Escolar Documentos
Profissional Documentos
Cultura Documentos
01672698
Enviado por
hariharankalyanDireitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
01672698
Enviado por
hariharankalyanDireitos autorais:
Formatos disponíveis
983
CORRESPONDENCE
[6] Y. T. Chien and K. S. Fu, "On Bayesian learning and stochastic
approximation," IEEE Trans. Syst., Sci., Cybern., vol. SSC-3, pp. 2538, June 1967.
171 T. Y. Young and G. Coraluppi, "Stochastic estimation of a mixture of
normal density functions using an information criterion," IEEE
Trans. Inform. Theorv, vol. IT-16, pp. 258-263, May 1970.
On Generating a Line "Parallel" to a
Digital Line-A Sequential Approach
ASHOK K. AGRAWALA
Abstract-This correspondence describes a sequential algorithm
which generates the chain coded description of a line "parallel" to
and at a fixed distance from another digital line. A few examples are
presented along with a comparison with a parallel approach.
Index Terms-Chain coding, image processing, line drawings,
parallel line algorithms.
I. INTRODUCTION
In a number of applications using line drawings, the need arises
for generating a digital line which is a fixed distance r away from
another digital line. For example, in cartography, a two line description of a road or a railroad may have to be generated from the
center line information; in mechanical drawings the thickness of a
part shown by a single line may have to be shown by having a second
line next to it.
A rich literature exists on digital handling and manipulation of
line drawings [1], [2]. However, it is interesting to note that despite
its importance and usefulness to digital processing of line drawings,
no direct solution to the problem of drawing a line parallel to a
digital line has been presented in the literature [3}-[5].
A quick analysis of the problem shows that a case for which this
problem has a trivial solution is when the original line A is a continuous straight line or a digital line along one of 8 principal directions
for a rectangular digitization grid. In both of these cases, the parallel
line is obtained by a simple translation. In most other cases of a
continuous or digital line, the solution is nontrivial.
Before proceeding any further, let us define what we mean by a
line "parallel" to an arbitrary,line. Let d(Bi,A,) be the distance
between two points B1 and As. Considering the line A as a set of
points {A,] let
d(Bi,A)
(1)
min Id(Bi,Ai) Ai E AI.
Then we define line B to be parallel to line A at a distance r from
it if the distance between any point on B to the point set A is exactly
r, i.e.,
=
functional form of the line A. As can be seen from a few examples
shown in Fig. 1, line B can be very complex. Usually it is a single
closed curve. But it may also consist of a few unconnected closed
curves.
Conceptually such a line can be obtained by moving the center of a
circle of radius r along the line A and generating the line B as the
boundary of the union of all these circular regions. This correpondence describes an algorithm based on this idea, which can be
used to generate a digital line B around a digital line A. The simple
procedures of this algorithm are not affected by the complexity of
the line A or the number of closed curve segments line B may have.
An approach to solving this problem could be to use a computationally parallel approach of propagation [1 ] followed by edge detection. The prppagation process can be carried out by filling in 4 or 8
neighbors of a point. By repeating the propagation step a few times
a square or an octagonal dark region may be obtained around each
point. Drawing a parallel line requires detecting the edge points
of this dark region by examining the neighbors of each point. The
parallel line is then obtained by following this edge to get a chain
code description and the connectivity of the line. This approach
can be implemented easily in a language like PAX [6].
While conceptually simple and intuitively appealing, the computationally parallel approach suffers from certain disadvantages.
To carry out the propagation in the parallel approach on a sequential machine, for each point in the two-dimensional array whether
the point is on the line or not, the number of operations required
is proportional to wr'. Then the edge detection has to be performed by
examining all the points in the array and some of their neighbors.
And, finally, the edge following may be nontrivial for complex
examples of parallel lines having segments. To assure that all the
segments were picked up one may have to examine the whole array
once more.
The algorithm presented here calls for examining only yr points
for each point of the line (and not the whole array) and directly
results in a chain coded description of the parallel line maintaining
its connectivity.
The general framework for the discussion here is presented in
Section II. Section III presents the algorithm. Some examples are
presented in Section IV and possible extensions are discussed in
Section V.
II. DESCRIPTION OF A DIGITIZED LINE
Let us consider the digitized version of a line A [2] as consisting
of the starting point Ao and a sequence of chain codes {fail, i =
1,2,... where ai may take values between 0 and 7 and is used to
specify the increment direction from point Ai-, to Ai. The directions
corresponding to the value of ai are illustrated in Fig. 2.
Note that we are treating the line as a directed line. Any point
Ai on this line is specified by its (X,Y) coordinate. To indicate
the connectivity, we should also specify the chain codes or links
required to go from Ai to Ai+, and Ai-,. We shall call these links
forward and back links. The forward link for At is ai+1 while its back
link is in the reverse direction of ai, which may be computed as
+ 4) mod 8.
Bi I d(Bi,A) = r}.
(2) (aiGiven
the description of the line as Ao and {fai, starting from Ao
If A and B are digital lines, the requirement of exact distance r we can easily traverse or follow the line in the forward direction.
has to be relaxed to allow the points of line B to fall on grid points. Back links are required to be able to traverse the line in the backward
Mathematically we may define line B to be the locus of points direction.
The operation of the algorithm requires the capability of examining
satisfying the definition above. In most cases, it is not easy to come
B=
up with the functional form of such
locus
even
if
we
know the
Manuscript received August 13, 1974; revised December 16, 1974.
This work was supported in part by the L.N.K. Corporation, Silver
Spring, Md.
The author is with the Department of Computer Science, University of
Maryland, College Park, Md.
20742.
any (X,Y) point to check if any lines pass through it. This may be
done by storing the line information in a two-dimensional index
array. The index array contains 3 entries for each of the two-dimensional digitization grid being considered. These entries are the line
number and the forward and back link. As only a few bits are required for each of these entries they can be coded easily in a single
word of memory. Note that a code is required to indicate that no
984
IEEE TRANSACTIONS ON COMPUTERS, OCTOBER
1975
Fig. 1. Examples of "parallel" lines.
6
Fig. 2.
Chain code directions.
C(i)
f'
C2
Fig. 3. A step of the algorithm.
line passes through a point. If a line is passing through some point,
the adjacent point on the line in forward or back direction can be
found by taking a step in the direction of forward or back link. Thus,
from this data structure any line stored in the index array can be
traversed in forward or reverse direction from any point of the line.
In the discussion here, we shall use the capital letters for lines or
curves. A capital letter with a suffix will be used to denote a point
on that line. Therefore Ai is the ith point of line A. Lower case letters
with or without suffixes will be used for the chain codes or links from
the corresponding point. As discussed above aif = ai+ and aib =
(ai + 4) mod 8. If a line changes at each step of processing, at the jth
step it will be identified as A (j).
III. THE ALGORITHM
The basic idea of this algorithm can be explained in terms of
Fig. 3 which shows a line A which has been examined up to its point
Ai-,. The corresponding parallel curve is B (i - 1). At the ith stage
the new point on the line A is Ai. With Ai as the center we draw a
circle C (i) of radius r which intersects B (i - 1) at points C( and Cs.
The new curve B (i) can now be obtained by deleting the portion
C(B1Cg of B (i - 1) and replacing it by C1C2C3. In other words,
we delete that portion of B (i - 1) which lies inside C(i) and replace it by that portion of C(i) which lies outside B (i - 1). Note
that if a portion of B (i - 1) lies inside C(i) and the corresponding
portion of C(i) lies inside B (i - 1) then the inside portion of
B(i - 1) is deleted and is not replaced by any portion of C(i).
This can occur when the line A intersects with itself or two points
on line A have a geometric distance of less than 2r while their
distance along the line is more than 7rr. A curve having more than 1
unconnected segment results in such cases.
The chain code description of lines allows one to easily replace
a portion of a line between two points by another line between
those points by appropriately changing the forward and back links
at the end locations in the index array or by actually replacing the
chain codes in the sequence. Further, as we are treating lines as
directed lines the detection of the inside/outside relationship is
straightforward. This can be done simply by going around the circle
C(i) from a point which is inside B (i - 1) and then detecting intersections. One such point is Co (i) which is on C(i) in the direction
aib, the back link at Ai. As Ai-, lies on the line joining Co(i) and
Ai,Co is less than r away from Ai-, and hence is inside B (i - 1).
In an actual implementation a number of additional complications
arise due to the geometry of C (i) and B (i - 1). While we only need
to go around C (i) once, at each point we need to know whether it is
inside or outside B (i - 1). For this purpose we use a flag PUTFLAG
which has a value 0 when C(i) is inside B(i - 1) and a value 1
when it is outside. We begin traversing C(i) from the point Co
which we know is inside and hence we may set PUTFLAG to zero.
The basic philosophy of this algorithm is to examine the points
on circle C (i) starting from Co. All points of C (i) for which PUTFLAG
is 1 are entered as a part of B (i) in the index array, i.e., an entry
is made at that point for B(i) having the forward and back links
specified by the corresponding links of C (i).
In Fig. 3, the intersections of line B (i - 1) and C (i) are shown
as very clearly marked. In practice, for digitized curves a number of
situations may arise at the intersection points. The action to be
taken under various conditions is shown in Table I. The action
985
CORRESPONDENCE
TABLE I
Initial
PUTFLAG
Intersect
with
B(i - 1)
O
O
O
O
O
O
O
1
1
1
1
1
1
1
No
Yes
Yes
Yes
Yes
Yes
Yes
No
Yes
Yes
Yes
Yes
Yes
Yes
Location
of bf
wrt C(i)
Location
of bb
wrt C(i)
along cf
inside
inside
along cb
along cb
along cb
outside
along cf
outside
along cf
inside
outside
along cf
along cf
isinde
outside
outside
outside
inside
along cb
along cb
along cf
inside
along cb
Make an
entry
in B(i)
No
Yes
No
Yes
No
No
Yes
Yes
Yes
Yes
Yes
Yes
Yes
Yes
Forward
Back
New
Link for Link for Deletion
PUTFLAG B(i) entry B(i) entry Pointer
0
1
0
1
0
0
1
1
1
1
1
0
0
0
cf
ef
bb
cf
cf
cf
cf
cf
bf
bf
bf
bb
cb
cb
cb
cb
cb
eb
cb
bb
bf
bf
bb
bb
bf
bb
.x
Fig. 4. Lines not intersecting at grid point.
depends on the direction of B (i - 1) with respect to C (i) at the at the end because the curve B (i) is always a complete curve for
point of intersection. In this table cf and cb represent the forward and the portion of A considered that far.
If this algorithm is implemented as discussed above 2irr points
back links of C(i) at that point. The actions to be taken depend on
the value of PUTFLAG and the location of bf and bb, the forward and have to be examined for every point on line A. This number may be
back links of the line B (i - 1) relative to C(i), at that point. The reduced to half by examining only those points of C(i) which lie
actions consist of adjusting the value of PuTFLAG, deciding to make on or outside C(i - 1).
an entry for B(i) with specified values of the links and marking
IV. EXAMPLES
some points of B (i - 1) for deletion.
As noted above, those portions of B (i - 1) which lie inside C(i)
A number of examples of this algorithm are presented in Figs.
have to be deleted. This can be accomplished by marking the points
5,
6, and 7. The original line A is shown in Figs. 5 (a), 6 (a), and 7 (a).
of B (i - 1) which are just inside C (i). The last column of the Table
I indicates the link to be used from the point under consideration A line B parallel to the line A at a distance of 5 was generated fot
to go to the point to be marked for deletion. A blank entry indicates each example and the final results are shown in Figs. 5 (b), 6 (b), and
7(b). The operation of this algorithm is further illustrated in the
that no point is to be marked.
As illustrated in Fig. 4, in a rectangular grid system, two lines output of intermediate processing for the example of Fig. 5 in Fig.
may intersect at a nongrid point. If we only examine points along the 5(c)-(f), and for the example of Fig. 6 in Figs. 6(c)-(g).
circle C (i), then we may miss the occurrence of such intersections
V. CONCLUDING REMARKS
which can be easily detected by testing for an intersection when the
cf has an odd value. We may test the point at (cf + 1) mod 8 from
While the discussion above assumed the curve C to be a circle,
Ct to check if B passes through there and has a forward or back any closed curve specified by a chain code sequence can be used
link which is perpendicular to cf pointing outside, i.e., is equal to with equal ease. The type of parallel curve we get will depend on the
(cf - 2)mod 8. When this occurs, the point of line B is marked for shape of the curve used. For example, rectangles will avoid the
deletion, and the value of PUTFLAG is changed from 0 to 1 or from 1 roundoff at sharp corners but will elongate more along one direction
to 0. An entry for the point under consideration is made only if compared to its perpendicular direction. The propagation approach
PUTFLAG was originally 1. The forward and back links are adjusted mentioned in the introduction does not allow the use of any arbitrary
to maintain the connectivity of B(i) by entering the forward link curve and is better suited for square or octagons as curve C.
as (cf - l)mod s and back link as cb. If PUTFLAG WaS originally zero,
The algorithm presented here used a fixed circle as the curve
no entry is made but the links are adjusted to maintain the connec- which was moved along the line A. Depending on the application,
tivity when the next point is entered. At that stage, the value we may modify the curved based on some parameters of the system.
PUTFLAG iS one.
For example, a different curve may be used for each value of aif.
The actions of Table I have to be considered for every point on
The simplicity of this algorithm makes it suitable as a primitive
C(i) starting from Co until we return to Co. At that time B(i) has step to carry out complex processing of lines. For example, the
been generated. Some old values of B(i - 1), which represent its crowding conditions near a line could be detected by finding how
arcs found to be inside C (i), may still have to be deleted. Both ends many other lines are- inside of B.
of these arcs are marked and therefore the deletion can be accomplished simply by tracing from one marked point to the other for
ACKNOWLEDGMENT
each arc.
I am grateful to Prof. A. Rosenfeld for his comments on the
The initiation of this algorithm requires that B (0) be set as C (0),
a circle with center at Ao and radius r. No special action is required manuscript and for pointing out how the parallel approach could be
986
IEEE TRANSACTIONS ON COMPUTERS, OCTOBER
B
B
B
AAAAAAAAAAA
AI
A
B
B
B
B
Ba
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
B
B
B
B
B
B
B
B
B
B
B
A
BBBBBBBBBBBBBBB
BBBBBBB
BEIBBB
BB
BB
B
B
B
B
B
B
B
B
B
B
B
A
A
A
A
A
A
A
A
A
A
A
B
B
B
B
B
B
B
B
B
B
B
B
B
B
B
B
B
B
B
B
B
BBBBB
BB
B
8BBBBS
BBBBBBBBBBBBBBB
AA
BB
B
A
AAAAAAAAAAA
B
B
AA
AAAAAAAAAAA
B
B
B
A
B
B
B
B
B
B
B
B
a
B
B
B
B
B
a
B
B
BBBBBBBBBBBBBBB
BB
B
(c)
(b)
A
A
A
A
A
A
A
A
A
A
A
B
B
B
B
B
BBBBB
BBBBB
AAAAAAAAAAA
B
B
BB
(a6)
BB
a
B
B
B
B
B
1975
BB
B
B
B
B
B
B
BBBBB
BBBBB
E3BBBB
(d)
(e)
Fig. 5.
BBBB8
B3
(f)
(a) The original line consisting of 51 points. (b) The final result
of the algorithm where
line B is drawn at
distance 5 from the line A.
(c)- (f ) Intermediate results after the algorithm has processed 11, 21, 31,
and 41 points of the line A, respectively.
B
B
-B
B8
BAAa
BBBBBBB
A'
Ba
A
B
BBBBBB8BBBB
987
CORRESPONDENCE
BBBBBBBBBBBBBBBBBBBB
BBBBB
AAAAAAAAAAAAAAANA
A
A
A
A
A
AA
AA
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
3B
A
A
AAAAAAAAAAAAAAAA
BBBBBBBBBBBBBBBBBBBB
BBBBBBBBBBBBBBBBB
3
B
B
a BBBBBBBBBBB
BB
BBBBB
3
a
A
A
A
B
B
B
B
B
A
A
BBBa BBBBBBBBBBBBBB
B
B
8
B
B
B
B
B
B
B
B
B
B
B
B
B
B
a
a
B
a
B
B8BBB
B
B
B
B
BBBBB
B
B
B
B
d
B
B
Fig. 6.
B
B
B
B
3
B
3
B
B
13
B
B
A
A
A
A
B
B
B
B
B
B
B
B
A
A
A
A
A
A
A
A
A
A
B
a
BBBB3
(a) The original line A consisting of 79 points. The line intersects
itself at a nongrid point. (b) The final result of the algorithm where a
line B is drawn at a distance 5 from the line A. Line B consists of two
unconnected segments. (c) An intermediate output after the algorithm
has processed 50 points of line A. Line B has only one- segment. (d)
Lines A and B after 63 points of line A. Line B still has only one segment.
(e) Lines A and B after 65 points of line A. Line B is broken into two
segments now. (f) Lines A and B after 70 points of line A. (g) Lines
A and B after 74 points of line A which is just about to intersect itself.
BB3BBB
B
3
38
3
3
B
AAAAAAAAAAAAAAAA
(d)
(e)
B
B
3
B
B
a
BBBBBBBBBBBBBBBBBBBB
B
B
BB339BBBBBBR3B3aBBBB
_3BB
B
B
B
B
B
BB3BB
A
A
A
3BBBBBBBBBBBB5
A
A
A
A
AAAAAAAAAAAAAAAA
BB
B B
B
B
AAAAAAAAAAAAAAAA
A
A
A
A
A
A
A
A
A
BBRBBB
A
a
8
B
(c)
8
8
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
A
BBBBBB
B
B
B
B
B
BBBBBBBBBBBBBBBBBBBB
B
B
AAAAAAAAAAAAAA
A
A
B B
B
B
B
B
B
B
AAAAAAAAAAAAAAAA
A
A
B
A
A
A
3
A
A
73
A
A
3
A
3BBBBB
a
A
B
B
A
B
A
B
B
A
a
A
B
A
B
A
B
A
B
A
A
A
A
A
(b)
(a)
AAAAAAAAAAAAAAAA
a
B
B
B
B
B
B
a a
BBBBB
A
A
A
AAAAAAAAAAAAAAAA
A
A
A
B
B
A
B
A
A
B
A
A
A
B
A
A
BBBBBB
A
3
B
A
A
B
A
B
A
A
B
A
a
3
A A
B
A
B
AA
B
A
B
AA
B
A
B
A
B
A
B
B
A
L
B
A
A
B
A
a
B
A
A
B
A
3
A
A
BBBBBB
A
A
A
A
B
A
A
A
B
A
a
3B
A
A
3
B B
AAAAAAAAAAAAAAAA
3
BB3BBBB9BBBBBBBBBBBB
B
B
BB9BBB
B
B
a
B
A
A
A
A
A
A
A
A
B
B
B
B
3
A
A
A
A
A
A
A
A
B
B
B
B
B
AAAAAAAAAAAAAAAA
B
B
BB
B
B
BBBBBBBBBBBB3BBBBBBB
(f)
Li
988
IEEE TRANSACTIONS ON COMPUTERS, OCTOBER 1975
B3
B3
E3
E3
E3
B BBBBBBBBBBB BBBBBB
Li
B
B
B
B
B
B
A
AA
A
A
A
A
A
A
BBBBBB
B
B
a
B
3
B
B
B
B
B
B
B
B
B
B
BBBBBB
A
A
A
A
A
A
A
A
A
A
A
A
A
A
AAAAAAAAAAAAAAAA
3B
8 B
BBBBB B
B
BBBBBBBBBBBBBBBBBB
(g)
Fig. 6.
B
B
3
8
B
3
B
B
B
B
B
B
B
B
B
B
B
B
B
AAAAAAAAAAAAAAAA
A
A
A
A
A
A
A
A
A
A
A A
AA
A
A
A
A
A
A
A
%AAAAAAAAAAAAAAAA
A
A
A
A
AAAAAAAAAAAAAAAA
B
B
B
A
A
A
AA
A A
A
A
A
A
(a)
Continued.
BH868
implemented easily using the language PAx. I would also like to
thank Prof. L. N. Kanal for his continued interest and interaction
during this work.
I)
B
A
AROBBB BBBBAA
BBBBB8a
R
8
AAAAAAAAAAAAAAAA
REFERENCES
[1] A. Rosenfeld, Picture Processing by Computer. New York: Academic,
1969.
A
A
AA
[21 H. Freeman, "Boundary encoding and processing," in Picture Proc.
AA
BU
essing and Psychopictorics, B. S. Lipkin and A. Rosenfeld, Eds. New
York: Academic, 1970, pp. 241-266.
[31 A. Rosenfeld and A. C. Kak, "Digital picture processing: A guide to
the literature," Univ. Maryland, College Park, Computer Science
Center Tech. Rep., Sept. 1973.
141 A. Rosenfeld, "Picture processing: 1972," Comput. Graphics, Image
Processing, vol. 1, pp. 394-416, 1972.
[51 -, "Progress in picture processing 1969-71," Comput. Surveys, vol.
5, pp. 81-108, 1973.
[61 E. G. Johnston, "The PAX II picture processing system," in Picture
Processing and Psychopictorics, B. S. Lipkin, and A. Rosenfeld, Eds.
New York: Academic, 1970, pp. 427-512.
BS
a
B
A
A
B
B
a
H
B
BBBBBA
A
A
A
A
A
AA
A A
AAAAAAAAAAAAAAAA
B
B
Ba
B
B
Bf
d3
B
B
B
*S
A
B
A
A
B3
a
A Note
-B
BOBSBBBABBa
BAB
B BR R
(b)
(a) The original line A consisting of 80 points. The line does not
intersect itself. (b) The flnal result of the algorithm where a line B
is drawn at a distance 5 from the line A. Line B consists of two unconnected segments even though the line A does not intersect itself.
Automatic Detection of
Texture Gradients
on
Fig. 7.
AZRIEL ROSENFELD
Abstract-The rate and direction of maximum change of texture
coarseness across a surface are important cues to the orientation
of the surface relative to the observer. This note describes a simple
method of automatically detecting these "texture gradients."
Index Terms-Image processing, picture processing,
sis, texture analysis, texture gradients.
scene
analy-
Manuscript received September 9, 1974; revised December 20, 1974.
This work was supported by the Division of Computer Research, National Science Foundation, under Grant GJ-32258X.
The author is with the Computer Science Center, University of Maryland, College Park, Md, 20742.
It was pointed out by Gibson 25 years ago [3] that the "texture
gradient" of a surface is an important cue in determining the
orientation of the surface relative to the observer's line of sight. By
"texture gradient" is here meant the rate and direction of maximum
change of texture coarseness across the surface.
About 15 years ago, Carel et al. [2] proposed a method of automatically detecting gradients, based on counting the numbers of times
edges are crossed by line scans in various directions. More recently,
Bajcsy and Lieberman [1] have described a texture gradient detection scheme, based on analyzing the Fourier power spectra of pieces
of the surface, determining a characteristic "element size" for each
piece, and looking for trends in these characteristic sizes as one moves
across the surface.
A simple space-domain method of texture gradient detection was
Você também pode gostar
- 10 - Chapter 3 Security in M CommerceDocumento39 páginas10 - Chapter 3 Security in M CommercehariharankalyanAinda não há avaliações
- Finite Length Discrete Fourier TransformDocumento23 páginasFinite Length Discrete Fourier TransformhariharankalyanAinda não há avaliações
- 2 Marks Questions & Answers: Cs-73 Digital Signal Processing Iv Year / Vii Semester CseDocumento18 páginas2 Marks Questions & Answers: Cs-73 Digital Signal Processing Iv Year / Vii Semester CsehariharankalyanAinda não há avaliações
- RarDocumento42 páginasRarntc7035Ainda não há avaliações
- Blooms Taxonomy Action VerbsDocumento1 páginaBlooms Taxonomy Action VerbsAmorBabe Tabasa-PescaderoAinda não há avaliações
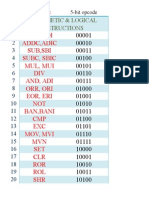
- Add, Adi Addc, Adic Sub, Sbi Subc, Sbic Mul, Mui DIV And, Adi Orr, Ori Eor, Eri NOT Ban, Bani CMP EXC Mov, Mvi MVN SET CLR ROR ROL SHRDocumento2 páginasAdd, Adi Addc, Adic Sub, Sbi Subc, Sbic Mul, Mui DIV And, Adi Orr, Ori Eor, Eri NOT Ban, Bani CMP EXC Mov, Mvi MVN SET CLR ROR ROL SHRhariharankalyanAinda não há avaliações
- How Does FPGA Work: OutlineDocumento17 páginasHow Does FPGA Work: OutlinehariharankalyanAinda não há avaliações
- Assignment1 SolutionsDocumento15 páginasAssignment1 SolutionshariharankalyanAinda não há avaliações
- The Yellow House: A Memoir (2019 National Book Award Winner)No EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Nota: 4 de 5 estrelas4/5 (98)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNo EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNota: 4 de 5 estrelas4/5 (5795)
- Never Split the Difference: Negotiating As If Your Life Depended On ItNo EverandNever Split the Difference: Negotiating As If Your Life Depended On ItNota: 4.5 de 5 estrelas4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNo EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNota: 4 de 5 estrelas4/5 (895)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNo EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNota: 4.5 de 5 estrelas4.5/5 (345)
- The Little Book of Hygge: Danish Secrets to Happy LivingNo EverandThe Little Book of Hygge: Danish Secrets to Happy LivingNota: 3.5 de 5 estrelas3.5/5 (400)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNo EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNota: 4.5 de 5 estrelas4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNo EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNota: 3.5 de 5 estrelas3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerNo EverandThe Emperor of All Maladies: A Biography of CancerNota: 4.5 de 5 estrelas4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNo EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNota: 4.5 de 5 estrelas4.5/5 (266)
- The Unwinding: An Inner History of the New AmericaNo EverandThe Unwinding: An Inner History of the New AmericaNota: 4 de 5 estrelas4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnNo EverandTeam of Rivals: The Political Genius of Abraham LincolnNota: 4.5 de 5 estrelas4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyNo EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyNota: 3.5 de 5 estrelas3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNo EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNota: 4 de 5 estrelas4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)No EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Nota: 4.5 de 5 estrelas4.5/5 (121)
- Zarah & Pharez: "Birth Marks"Documento16 páginasZarah & Pharez: "Birth Marks"Enrique RamosAinda não há avaliações
- No BullshitDocumento108 páginasNo BullshitVoodoo DollAinda não há avaliações
- Exercise 1 - MatchingDocumento2 páginasExercise 1 - MatchingLisa Rusli Dewi0% (1)
- Legal Method - NehaDocumento23 páginasLegal Method - NehaNeha PanchpalAinda não há avaliações
- Terapia Sistemica de Familia.Documento15 páginasTerapia Sistemica de Familia.Oscar GonzalezAinda não há avaliações
- Realism in English LiteratureDocumento7 páginasRealism in English LiteratureShahid AzadAinda não há avaliações
- Summary and ParaphraseDocumento2 páginasSummary and ParaphraseRaja KumarAinda não há avaliações
- Final Report (Innovation Product)Documento28 páginasFinal Report (Innovation Product)Siti Sarah100% (1)
- Servant Leadership QuestionnaireDocumento3 páginasServant Leadership QuestionnairedeepikaAinda não há avaliações
- Behaviour Management: By:Ms. Ruqaiyya Fazaia Degree College, Faisal Secondary SectionDocumento39 páginasBehaviour Management: By:Ms. Ruqaiyya Fazaia Degree College, Faisal Secondary SectionProlific YouAinda não há avaliações
- What Is A WorkshopDocumento23 páginasWhat Is A Workshoparbion7Ainda não há avaliações
- Math Grade 1 TG Q1 and Q2Documento169 páginasMath Grade 1 TG Q1 and Q2Sheryl Balualua Mape-SalvatierraAinda não há avaliações
- Ie 256 P 3Documento54 páginasIe 256 P 3khawarayubAinda não há avaliações
- Development Stages in Middle and Late AdDocumento76 páginasDevelopment Stages in Middle and Late AdGelli Ann RepolloAinda não há avaliações
- B.V. Raman - Prasna Marga-1 PDFDocumento276 páginasB.V. Raman - Prasna Marga-1 PDFpkapur84100% (1)
- Bba Syllabus Apsu RewaDocumento42 páginasBba Syllabus Apsu Rewadev2885Ainda não há avaliações
- Outline ECON201 GeneralDocumento2 páginasOutline ECON201 GeneralDavidMachelAinda não há avaliações
- MGN-231report FileDocumento7 páginasMGN-231report FileRohit KumarAinda não há avaliações
- The Judgment That Saves (Mt. 25.31-46)Documento9 páginasThe Judgment That Saves (Mt. 25.31-46)Paul BurkhartAinda não há avaliações
- NewDocumento709 páginasNewAnderson LuisAinda não há avaliações
- Educational TechnologyDocumento8 páginasEducational TechnologyMa Noemie PatayonAinda não há avaliações
- What Are Academic DisciplinesDocumento59 páginasWhat Are Academic DisciplinesJohn Michael ArtangoAinda não há avaliações
- IMC Notes - 1Documento75 páginasIMC Notes - 1Aayush Sinha100% (1)
- Ibl Presentation LinuxtegarDocumento7 páginasIbl Presentation LinuxtegarJoey De CelioAinda não há avaliações
- Consulting ProposalDocumento8 páginasConsulting ProposalShubhi KhannaAinda não há avaliações
- A Book of SecretsDocumento311 páginasA Book of Secretsfrankie5791% (11)
- The Africas of Pancho Guedes: An African CollectionDocumento5 páginasThe Africas of Pancho Guedes: An African CollectionAlexandre PomarAinda não há avaliações
- Holle Lesson PlanningDocumento17 páginasHolle Lesson PlanningFlavia Uliana LimaAinda não há avaliações
- Preparing For Interviews at The WBGDocumento3 páginasPreparing For Interviews at The WBGkadekpramithaAinda não há avaliações
- Doctrine of Basic StructureDocumento25 páginasDoctrine of Basic StructureHimanshu RajaAinda não há avaliações