Escolar Documentos
Profissional Documentos
Cultura Documentos
Iethical HackingCEH
Enviado por
rosslovelady0 notas0% acharam este documento útil (0 voto)
5 visualizações1 páginaiEthical
Título original
iEthical-HackingCEH
Direitos autorais
© © All Rights Reserved
Formatos disponíveis
PDF, TXT ou leia online no Scribd
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoiEthical
Direitos autorais:
© All Rights Reserved
Formatos disponíveis
Baixe no formato PDF, TXT ou leia online no Scribd
0 notas0% acharam este documento útil (0 voto)
5 visualizações1 páginaIethical HackingCEH
Enviado por
rossloveladyiEthical
Direitos autorais:
© All Rights Reserved
Formatos disponíveis
Baixe no formato PDF, TXT ou leia online no Scribd
Você está na página 1de 1
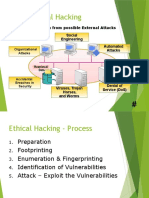
iEthical Hacking(CEH)
1. Introduction to Ethical Hacking
2. Footprinting and Reconnaissance
3. Scanning Networks
4. Enumeration
5. System Hacking
6. Trojans and Backdoors
7. Viruses and Worms
8. Sniffers
9. Social Engineering
10. Denial of Service
11. Session Hijacking
12. Hacking Webservers
13. Hacking Web Applications
14. SQL Injection
15. Hacking Wireless Networks
16. Evading IDS, Firewalls and Honeypots
17. Buffer Overflows
18. Cryptography
19. Penetration Testing
Você também pode gostar
- Ethical HackingDocumento3 páginasEthical HackingGaurav GhandatAinda não há avaliações
- Hacking PresentationDocumento14 páginasHacking PresentationpamukumarAinda não há avaliações
- CYBER SECURITY & ETHICAL HACKING COLLEGE WORKSHOPSDocumento7 páginasCYBER SECURITY & ETHICAL HACKING COLLEGE WORKSHOPSDeepak SharmaAinda não há avaliações
- App inDocumento1 páginaApp inAamir AkhtarAinda não há avaliações
- Certified Ethical HackingDocumento5 páginasCertified Ethical HackingOwen MasiberahAinda não há avaliações
- Ethical Hacking and Counter Measures Course OutlineDocumento7 páginasEthical Hacking and Counter Measures Course Outlineresearch.aiAinda não há avaliações
- Hacking Course Plan 1Documento3 páginasHacking Course Plan 1Pankaj SharmaAinda não há avaliações
- HCSP Cyber Security Training ProgramDocumento9 páginasHCSP Cyber Security Training ProgramShamsher KhanAinda não há avaliações
- Types of Internet & E-Commerce Computer Crime ExplainedDocumento15 páginasTypes of Internet & E-Commerce Computer Crime ExplainedcatchriyazAinda não há avaliações
- Information About Ethical HackingDocumento2 páginasInformation About Ethical HackingSoham SawantAinda não há avaliações
- Computer Networks NoteDocumento38 páginasComputer Networks NoteSimple GuptaAinda não há avaliações
- A N Tcybersecurity Awareness Jul 23Documento19 páginasA N Tcybersecurity Awareness Jul 23Subramanian RamakrishnanAinda não há avaliações
- Ethical Hacking Syllabus: Rooman Technologies PVT LTDDocumento7 páginasEthical Hacking Syllabus: Rooman Technologies PVT LTDNepsonAinda não há avaliações
- Paper-1: Ethical Hacking ContentsDocumento7 páginasPaper-1: Ethical Hacking Contents9630455310Ainda não há avaliações
- Final Hacking BookDocumento198 páginasFinal Hacking BookC Cube Cad Centre - ErodeAinda não há avaliações
- Why - Ethical Hacking: Social Engineering Automated Attacks Protection From Possible External AttacksDocumento14 páginasWhy - Ethical Hacking: Social Engineering Automated Attacks Protection From Possible External AttacksfaizaAinda não há avaliações
- Ethical Hacking: Presented By: CYBER SHIELDDocumento19 páginasEthical Hacking: Presented By: CYBER SHIELDHaval AbdulkarimAinda não há avaliações
- Management Information SystemDocumento4 páginasManagement Information Systematif0078Ainda não há avaliações
- Ethical HackingDocumento16 páginasEthical HackingasgdAinda não há avaliações
- Diploma in Ethical Hacking CourseDocumento33 páginasDiploma in Ethical Hacking CourseWaseem AkramAinda não há avaliações
- Top 50 Cyber Security Interview Questions and Answers 2022Documento15 páginasTop 50 Cyber Security Interview Questions and Answers 2022Anirban deyAinda não há avaliações
- Units 7 and 8 - Computer Etiquette and Computer & CyberSecuritiesDocumento20 páginasUnits 7 and 8 - Computer Etiquette and Computer & CyberSecuritiesmarsan walangAinda não há avaliações
- UntitledDocumento1 páginaUntitledRituraj GoswamiAinda não há avaliações
- Ethical Hacking ModulesDocumento21 páginasEthical Hacking Modulessarwarbilal523Ainda não há avaliações
- MCE Cybersecurity ForensicDocumento105 páginasMCE Cybersecurity Forensicgowdanischith03Ainda não há avaliações
- Cyber Security ApponixDocumento4 páginasCyber Security ApponixAshokAinda não há avaliações
- Cyber Crime Prevention and DetectionDocumento4 páginasCyber Crime Prevention and DetectionJoshua AyoolaAinda não há avaliações
- Internship Weekly ReportDocumento6 páginasInternship Weekly Reportmrharshilpatel8802Ainda não há avaliações
- Syllabus For Diferent Courses Related To Cyber SecurityDocumento2 páginasSyllabus For Diferent Courses Related To Cyber Securitysneha kotawadekarAinda não há avaliações
- Introduction To Ethical HackingDocumento4 páginasIntroduction To Ethical HackingPreethi PreethiAinda não há avaliações
- Ethical Hacking V9: DescriptionDocumento5 páginasEthical Hacking V9: DescriptionramanaAinda não há avaliações
- CO 405 Internet Security Lab ReportDocumento27 páginasCO 405 Internet Security Lab ReportUtkarshPrasad100% (1)
- Basic Topics: Introduction To Information SecurityDocumento4 páginasBasic Topics: Introduction To Information SecurityTanujSoodAinda não há avaliações
- Network and System Security CEH TrainingDocumento3 páginasNetwork and System Security CEH TrainingSamuel GetachewAinda não há avaliações
- Security+ SY0-501Documento2 páginasSecurity+ SY0-501nmmMJKJAinda não há avaliações
- Cyber SecurityDocumento3 páginasCyber SecuritySAMAY N. JAINAinda não há avaliações
- Certified Ethical Hacking: Ron Woerner, CISSP, CEHDocumento35 páginasCertified Ethical Hacking: Ron Woerner, CISSP, CEHranjithc24Ainda não há avaliações
- Top 40 Ethical Hacking Interview Questions and Answers For 2022Documento9 páginasTop 40 Ethical Hacking Interview Questions and Answers For 2022Anirban deyAinda não há avaliações
- CEH Certification Notes: Complete Guide to Ethical Hacking ModulesDocumento97 páginasCEH Certification Notes: Complete Guide to Ethical Hacking ModulesSachjith MAinda não há avaliações
- CyberDocumento5 páginasCybermuna cliffAinda não há avaliações
- Proposal Cyber Security TrainingDocumento7 páginasProposal Cyber Security TrainingDhruv PanditAinda não há avaliações
- Cyber Security BrochureDocumento5 páginasCyber Security BrochureShweta HosmaniAinda não há avaliações
- CYBER Terrorism NewDocumento84 páginasCYBER Terrorism NewNalin JayaratneAinda não há avaliações
- Cryptography and Cyber SecurityDocumento162 páginasCryptography and Cyber SecuritycygnusvesaliusAinda não há avaliações
- Cyber Security MumbaiDocumento18 páginasCyber Security Mumbairony raiAinda não há avaliações
- Live WireDocumento2 páginasLive Wireharshada kavdeAinda não há avaliações
- Certified Ethical Hacker v9Documento9 páginasCertified Ethical Hacker v9JJ Asonyer100% (1)
- Presentation 1Documento11 páginasPresentation 1Harsh RavadkaAinda não há avaliações
- IP SPOOFING DocumentationDocumento18 páginasIP SPOOFING DocumentationAncy AnasAinda não há avaliações
- Session HijackingDocumento21 páginasSession HijackingbillhjkAinda não há avaliações
- 19cse304-Cybersecurity Answer KeyDocumento19 páginas19cse304-Cybersecurity Answer KeyabhiAinda não há avaliações
- CNS SyllabusDocumento1 páginaCNS SyllabusgdeepthiAinda não há avaliações
- System SecurityDocumento4 páginasSystem SecurityTanishka MayekarAinda não há avaliações
- Ethical Hacking 12-SeptDocumento13 páginasEthical Hacking 12-SeptArun KrishnanAinda não há avaliações
- CompTIA Security+ (SY0-601) LearnDocumento81 páginasCompTIA Security+ (SY0-601) LearnbuntyhibuntyAinda não há avaliações
- TA4 - Cyber Security - 1688734977204Documento66 páginasTA4 - Cyber Security - 1688734977204Deepak KumarAinda não há avaliações
- Ip Spoofing: A Seminar Report On Techniques And ApplicationsDocumento12 páginasIp Spoofing: A Seminar Report On Techniques And ApplicationsCharan royalAinda não há avaliações
- W.E.F Academic Year 2012-13 G' SchemeDocumento5 páginasW.E.F Academic Year 2012-13 G' SchemeSanket bhosaleAinda não há avaliações
- DigitalForensic FlyerDocumento3 páginasDigitalForensic Flyercmpn.20102a0032Ainda não há avaliações
- How To Install Snort NIDS On Ubuntu LinuxDocumento9 páginasHow To Install Snort NIDS On Ubuntu LinuxrossloveladyAinda não há avaliações
- Monitor Traffic On Specific PCs - THWACKDocumento3 páginasMonitor Traffic On Specific PCs - THWACKrossloveladyAinda não há avaliações
- Ebook - SysAdmin Guide To Azure IaaSDocumento85 páginasEbook - SysAdmin Guide To Azure IaaSSrinivas ReddyAinda não há avaliações
- Gartner MQ Data Centre Outsourcing & Infrastructure Utility Services - EuropeDocumento38 páginasGartner MQ Data Centre Outsourcing & Infrastructure Utility Services - EuroperossloveladyAinda não há avaliações
- EICON DIVA softSS7ReferenceGuideDocumento56 páginasEICON DIVA softSS7ReferenceGuiderossloveladyAinda não há avaliações
- Gartner MQ Intrusion Detection & Prevention SystemsDocumento46 páginasGartner MQ Intrusion Detection & Prevention SystemsrossloveladyAinda não há avaliações
- AllData4HP22 Valve Body DiagramsDocumento7 páginasAllData4HP22 Valve Body Diagramsrosslovelady100% (4)
- Configure Sflow Export On Dell Power Connect Switches - SolarWinds Worldwide, LLC. Help and SupportDocumento1 páginaConfigure Sflow Export On Dell Power Connect Switches - SolarWinds Worldwide, LLC. Help and SupportrossloveladyAinda não há avaliações
- How To Run VMware ESXI 7.0 On Hardware With Unsupported CPUs - Flemming's BlogDocumento5 páginasHow To Run VMware ESXI 7.0 On Hardware With Unsupported CPUs - Flemming's BlogrossloveladyAinda não há avaliações
- Ebook - SysAdmin Guide To Azure IaaSDocumento85 páginasEbook - SysAdmin Guide To Azure IaaSSrinivas ReddyAinda não há avaliações
- Building A Multi-Lingual OCR EngineDocumento21 páginasBuilding A Multi-Lingual OCR EnginerossloveladyAinda não há avaliações
- Cloud Security - A Primer by Yogesh Gupta, CISSP® CCSK CCSP - The Cloud, Services, Standards - PeerlystDocumento8 páginasCloud Security - A Primer by Yogesh Gupta, CISSP® CCSK CCSP - The Cloud, Services, Standards - PeerlystrossloveladyAinda não há avaliações
- BIG-IP Systems Getting Started GuideDocumento102 páginasBIG-IP Systems Getting Started Guidesh_ashokAinda não há avaliações
- 2016 Fee-Help BookletDocumento33 páginas2016 Fee-Help BookletrossloveladyAinda não há avaliações
- (Ptsecurity, 2016) Positive Research 2016 EngDocumento104 páginas(Ptsecurity, 2016) Positive Research 2016 EngrossloveladyAinda não há avaliações
- ANU Crawford Academic Skills Handbook Aug 2015Documento89 páginasANU Crawford Academic Skills Handbook Aug 2015rossloveladyAinda não há avaliações
- Maguire IK2555 Lectures 20160108 HandoutsDocumento591 páginasMaguire IK2555 Lectures 20160108 HandoutsrossloveladyAinda não há avaliações
- Simon Hackett Submission - Enquiry Into Australian Telco Networks Sub136dDocumento34 páginasSimon Hackett Submission - Enquiry Into Australian Telco Networks Sub136drossloveladyAinda não há avaliações
- Maguire 2G1330 Mobile & Wireless Network Architectures P4-Lecture2-2002Documento41 páginasMaguire 2G1330 Mobile & Wireless Network Architectures P4-Lecture2-2002rossloveladyAinda não há avaliações
- 2 Mobile Network Architecture SigPloiter - SigPloit Wiki GitHubDocumento2 páginas2 Mobile Network Architecture SigPloiter - SigPloit Wiki GitHubrossloveladyAinda não há avaliações
- KS User ManualDocumento36 páginasKS User ManualrossloveladyAinda não há avaliações
- 1 Welcome To SigPloit SigPloiter - SigPloit Wiki GitHubDocumento1 página1 Welcome To SigPloit SigPloiter - SigPloit Wiki GitHubrossloveladyAinda não há avaliações
- 24 EthicalCaseStudiesDocumento16 páginas24 EthicalCaseStudiesrossloveladyAinda não há avaliações
- OFFICE 365 PROXY GUIDEDocumento4 páginasOFFICE 365 PROXY GUIDErossloveladyAinda não há avaliações
- Good Work Business Plan PDFDocumento34 páginasGood Work Business Plan PDFACBAinda não há avaliações
- IOS Forensics Where Are We Now Mattia Epifani Pasquale Stirparo (SANS) 2016Documento64 páginasIOS Forensics Where Are We Now Mattia Epifani Pasquale Stirparo (SANS) 2016rossloveladyAinda não há avaliações
- UniSA PHD Examiner FAQsDocumento5 páginasUniSA PHD Examiner FAQsrossloveladyAinda não há avaliações
- Android Forensics - Simplifying Cell Phone Examinations - Lessard & Kessler (ECU) 2010.Documento13 páginasAndroid Forensics - Simplifying Cell Phone Examinations - Lessard & Kessler (ECU) 2010.rosslovelady100% (1)
- Critique of The CISSP Common Body of Knowledge of Cryptography - Neuhaus & GheorgheDocumento3 páginasCritique of The CISSP Common Body of Knowledge of Cryptography - Neuhaus & GheorgherossloveladyAinda não há avaliações