no repetition of data, this helps in saving.
To permit simple retrieval of data in response to query and report request.
To simplify the maintenance of the data through updates, insertions, deletions.
To reduce the need to restructure or reorganize data which new application
)equirements arise.
4H
TA>LE7 7TRUCTURE
1/ $ayB#eg
Fiel& Data ty$e Lengt( .ey
! nt 44 0rimary key
Jsername 1archar 7>>> E
Jserpass 1archar 7>>> E
5ranch 1archar 7>>> E
!ate of "oining 1archar 7>>> E
5ranch 1archar 7>>> E
6alary 1archar 7>>> E
*/ t"&ent
Fiel& name Data ty$e Lengt( .ey
! nt 7>>> 0rimary key
Name 1archar 7>>> E
-ourse 1archar 7>>> E
&obile 1archar 7>>> E
:ee sub 1archar 7>>> E
:ees 1archar 7>>> E
0aid 1archar 7>>> E
5alance 1archar 7>>> E
*ddress 1archar 7>>> E
:ather name 1archar 7>>> E
&other name 1archar 7>>> E
!ate of birth 1archar 7>>> E
!ate of "oining 1archar 7>>> E
Dualification 1archar 7>>> E
Trainer 1archar 7>>> E
CHAPTER-1
INTRODUCTION TO +AVA
49
2ava is a small, simple, safe, ob"ect oriented, interpreted or dynamically
optimized, byte coded, architectural, garbage collected, multithreaded
programming language with a strongly typed exceptionEhandling for writing
distributed and dynamically extensible programs.
2ava is an ob"ect oriented programming language. 2ava is a highElevel, third
generation language like -, :()T)*N, 6mall talk, 0earl and many others. /ou
can use "ava to write computer applications that crunch numbers, process words,
play games, store data or do any of the thousands of other things computer
software can do.
6pecial programs called applets that can be downloaded from the internet and
played safely within a web browser. 2ava a supports this application and the
follow features make it one of the best programming languages.
t is simple and ob"ect oriented
t helps to create user friendly interfaces.
t is very dynamic.
t supports multithreading.
t is platform independent
t is highly secure and robust.
t supports internet programming
+a%a is a programming language originally developed by 6un &icrosystems and
released in 4KK? as a core component of 6unFs 2ava platform. The language
derives much of its syntax from - and -NN but has a simpler ob"ect model and
fewer lowElevel facilities. 2ava applications are typically compiled to byte code
which can run on any 2ava virtual machine B21&C regardless of computer
architecture.
The original and reference implementation 2ava compilers, virtual machines, and
class libraries were developed by 6un from 4KK?. *s of &ay 3>>9, in compliance
with the specifications of the 2ava -ommunity 0rocess, 6un made available most
of their 2ava technologies as free software under the 'NJ 'eneral 0ublic +icense.
(thers have also developed alternative implementations of these 6un
technologies, such as the 'NJ -ompiler for 2ava and 'NJ -lass path.
4=
The 2ava language was created by 2ames 'osling in 2une 4KK4 for use in a set top
box pro"ect. The language was initially called Oak, after an oak tree that stood
outside 'oslingFs office E and also went by the name Green E and ended up later
being renamed to Java, from a list of random words. 'oslingFs goals were to
implement a virtual machine and a language that had a familiar -<-NN style of
notation.
P#ima#y g!al
There were five primary goals in the creation of the 2ava language;
1/ Ot should use the ob"ectEoriented programming methodology.
*/ t should allow the same program to be executed on multiple operating
systems.
1/ t should contain builtEin support for using computer networks.
4/ t should be designed to execute code from remote sources securely.
6/ t should be easy to use by selecting what were considered the good parts
of other ob"ectEoriented languages.
The Java platform is the name for a bundle of related programs, or platform, from
6un which allow for developing and running programs written in the 2ava
programming language. The platform is not specific to any one processor or
operating system, but rather an execution engine Bcalled a virtual machineC and a
compiler with a set of standard libraries which are implemented for various
hardware and operating systems so that 2ava programs can run identically on all of
them.
!ifferent MeditionsM of the platform are available, including;
1/ 2ava &, B&icro ,ditionC; 6pecifies several different sets of libraries Bknown
as profilesC for devices which are sufficiently limited that supplying the full set
of 2ava libraries would take up unacceptably large amounts of storage.
*/ 2ava 6, B6tandard ,ditionC; :or general purpose use on desktop 0-s, servers
and similar devices.
1/ 2ava ,, B,nterprise ,ditionC; 2ava 6, plus various *0s useful for multiEtier
clientEserver enterprise applications.
4K
The 2ava 0latform consists of several programs, each of which provides a distinct
portion of its overall capabilities. :or example, the 2ava compiler, which converts
2ava source code into 2ava bytecode Ban intermediate language for the 2ava 1irtual
&achine B21&CC, is provided as part of the 2ava !evelopment @it B2!@C. The
sophisticated 2ava )untime ,nvironment B2),C, complementing the 21& with a
"ustEinEtime B2TC compiler, converts intermediate bytecode into native machine
code on the fly. *lso supplied are extensive libraries BpreEcompiled into 2ava
bytecodeC containing reusable code, as well as numerous ways for 2ava
applications to be deployed, including being embedded in a web page as an
*ppletG There are several other components, some available only in certain
editions.
The essential components in the platform are the 2ava language compiler, the
libraries, and the runtime environment in which 2ava intermediate bytecode
MexecutesM according to the rules laid out in the virtual machine specification.
Fig 6 +a%a En%i#!nment
+a%a Vi#t"al Ma'(ine
3>
The heart of the 2ava 0latform is the concept of a Mvirtual machineM that
executes 2ava bytecode programs. This bytecode is the same no matter
what hardware or operating system the program is running under. There is
a 2T compiler within the Java Virtual Machine, or 21&. The 2T compiler
translates the 2ava bytecode into native processor instructions at runEtime
and caches the native code in memory during execution.
The use of bytecode as an intermediate language permits 2ava programs to
run on any platform that has a virtual machine available. The use of a 2T
compiler means that 2ava applications, after a short delay during loading
and once they have Mwarmed upM by being all or mostly 2TEcompiled, tend
to run about as fast as native programs. 6ince 2), version 4.3, 6unFs 21&
implementation has included a "ustEinEtime compiler instead of an
interpreter.
*lthough 2ava programs are 0latform ndependent, the code of the 2ava
1irtual &achine B21&C that execute these programs are not. ,very
(perating 6ystem has its own 21&.
Cla lib#a#ie
n most modern operating systems, a large body of reusable code is provided to
simplify the programmerFs "ob. This code is typically provided as a set of
dynamically loadable libraries that applications can call at runtime. 5ecause the
2ava 0latform is not dependent on any specific operating system, applications
cannot rely on any of the existing libraries. nstead, the 2ava 0latform provides a
comprehensive set of standard class libraries, containing much of the same
reusable functions commonly found in modern operating systems. The 2ava class
libraries serve three purposes within the 2ava 0latform. +ike other standard code
libraries, they provide the programmer a wellEknown set of functions to perform
common tasks, such as maintaining lists of items or performing complex string
parsing. n addition, the class libraries provide an abstract interface to tasks that
would normally depend heavily on the hardware and operating system. Tasks such
as network access and file access are often heavily dependent on the native
capabilities of the platform. The 2ava "ava.net and "ava.io libraries implement the
required native code internally, then provide a standard interface for the 2ava
34
applications to perform those tasks. :inally, when some underlying platform does
not support all of the features a 2ava application expects, the class libraries can
either emulate those features using whatever is available, or at least provide a
consistent way to check for the presence of a specific feature.
Plat3!#m in&e$en&en'e
(ne characteristic, platform independence, means that programs written in the
2ava language must run similarly on any supported hardware<operatingEsystem
platform. (ne should be able to write a program once, compile it once, and run it
anywhere. This is achieved by most 2ava compilers by compiling the 2ava
language code halfway Bto 2ava bytecodeC I simplified machine instructions
specific to the 2ava platform. The code is then run on a virtual machine B1&C, a
program written in native code on the host hardware that interprets and executes
generic 2ava bytecode. Bn some 21& versions, bytecode can also be compiled to
native code, either before or during program execution, resulting in faster
execution.C :urther, standardized libraries are provided to allow access to features
of the host machines Bsuch as graphics, threading and networkingC in unified
ways. Note that, although there is an explicit compiling stage, at some point, the
2ava bytecode is interpreted or converted to native machine code by the 2T
compiler.
The first implementations of the language used an interpreted virtual machine to
achieve portability. These implementations produced programs that ran more
slowly than programs compiled to native executables, for instance written in - or
-NN, so the language suffered a reputation for poor performance. &ore recent
21& implementations produce programs that run significantly faster than before,
using multiple techniques.
(ne technique, known as just-in-time compilation B2TC, translates the 2ava byte
code into native code at the time that the program is run, which results in a
program that executes faster than interpreted code but also incurs compilation
overhead during execution. &ore sophisticated 1&s use dynamic recompilation,
in which the 1& can analyze the behavior of the running program and selectively
recompile and optimize critical parts of the program. !ynamic recompilation can
33
achieve optimizations superior to static compilation because the dynamic compiler
can base optimizations on knowledge about the runtime environment and the set
of loaded classes, and can identify the hot spots Bparts of the program, often inner
loops, that take up the most execution timeC. 2T compilation and dynamic
recompilation allow 2ava programs to take advantage of the speed of native code
without losing portability.
*nother technique, commonly known as static compilation, is to compile directly
into native code like a more traditional compiler. 6tatic 2ava compilers, such as
'-2, translate the 2ava language code to native ob"ect code, removing the
intermediate byte code stage. This achieves good performance compared to
interpretation, but at the expense of portabilityL the output of these compilers can
only be run on a single architecture. 6ome see avoiding the 1& in this manner as
defeating the point of developing in 2avaL however it can be useful to provide both
a generic byte code version, as well as an optimized native code version of an
application.
A"t!mati' mem!#y management
(ne of the ideas behind 2avaFs automatic memory management model is that
programmers be spared the burden of having to perform manual memory
management. n some languages the programmer allocates memory for the
creation of ob"ects stored on the heap and the responsibility of later deallocating
that memory also resides with the programmer. f the programmer forgets to
deallocate memory or writes code that fails to do so, a memory leak occurs and
the program can consume an arbitrarily large amount of memory. *dditionally, if
the program attempts to deallocate the region of memory more than once, the
result is undefined and the program may become unstable and may crash. :inally,
in non garbage collected environments, there is a certain degree of overhead and
complexity of userEcode to track and finalize allocations. (ften developers may
box themselves into certain designs to provide reasonable assurances that memory
leaks will not occur.
n 2ava, this potential problem is avoided by automatic garbage collection. The
programmer determines when ob"ects are created, and the 2ava runtime is
responsible for managing the ob"ectFs lifecycle. The program or other ob"ects can
3%
reference an ob"ect by holding a reference to it Bwhich, from a lowElevel point of
view, is its address on the heapC. Ahen no references to an ob"ect remain, the 2ava
garbage collector automatically deletes the unreachable ob"ect, freeing memory
and preventing a memory leak. &emory leaks may still occur if a programmerFs
code holds a reference to an ob"ect that is no longer neededPin other words, they
can still occur but at higher conceptual levels. The use of garbage collection in a
language can also affect programming paradigms. f, for example, the developer
assumes that the cost of memory allocation<recollection is low, they may choose
to more freely construct ob"ects instead of preEinitializing, holding and reusing
them. Aith the small cost of potential performance penalties BinnerEloop
construction of large<complex ob"ectsC, this facilitates threadEisolation Bno need to
synchronize as different threads work on different ob"ect instancesC and dataE
hiding. The use of transient immutable valueEob"ects minimizes sideEeffect
programming.
-omparing 2ava and -NN, it is possible in -NN to implement similar functionality
Bfor example, a memory management model for specific classes can be designed
in -NN to improve speed and lower memory fragmentation considerablyC, with the
possible cost of adding comparable runtime overhead to that of 2avaFs garbage
collector, and of added development time and application complexity if one favors
manual implementation over using an existing thirdEparty library. n 2ava, garbage
collection is builtEin and virtually invisible to the developer. That is, developers
may have no notion of when garbage collection will take place as it may not
necessarily correlate with any actions being explicitly performed by the code they
write. !epending on intended application, this can be beneficial or
disadvantageous; the programmer is freed from performing lowElevel tasks, but at
the same time loses the option of writing lower level code. *dditionally, the
garbage collection capability demands some attention to tuning the 21&, as large
heaps will cause apparently random stalls in performance.
2ava does not support pointer arithmetic as is supported in, for example, -NN. This
is because the garbage collector may relocate referenced ob"ects, invalidating such
pointers. *nother reason that 2ava forbids this is that type safety and security can
no longer be guaranteed if arbitrary manipulation of pointers is allowed.
Pe#3!#man'e
37
2avaFs performance has improved substantially since the early versions, and
performance of 2T compilers relative to native compilers has in some tests been
shown to be quite similar. The performance of the compilers does not necessarily
indicate the performance of the compiled codeL only careful testing can reveal the
true performance issues in any system.
3?
1/1 REMOTE METHOD INVOCATION :RMI;
)& is a specification that enables one 21& to invoke methods in an ob"ect
located in another 21&. These two 21&s could be running on the same computer
as separate processes. )& is implemented on the middleEtier of the threeEtier
architecture framework, thereby facilitating the programmers to invoke distributed
components across a networked environment. 6un introduced )& as an easy
alternative to the complex coding involved in serverEsocket programming. :or
using )&, the programmer need not know socket programming or multi
threading and needs to strongly concentrate on developing the business logic.
)& is built up on the specification of how remote and local ob"ects interoperate.
+ocal ob"ects are the ob"ects that execute on the local machine. )emote ob"ects
are those execute on all other machines. (b"ects on the remote hosts are exported
so that they can be invoked remotely. *n ob"ect exports itself by registering itself
with a )emote )egistry 6erver. * remote )egistry 6erver is a server that runs on a
server and helps the ob"ects on the other hosts to remotely access its registered
ob"ects. The registry service maintains a database of all the named remote ob"ects.
2avas )& approach is organized into a client<server framework. * local ob"ect
that invokes a method of a remote ob"ect is referred to as a client ob"ect and the
remote ob"ect whose methods are invoked is referred to as a server ob"ect.
*t the server side, an )& service is created. This service is an ob"ect with a main
class that does nothing else than creating the remote ob"ect with new and binding
it into an )& registry with a unique name. The client needs to know this remote
registry to get a reference to the service. (nce the client has this reference, it can
make remote method calls with parameters and return values as if the ob"ect
BserviceC were to be on the local host. (b"ects are transmitted through
serialization.
3H
)& is the ob"ect equivalent of )emote 0rocedure -all B)0-C. Ahile )0- allows
you to all procedures over a network, )& invokes an ob"ects methods over a
network. n the )& model, the server defines ob"ects methods over a network. n
the )& model, the server defines ob"ects that the client can use remotely. The
clients can now invoke methods of this remote ob"ect as if it were a local ob"ects
running in the same virtual machine as the client. )& hides the underlying
mechanism of transporting method arguments and return values across the
network.
)& follows a threeEtier architecture that is quite similar to -()5*, which
enables communication between distributed components written in different
languages. -()5* requires additional middleware called ()5 B(b"ect )equest
5rokerC to provide data translation from one language to another.
-()5* differs from 2ava )& in a number of ways;
4. -()5* is a languageEindependent standard.
3. -()5* includes many other mechanisms in its standard Bsuch as a
standard for T0 monitorsC none of which are part of 2ava )&.
-omponents of a !istributed )& *pplication
1/ RMI 7e#%e#
)& 6erver contains the ob"ects whose methods are to be invoked
remotely. The server creates several remote ob"ects and makes a reference
of these ob"ects in the )& registry. BThe remote ob"ect is an ordinary
ob"ect in the address space of the server processC.
*/ RMI Client
The client is the process that is invoking a method on a remote ob"ect. The
client gets the reference of one or more remote ob"ects from the )&
registry by looking up the ob"ect name. The client then invokes the
methods on the remote ob"ects to access the services of the remote ob"ects.
(nce the client gets the reference of the remote ob"ect, the methods
in the remote ob"ect are invoked "ust like the methods of a local ob"ect.
39
1/ RMI Regit#y
6ince both the client and the server may reside on different
machine<processes, there needs to be a mechanism that can establish a
relationship between the two. 2ava )& uses a network based registry
program called )& )egistry to keep track of the distributed ob"ects.
)& )egistry is a service that runs on the )& server. The remote ob"ects Bserver
ob"ectsC created by the server are registered by the ob"ects unique name in this
registry. n other words, the server ob"ect makes methods available for remote
invocation by binding it to a name in the )& )egistry. The client ob"ect can thus
check for the availability of a certain server ob"ect by looking up its name in the
registry. The )& )egistry will act as a central management point for 2ava )&. )&
)egistry is a simple name repository.
1/* RMI A#'(ite't"#e
The )& architecture consists of three layers
7t"b,7Celet!n Laye#
Rem!te Re3e#en'e Laye#
T#an$!#t Laye#
Fig 9 RMI A#'(ite't"#e
7t"b,7Celet!n Laye#
3=
JVM
-lient
6tub
)emote )eference
rereremotrereere
Transport Layer
JVM
6erver
6keleton
)emote )eference
+ayer
Transport Layer
The 6tub<6keleton layer listens to the remote method calls made by the client and redirect
these to the remote )& services on the server. This layer consists of 6tub and 6keleton
6ince the two ob"ects may physically reside on different machines, a mechanism is
needed to transmit the clientFs request to invoke a method on the server ob"ect.
7t"b
6tub resides in the client machine. To invoke methods of a remote ob"ect, the request on
the client side starts with the stub. The stub acts as a proxy to the skeleton. Ahen a client
invokes a server method, the 21& looks at the stub to do the type checking. The request
is then routed to the skeleton on the server, which in turn calls the appropriate method on
the server ob"ect. The stub packages a block of bytes, which should be the parameters in
the remote method. This package uses a deviceEindependent encoding of the parameters
used. This process of encoding the parameters is called parameter marshaling. Ahen the
client calls a remote method, the stub is invoked and it does the following;
o nitiates a connection with the remote 21&
o &arshals Bprepares and transmitsC the parameters to the server.
o Aaits for the result of the method invocation
o Jnmarshals BreadsC the return value or exception returned.
o )eturns the value to the client.
7Celet!n
6keleton resides on the server machine. 6tub communicates the method invocations to
the remote ob"ect through the skeleton. 6keleton is a server side proxy that continues
communication with the stub y reading the parameters for the call, making the call to the
remote service implementation ob"ect, accepting the return value and writing the return
value back to the stub.
6keleton performs the following operations for each received call;
o Jnmarshals BreadsC the parameters for the remote method.
o nvoke the method in the actual remote ob"ect implementation.
o &arshals the result to the caller.
o The skeleton is responsible for dispatching the client call to the
actual ob"ect implementation.
The 6tub implements only the remote interfaces. Ahen the client calls a remote method
the stub marshals and serializes the data over the network to the 6keleton. The 6keleton
in turn unmarshals and deserializes the data on the remote machine and passes the data to
3K
the actual method implementation. *fter the method completes, the return value is
delivered back to the client in the reverse order.
Rem!te Re3e#en'e Laye#
The )emote )eference +ayer interprets and manages the references made by the client to
the remote ob"ect on the server. This layer is present on the client as well as the server.
The ))+ on the clientEside receives the request for the methods from the stub that is
transferred as a marshaled stream of data to the ))+ of the server.
T#an$!#t Laye#
The transport layer is a link between the ))+ on the server side and the ))+ on the client
side. The Transport +ayer is responsible for setting up new connections. ts also
responsible for handling remote ob"ects that residing in its address space.
1/1 RMI Pa'Cage
"ava.rmi
"ava.rmi.registry
"ava.rmi.server
1/4 +a%a * Ente#$#ie E&iti!n :+*EE;)
The 23,, platform uses a multitier distributed application model. *pplication logic is
divided into components according to function, and the various application components
that make up a 23,, application are installed on different machines depending on the tier
in the multitier 23,, environment to which the application component belongs. :igure 4E
4 shows two multitier 23,, applications divided into the tiers described in the following
list. The 23,, application parts shown in :igure are presented in 23,, -omponents.
-lientEtier components run on the client machine.
AebEtier components run on the 23,, server.
5usinessEtier components run on the 23,, server.
,nterprise information system B,6CEtier software runs on the ,6 server.
*lthough a 23,, application can consist of the three or four tiers shown in :igure 23,,
multitier applications are generally considered to be threeEtiered applications because they
are distributed over three different locations; client machines, the 23,, server machine,
and the database or legacy machines at the back end. ThreeEtiered applications that run in
this way extend the standard twoEtiered client and server model by placing a
multithreaded application server between the client application and backEend storage.
%>
Fig = M"ltitie#e& A$$li'ati!n
+*EE C!m$!nent
23,, applications are made up of components. * J2EE component is a selfEcontained
functional software unit that is assembled into a 23,, application with its related classes
and files and that communicates with other components. The 23,, specification defines
the following 23,, components;
*pplication clients and applets are components that run on the client.
2ava 6erver and 2ava 6erver 0ages B260C technology components are Aeb
components that run on the server.
,nterprise 2ava5eans B,25C components Benterprise beansC are business
components that run on the server.
23,, components are written in the 2ava programming language and are compiled in the
same way as any program in the language. The difference between 23,, components and
MstandardM 2ava classes is that 23,, components are assembled into a 23,, application,
verified to be well formed and in compliance with the 23,, specification, and deployed
to production, where they are run and managed by the 23,, server.
+*EE Client
* 23,, client can be a Aeb client or an application client.
%4
-eb Client
* Aeb client consists of two parts; dynamic Aeb pages containing various types
of markup language B.T&+, 8&+, and so onC, which are generated by Aeb
components running in the Aeb tier, and a Aeb browser, which renders the pages
received from the server.
A$$let
* Aeb page received from the Aeb tier can include an embedded applet. *n
applet is a small client application written in the 2ava programming language that
executes in the 2ava virtual machine installed in the Aeb browser. .owever, client
systems will likely need the 2ava 0lugEin and possibly a security policy file in
order for the applet to successfully execute in the Aeb browser. Aeb components
are the preferred *0 for creating a Aeb client program because no plugEins or
security policy files are needed on the client systems. *lso, Aeb components
enable cleaner and more modular application design because they provide a way
to separate applications programming from Aeb page design. 0ersonnel involved
in Aeb page design thus do not need to understand 2ava programming language
syntax to do their "obs.
A$$li'ati!n Client
* 23,, application client runs on a client machine and provides a way for users to
handle tasks that require a richer user interface than can be provided by a markup
language. t typically has a graphical user interface B'JC created from 6wing or
*bstract Aindow Toolkit B*ATC *0s, but a commandEline interface is certainly
possible. *pplication clients directly access enterprise beans running in the
business tier. .owever, if application requirements warrant it, a 23,, application
client can open an .TT0 connection to establish communication with a servlet
running in the Aeb tier.
+a%a>ean C!m$!nent A#'(ite't"#e)
The server and client tiers might also include components based on the 2ava5eans
component architecture B2ava5eans componentC to manage the data flow between an
application client or applet and components running on the 23,, server or between server
components and a database. 2ava5eans components are not considered 23,, components
by the 23,, specification. 2ava5eans components have instance variables and get and set
methods for accessing the data in the instance variables. 2ava5eans components used in
%3
this way are typically simple in design and implementation, but should conform to the
naming and design conventions outlined in the 2ava5eans component architecture.
+*EE 7e#%e# C!mm"ni'ati!n
The client communicates with the business tier running on the 23,, server either directly
or, as in the case of a client running in a browser, by going through 260 pages or servlets
running in the Aeb tier.23,, application uses a thin browserEbased client or thick
application client. n deciding which one to use, you should be aware of the tradeEoffs
between keeping functionality on the client and close to the user Bthick clientC and offE
loading as much functionality as possible to the server Bthin clientC. The more
functionality you offEload to the server, the easier it is to distribute, deploy, and manage
the applicationL however, keeping more functionality on the client can make for a better
perceived user experience.
Fig ? 7e#%e# C!mm"ni'ati!n
-eb C!m$!nent
23,, Aeb components can be either servlets or 260 pages. Servlets are 2ava programming
language classes that dynamically process requests and construct responses. JS pa!es
are textEbased documents that execute as servlets but allow a more natural approach to
creating static content. 6tatic .T&+ pages and applets are bundled with Aeb components
during application assembly, but are not considered Aeb components by the 23,,
specification. 6erverEside utility classes can also be bundled with Aeb components and,
like .T&+ pages, are not considered Aeb components. +ike the client tier and as shown
%%
in :igure 4E%, the Aeb tier might include a 2ava5eans component to manage the user
input and send that input to enterprise beans running in the business tier for processing.
Fig @ -eb Tie# an& +*EE A$$li'ati!n
>"ine C!m$!nent
5usiness code, which is logic that solves or meets the needs of a particular business
domain such as banking, retail, or finance, is handled by enterprise beans running in the
business tier. *n enterprise bean also retrieves data from storage, processes it Bif
necessaryC, and sends it back to the client program.
Fig 1A >"ine an& EI7 Tie#
There are three kinds of enterprise beans; session beans, entity beans, and messageEdriven
beans. * session "ean represents a transient conversation with a client. Ahen the client
%7
finishes executing, the session bean and its data are gone. n contrast, an entity "ean
represents persistent data stored in one row of a database table. f the client terminates or
if the server shuts down, the underlying services ensure that the entity bean data is saved.
* messa!e-driven "ean combines features of a session bean and a 2ava &essage 6ervice
B2&6C message listener, allowing a business component to receive 2&6 messages
asynchronously. This tutorial describes entity beans and session beans.
Ente#$#ie In3!#mati!n 7ytem Tie#
The enterprise information system tier handles enterprise information system software
and includes enterprise infrastructure systems such as enterprise resource planning B,)0C,
mainframe transaction processing, database systems, and other legacy information
systems. 23,, application components might need access to enterprise information
systems for database connectivity
1/6 +a%a 7e#%e# Page :+7P;)
2ava 6erver 0ages technology is the 2ava platform technology for building applications
containing dynamic Aeb content such as .T&+, !.T&+ and 8&+. The 2ava 6erver
0ages technology enables the authoring of Aeb pages that create dynamic content easily
but with maximum power and flexibility.
The 2ava 6erver 0ages technology offers a number of advantages;
Q#rite Once$ %un &nywhere properties'
The 2ava 6erver 0ages technology is platform independent, both in its dynamic Aeb
pages, its Aeb servers, and its underlying server components. /ou can author 260
pages on any platform, run them on any Aeb server or Aeb enabled application
server, and access them from any Aeb browser. /ou can also build the server
components on any platform and run them on any server.
Q(i!h )uality tool support
The Arite (nce, )un *nywhere properties of 260 allows the user to choose "est-of-
"reed tools.
Q%euse of components and ta! li"raries
The 2ava 6erver 0ages technology emphasizes the use of reusable components such
as; 2ava5eans components, ,nterprise 2ava5eans components and tag libraries.
These components can be used in interactive tools for component development and
page composition. This saves considerable development time while giving the crossE
platform power and flexibility of the 2ava programming language and other scripting
%?
languages.
QSeparation of dynamic and static content
The 2ava 6erver 0ages technology enables the separation of static content from
dynamic content that is inserted into the static template. This greatly simplifies the
creation of content. This separation is supported by beans specifically designed for
the interaction with serverEside ob"ects.
QSupport for scriptin! and actions
The 2ava 6erver 0ages technology supports scripting elements as well as actions.
*ctions permit the encapsulation of useful functionality in a convenient form that
can also be manipulated by toolsL scripts provide a mechanism to !lue to!ether this
functionality in a perEpage manner.
1/9 +7P a#'(ite't"#e
260s are built on top of 6JNs servlet technology. 260s are essential an .T&+ page with
special 260 tags embedded. These 260 tags can contain 2ava code. The 260 file extension
is ."sp rather than .htm or .html. The 260 engine parses the ."sp and creates a 2ava servlet
source file. t then compiles the source file into a class fileL this is done the first time and
this why the 260 is probably slower the first time it is accessed. *ny time after this the
special compiled servlet is executed and is therefore returns faster.
1/= +a%a 7'#i$t
2ava6cript is a programming language that allows scripting of events, ob"ects, and actions
to create nternet applications. * website development environment will allow the
creation of nteractive Aeb 0ages. The coding techniques are capable of accepting a
clientFs requests and processing these requests. The web site development environment
should also provide the facility for FvalidatingF user input. Aith 2ava6cript, forms are a
consideration in nearly every page you design. -apturing user requests is traditionally
done via a FformF. 6o the web site needs to have facilities to create forms. Text fields and
text areas can dynamically change in response to user responses.
TOMCAT 6/A
Tomcat is a servlet container and 2ava 6erver 0ages implementation it may be used stand
alone, or in con"unction with several popular web servers.
o *pache version 4.% or later
o &6 nternet nformation 6erver ,version 7.> or later
%H
o &6 personel web server, version 7.> or later
o Net6cape enterprise server , version %.> or later
Tomcat is a security update release. This release closes a whole that potentially allowed
access to resources protected by a Rsecurity constraint S in web.xml.
Intalling an& R"nning T!m'at 6/A
Tomcat requires a 2ava )untime ,nvironment B2),C.-onformant to 2), 4.4 or later
including any 2ava3 platform system. f one wishes to develop applications you will need
a "ava compiler, such as the one included in a "ava development kit 4.4 or later
environment including 2!@s conformant with 2ava3.
1/? Teting)
6oftware Testing is the process of executing software in a controlled manner, in order to
answer the question E !oes the software behave as specifiedG. 6oftware testing is often
used in association with the terms verification and validation. 1alidation is the checking
or testing of items, includes software, for conformance and consistency with an associated
specification. 6oftware testing is "ust one kind of verification, which also uses techniques
such as reviews, analysis, inspections, and walkthroughs. 1alidation is the process of
checking that what has been specified is what the user actually wanted.
1alidation ) *re we doing the right "obG
1erification ) *re we doing the "ob rightG
6oftware testing should not be confused with debugging. !ebugging is the process of
analyzing and localizing bugs when software does not behave as expected. *lthough the
identification of some bugs will be obvious from playing with the software, a methodical
approach to software testing is a much more thorough means for identifying bugs.
!ebugging is therefore an activity which supports testing, but cannot replace testing.
(ther activities which are often associated with software testing are static analysis and
dynamic analysis. 6tatic analysis investigates the source code of software, looking for
problems and gathering metrics without actually executing the code. !ynamic analysis
looks at the behavior of software while it is executing, to provide information such as
execution traces, timing profiles, and test coverage information. Testing is a set of activity
that can be planned in advanced and conducted systematically. Testing begins at the
module level and work towards the integration of entire computers based system. Nothing
%9
is complete without testing, as it vital success of the system testing ob"ectives, there are
several rules that can serve as testing ob"ectives include;
Testing is a process of executing a program with the intend of findingan error.
* good test case is one that has high possibility of finding an undiscovered error.
* successful test is one that uncovers an undiscovered error.
f a testing is conducted successfully according to the ob"ectives as stated above, it would
uncovered errors in the software also testing demonstrate that the software function
appear to be working according to the specification, that performance requirement appear
to have been met.
There are three ways to test program.
:or correctness
:or implementation efficiency
:or computational complexity
Test for correctness are supposed to verify that a program does exactly what it was
designed to do. This is much more difficult than it may at first appear, especially for large
programs.
TE7T PLAN
* test plan implies a series of desired course of action to be followed in accomplishing
various testing methods. The Test 0lan acts as a blue print for the action that is to be
followed. The software engineers create a computer program, its documentation and
related data structures. The software developers is always responsible for testing the
individual units of the programs, ensuring that each performs the function for which it
was designed. There is an independent test group BT'C which is to remove the inherent
problems associated with letting the builder to test the thing that has been built. The
specific ob"ectives of testing should be stated in measurable terms. 6o that the mean time
to failure, the cost to find and fix the defects, remaining defect density or frequency of
occurrence and test workEhours per regression test all should be stated within the test
plan.
The levels of testing include;
Jnit testing
ntegration Testing
!ata validation Testing
(utput Testing
CHAPTER-4
OUTPUT
%=
7CREEN 7HOT7)
H!me Page)
Fig 11 (!me $age
A&min L!gin)
Fig 1* a&min l!gin
On Filling In'!##e't Detail)
%K
Fig 11 !n 3illing in'!##e't &etail
On Filling C!##e't Detail)
Fig 14 !n 3illing '!##e't &etail
C#eate ne8 a''!"ntant $age)
7>
Fig 16 ne8 a''!"ntant $age
A3te# '#eating a''!"ntant ea'( a''!"ntant 'an l!gin t(#!"g( 8el'!me
$age/ An& a&min 'an b#!8e any a''!"ntant a 3!ll!8)
Fig 19 b#!8e
A''!"ntant L!gin)
74
Fig 1= a''!"ntant l!gin
7ea#'(ing Re'!#&)
Fig 1? ea#'(ing #e'!#&
T! a&& ne8 #e'!#&)
73
Fig 1@ ne8 #e'!#&
T! m!&i3y &etail 3i#t 3in& t(e #e'!#& y!" 8ant t! m!&i3y it a 3!ll!8)
Fig *A m!&i3y
N!8 $!int t(e i& !3 #e$e'ti%e #!8)
7%
Fig *1 &etail t! be '(ange&
D"e#y t! A&min)
Fig ** 2"e#y
CHAPTER-6
77
CONCLU7ION
The pro"ect titled as #payment billing system$ is a web based application. This software
provides facility for, create, update and delete accountant details after login. t can search
branch wise accountant. *nd also search all candidates studying in the various branches
and can update and delete them. 6oftware is developed with modular approach. *ll
modules in the system have been tested with valid data and invalid data and everything
work successfully. Thus the system has fulfilled all the ob"ectives identified and is able to
replace the existing system. The pro"ect has been completed successfully with the
maximum satisfaction of the organization. The constraints are met and overcome
successfully. The system is designed as like it was decided in the design phase. The
pro"ect gives good idea on developing a fullEfledged application satisfying the user
requirements. The system is very flexible and versatile. This software has a userEfriendly
screen that enables the user to use without any inconvenience. 1alidation checks induced
have greatly reduced errors. 0rovisions have been made to upgrade the software.
CHAPTER-9
7?
FUTURE 7COPE
n future we can use photo reorganization instead of using heterogeneous database more
over .igh speed, accuracy and nonEredundant data are the main advantages of the
proposed system. n the proposed system the user is provided with a choice of data
screen, which are similar in formats to the source documents. !ata entry errors can be
minimized through validity checks. *fter the verification only the data are placed the
permanent database. The software can be developed further to include a lot of modules
because the proposed system is developed on the view of future, for example we should
develop the system as a database independent using 2!5- so we can connect it to any
other database, Now the proposed system is based on 0- and intranet but in the future if
we need to convert it into internet then we need to change the front end only because we
are developing this on the basis of ((0 technology and most of the business logics are
bounded in the class files and module like reusable components.
7H
APPENDIE
-oding
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RhtmlS
RheadS
RtitleS
Aelcome 0age
R<titleS
Rlink relVMstylesheetM typeVMtext<cssM hrefVMstyle.cssM <S
R<headS
RbodyS
Rdiv idVMouterMS
Rdiv idVMheaderMS
Rdiv idVMlogoMS
Rh4S
0ayment 5illing 6ystem
R<h4S
R<divS
R<divS
Rdiv idVMbannerMS
Rdiv classVMcaptionsMS
Rh3S6ign inR<h3S
R<divS
Rimg srcVMmages<banner."pgM altVMM <S
R<divS
Rdiv idVMnavMS
RulS
Rli classVMfirstMS
Ra hrefVMhome."spMS.omeR<aS
R<liS
RliS
Ra hrefVMgeneralinfo."spMSNew )egistrationR<aS
R<liS
RliS
Ra hrefVMmodify."spMS&odify !etailR<aS
R<liS
RliS
Ra hrefVMahome."spMS*dministratorR<aS
R<liS
RliS
Ra hrefVMcontactus."spMS-ontact usR<aS
R<liS
R<ulSRbr classVMclearM <S
R<divS
RT
ifBrequest.get*ttributeBMnotloginXmsgMCYVnullC
Z
out.printBMRfont sizeVF3F colorVFredF mSMCL
out.printBrequest.get*ttributeBMnotloginXmsgMCCL
79
out.printBMR<fontSMCL
[
TS
RT
ifBrequest.get*ttributeBM,rrorMCYVnullC
Z
out.printBMRfont sizeVF3F colorVFredF mSMCL
out.printBrequest.get*ttributeBM,rrorMCCL
out.printBMR<fontSMCL
[
TS
Rdiv idVMmainMS
Rtable alignVMrightMS
Rtr alignVMcenterMS
Rtd styleVMcolor; navyLMSR5SNoticeR<5SR<tdS
R<trS
RtrS
RtdS
RdivS
Rmarquee directionVMupM widthVM%>>pxM truespeedVMtruespeedM
onmouseoverVMstopBCM onmouseoutVMstartBCM styleVMcolor; redLMSAelcome
*dministrator sir.
/ou -an 1isit a lot of information
about my various 5ranches.and *ccountants
R<marqueeS
R<divS
R<tdS
R<trS
R<tableS
Rh% styleVMcolor; navyLM alignVMcenterMSR5S-onsultant;E 'oralR<5SR<h%S
Rdiv idVMboxMS
Rform methodVMpostM actionVMaloginprocess."spMS
RtableS
RtrS
Rtd styleVMcolor;navyLMSR5S +ogin :ormR<5SR<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
RtrS
RtdSJser Name;R<tdS
RtdSRinput typeVMtextM nameVMusernameM<SR<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
7=
RtrS
RtdS0assword;R<tdS
RtdSRinput typeVMpasswordM nameVMuserpassM<SR<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
RtrS
RtdS\nbspLR<tdS
RtdSRinput typeVMsubmitM valueVM6ign inMSR<tdS
R<trS
R<tableS
R<formS
RbrS
R<divS
R<divS
R<divS
R"sp;include pageVMfooter."spMSR<"sp;includeS
R<bodyS
R<htmlS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page importVM"ava.sql.WM TS
RT
6tring nVrequest.get0arameterBMvalMCL
6tring branchVrequest.get0arameterBMbranchMCL
ifBn.lengthBCS>C
Z
try
Z
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMselect W from payXreg where
branchVFMNbranchNMF and username like FTMNnNMTFMCL
<<ps.set6tringB4,nCL
out.printBMRbrSMCL
)esult6et rsVps.executeDueryBCL
out.printBMRtable borderVF?F cellspacingV? cellpaddingV3 idVFmyTableFSMCL
out.printBMRtrSRtdSRa hrefVF]F nameVF!F
onmouseoverVF"avascript;view*llnfoBthis.nameCFSR5S!R<5SR<aSR<tdSRtdSR5SNa
meR<5SR<tdSRtdSR5S6alaryR<5SR<tdSR<trSMCL
whileBrs.nextBCC
Z
out.printBMRtrSRtdSRa hrefVF]F nameVFMNrs.get6tringB4CNMF
onmouseoverVF"avascript;view*llBthis.nameCFSMNrs.get6tringB4CNMR<aSR<tdSMCL
out.printBMRtdSMNrs.get6tringB3CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB9CNMR<tdSMCL
out.printBMR<trSMCL
[
out.printBMR<tableSMCL
7K
con.closeBCL
[
catchB,xception eC
Z
e.print6tackTraceBCL
[
[<<end of if
TS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RhtmlS
RheadS
RtitleS
*dmin .ome
R<titleS
RscriptS
var requestL
function sendnfoBC
Z
var branchVdocument.myform.select.valueL
var vVdocument.myform.findName.valueL
var urlVMafindname."spGvalVMNvNM\branchVMNbranchL
ifBwindow.8&+.ttp)equestC
Z
requestVnew 8&+.ttp)equestBCL
[
else ifBwindow.*ctive8(b"ectC
Z
requestVnew *ctive8(b"ectBM&icrosoft.8&+.TT0MCL
[
try
Z
request.onreadystatechangeVgetnfoL
request.openBM',TM,url,trueCL
request.sendBCL
[
catchBeC
Z
alertBMJnable to connect to serverMCL
[
[
function getnfoBC
Z
ifBrequest.ready6tateVV7C
Z
var valVrequest.responseTextL
document.get,lement5ydBFlocationFC.inner.T&+VvalL
[
[
function view*llBnameC
Z
?>
var vVnameL
var urlVMaviewall."spGvalVMNvL
ifBwindow.8&+.ttp)equestC
Z
requestVnew 8&+.ttp)equestBCL
[
else ifBwindow.*ctive8(b"ectC
Z
requestVnew *ctive8(b"ectBM&icrosoft.8&+.TT0MCL
[
try
Z
request.onreadystatechangeVget*llnfoL
request.openBM',TM,url,trueCL
request.sendBCL
[
catchBeC
Z
alertBMJnable to connect to serverMCL
[
[
function get*llnfoBC
Z
ifBrequest.ready6tateVV7C
Z
var valVrequest.responseTextL
document.get,lement5ydBFbottomFC.inner.T&+VvalL
[
[
R<scriptS
R<headS
Rdiv idVMouterMS
R"sp;include pageVMheader."spMSR<"sp;includeS
RT
6tring isloginVB6tringCsession.get*ttributeBMisloginMCL
ifBisloginVVnullC
Z
request.set*ttributeBMnotloginXmsgM,M6orry,0lease do +ogin firstMCL
TS
R"sp;forward pageVMindex."spMSR<"sp;forwardS
RT
[
TS
Rbody widthVM4>>MS
Rdiv idVMmainMS
Rh% styleVMcolor; navyLM alignVMcenterMSR5S-onsultant;E 'oralR<5SR<h%S
Rdiv idVMboxMS
RT
ifBrequest.get*ttributeBMmsgMCYVnullC
Z
?4
6tring msgVB6tringCrequest.get*ttributeBMmsgMCL
out.printBMRfont styleVFcolor; navyFSR5SMCL
out.printBmsgCL
out.printBMR<5SR<fontSMCL
[
TS
Rform nameVMmyformM S
RtableS
RtrS
RtdSRfont styleVMcolor; navyLMS5ranch;R<fontSR<tdS
RtdS
Rselect nameVMbranchM idVMselectMS
RoptionSE6elect a 5ranchER<optionS
RoptionS6olanR<optionS
RoptionS!elhiR<optionS
RoptionS-handigarhR<optionS
R<selectS
R<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
RtrS
RtdSRfont styleVMcolor; navyLMS:ind;ER<fontSR<tdS
RtdS
Rinput typeVMtextM alignVMrightM nameVMfindNameM
onkeyupVMsendnfoBCMSR<inputS
R<tdS
R<trS
R<tableS
Rdiv idVMrightM alignVMrightMS
Ra hrefVMcreate."spMSRfont styleVMcolor; navyLMSR5S-reate New
*ccountantR<5SR<fontSR<aS
R<divS
Rdiv idVMlocationM alignVMleftMSR<divS
R<formS
Rdiv idVMbottomM alignVM"ustifyMSR<divS
Rdiv idVMgetgeninfoM alignVM"ustifyMSR<divS
R<divS
R<divS
R<bodyS
R"sp;include pageVMfooter."spMSR<"sp;includeS
R<divS
R<htmlS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTUpage importVMorg.omg.-()5*.0J5+-X&,&5,)MTS
RT
6tring usernameVget6ervlet-ontextBC.getnit0arameterBMJsernameMCL
6tring passwordVget6ervlet-ontextBC.getnit0arameterBM0asswordMCL
?3
ifBrequest.get0arameterBMusernameMC.equalsgnore-aseBusernameC\\
request.get0arameterBMuserpassMC.equalsgnore-aseBpasswordCC
Z
session.set*ttributeBMisloginM,Mplz sign in firstMCL
TS
R"sp;forward pageVMahome."spMSR<"sp;forwardS
RT
[
else
Z
request.set*ttributeBM,rrorM,M6orryY Jsername or 0assword ,rror. plz ,nter -orrect
!etailMCL
session.set*ttributeBM+oginmsgM,Mplz sign in firstMCL
TS
R"sp;forward pageVMadmin."spMSR<"sp;forwardS
RT
[
TS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page importVM"ava.sql.WM TS
RT
6tring nVrequest.get0arameterBMvalMCL
ifBn.lengthBCS>C
Z
try
Z
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMdelete from payXreg where id
VFMNnNMFMCL
int "Vps.executeJpdateBCL
ifB"S>C
Z
request.set*ttributeBMmsgM,M)ecord .as been 6uccessfully !eletedMCL
[
else
Z
request.set*ttributeBMmsgM,MThere is some problemMCL
[
[
catchB,xception eC
Z
e.print6tackTraceBCL
[
[<<end of if
TS
R"sp;forward pageVMahome."spMSR<"sp;forwardS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTUpage importVM"ava.sql.WMTS
?%
RT
try
Z
6tring usernameVrequest.get0arameterBMusernameMCL
6tring userpassVrequest.get0arameterBMuserpassMCL
6tring dateofbirthVrequest.get0arameterBMdobMCL
6tring dateof"oiningVrequest.get0arameterBMdo"MCL
6tring salaryVrequest.get0arameterBMsalaryMCL
6tring branchVrequest.get0arameterBMbranchMCL
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMinsert into payXreg
valuesBG,G,G,G,G,G,GCMCL
ps.setntB4,3CL
ps.set6tringB3,usernameCL
ps.set6tringB%,userpassCL
ps.set6tringB7,branchCL
ps.set6tringBH,dateofbirthCL
ps.set6tringB?,dateof"oiningCL
ps.set6tringB9,salaryCL
int sVps.executeJpdateBCL
6ystem.out.printBsCL
[
catchB6D+,xception e3C
Z
e3.print6tackTraceBCL
[
TS
R"sp;forward pageVMahome."spMSR<"sp;forwardS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page importVM"ava.sql.WM TS
RT
6tring nVrequest.get0arameterBMvalMCL
ifBn.lengthBCS>C
Z
try
Z
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMselect W from payXreg where id
VFMNnNMFMCL
<<ps.set6tringB4,nCL
)esult6et rsVps.executeDueryBCL
out.printBMRbrSMCL
out.printBMRtable borderVF?F cellspacingV? cellpaddingV3SMCL
out.printBMRtrSRtdSRa hrefVF]F nameVF!F
onmouseoverVF"avascript;view*llnfoBthis.nameCFSR5S!R<5SR<aSR<tdSRtdSR5SJs
er nameR<5SR<tdSRtdSR5S0asswordR<5SR<tdSRtdSR5S!ate of
?7
"oiningR<5SR<tdSRtdSR5S!ate of
5irthR<5SR<tdSRtdSR5S6alaryR<5SR<tdSRtdSR5S)emoveR<5SR<tdSR<trSMCL
whileBrs.nextBCC
Z
out.printBMRtrSRtdSRa hrefVF]F nameVFMNrs.get6tringB4CNMF
onmouseoverVF"avascript;view*llnfoBthis.nameCFSMNrs.get6tringB4CNMR<aSR<tdSMCL
out.printBMRtdSMNrs.get6tringB3CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB%CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB?CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringBHCNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB9CNMR<tdSMCL
out.printBMRtdSRa hrefVFaremove."spGvalVMNrs.get6tringB4CNMF
nameVFMNrs.get6tringB4CNMFS!eleteR<aSR<tdSMCL
out.printBMR<trSMCL
[
out.printBMR<tableSMCL
con.closeBCL
[
catchB,xception eC
Z
e.print6tackTraceBCL
[
[<<end of if
TS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RhtmlS
Rdiv idVMouterMS
R"sp;include pageVMheader."spMSR<"sp;includeS
RT
6tring isloginVB6tringCsession.get*ttributeBMisloginMCL
ifBisloginVVnullC
Z
request.set*ttributeBMnotloginXmsgM,M6orry,0lease do +ogin firstMCL
TS
R"sp;forward pageVMindex."spMSR<"sp;forwardS
RT
[
TS
RbodyS
R:ont styleVMcolor; navyLM sizeVM7MS-ontact Js;R<:ontS
Rform methodVMpostM nameVMmyformM idVMmyformM actionVMquery."spMS
Rtable widthVM4>>TMS
RtrS
RtdS
Rtable widthVM??TM alignVMleftM S
RtrS
RtdSRimg srcVMmages<pic>4."pgM<SR<tdS
RtdS
R:ont styleVMcolor; navyLM sizeVM%MSR5S/our
Duery;R<5SR<:ontSRbrS
??
Rtextarea nameVMqueryM styleVMwidth; H>>pxL
height;=>pxMSR<textareaSRbrS
R:ont styleVMcolor; navyLM
sizeVM3MSR5S,mail;R<5SR<:ontSRinput typeVMtextM nameVMemailM styleVMwidth;
4=>pxL M<S
Rinput typeVMsubmitM valueVMsubmitM styleVMpadding; 3px
3pxM S
R<tdS
R<trS
R<tableS
R<tdS
RtdS
Rtable alignVMrightM S
Rtr alignVMleftMS
RtdS
R:ont styleVMcolor; navyLM sizeVM%MS-ontact No.
NK4K7?K=?7K=3R<:ontSRbrS
R:ont styleVMcolor; navyLM sizeVM%MS,mail
id;m"=4KH3Ugmail.comR<:ontSRbrS
R:ont styleVMcolor; navyLM sizeVM%MS-ontact
0erson;&anishR<:ontS
R<tdS
R<trS
R<tableS
R<tdS
R<trS
R<tableS
R<formS
R<bodyS
R"sp;include pageVMfooter."spMSR<"sp;includeS
R<divS
R<htmlS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RhtmlS
Rdiv idVMouterMS
R"sp;include pageVMheader."spMSR<"sp;includeS
Rdiv idVMmainMS
Rh% styleVMcolor; navyLM alignVMcenterMSR5S-onsultant;E 'oralR<5SR<h%S
Rdiv idVMboxMS
Rform nameVMmyformM actionVMasave."spMS
RtableS
RtrS
RtdS5ranch;R<tdS
RtdS
Rselect nameVMbranchMS
RoptionSE6elect a 5ranchER<optionS
RoptionS6olanR<optionS
RoptionS!elhiR<optionS
RoptionS-handigarhR<optionS
R<selectS
?H
R<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
RtrS
RtdSJsername;R<tdS
RtdS
Rinput typeVMtextM nameVMusernameM<S
R<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
RtrS
RtdS0assword;R<tdS
RtdS
Rinput typeVMpasswordM nameVMuserpassM<S
R<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
RtrS
RtdS!ate of 2oining;R<tdS
RtdS
Rinput typeVMtextM nameVMdo"M<S
R<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
RtrS
RtdS!ate of 5irth;R<tdS
RtdS
Rinput typeVMtextM nameVMdobM<S
R<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
RtrS
RtdS6alary;R<tdS
RtdS
Rinput typeVMtextM nameVMsalaryM<S
R<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
?9
RtrS
RtdS\nbspLR<tdS
RtdS
Rinput typeVMsubmitM valueVMcreateM styleVMpadding; 3MS
R<tdS
R<trS
RtrS
RtdSRbrSR<tdS
R<trS
R<tableS
Rdiv idVMlocationM alignVMleftMSR<divS
R<formS
R<divS
R<divS
R"sp;include pageVMfooter."spMSR<"sp;includeS
R<divS
R<htmlS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page importVM"ava.sql.WM TS
RT
6tring nVrequest.get0arameterBMvalMCL
ifBn.lengthBCS>C
Z
try
Z
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMselect W from student where name
like FTMNnNMTFMCL
<<ps.set6tringB4,nCL
out.printBMRbrSMCL
)esult6et rsVps.executeDueryBCL
out.printBMRtable borderVF?F cellspacingV? cellpaddingV3 idVFmyTableFSMCL
out.printBMRtrSRtdSRa hrefVF]F nameVF!F
onmouseoverVF"avascript;view*llnfoBthis.nameCFSR5S!R<5SR<aSR<tdSRtdSR5SNa
meR<5SR<tdSRtdSR5S&obileR<5SR<tdSR<trSMCL
whileBrs.nextBCC
Z
out.printBMRtrSRtdSRa hrefVF]F nameVFMNrs.get6tringB4CNMF
onmouseoverVF"avascript;view*llBthis.nameCFSMNrs.get6tringB4CNMR<aSR<tdSMCL
out.printBMRtdSMNrs.get6tringB3CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB7CNMR<tdSMCL
out.printBMR<trSMCL
[
out.printBMR<tableSMCL
con.closeBCL
[
catchB,xception eC
Z
?=
e.print6tackTraceBCL
[
[<<end of if
TS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page importVM"ava.sql.WM TS
RT
6tring nVrequest.get0arameterBMvalMCL
ifBn.lengthBCS>C
Z
try
Z
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMselect W from student where name
like FTMNnNMTFMCL
<<ps.set6tringB4,nCL
out.printBMRbrSMCL
)esult6et rsVps.executeDueryBCL
out.printBMRtable borderVF?F cellspacingV? cellpaddingV3 idVFmyTableFSMCL
out.printBMRtrSRtdSRa hrefVF]F nameVF!F
onmouseoverVF"avascript;view*llnfoBthis.nameCFSR5S!R<5SR<aSR<tdSRtdSR5SNa
meR<5SR<tdSRtdSR5S&obileR<5SR<tdSR<trSMCL
whileBrs.nextBCC
Z
out.printBMRtrSRtdSRa hrefVF]F nameVFMNrs.get6tringB4CNMF
onmouseoverVF"avascript;send'ennfoBthis.nameCFSMNrs.get6tringB4CNMR<aSR<tdSMCL
out.printBMRtdSMNrs.get6tringB3CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB7CNMR<tdSMCL
out.printBMR<trSMCL
[
out.printBMR<tableSMCL
con.closeBCL
[
catchB,xception eC
Z
e.print6tackTraceBCL
[
[<<end of if
TS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RhtmlS
Rlink relVMstylesheetM typeVMtext<cssM hrefVMstyle.cssM <S
Rdiv idVMheaderMS
Rh7S
-opyright 3>47 *ll rights reserved.fore more information please visit; Ra
hrefVMwww."avatpoint.comMSRfont styleVMcolor; yellowLMS"avatpoint.comR<fontSR<aS
R<h7S
R<divS
?K
R<htmlS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page importVM"ava.sql.WM TS
RT
6tring nVrequest.get0arameterBMvalMCL
ifBn.lengthBCS>C
Z
try
Z
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMselect W from student where name
like FMNnNMTFMCL
<<ps.set6tringB4,nCL
out.printBMRbrSMCL
)esult6et rsVps.executeDueryBCL
out.printBMRtable borderVF?F cellspacingV? cellpaddingV3 idVFmyTableFSMCL
out.printBMRtrSRtdSRa hrefVF]F nameVF!F
onmouseoverVF"avascript;get'ennfoBthis.nameCFSR5S!R<5SR<aSR<tdSRtdSR5SNa
meR<5SR<tdSRtdSR5S&obileR<5SR<tdSR<trSMCL
whileBrs.nextBCC
Z
out.printBMRtrSRtdSRa hrefVF]F nameVFMNrs.get6tringB4CNMF
onmouseoverVF"avascript;send'ennfoBthis.nameCFSMNrs.get6tringB4CNMR<aSR<tdSMCL
out.printBMRtdSMNrs.get6tringB3CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB7CNMR<tdSMCL
out.printBMR<trSMCL
[
out.printBMR<tableSMCL
con.closeBCL
[
catchB,xception eC
Z
e.print6tackTraceBCL
[
[<<end of if
TS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RhtmlS
RheadS
RtitleS
New )egistration
R<titleS
RscriptS
var requestL
function sendnfoBC
Z
var vVdocument.myform.findName.valueL
var urlVMfindname4."spGvalVMNvL
H>
ifBwindow.8&+.ttp)equestC
Z
requestVnew 8&+.ttp)equestBCL
[
else ifBwindow.*ctive8(b"ectC
Z
requestVnew *ctive8(b"ectBM&icrosoft.8&+.TT0MCL
[
try
Z
request.onreadystatechangeVgetnfoL
request.openBM',TM,url,trueCL
request.sendBCL
[
catchBeC
Z
alertBMJnable to connect to serverMCL
[
[
function getnfoBC
Z
ifBrequest.ready6tateVV7C
Z
var valVrequest.responseTextL
document.get,lement5ydBFhiFC.inner.T&+VvalL
[
[
function send'ennfoBnameC
Z
var vVnameL
var urlVMgetgeninfoname."spGvalVMNvL
ifBwindow.8&+.ttp)equestC
Z
requestVnew 8&+.ttp)equestBCL
[
else ifBwindow.*ctive8(b"ectC
Z
requestVnew *ctive8(b"ectBM&icrosoft.8&+.TT0MCL
[
try
Z
request.onreadystatechangeVget'ennfoL
request.openBM',TM,url,trueCL
request.sendBCL
[
catchBeC
Z
alertBMJnable to connect to serverMCL
[
[
H4
function get'ennfoBC
Z
ifBrequest.ready6tateVV7C
Z
var valVrequest.responseTextL
document.get,lement5ydBFhelloFC.inner.T&+VvalL
[
[
function set:ormBC
Z
var urlVMsetform."spML
ifBwindow.8&+.ttp)equestC
Z
requestVnew 8&+.ttp)equestBCL
[
else ifBwindow.*ctive8(b"ectC
Z
requestVnew *ctive8(b"ectBM&icrosoft.8&+.TT0MCL
[
try
Z
request.onreadystatechangeVget:ormL
request.openBM',TM,url,trueCL
request.sendBCL
[
catchBeC
Z
alertBMJnable to connect to serverMCL
[
[
function get:ormBC
Z
ifBrequest.ready6tateVV7C
Z
var valVrequest.responseTextL
document.get,lement5ydBFhelloFC.inner.T&+VvalL
[
[
function getBob"C
Z
var poststr V MidVM N
encodeJ)B document.get,lements5yNameBMidMC.value CL
M\nameVM N encodeJ)B document.get,lements5yNameBMnameMC.value CL
M\courseVM N
encodeJ)B document.get,lements5yNameBMcourseMC.value CL
M\mobileVM N encodeJ)B document.get,lements5yNameBMmobileMC.value
CL
M\fathernameVM N
encodeJ)B document.get,lements5yNameBMfathernameMC.value CL
H3
M\mothernameVM N
encodeJ)B document.get,lements5yNameBMmothernameMC.value CL
M\qualificationVM N
encodeJ)B document.get,lements5yNameBMqualificationMC.value CL
M\dateofbirthVM N
encodeJ)B document.get,lements5yNameBMdateofbirthMC.value CL
M\dateof"oiningVM N
encodeJ)B document.get,lements5yNameBMdateof"oiningMC.value CL
M\feesubVM N
encodeJ)B document.get,lements5yNameBMfeesubMC.value CL
M\paidVM N encodeJ)B document.get,lements5yNameBMpaidMC.value CL
M\feeVM N encodeJ)B document.get,lements5yNameBMfeeMC.value CL
M\balanceVM N
encodeJ)B document.get,lements5yNameBMbalanceMC.value CL
M\addressVM N
encodeJ)B document.get,lements5yNameBMaddressMC.value CL
M\descriptionVM N
encodeJ)B document.get,lements5yNameBMdescriptionMC.value CL
M\trainerVM N
encodeJ)B document.get,lements5yNameBMtrainerMC.value CL
make0(6T)equestBMsave."spM,poststrCL
[
function make0(6T)equestBurl, parametersC
Z
httpXrequestVfalseL
ifBwindow.8&+.ttp)equestC
Z
<< &ozilla, 6afari,...
httpXrequest V new 8&+.ttp)equestBCL
if BhttpXrequest.override&imeTypeC
Z
<< set type accordingly to anticipated content type
<<httpXrequest.override&imeTypeBFtext<xmlFCL
httpXrequest.override&imeTypeBFtext<htmlFCL
[
[
else if Bwindow.*ctive8(b"ectC
Z
<< ,
try
Z
httpXrequest V new *ctive8(b"ectBM&sxml3.8&+.TT0MCL
[
catchBeC
Z
try
Z
httpXrequest V new *ctive8(b"ectBM&icrosoft.8&+.TT0MCL
[
catchBeCZ[
H%
[
[
ifBYhttpXrequestC
Z
alertBF-annot create 8&+.TT0 instanceFCL
return falseL
[
httpXrequest.onreadystatechange V alert-ontentsL
httpXrequest.openBF0(6TF, url, trueCL
httpXrequest.set)equest.eaderBM-ontentEtypeM, Mapplication<xEwwwEformE
urlencodedMCL
httpXrequest.set)equest.eaderBM-ontentElengthM, parameters.lengthCL
httpXrequest.set)equest.eaderBM-onnectionM, McloseMCL
httpXrequest.sendBparametersCL
[
R<scriptS
R<headS
Rdiv idVMouterMS
R"sp;include pageVMheader."spMSR<"sp;includeS
RT
6tring isloginVB6tringCsession.get*ttributeBMisloginMCL
ifBisloginVVnullCZ
request.set*ttributeBMnotloginXmsgM,M6orry,0lease do +ogin firstMCL
TS
R"sp;forward pageVMindex."spMSR<"sp;forwardS
RT
[
TS
Rbody widthVM4>>MS
Rdiv idVMmainMS
Rh% styleVMcolor; navyLM alignVMcenterMSR5S-onsultant;E 'oralR<5SR<h%S
Rdiv idVMboxMS
Rform actionVMsave."spM nameVMmyformM idVMhelloM methodVMpostMS
Rtable widthVM4>>TMS
RtrS
RtdS
Rtable widthVM??TM alignVMleftM styleVMtableElayout; fixedLMS
RtrS
RtdS
Rtable cellspacingV4? cellpaddingV4?MS
RtrS
RtdS
Rfont styleVMcolor;navyMSR5S6tudent
!etail;R<5SR<fontS
R<tdS
R<trS
RtrS
RtdSR5S!;R<5SR<tdS
RtdS
Rinput typeVMtextM nameVMidMSR<inputS
H7
R<tdS
R<trS
RtrS
RtdSR5SName;R<5SR<tdS
RtdS
Rinput typeVMtextM nameVMnameM SR<inputS
R<tdS
R<trS
RtrS
RtdSR5S-ourse;R<5SR<tdS
RtdSRinput typeVMtextM
nameVMcourseMSR<inputSR<tdS
R<trS
RtrS
RtdSR5S&obile;R<5SR<tdS
RtdS
Rinput typeVMtextM nameVMmobileMSR<inputS
R<tdS
R<trS
RtrS
RtdSR5S:atherFs Name;R<5SR<tdS
RtdS
Rinput typeVMtextM
nameVMfathernameMSR<inputS
R<tdS
R<trS
RtrS
RtdSR5S&otherFs Name;R<5SR<tdS
RtdS
Rinput typeVMtextM
nameVMmothernameMSR<inputS
R<tdS
R<trS
RtrS
RtdSR5SDualification;R<5SR<tdS
RtdS
Rinput typeVMtextM
nameVMqualificationMSR<inputS
R<tdS
R<trS
RtrS
RtdSR5S!ate of 5irth;R<5SR<tdS
RtdS
Rinput typeVMtextM
nameVMdateofbirthMSR<inputS
R<tdS
R<trS
RtrS
RtdSR5S!ate of 2oining;R<5SR<tdS
RtdS
H?
Rinput typeVMtextM nameVMdateof"oiningM
SR<inputS
R<tdS
R<trS
RtrS
RtdSR5S!ate of 6ubmission;R<5SR<tdS
RtdS
Rinput typeVMtextM nameVMfeesubM
SR<inputSR<tdS
R<trS
RtrS
RtdSR5S0aid;R<5SR<tdS
RtdS
Rinput typeVMtextM nameVMpaidM SR<inputS
R<tdS
R<trS
RtrS
RtdSR5S:ee;R<5SR<tdS
RtdS
Rinput typeVMtextM nameVMfeeM SR<inputS
R<tdS
R<trS
RtrS
RtdSR5S5alance;R<5SR<tdS
RtdS
Rinput typeVMtextM nameVMbalanceM SR<inputS
R<tdS
R<trS
RtrS
RtdSR5S*ddress;R<5SR<tdS
RtdS
Rinput typeVMtextM nameVMaddressMSR<inputS
R<tdS
R<trS
RtrS
RtdSR5S!escription;R<5SR<tdS
RtdS
Rinput typeVMtextM
nameVMdescriptionMSR<inputS
R<tdS
R<trS
RtrS
RtdSR5STrainer;R<5SR<tdS
RtdS
Rinput typeVMtextM nameVMtrainerMSR<inputS
R<tdS
R<trS
RtrS
RtdS\nbspLR<tdS
RtdS
HH
Rinput styleVMpadding;%px %pxM valueVM6aveM
typeVMsubmitMS
R<tdS
R<trS
R<tableS
R<tdS
R<trS
R<tableS
R<tdS
R<trS
R<tableS
R<formS
R<divS
R<divS
R<bodyS
R"sp;include pageVMfooter."spMSR<"sp;includeS
R<divS
R<htmlS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page importVM"ava.sql.WM TS
RT
6tring nVrequest.get0arameterBMvalMCL
ifBn.lengthBCS>C
Z
try
Z
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMselect W from student where id
VFMNnNMFMCL
<<ps.set6tringB4,nCL
)esult6et rsVps.executeDueryBCL
out.printBMRbrSMCL
out.printBMRtable borderVF?F cellspacingV? cellpaddingV3SMCL
out.printBMRtrSRtdSR5S!R<5SR<aSR<tdSRtdSR5SNameR<5SR<tdSRtdSR5S-ourseR<
5SR<tdSRtdSR5S&obileR<5SR<tdSRtdSR5S:ather NameR<5SR<tdSRtdSR5S&other
NameR<5SR<tdSRtdSR5SDualificationR<5SR<tdSRtdSR5S!ate of
5irthR<5SR<tdSRtdSR5S!ate of
2oiningR<5SR<tdSRtdSR5S*ddressR<5SR<tdSRtdSR5S!escriptionR<5SR<tdSRtdSR5
STrainerR<5SR<tdSR<trSMCL
whileBrs.nextBCC
Z
out.printBMRtrSRtdSMNrs.get6tringB4CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB3CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB%CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB7CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB4>CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB44CNMR<tdSMCL
H9
out.printBMRtdSMNrs.get6tringB4%CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB43CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB47CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringBKCNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB4?CNMR<tdSMCL
out.printBMRtdSMNrs.get6tringB4HCNMR<tdSR<trSMCL
[
out.printBMR<tableSMCL
con.closeBCL
[
catchB,xception eC
Z
e.print6tackTraceBCL
[
[<<end of if
TS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page importVM"ava.sql.WM TS
RT
6tring nVrequest.get0arameterBMvalMCL
ifBn.lengthBCS>C
Z
try
Z
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMselect W from student where
idVFMNnNMFMCL
<<ps.set6tringB4,nCL
)esult6et rsVps.executeDueryBCL
out.printBMRbrSMCL
out.printBMRform actionVFsave4."spF nameVFmyformF idVFmyformFSMCL
out.printBMRtable cellspacingV4? cellpaddingV4?SMCL
whileBrs.nextBCC
Z
out.printBMRtrSRtdSRfont styleVFcolor;navyFSR5S6tudent
!etail;R<5SR<fontSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S!;R<5SR<tdSRtdSRinput typeVFtextF nameVFidF
valueVFMNrs.get6tringB4CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5SName;R<5SR<tdSRtdSRinput typeVFtextF nameVFnameF
valueVFMNrs.get6tringB3CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S-ourse;R<5SR<tdSRtdSRinput typeVFtextF
nameVFcourseF valueVFMNrs.get6tringB%CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S&obile;R<5SR<tdSRtdSRinput typeVFtextF
nameVFmobileF valueVFMNrs.get6tringB7CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S:atherFs Name;R<5SR<tdSRtdSRinput typeVFtextF
nameVFfathernameF valueVFMNrs.get6tringB4>CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S&otherFs Name;R<5SR<tdSRtdSRinput typeVFtextF
nameVFmothernameF valueVFMNrs.get6tringB44CNMFSR<inputSR<tdSR<trSMCL
H=
out.printBMRtrSRtdSR5SDualification;R<5SR<tdSRtdSRinput typeVFtextF
nameVFqualificationF valueVFMNrs.get6tringB4%CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S!ate of 5irth;R<5SR<tdSRtdSRinput typeVFtextF
nameVFdateofbirthF valueVFMNrs.get6tringB43CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S!ate of 2oining;R<5SR<tdSRtdSRinput typeVFtextF
nameVFdateof"oiningF valueVFMNrs.get6tringB47CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S!ate of 6ubmission;R<5SR<tdSRtdSRinput typeVFtextF
nameVFfeesubF valueVFMNrs.get6tringB?CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S0aid;R<5SR<tdSRtdSRinput typeVFtextF nameVFpaidF
valueVFMNrs.get6tringB9CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S:ee;R<5SR<tdSRtdSRinput typeVFtextF nameVFfeeF
valueVFMNrs.get6tringBHCNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S5alance;R<5SR<tdSRtdSRinput typeVFtextF
nameVFbalanceF valueVFMNrs.get6tringB=CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S*ddress;R<5SR<tdSRtdSRinput typeVFtextF
nameVFaddressF valueVFMNrs.get6tringBKCNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5S!escription;R<5SR<tdSRtdSRinput typeVFtextF
nameVFdescriptionF valueVFMNrs.get6tringB4?CNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR5STrainer;R<5SR<tdSRtdSRinput typeVFtextF
nameVFtrainerF valueVFMNrs.get6tringB4HCNMFSR<inputSR<tdSR<trSMCL
out.printBMRtrSRtdSR<tdSRtdSRinput styleVFpadding;%px %pxF valueVF,dit \
6aveF typeVFsubmitFSR<tdSR<trSMCL
out.printBMR<formSMCL
[
con.closeBCL
[
catchB,xception eC
Z
e.print6tackTraceBCL
[
[<<end of if
TS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page languageVM"avaM importVM"ava.util.WM page,ncodingVM6(E==?KE4MTS
RTU page importVM"ava.sql.WM TS
RT
6tring nVrequest.get0arameterBMvalMCL
ifBn.lengthBCS>C
Z
try
Z
-lass.forNameBMcom.mysql."dbc.!riverMCL
-onnection
conV!river&anager.get-onnectionBM"dbc;mysql;<<localhost<paymentM,MrootM,MMCL
0repared6tatement psVcon.prepare6tatementBMselect W from student where id
VFMNnNMFMCL
<<ps.set6tringB4,nCL
)esult6et rsVps.executeDueryBCL
out.printBMRbrSMCL
HK
out.printBMRtable borderVF?F cellspacingV? cellpaddingV3SMCL
whileBrs.nextBCC
Z
out.printBMRtrSRtdSR5S!R<5SR<tdSRtdSMNrs.get6tringB4CNMR<tdSR<trSMCL
out.printBMRtrSRtdSR5SNameR<5SR<tdSRtdSMNrs.get6tringB3CNMR<tdSR<trSMCL
out.printBMRtrSRtdSR5S-ourseR<5SR<tdSRtdSMNrs.get6tringB%CNMR<tdSR<trSMCL
out.printBMRtrSRtdSR5S&obileR<5SR<tdSRtdSMNrs.get6tringB7CNMR<tdSR<trSMCL
out.printBMRtrSRtdSR5S!ate of
submissionR<5SR<tdSRtdSMNrs.get6tringB?CNMR<tdSR<trSMCL
out.printBMRtrSRtdSR5STotal
:eeR<5SR<tdSRtdSMNrs.get6tringBHCNMR<tdSR<trSMCL
out.printBMRtrSRtdSR5S0aid
*mountR<5SR<tdSRtdSMNrs.get6tringB9CNMR<tdSR<trSMCL
out.printBMRtrSRtdSR5S5alanceR<5SR<tdSRtdSMNrs.get6tringB=CNMR<tdSR<trSMCL
out.printBMRa hrefVF]F nameVFMNrs.get6tringB4CNMF
onmouseoverVF"avascript;send'ennfoBthis.nameCF SRfont styleVFcolor;
navyLFSR5S'eneral nformationR<5SR<fontSR<aSMCL
[
out.printBMR<tableSMCL
con.closeBCL
[
catchB,xception eC
Z
e.print6tackTraceBCL
[
[<<end of if
TS
RT
session.invalidateBCL
TS
R"sp;forward pageVMindex."spMSR<"sp;forwardSS
9>
REFERENCE7
>OO.7)
-harles .ampfed B3>>>C ^nstant 2ava 6erver 0ages Jniversity of Toronto
.erbert 6childt B3>>>C ^2ava -omplete )eference Tata &c'raw .ill
2ohn _ukowski B3>>>C ^&astering 2ava3 505 0ublications
2amie 2aworsky ^23,, 5ible Techmedia
6tefen !enninger ^,nterprise 2ava 5eansE3.4 *uthors 0ress
an 6omerville ^6oftware engineering
)a"eev mall ^6oftware engineering
,lmasri Navathe ^:undamentals of database systems
ONLINE REFERENCE)
www."ava.sun.com
www.w%schools.com
www.wikipedia.com
94
Você também pode gostar
- Chapter Three Research and Design MethodologyDocumento25 páginasChapter Three Research and Design MethodologyVincent KorieAinda não há avaliações
- Vision of A Bitcoin Client Linux Distribution v01Documento3 páginasVision of A Bitcoin Client Linux Distribution v01michaelusAinda não há avaliações
- Introduction To BitcoinDocumento15 páginasIntroduction To BitcoinPapori BorgohainAinda não há avaliações
- Lionshare Simplified PDFDocumento8 páginasLionshare Simplified PDFHIGHLIGHT latestAinda não há avaliações
- QuestionDocumento1 páginaQuestionSimon InenejiAinda não há avaliações
- Online BankingDocumento98 páginasOnline Bankingnitish_j100% (2)
- No 1 How To Make Money OnlineDocumento12 páginasNo 1 How To Make Money Onlinejan bobekAinda não há avaliações
- BTC 2021 Form CSDocumento40 páginasBTC 2021 Form CSisty5nnt100% (1)
- Payment Billing System DocumentDocumento66 páginasPayment Billing System DocumentUsha AvinashAinda não há avaliações
- Help WebcamDocumento12 páginasHelp WebcamAshuKumarAinda não há avaliações
- Crypto Exchange FormatDocumento1 páginaCrypto Exchange Formatlachance lachanceAinda não há avaliações
- METROLAND - Billing FormatDocumento3 páginasMETROLAND - Billing FormatVer Development Corp.Ainda não há avaliações
- Online Banking - WikipediaDocumento39 páginasOnline Banking - WikipediaAjay RathodAinda não há avaliações
- Free Investment Banking TutorialsDocumento38 páginasFree Investment Banking Tutorialsmurary0% (1)
- Elite Crypto TradingDocumento2 páginasElite Crypto TradingPablo Gabrio100% (1)
- Progress BillingDocumento2 páginasProgress BillingrpillzAinda não há avaliações
- Smart Billing.....Documento110 páginasSmart Billing.....langraAinda não há avaliações
- Bitcoin InvestmentDocumento2 páginasBitcoin InvestmentMilitary BaseAinda não há avaliações
- How To Crack A Binary File FormatDocumento5 páginasHow To Crack A Binary File FormatlutfikasimAinda não há avaliações
- I'm Sorry If I'm Causing Any Inconvenience I Was Going Through SomeDocumento10 páginasI'm Sorry If I'm Causing Any Inconvenience I Was Going Through Somekelvinpleasure777Ainda não há avaliações
- Bitcoin Format: Join Tradingview On DerivDocumento1 páginaBitcoin Format: Join Tradingview On DerivPhilip TuckerAinda não há avaliações
- BTC 6Documento3 páginasBTC 6Pablo Gabrio100% (3)
- Bit Coin PDF Cryptocurrency BitcoinDocumento1 páginaBit Coin PDF Cryptocurrency BitcoinEjam ChukukaAinda não há avaliações
- Lother's ScriptDocumento4 páginasLother's Scriptyindu cameraAinda não há avaliações
- Tradecap Managed Account ServicesDocumento4 páginasTradecap Managed Account ServicesRajesh ThangarajAinda não há avaliações
- Online Tracking SystemDocumento87 páginasOnline Tracking SystemJaldeepAinda não há avaliações
- Fund Loan Form PDFDocumento3 páginasFund Loan Form PDFsarge18100% (1)
- Consignment Delivery Form ADocumento1 páginaConsignment Delivery Form ALogia GamerAinda não há avaliações
- Micro Eros Te/Tm DR List (225 Drs / Te/Tm/Bdm)Documento43 páginasMicro Eros Te/Tm DR List (225 Drs / Te/Tm/Bdm)Poornima PaiAinda não há avaliações
- Chat 2Documento35 páginasChat 2superedgarvm4974Ainda não há avaliações
- Forex Trading and Investment PDFDocumento160 páginasForex Trading and Investment PDFManop Metha100% (1)
- Real Estate 2Documento20 páginasReal Estate 2urvashiakshayAinda não há avaliações
- Investment Agreeement FormatDocumento2 páginasInvestment Agreeement Formatreynaldo sicogalAinda não há avaliações
- HOW I MAKE MONEY TO TRAVEL (TipsDocumento10 páginasHOW I MAKE MONEY TO TRAVEL (TipsShyam BambalAinda não há avaliações
- MavisDocumento26 páginasMavisTarasAinda não há avaliações
- Document 1Documento2 páginasDocument 1Paperairplane123 paper100% (1)
- Appartment ManagementdocumentDocumento58 páginasAppartment ManagementdocumentKingShankarAinda não há avaliações
- Iba Notes-Gabriel NarteyDocumento55 páginasIba Notes-Gabriel NarteyNanette Quarcoo0% (1)
- Management BillingDocumento37 páginasManagement BillingSrinivas ThatavarthyAinda não há avaliações
- Bills Buying and Selling RatesDocumento2 páginasBills Buying and Selling RatesEnamul Haque100% (1)
- Model FormatDocumento175 páginasModel Formatjain93kunalAinda não há avaliações
- How To Make Money Trading ForexDocumento13 páginasHow To Make Money Trading ForexAndra Maria100% (1)
- BillingDocumento83 páginasBillingadinoAinda não há avaliações
- Technofab Engineering Limited: Remburshment of Cell Phone ExpancesDocumento1 páginaTechnofab Engineering Limited: Remburshment of Cell Phone ExpancessatenderroseAinda não há avaliações
- WhatsApp TricksDocumento38 páginasWhatsApp TricksSales Online100% (1)
- Real Estate in SrsDocumento12 páginasReal Estate in Srsfyp 2019Ainda não há avaliações
- Bitcoin Format PDF PDF Investing Option (Finance)Documento1 páginaBitcoin Format PDF PDF Investing Option (Finance)Mark Scott50% (2)
- Chatting Format-1 PDF Anger HeavenDocumento1 páginaChatting Format-1 PDF Anger HeavenKate JayAinda não há avaliações
- Dont Pay With Itunes Gift Cards FinalDocumento1 páginaDont Pay With Itunes Gift Cards FinalJack WilliamsAinda não há avaliações
- Formats For V2V2Documento1 páginaFormats For V2V2MarkAinda não há avaliações
- EI Fund Transfer Intnl TT Form V3.0Documento1 páginaEI Fund Transfer Intnl TT Form V3.0Tosin SimeonAinda não há avaliações
- Online BankingDocumento13 páginasOnline BankingHarmanSinghAinda não há avaliações
- Change of OwnershipDocumento3 páginasChange of OwnershipsatyajoshiAinda não há avaliações
- Christmas Billing Format 1 2Documento1 páginaChristmas Billing Format 1 2Promise Segun100% (1)
- Order Taking and BillingDocumento25 páginasOrder Taking and Billingaustin vincent100% (1)
- Text FA3D5960F352 1Documento3 páginasText FA3D5960F352 1atagaaisosaAinda não há avaliações
- Purchase Order 1Documento83 páginasPurchase Order 1Parveen KumarAinda não há avaliações
- WelcomeDocumento6 páginasWelcomeParveen KumarAinda não há avaliações
- PronounsDocumento10 páginasPronounsParveen KumarAinda não há avaliações
- Assignment OF English Submitted To: Mrs. Lovely Raj: Submitted By: Nargis Class B.A. 1st Roll No:3143620067Documento8 páginasAssignment OF English Submitted To: Mrs. Lovely Raj: Submitted By: Nargis Class B.A. 1st Roll No:3143620067Parveen KumarAinda não há avaliações
- Training Report (Mukta2)Documento64 páginasTraining Report (Mukta2)Parveen KumarAinda não há avaliações
- Cost of Capital BDocumento42 páginasCost of Capital BParveen KumarAinda não há avaliações
- Financial Analysis HDFC BANK1Documento66 páginasFinancial Analysis HDFC BANK1Parveen KumarAinda não há avaliações
- Acknowledgement: Surender Kumar Mandal (6814136)Documento3 páginasAcknowledgement: Surender Kumar Mandal (6814136)Parveen KumarAinda não há avaliações
- A Practical File ON New Media: D.A.V. College For Girls Yamunananagar - 135001Documento1 páginaA Practical File ON New Media: D.A.V. College For Girls Yamunananagar - 135001Parveen KumarAinda não há avaliações
- LadderDocumento29 páginasLadderParveen KumarAinda não há avaliações
- Mca Butter Blue GoldenDocumento5 páginasMca Butter Blue GoldenParveen KumarAinda não há avaliações
- FDESHDocumento5 páginasFDESHParveen KumarAinda não há avaliações
- Research Report FinalDocumento71 páginasResearch Report FinalParveen KumarAinda não há avaliações
- Seminar Report: Haryana Engineering College, JagadhriDocumento7 páginasSeminar Report: Haryana Engineering College, JagadhriParveen KumarAinda não há avaliações
- A Knowledge MentDocumento5 páginasA Knowledge MentParveen KumarAinda não há avaliações
- Bank ReportDocumento57 páginasBank ReportParveen KumarAinda não há avaliações
- Air Hybrid Cycle Mod 3Documento27 páginasAir Hybrid Cycle Mod 3Parveen Kumar100% (1)
- Bank ReportDocumento57 páginasBank ReportParveen KumarAinda não há avaliações
- Sourav StartingDocumento4 páginasSourav StartingParveen KumarAinda não há avaliações
- Chapter-1: An Idea About The ProjectDocumento41 páginasChapter-1: An Idea About The ProjectParveen KumarAinda não há avaliações
- Recruitment & Selection Process VodafoneDocumento9 páginasRecruitment & Selection Process VodafoneParveen KumarAinda não há avaliações
- A Project Report ON: Demonstration of Air EngineDocumento1 páginaA Project Report ON: Demonstration of Air EngineParveen KumarAinda não há avaliações
- Front Pages of ProjectDocumento9 páginasFront Pages of ProjectParveen KumarAinda não há avaliações
- Segway: Bachelor of Technology in Mechanical EngineeringDocumento1 páginaSegway: Bachelor of Technology in Mechanical EngineeringParveen KumarAinda não há avaliações
- Shell and Tube Heat Exchanger: Haryana Engineering College JagadhriDocumento4 páginasShell and Tube Heat Exchanger: Haryana Engineering College JagadhriParveen KumarAinda não há avaliações
- Shell and Tube Heat Exchanger: Haryana Engineering College JagadhriDocumento4 páginasShell and Tube Heat Exchanger: Haryana Engineering College JagadhriParveen KumarAinda não há avaliações
- Wireless Energy MeterDocumento6 páginasWireless Energy MeterParveen KumarAinda não há avaliações
- SegwayDocumento21 páginasSegwayParveen KumarAinda não há avaliações
- Wind TurbineDocumento4 páginasWind TurbineParveen KumarAinda não há avaliações
- Shell and Tube Heat Exchanger: Haryana Engineering College JagadhriDocumento4 páginasShell and Tube Heat Exchanger: Haryana Engineering College JagadhriParveen KumarAinda não há avaliações
- Online Employee Health Care System-SynopsisDocumento6 páginasOnline Employee Health Care System-SynopsisNageshwar SinghAinda não há avaliações
- A K Azad 04.10.2020 ICT - IfrastructureDocumento135 páginasA K Azad 04.10.2020 ICT - Ifrastructureashraf294Ainda não há avaliações
- Aveva GCD Creator 4.1.2 Full Fix Release 53257 Windows 10, Windows Server 2012 R2, Windows Server 2016, Windows Server 2019Documento4 páginasAveva GCD Creator 4.1.2 Full Fix Release 53257 Windows 10, Windows Server 2012 R2, Windows Server 2016, Windows Server 2019Alex PAAinda não há avaliações
- The V Model 1Documento18 páginasThe V Model 1JoshuaThackerAinda não há avaliações
- System Analysis and DesignDocumento410 páginasSystem Analysis and Designerangirifad92% (13)
- The Database Environment and Development ProcessDocumento55 páginasThe Database Environment and Development Processاسامه العبسيAinda não há avaliações
- Electronic Government - Concepts, Tools, Methodologies, and Applications - Introductory ChapterDocumento35 páginasElectronic Government - Concepts, Tools, Methodologies, and Applications - Introductory ChapterСтаменић МаринаAinda não há avaliações
- CAIS 04 Carey Etal HCI in Is CurriculaDocumento24 páginasCAIS 04 Carey Etal HCI in Is CurriculaPako MogotsiAinda não há avaliações
- ForresterWave RPTDocumento12 páginasForresterWave RPTjunohcu310Ainda não há avaliações
- Chapter 12 - Information Systems DevelopmentDocumento27 páginasChapter 12 - Information Systems DevelopmentSelena ReidAinda não há avaliações
- Bhargavi: SummaryDocumento5 páginasBhargavi: SummaryxovoAinda não há avaliações
- Systems Analysis and Design by Dennis AllanDocumento4 páginasSystems Analysis and Design by Dennis AllanGrace Ann Aceveda Quinio100% (1)
- Director Project Portfolio Management in Sacramento CA Resume Carl ReedDocumento2 páginasDirector Project Portfolio Management in Sacramento CA Resume Carl ReedCarlReed2Ainda não há avaliações
- Seven Pragmatic Practices To Improve Software QualityDocumento10 páginasSeven Pragmatic Practices To Improve Software QualityZeeshan Ahmed KhanAinda não há avaliações
- No. CLO PLO (Code) Taxonomies and Generic Skills T&L Methods Assessment MethodsDocumento2 páginasNo. CLO PLO (Code) Taxonomies and Generic Skills T&L Methods Assessment MethodsError 404Ainda não há avaliações
- Novel Approach To Evaluate Student Performance Using Data MiningDocumento31 páginasNovel Approach To Evaluate Student Performance Using Data MiningRahul KanojiaAinda não há avaliações
- Classical Waterfall ModalDocumento6 páginasClassical Waterfall Modalsatyam patidarAinda não há avaliações
- Position of Responsibility: Bindu Chandra Shekhar MishraDocumento2 páginasPosition of Responsibility: Bindu Chandra Shekhar Mishraankit mohanAinda não há avaliações
- CPDSDocumento319 páginasCPDSrupakothurAinda não há avaliações
- Arvind - Resume Updated (F)Documento4 páginasArvind - Resume Updated (F)Pradip ShawAinda não há avaliações
- SQA - QuizDocumento8 páginasSQA - Quiztazeem khanAinda não há avaliações
- SDLCDocumento31 páginasSDLCBikash KandelAinda não há avaliações
- 008 - FISE Report FormatDocumento4 páginas008 - FISE Report FormatSarmila MahendranAinda não há avaliações
- 2nd Year FLPDocumento3 páginas2nd Year FLPLaraib ZafarAinda não há avaliações
- Compute Value of e To N Number PROJECTDocumento14 páginasCompute Value of e To N Number PROJECTKapil SidhpuriaAinda não há avaliações
- CCI-RFID Student Monitoring System With Web AppsDocumento39 páginasCCI-RFID Student Monitoring System With Web AppsSarmiento B. Fred100% (1)
- FSD Unit 1 16072016 071724AMDocumento15 páginasFSD Unit 1 16072016 071724AMShrujal TailorAinda não há avaliações
- Pattys Delivery SystemDocumento13 páginasPattys Delivery Systemmark elmer LisondraAinda não há avaliações
- Project SampleDocumento63 páginasProject SampleNilesh SatoseAinda não há avaliações
- Final Year Project Report Community Policing Mobile ApplicationDocumento57 páginasFinal Year Project Report Community Policing Mobile ApplicationOyo Wilfred RobertAinda não há avaliações