Escolar Documentos
Profissional Documentos
Cultura Documentos
My Seminar Project Report 2nd
Enviado por
Abhilash HegdeDireitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
My Seminar Project Report 2nd
Enviado por
Abhilash HegdeDireitos autorais:
Formatos disponíveis
VISVESHWARAIAH TECHNOLOGICAL UNIVERSITY
BELGAUM
A SEMINAR REPORT
on
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
Submitted in partial fulfillment of the requirement for the degree of
BACHELOR IN ENGINEERING
in
ELECTRONICS AND COMMUNICATION DEPARTMENT
by
PUNITH KUMAR C T
[1RN12EC114]
2016
R.N.S INSTITUTE OF TECHNOLOGY
Channasandra, Bangalore 560098
DATE: 29th MARCH 2016
EVALUATED BY:
(Signature)
Asst.Prof. Kalpana M
(Signature)
Asst.Prof. Saraswathi Joshi
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
ABSTRACT
In response to the emerging deployment of IPv6 on network devices, this paper proposes the
integration of IPv6 on Lock-Keeper, an implementation of a high level security system for
preventing online attacks. It is designed to permit the secure data exchange over physically
separated networks in an IPv4-based environment. A new intercommunication module is
added to manage IPv4/IPv6 handoff inside the Lock- Keeper, which provides several
benefits.
First, the Lock-Keeper gains the flexibility to work in IPv4/IPv6 environments. Second, an
application layer gateway to bridge IPv4 and IPv6 networks is achieved. Third, the IP-layer
protocol isolation is realized inside the Lock-Keeper to enhance the security of the protected
network by exchanging data between physically separated networks using different IP
protocols.
IPv6 is extremely popular with companies, organizations and Internet service providers (ISP)
due to the limitations of IPv4. In order to prevent an abrupt change from IPv4 to IPv6, three
mechanisms will be used to provide a smooth transition from IPv4 to IPv6 with minimum
effect on the network. These mechanisms are Dual-Stack, Tunnel and Translation. This
research will shed the light on IPv4 and IPv6 and assess the automatic and manual transition
strategies of the IPv6 by comparing their performances in order to show how the transition
strategy affects network behaviour.
The motivation for this method is to allow isolated IPv6 hosts, located on a physical link
which has no directly connected IPv6 router, to become fully functional IPv6 hosts by using
an IPv4 domain that supports IPv4 multicast as their virtual local link. It uses IPv4 multicast
as a "virtual Ethernet".
VIII SEM ,B.E [ECE] ,RNSIT
Page | 2
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
TABLE OF CONTENTS
1. INTRODUCTION.4
1.1 IPV4 ......5
1.2 IPV6...6
1.3 LOCK-KEEPER....8
1.4 LOCK-KEEPER ARCHITECHTURE10
2. TRANSITION STRATEGIES
2.1 DUAL STACK.....11
2.2 TUNNELING...12
2.3 TRANSLATION..13
2.4 PROTOCOL ISOLATION FOR SECURITY......14
3. IPV4/IPV6 HANDOFF INSIDE THE LOCK-KEEPER......15
3.1 IP CONFIGURATION ON LOCK-KEEPER..16
4. RESULT AND CONCLUSIONS
4.1 EXPERIMENTAL RESULT....18
4.2 CONCLUSION.19
5. REFERENCES..20
VIII SEM ,B.E [ECE] ,RNSIT
Page | 3
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
LIST OF FIGURES
1.1
1.2
1.3
1.4
1.5
2.1
2.2
2.3
2.4
3.1
3.2
3.3
4.1
IPV4 HEADER.........7
FIVE CLASSES OF IPV4 ADDRESS......8
IPV6 HEADER..9
LOCK-KEEPER COMPONENTS........10
THE STATES OF SWITCH INTERVAL
IN THE SINGLE GATE LOCK-KEEPER SYSTEM...11
DUAL STACK..14
TUNNELING.15
HEADER TRANSLATION...15
PROTOCOL ISOLATION FOR SECURITY....16
ENABLING IPV4/IPV6 ON ALL NETWORK INTERFACES OF LOCK-KEEPER.18
IP CONFIGURATIONS ON LOCK-KEEPER...19
IP-BASE EXCHANGE MODULE FUNCTIONALITY.20
PERCENTALE INCREASE IN TRANSFER TIME FOR DIFFERENT FILE SIZES...22
VIII SEM ,B.E [ECE] ,RNSIT
Page | 4
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
CHAPTER 1
INTRODUCTION
VIII SEM ,B.E [ECE] ,RNSIT
Page | 5
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
INTRODUCTION
The depletion of IPv4 addresses was the main motivation behind designing IPv6. It provides
a 128-bit address space instead of a 32-bit address space in IPv4. So, IPv6 will have enough
unique addresses for variable types of products, such as smart phones, IP TV, automobiles,
etc. Moreover, IPv6 expands and optimizes some features of IPv4 to make it more powerful.
IPv6 was designed with stateless address auto-configuration, mandatory IPSec for security,
enhanced mobility, simple header structure, Quality of Service (QoS) provisioning, and more.
IPv6 is a next generation Internet layer protocol which is designed by Internet Engineering
Task force (IETF) to overcome the limitations of IPv4 networks. IPv4 addresses being 32 bits
in size provide approximately 4.3 billion addresses as compared to IPv6 address which is 128
bits in size and provides approximately 3.4*10^38 addresses. Security attacks have been
common across the Internet therefore in order to protect IPv6 networks from security attacks,
IPSec is made an inbuilt component of IPv6 and it ensures the integrity, authenticity and
confidentiality of data transmitted across the networks. IPSec is a networking layer protocol
which is used to protect the data between two devices. IPSec encrypts and authenticates the
packets before sending them across the Internet. Using IPSec in IPv6 further enhances the
security and protects the data sent in IPv6 networks.
The communication evaluation identifies IPv4 as being limited in not only the addresses
available for customers but also in the services that consumers need to access the
applications. The new version (IPv6) is found to have solved these issues of IPv4 by
extending the size of the network in order to accommodate more customers; it is also easier to
reconfigure addresses.
IPv6 also provides a higher performance, particularly during real time traffic, which requires
quality of service (QoS), and the overall processing time is reduced.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 6
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
IPv4
The Internet depends on protocol that is known as Internet Protocol version 4 (IPv4), which
uses Classless Interdomain Routing (CIDR) and 32 bit: this protocol can cover 4.3 billion
nodes around the world. Because the technology is developing, and many different services
and devices use 3G and 4G, IPv4 is approaching its limit there is not enough IPs available
from internet service providers (ISP) to meet customer demand.
Fig 1.1 IPv4 header
IPv4 is considered the core of internet addressing, as it allows transmission of data using
TCP/IP. In previous years, this protocol proved its stability and reliability in working in the
internet environment in order to provide a connection for millions of nodes.
In general, IPv4 contains five classes. Each class provides different limits to the address
numbers for networks and hosts; the figure 2 shows the types of addresses and their range.
Class A addresses were designed for large organizations with a large number of attached hosts
or routers. Class B addresses were designed for midsize organizations with tens of thousands
of attached hosts or routers. Class C addresses were designed for small organizations with a
small number of attached hosts or routers.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 7
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
Figure 1.2 shows the five classes of IPv4 address.
A block in class A address is too large for almost any organization. This means most of the
addresses in class A were wasted and were not used. A block in class B is also very large,
probably too large for many of the organizations that received a class B block. A block in
class C is probably too small for many organizations. Class D addresses were designed for
multicasting. class E addresses were reserved for future use.
IPv6
IPv6 is also known as IP next generation: it is considered evolutionary from IPv4, as it does
not make a radical change to IPv4 and the basic concept remains the same, but some features
have been added, which help to improve performance and provide a good service for
customers. In IPv6, the NAT was eliminated, which is considered an advantage.
The IP address is a combination of the MAC address for the interface and the prefix from the
router. The IPv6 size is 128 bits, comprised of Hexadecimal digits which are able to provide
3.8X10^38 addresses, which are enough to give a unique address to each device for today and
the future. Each four digits are separated by a colon which provides eight parts; the zeroes
can be omitted to make the address smaller as shown in figure 3
VIII SEM ,B.E [ECE] ,RNSIT
Page | 8
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
Fig 1.3 IPv6 header
The IPv6 provides solutions for weakness in IPv4, such as address exhaustion: IPv6nprovides
addresses with 128 bit, there are no private addresses, and the transmission of data is end to
end. IPv4 depends on manual or dynamic host configuration for addressing, whereas IPv6
uses auto configuration: the configuration is done automatically without the need to send a
query and wait for a response from the DHCP server. The security with IPv4 is optional, so
data transferred over the Internet could be hacked; IPv6, however, has IPsec in-built so that
data is encrypted.
IPSEC
IPSec is an Internet layer protocol designed for providing security at the network layer. It is
used to provide authenticity, integrity and confidentiality between two peers communicating
over the network. It ensures safe transmission of data across networking devices.
The objective of IPSec is to provide:
Authentication It ensures data has been sent by an identified sender.
Data Confidentiality It provides protection to data by encrypting the information being
transmitted.
Data Integrity Specifies that there are no changes while transmitting data across the
networks and packets are sent to the receiver intact.
Avoid replay attacks The transmitted packets do not get altered by any of the attacks
deployed by any attacker.
LOCK-KEEPER
VIII SEM ,B.E [ECE] ,RNSIT
Page | 9
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
Lock-Keeper is a high-level security solution based on the simple idea of "Physical
Separation". It is a hardware-based device and works to provide secure data exchange
between physically separated networks. Based on the simple principle that "the ultimate
method to secure a network is to disconnect it" the Lock-Keeper can entirely prevent sessionbased and protocol-based network attacks (i.e. so-called "online attack") by physically
isolating your sensitive network from external world.
In response to the emerging deployment of IPv6 on network devices, in this paper, IPv6 is
integrated to the network security device named Lock-Keeper. The Lock-Keeper system
has been offered as a high level security product to prevent online attacks against an internal
IPv4-based network. It works as switch and permits data exchange between two physically
separated networks without establishing direct physical connections.
Figure 1.4 Lock-Keeper components
Fig. 4 shows the abstract principle of Lock-Keepers operation. The Lock-Keeper system
consists of four components: INNER, OUTER, GATE, and a switch module. To support IPv6
on Lock-Keeper, a new IPv4/IPv6 handoff transformation mechanism is implemented for
managing the IPv4/IPv6 intercommunication process inside the Lock-Keeper.
Features of Lock-keeper
VIII SEM ,B.E [ECE] ,RNSIT
Page | 10
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
The Highest Level Protection of the Internal Network
Implementation of the security principle of "Physical Separation"
Flexible Design based on the security concept of "Secure it first,
build it later"
Simple and Seamless Combination with other Third-Party Security Methods
Additional Functionalities with Enhanced Security:
Integrated Application Proxy/Server for File/Email-Exchange
IPv6 over Lock-Keeper
Secure Web Service Gateway
Strong and Federated Authentication for SOA Environment.
The Lock-Keeper System
Hardware Architecture of the Single Gate Lock-Keeper
Fig 1.5 The states of switch interval in the Single Gate Lock-Keeper System
The Single Gate Lock-Keeper system, which consists of three active Single Board Computers
(SBCs): INNER, OUTER and GATE, is a simple implementation of the Lock-Keeper
technology. Each Lock-Keeper SBC has its own physical components (CPU, RAM, hard
disk, network cards, etc.). INNER is connected to the internal network with high-level
security requirements, for example an intranet of a company as well as the OUTER computer
on the opposite side is connected to the less secure network, e.g., the Internet. The third LockKeeper SBC, GATE, is set up to perform a detailed analysis of the traffic passing through. All
three components are connected to a patented switching unit that restricts their
communication.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 11
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
The two defined states of switch states (interval 0: INNER and GATE connected to each
other, interval 1: GATE and OUTER connected to each other), ensured by the above
mentioned SingleGate Lock-Keeper switch PCB, are shown in Figure. INNER and OUTER,
along with their respectively connected networks, i.e. internal network and external network,
cannot be connected directly at any time. The switch PCB enables and disables connections
on the physical level, i.e., interrupts the data transmission cables. The function and timing of
this unit is autonomous and cannot be changed or disengaged by someone who has access to
the rest of the system. Thus, neither external attackers nor insiders can change or bypass the
state of the physical separation of the networks.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 12
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
CHAPTER 2
TRANSITION STRATEGIES
VIII SEM ,B.E [ECE] ,RNSIT
Page | 13
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
TRANSITION STRATEGIES
Transition strategies are methods that provide a means of connection between IPv4 and IPv6,
as these two protocols cannot understand each other. Therefore, in order to transfer data, a
special method is needed.
The three strategies are:
Dual-Stack: This method is used to understand simultaneously IPv4 and IPv6: regardless of
which protocol is used, when the traffic is received the node is able to respond.
Tunnel: This strategy is employed when there are two networks that are using the same IP
version but are separated by another network that has a different IP. The tunnel method
establishes a virtual link through the networks by providing a connection in the middle of
them.
Translation: This method is similar to NAT, as it changes the IP packet from IPv4 to IPv6and
vice versa, depending on the source and the destination
Dual-Stack
The Dual Stack technique uses IPv4 and IPv6 within the same stack in parallel. The choice of
protocol is decided by the administrator policies, along with what kind of service is required
and which type of network is used. This technology does not make any change to the packet
header and at the same time does not make encapsulation between IPv4 and IPv6. This
technology is known as native dual stack or Dual IP layer.
Fig 2.1 Dual Stack
VIII SEM ,B.E [ECE] ,RNSIT
Page | 14
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
To determine which version to use when sending a packet to a destination, the source host
queries the DNS. If the DNS returns an IPv4 address, the source host sends an IPv4 packet. If
the DNS returns an IPv6 address, the source host sends an IPv6 packet.
Tunneling
Tunneling is a strategy used when two computers using IPv6 want to communicate with each
other and the packet must pass through a region that uses IPv4. To pass through this region,
the packet must have an IPv4 address. So the IPv6 packet is encapsulated in an IPv4 packet
when it enters the region, and it leaves its capsule when it exits the region. It seems as if the
IPv6 packet goes through a tunnel at one end and emerges at the other end. To make it clear
that the IPv4 packet is carrying an IPv6 packet as data, the protocol value is set to 41.
Tunneling is shown in Figure
Fig 2.2 Tunneling
Header Translation
Fig 2.3 Header Translation
VIII SEM ,B.E [ECE] ,RNSIT
Page | 15
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
Header translation is necessary when the majority of the Internet has moved to IPv6 but some
systems still use IPv4. The sender wants to use IPv6, but the receiver does not understand
IPv6. Tunneling does not work in this situation because the packet must be in the IPv4 format
to be understood by the receiver. In this case, the header format must be totally changed
through header translation. The header of the IPv6 packet is converted to an IPv4 header.
Header translation uses the mapped address to translate an IPv6 address to an IPv4 address.
Protocol Isolation for Security
Generally, network layer separation can be done by subnetting, which creates different
networks. Two nodes in different subnets communicate with each other through the gateway
only.
Idea of Protocol Isolation for security is introduced by Microsoft to protect entire LANs
from the external Internet. In this model, an Internet server with two network adapters has
been used. One of these adapters is connected to the Internet using the IP protocol, and the
other is connected to the LAN which runs another protocol such as the IPX protocol.
Fig 2.4 Protocol Isolation for Security
The resources on the server are accessible from both directions, but the data cannot be passed
through, i.e., Internet users can reach the server, but cannot access the Intranet because it
requires IPX. The advantage of protocol isolation model is that the LAN users can share
information with Internet users without exposing the LAN to unauthorized users. On the
other hand, one limitation of this model is that the LAN users cannot directly access the
Internet.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 16
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
VIII SEM ,B.E [ECE] ,RNSIT
Page | 17
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
CHAPTER 3
IPV4/IPV6 HANDOFF INSIDE THE
LOCK-KEEPER
VIII SEM ,B.E [ECE] ,RNSIT
Page | 18
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
IPV4/IPV6 HANDOFF INSIDE THE LOCK-KEEPER
Fig 3.1 Enabling IPv4/IPv6 on all network interfaces of Lock-Keeper
On each component of Lock-Keeper, there is a separated network card. These three network
cards are connected by the LK-Switch Module and responsible for the data transmission
inside the Lock-Keeper system. Besides, on INNER and OUTER, there are two additional
network interfaces, respectively exposing services to internal and external users. Each
interface could have IPv4, IPv6, or both. So, there are many possibilities for IP combinations
on Lock-Keeper to support IP protocol isolation and to achieve the IPv4/IPv6 handoff. By
properly configuring the Lock- Keeper network interfaces, the packets could pass through the
Lock-Keeper using different IP protocols. The most flexible one is to enable both IPv4 and
IPv6 on all interfaces as shown in Fig.10. In this case, the Lock-Keeper will gain high
flexibility to work in IPv4/IPv6 networks at both sides, OUTER and INNER.
IP configurations on Lock-Keeper
The X in the Fig.11 means that the protocol is not supported at the corresponding network
interface. The most interesting configuration cases are shown in Case 1 and Case 2. In these
cases, the Lock-Keeper can communicate with IPv4 and IPv6 at both sides, INNER and
OUTER. Besides achieving high flexibility, a virtual barrier is created on the GATE. So,
messages will be carried through the Lock-Keeper parts using two different IP protocols.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 19
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
Figure 3.2 Some other possible IP configurations on Lock-Keeper
In Case 1, IPv4 is used for GATE-OUTER communication, while IPv6 is used for GATEINNER communication. In Case 2, GATE/OUTER communicate by using IPv6 while
GATE/INNER communicate by IPv4. Accordingly, an isolation protocol region will be
created at the GATE to enhance the Lock-Keeper security. However, these cases require small
modification on GATEs Lock-Keeper Secure Data Exchange LK-SDE software modules to
support IPv6.
The Cases 3 and 5 do not need modifications to GATEs LK-SDE software modules. These
cases provide the flexibility to communicate with IPv4 or IPv6 at the external side of the
OUTER. At the same time, IPv6 traffic is stopped at the OUTER. And IPv4 is used for the
communication between GATE-OUTER and GATE-INNER.
Case 5 allows the INNER to communicate only by IPv6. The Cases 4 and 6 mainly depend
on IPv6 protocol for the Lock-Keeper internal communication and these cases need
modifications to GATEs LK-SDE software modules to support IPv6.
To mitigate this vulnerability, a new IP-Based eXchange (IP-BX) module is added on
OUTER of the Lock-Keeper. This Module manages the intercommunication process between
IPv4 and IPv6. The functionality of this module is to receive the IPv4/IPv6 packets and then
checks the Version field value in IP header. Base on the Version field value, IP-BX
VIII SEM ,B.E [ECE] ,RNSIT
Page | 20
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
module selects the proper IP protocol to carry data. For example, if the data received by IPv6
at the OUTER,
IP-BX module can decide to use IPv4 for GATE INNER communication. In this way, the
network protocol separation is achieved to enhance security by exchanging data between
physically separated networks using different IP protocols.
Figure 3.3 IP-Base eXchange module functionality
IP protocol isolation security is a powerful solution in mixed IPv4/IPv6 networks. Because
IPv4 firewalls cannot be deployed for IPv6, both IPv4-based and IPv6-based firewalls are
needed to be configured and managed carefully. Otherwise, the internal networks can be
vulnerable to some attack due to IPv6 protocol misused. Even in case of enabling IPv4 and
IPv6 on all of the Lock-Keeper interfaces, the IP protocol isolation is still possible if the IPBX works according to the algorithm which is shown in Figure 12.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 21
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
CHAPTER 4
RESULTS AND
CONCLUSION
VIII SEM ,B.E [ECE] ,RNSIT
Page | 22
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
EXPERIMENTAL RESULT
Even though IPv6 data header length is twice as that of the IPv4 header implying that IPv6
has a higher overhead than IPv4, the time delay through the Lock-Keeper is almost identical
in both cases, i.e., with original IPv4-only and with integrating IPv6. By experiment, we
found that the Lockkeeper has about 0.08 % increases in the transfer time than with IPv4only when an external user uses IPv6 to get 1GB file form IPv6-internal server. IPv4
outperforms IPv6 by only about 0.001% for transferring 10KB file. For smaller file sizes, the
transfer times are roughly equal. Fig. 8 shows the percentage increase in transfer time through
the Dual Gate Lock-Keeper by integrating IPv6 comparing to the original IPv4-only LockKeeper when transferring different file sizes.
Fig 4.1 Percentale increase in transfer time for different file sizes due to
integrating IPv6 on Lock-Keeper comparing to the original LockKeeper.
The above results have been possible since IPv6 header structure is designed to get a
simplified standard format which can be processed faster than IPv4 headers. Moreover, the
switching mechanism, queuing delay, and scanning time inside the Lock-Keeper from the
significant portion of the total transfer time rather than the processing time.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 23
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
CONCLUSION
IPv6 is a viable solution to IPv4 addressing space depletion problem. Accordingly, IPv6 is
being integrated into more and more new products. However, the migration to IPv6 may
take many years and new products should be able to communicate with both IPv4 and
IPv6 during the coexistence period.
Increasing the usability of the Lock-Keeper to work with both IPv4 and IPv6.
Enhancing the security of the Lock-Keeper protected network by integrating an IPv4/IPv6
protocol handoff mechanism.
Providing a physical separation based IPv4/IPv6 isolation approach.
we integrate IPv6 on the Lock-Keeper to extend it to work in both IP4/IPv6 environments in
a secure way. An IPv4/IPv6 isolation mechanism based on the protocol separation is used to
permit the secure data exchange over physically separated networks.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 24
IPv4/IPv6 Handoff on Lock-Keeper for High
Flexibility and Security
2016
REFERENCES
[1] F. Cheng, P. Ferring, C. Meinel, G. M llenheim, and J. Bern, The DualGate LockKeeper: A Highly Efficient, Flexible and Applicable Network Security Solution, in
Proceedings of the 4th ACIS International Conference on Software Engineering, Artificial
Intelligence, Networking, and Parallel/Distributed Computing (SNPD 2003). Luebeck,
Germany. October 16-18, 2003.
[2] Lock-Keeper Website, Dec. 2010, http://www.lock-keeper.org/
[3] Ali Albkerat and Biju Issac, Analysis of IPV6 Transition Technologies, International
Journal of Computer Networks & Communications (IJCNC)
Vol.6, No.5, September 2014.
[4] F. Cheng, and C. Meinel, Lock-Keeper: A new implementation of physical separation
technology, In: Paulus, S., Pohlmann, N., Reimer, H. (eds.) Securing Electronic Business
Processes: Highlights of the Information Security Solutions Europe Conference, (ISSE 2006),
Friedrich Vieweg & Sohn Verlag, 2006, pp. 275286.
[5] D. S. Punithavathani and K. Sankaranarayanan, IPv4/IPv6 Transition Mechanisms
European Journal of Scientific Research, Vol.34 No.1, 2009, pp.110-124.
[6]
J. Bi, J. Wu, and X. Leng. IPv4/IPv6 Transition Technologies and Univer6
Architecture, IJCSNS International Journal of Computer Science and Network Security, Vol.
7(1), January 2007, pp. 232-243.
[7] Tina Sharma and Savita Shiwani, Statistical Results of IPSec in IPv6 Networks,
International Journal of Computer Applications (0975 8887) Volume 79 No.2, October
2013.
VIII SEM ,B.E [ECE] ,RNSIT
Page | 25
Você também pode gostar
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNo EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNota: 4 de 5 estrelas4/5 (5794)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNo EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNota: 4 de 5 estrelas4/5 (895)
- The Yellow House: A Memoir (2019 National Book Award Winner)No EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Nota: 4 de 5 estrelas4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingNo EverandThe Little Book of Hygge: Danish Secrets to Happy LivingNota: 3.5 de 5 estrelas3.5/5 (400)
- The Emperor of All Maladies: A Biography of CancerNo EverandThe Emperor of All Maladies: A Biography of CancerNota: 4.5 de 5 estrelas4.5/5 (271)
- Never Split the Difference: Negotiating As If Your Life Depended On ItNo EverandNever Split the Difference: Negotiating As If Your Life Depended On ItNota: 4.5 de 5 estrelas4.5/5 (838)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyNo EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyNota: 3.5 de 5 estrelas3.5/5 (2259)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNo EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNota: 4.5 de 5 estrelas4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNo EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNota: 3.5 de 5 estrelas3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnNo EverandTeam of Rivals: The Political Genius of Abraham LincolnNota: 4.5 de 5 estrelas4.5/5 (234)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNo EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNota: 4.5 de 5 estrelas4.5/5 (266)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNo EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNota: 4.5 de 5 estrelas4.5/5 (345)
- The Unwinding: An Inner History of the New AmericaNo EverandThe Unwinding: An Inner History of the New AmericaNota: 4 de 5 estrelas4/5 (45)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNo EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNota: 4 de 5 estrelas4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)No EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Nota: 4.5 de 5 estrelas4.5/5 (121)
- 2023 2 Acca111 - Accounting Information Systems - IntroductionDocumento40 páginas2023 2 Acca111 - Accounting Information Systems - IntroductionShefannie PaynanteAinda não há avaliações
- 以太网进阶培训 Part1 STM32以太网外设Documento53 páginas以太网进阶培训 Part1 STM32以太网外设Haykel MhedhbiAinda não há avaliações
- Learn ChatGPT - The Future of Learning (2022)Documento34 páginasLearn ChatGPT - The Future of Learning (2022)Tibor Skulkersen100% (1)
- Venom VB-303: User ManualDocumento32 páginasVenom VB-303: User ManualMmAinda não há avaliações
- Advance Pricing ProfilesDocumento28 páginasAdvance Pricing Profileskoushikmajumder1238333Ainda não há avaliações
- Customising Tables For InfoTypesDocumento3 páginasCustomising Tables For InfoTypesAniruddha DeshmukhAinda não há avaliações
- NE MotoHawk Resource Guide PDFDocumento105 páginasNE MotoHawk Resource Guide PDFMarkus SenojAinda não há avaliações
- TEJ3M Exam Review Sheet June 2015 (No Networking)Documento6 páginasTEJ3M Exam Review Sheet June 2015 (No Networking)AliAinda não há avaliações
- Microwave Communication SystemsDocumento14 páginasMicrowave Communication SystemsHarreniAinda não há avaliações
- CounterACT Console User Manual 7.0.0Documento756 páginasCounterACT Console User Manual 7.0.0bkshrestha69100% (2)
- BlogDocumento14 páginasBlogmaximus2782Ainda não há avaliações
- Noteshub - Co.In - Download Android App: Scanned by CamscannerDocumento72 páginasNoteshub - Co.In - Download Android App: Scanned by CamscannerBhavay AnandAinda não há avaliações
- CLI Management User GuideDocumento25 páginasCLI Management User GuideerickgugoAinda não há avaliações
- The Business Value of Oracle Database Appliance: Executive SummaryDocumento16 páginasThe Business Value of Oracle Database Appliance: Executive SummaryyurijapAinda não há avaliações
- Unwired Learning: The Ultimate Python Developer BundleDocumento19 páginasUnwired Learning: The Ultimate Python Developer BundleNnnnngdggAinda não há avaliações
- Python Classes and ObjectsDocumento58 páginasPython Classes and ObjectsVitor Matheus100% (1)
- Remote Access To LAN - SoftEther VPN ProjectDocumento5 páginasRemote Access To LAN - SoftEther VPN Projectsmang10Ainda não há avaliações
- Unit 3: Name: Date: Score: / 50 PointsDocumento2 páginasUnit 3: Name: Date: Score: / 50 PointsMachtia Nemachtia100% (5)
- Jenkins Book PDFDocumento224 páginasJenkins Book PDFAmir AzizAinda não há avaliações
- The Phishing GuideDocumento47 páginasThe Phishing Guidezorantic1Ainda não há avaliações
- About SAP GatewayDocumento12 páginasAbout SAP GatewayDinakar Babu JangaAinda não há avaliações
- Docu31714 EMC VNX5100 and VNX5300 Series Storage Systems Disk and OE MatrixDocumento7 páginasDocu31714 EMC VNX5100 and VNX5300 Series Storage Systems Disk and OE MatrixMariappan KalaivananAinda não há avaliações
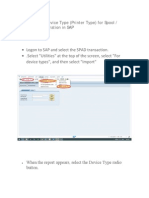
- How To Import Device Type in SAPDocumento4 páginasHow To Import Device Type in SAPMuhammad ShoaibAinda não há avaliações
- Usb Cam LogDocumento4 páginasUsb Cam LogJuan Agustin Bravo LeonAinda não há avaliações
- Computer ScienceDocumento2 páginasComputer ScienceNeha agrawalAinda não há avaliações
- ChangelogDocumento2 páginasChangelogmanuelaAinda não há avaliações
- Adobe Launch Cheat SheetDocumento1 páginaAdobe Launch Cheat SheetJason MintAinda não há avaliações
- Introduction & Product Overview: Ian Maynard - Senior Engineer EMEADocumento22 páginasIntroduction & Product Overview: Ian Maynard - Senior Engineer EMEAМахендра СингхAinda não há avaliações
- Release Mode Bundle ErrorDocumento11 páginasRelease Mode Bundle ErrorRaman deepAinda não há avaliações
- SIMCom 3G MQTT Application Note V1.00Documento18 páginasSIMCom 3G MQTT Application Note V1.00Sijeo PhilipAinda não há avaliações