Escolar Documentos
Profissional Documentos
Cultura Documentos
Adjusting DNS To Secure Servers Against DDoS Attacks
Enviado por
tudocrisDescrição original:
Título original
Direitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
Adjusting DNS To Secure Servers Against DDoS Attacks
Enviado por
tudocrisDireitos autorais:
Formatos disponíveis
Adjusting DNS to secure servers against DDoS attacks
DNS open recursion service can be used to conduct malicious attacks on a network. This can
occur when the default setting for DNS services is not adjusted upon installation. When used
maliciously, the service can send Distributed Denial of Service (DDoS) attacks by a third party
with malicious intentions. This can be prevented by adjusting your DNS settings. Choose your
operating system (Windows or Linux) and follow the instructions below:
Windows
Disable recursion on the DNS server: http://technet.microsoft.com/en-
us/library/cc787602%28v=ws.10%29.aspx
Then rename the 'root hints cache file' to prevent reference to the root zones being used for DNS
amplification attacks:
- Open the folder %systemroot%\system32\dns and rename cache.dns to cache.dns.orig
- Once these modifications are complete, you must restart the DNS service.
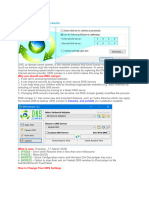
Plesk
1) Log in to your Plesk Panel as admin.
2) On the left menu, select "Server Management > Tools & Settings" section (previously called
"Server").
3) In the main panel, select "DNS Template Settings" (previously called "DNS Settings".
4) Select the DNS Recursion Tab.
5) Select the Deny option and click the Set button to complete the operation.
Linux
Edit the file /etc/named.conf and change the below variables in the "options{" section to secure
your DNS service:
version "unknown";
allow-transfer {none;};
allow-recursion {none;};
allow-query-cache {none;}; // for BIND 9.4+
recursion no;
additional-from-cache no;
Once these modifications are complete, you must restart the DNS service.
If you must use DNS recursion to provide service to your customers, iWeb requires that you
restrict the usage scope to localhost, localnets, and/or your customers IP ranges.
Windows servers running DNS open recursion can use Windows firewall to limit access to
DNS service and prevent from being exploited.
DNS TCP/UDP incoming firewall settings/rules:
*Local IP*: any
*Remote IP - /These IPs:/* Add all of your trusted IPs (other
servers of your network).
If the server has a Windows Active Directory
domain, you will have to add the source IPs that use this service.
Bind under Windows Plesk (allowing localhost and localnets)
1) Connect to your dedicated server.
2) From the Start menu, click Run, and enter the following command:
notepad "%plesk_dir%dns\etc\named.user.conf"
3) Modify the file to set allow-recursion to localnets instead of any.
4) Save and close the file. The options settings will looks like:
options { allow-transfer { localhost; localnets; }; allow-recursion { localhost; localnets; };
listen-on-v6 { none; }; version none; additional-from-cache no; };
5) Restart "named" service. From the Start menu, as administrator, click Run and run "cmd",
then type the following command in the command prompt:
net stop named && net start named
Other BIND advanced settings under Linux (allowing localhost, localnets and specific IPs)
acl "trusted"{
192.168.0.0/16; // change IPs as required
xx.15.128.0/19; // change IPs as required
localhost;
localnets;
};
options{
...
allow-query { trusted; }; // trusted could be replaced by any only if necessary
allow-transfer { trusted; };
allow-recursion { trusted;} ;
allow-query-cache { trusted; }; // for BIND 9.4+
additional-from-cache no;
...
};
----------------------
You can test your IPs with the following methods:
dig +noall +comment @<IP>
(flags: qr rd ra; means open recursive )
nmap -Pn --script=dns-recursion -sU -p53 <IP>
(you will have the following text if the DNS is open recursive: |_dns-recursion: Recursion
appears to be enabled)
Você também pode gostar
- Integrate Linux Mint 17.1 To Windows Server 2012 Active Directory Domain ControllerDocumento44 páginasIntegrate Linux Mint 17.1 To Windows Server 2012 Active Directory Domain ControlleradaucyjrAinda não há avaliações
- DNS Migration ProcedureDocumento2 páginasDNS Migration ProcedureZach PaulAinda não há avaliações
- DNS Masq SetupDocumento30 páginasDNS Masq SetupMd. Rezwan Ul AlamAinda não há avaliações
- Domain Name SystemDocumento16 páginasDomain Name SystemAbdul Khaliq100% (2)
- DNS (Domain Name Services, Named, NDC)Documento12 páginasDNS (Domain Name Services, Named, NDC)ankit boxerAinda não há avaliações
- Configuration of a Simple Samba File Server, Quota and Schedule BackupNo EverandConfiguration of a Simple Samba File Server, Quota and Schedule BackupAinda não há avaliações
- Configuration of a Simple Samba File Server, Quota and Schedule BackupNo EverandConfiguration of a Simple Samba File Server, Quota and Schedule BackupAinda não há avaliações
- Additional-From-Cache Impact On PerformanceDocumento10 páginasAdditional-From-Cache Impact On Performanceweb1_webteamAinda não há avaliações
- DNS (Domain Name System) OverviewDocumento8 páginasDNS (Domain Name System) Overviewalimo benAinda não há avaliações
- DNSDocumento9 páginasDNSSraVanKuMarThadakamallaAinda não há avaliações
- Linux BCA 5th Semester India AssamDocumento9 páginasLinux BCA 5th Semester India AssamJavedAinda não há avaliações
- Setting Up Zimbra and BackupDocumento13 páginasSetting Up Zimbra and BackupCollins EmadauAinda não há avaliações
- Step by Step Linux GuideDocumento396 páginasStep by Step Linux GuideRahul100% (24)
- Likewise OpenDocumento3 páginasLikewise Openyyha5155Ainda não há avaliações
- 4.1 - DNS Console OverviewDocumento10 páginas4.1 - DNS Console Overviewmha53Ainda não há avaliações
- Configure A New DNS ServerDocumento3 páginasConfigure A New DNS ServerKamlesh Kumar MishraAinda não há avaliações
- Configure A DNS Server Using BIND: Section 1Documento48 páginasConfigure A DNS Server Using BIND: Section 1Edri YansyahAinda não há avaliações
- How To Linux Terminal Server Project (LTSP)Documento6 páginasHow To Linux Terminal Server Project (LTSP)yaniss78Ainda não há avaliações
- Lab 1 BDocumento18 páginasLab 1 BTashinga Ryan ManunureAinda não há avaliações
- Part A - V7 Exam Questions: 1. Configure SELINUXDocumento43 páginasPart A - V7 Exam Questions: 1. Configure SELINUXAhmed Abdelfattah50% (4)
- Lab 2.1: Domain Name Service (DNS) : November 2018Documento7 páginasLab 2.1: Domain Name Service (DNS) : November 2018Tri HartonoAinda não há avaliações
- Change DNS Settings in Windows XPDocumento3 páginasChange DNS Settings in Windows XPIas Aspirant AbhiAinda não há avaliações
- Tinydns On Centos 5.4Documento4 páginasTinydns On Centos 5.4VL RickettsAinda não há avaliações
- Step by Step Process in Windows Server InstallationDocumento5 páginasStep by Step Process in Windows Server InstallationKathryn Ann FlorentinoAinda não há avaliações
- DRBL WinrollDocumento5 páginasDRBL Winrollmakhno3105Ainda não há avaliações
- What Are The Run Levels in Linux: 1) Runlevels Are Used To Specify DifferentDocumento5 páginasWhat Are The Run Levels in Linux: 1) Runlevels Are Used To Specify DifferentBasarkar SrikerAinda não há avaliações
- Step by Step Linux GuideDocumento396 páginasStep by Step Linux GuideAnonymous BOOmZGAinda não há avaliações
- DDNS ClientDocumento15 páginasDDNS ClientMageon7Ainda não há avaliações
- Active Directory Instal at IonDocumento10 páginasActive Directory Instal at IonavikbanerjeeAinda não há avaliações
- Dns Jumper v2Documento15 páginasDns Jumper v2rositadw74Ainda não há avaliações
- Window Server 2012 (Basic Configs)Documento33 páginasWindow Server 2012 (Basic Configs)Jordano ChambilloAinda não há avaliações
- Setting Up DNS Server On CentOS 7 - UnixmenDocumento16 páginasSetting Up DNS Server On CentOS 7 - Unixmenpaul andradeAinda não há avaliações
- Rhce Question and AnswerDocumento27 páginasRhce Question and AnswerRaj ShuklaAinda não há avaliações
- Expand IDS Company's Network: I. ProblemsDocumento8 páginasExpand IDS Company's Network: I. Problemshqthang19952602Ainda não há avaliações
- Plesk 10 Pci Compliance GuideDocumento10 páginasPlesk 10 Pci Compliance GuideJack JillAinda não há avaliações
- How To Remove Customer and Business Manager (CBM, Formerly Plesk Billing) From Plesk - Help Center PDFDocumento6 páginasHow To Remove Customer and Business Manager (CBM, Formerly Plesk Billing) From Plesk - Help Center PDFxserverAinda não há avaliações
- Quick Configuration of Openldap and Kerberos In Linux and Authenicating Linux to Active DirectoryNo EverandQuick Configuration of Openldap and Kerberos In Linux and Authenicating Linux to Active DirectoryAinda não há avaliações
- Evaluation of Some Intrusion Detection and Vulnerability Assessment ToolsNo EverandEvaluation of Some Intrusion Detection and Vulnerability Assessment ToolsAinda não há avaliações
- Evaluation of Some Windows and Linux Intrusion Detection ToolsNo EverandEvaluation of Some Windows and Linux Intrusion Detection ToolsAinda não há avaliações
- Protecting Confidential Information: How to Securely Store Sensitive DataNo EverandProtecting Confidential Information: How to Securely Store Sensitive DataAinda não há avaliações
- Overview of Some Windows and Linux Intrusion Detection ToolsNo EverandOverview of Some Windows and Linux Intrusion Detection ToolsAinda não há avaliações
- DRBD-Cookbook: How to create your own cluster solution, without SAN or NAS!No EverandDRBD-Cookbook: How to create your own cluster solution, without SAN or NAS!Ainda não há avaliações
- Some Tutorials in Computer Networking HackingNo EverandSome Tutorials in Computer Networking HackingAinda não há avaliações
- Red Hat Enterprise Linux 6 Administration: Real World Skills for Red Hat AdministratorsNo EverandRed Hat Enterprise Linux 6 Administration: Real World Skills for Red Hat AdministratorsAinda não há avaliações
- Hiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessNo EverandHiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessAinda não há avaliações
- Securing HP NonStop Servers in an Open Systems World: TCP/IP, OSS and SQLNo EverandSecuring HP NonStop Servers in an Open Systems World: TCP/IP, OSS and SQLAinda não há avaliações
- Evaluation of Some SMTP Testing, Email Verification, Header Analysis, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsNo EverandEvaluation of Some SMTP Testing, Email Verification, Header Analysis, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsAinda não há avaliações
- CentOS Stream 9 Essentials: Learn to Install, Administer, and Deploy CentOS Stream 9 SystemsNo EverandCentOS Stream 9 Essentials: Learn to Install, Administer, and Deploy CentOS Stream 9 SystemsAinda não há avaliações
- Lotus Domino Interview Questions, Answers, and Explanations: Lotus Domino Certification ReviewNo EverandLotus Domino Interview Questions, Answers, and Explanations: Lotus Domino Certification ReviewAinda não há avaliações
- Comparative Study of Google Android, Apple iOS and Microsoft Windows Phone Mobile Operating SystemsDocumento6 páginasComparative Study of Google Android, Apple iOS and Microsoft Windows Phone Mobile Operating SystemstudocrisAinda não há avaliações
- Configuring Cisco Stackwise VirtualDocumento22 páginasConfiguring Cisco Stackwise VirtualtudocrisAinda não há avaliações
- LLDP-MED and Cisco Discovery Protocol - White - Paper0900aecd804cd46d PDFDocumento13 páginasLLDP-MED and Cisco Discovery Protocol - White - Paper0900aecd804cd46d PDFtudocrisAinda não há avaliações
- GNS3 Lab Configuring ASA Using ASDMDocumento6 páginasGNS3 Lab Configuring ASA Using ASDMtudocrisAinda não há avaliações
- Cisco IPSec Easy VPN Server Configuration GuideDocumento6 páginasCisco IPSec Easy VPN Server Configuration GuidetudocrisAinda não há avaliações
- Configuring VRF LiteDocumento12 páginasConfiguring VRF Litetudocris100% (1)
- Understanding MSTPDocumento26 páginasUnderstanding MSTPtudocrisAinda não há avaliações
- L2VPN ArchitecturesDocumento651 páginasL2VPN Architecturestudocris100% (3)
- Understanding MSTPDocumento26 páginasUnderstanding MSTPtudocrisAinda não há avaliações
- Number Theory and Public Key Cryptography: SyllabusDocumento26 páginasNumber Theory and Public Key Cryptography: SyllabusGeethanjali KotaruAinda não há avaliações
- BSI CyberSecurity ReportDocumento11 páginasBSI CyberSecurity ReportJeya Shree Arunjunai RajAinda não há avaliações
- BV SessionID @@@@1894608536.1344507463@@@@& BV EngineID CcdhadfhhhjihgjcefecehidfgmdfimDocumento1 páginaBV SessionID @@@@1894608536.1344507463@@@@& BV EngineID CcdhadfhhhjihgjcefecehidfgmdfimAshish TripathiAinda não há avaliações
- Payroll Management SystemDocumento101 páginasPayroll Management SystemManjeet Singh50% (2)
- CSF Form UpdatedDocumento1 páginaCSF Form UpdatedppAinda não há avaliações
- Cyber Security Analysis of Internet Banking in Emerging Countries: User and Bank PerspectivesDocumento12 páginasCyber Security Analysis of Internet Banking in Emerging Countries: User and Bank PerspectivesRebecca BolledduAinda não há avaliações
- Verizon Split Data Routing Dual APN OverviewDocumento5 páginasVerizon Split Data Routing Dual APN OverviewVinit PatelAinda não há avaliações
- Extreme Networks Summit 400-48Documento1.194 páginasExtreme Networks Summit 400-48hdinformatica100% (1)
- Junos NAT ExamplesDocumento14 páginasJunos NAT ExamplesWerner ViljoenAinda não há avaliações
- Ee 1c Lesson 8 Auxiliary SystemDocumento9 páginasEe 1c Lesson 8 Auxiliary SystemRodrigo BabijisAinda não há avaliações
- Thesis On Palmprint RecognitionDocumento8 páginasThesis On Palmprint Recognitionlisadavidsonsouthbend100% (2)
- 9.3.2.10 Packet Tracer Lab Walk ThroughDocumento5 páginas9.3.2.10 Packet Tracer Lab Walk Throughjstring69Ainda não há avaliações
- Oracle® Hyperion Data Relationship Management: Administrator's Guide Release 11.1.2.2Documento132 páginasOracle® Hyperion Data Relationship Management: Administrator's Guide Release 11.1.2.2Richa SrivastavAinda não há avaliações
- Prices and Stocks Subject To Change Without Prior Notice, Please Check With Our Branches. .Documento3 páginasPrices and Stocks Subject To Change Without Prior Notice, Please Check With Our Branches. .ihasakevinsAinda não há avaliações
- Windows XP TweaksDocumento11 páginasWindows XP TweakswayneAinda não há avaliações
- Iso/iec 7812Documento2 páginasIso/iec 7812darezzo.guido0% (1)
- Skibell 2002 Computer HackerDocumento21 páginasSkibell 2002 Computer HackerMaryam AbpakhshAinda não há avaliações
- Gemmw: Mathematics in The Modern World Module 5: Cryptography Learning OutcomesDocumento15 páginasGemmw: Mathematics in The Modern World Module 5: Cryptography Learning OutcomesDANIAinda não há avaliações
- Challan PDFDocumento1 páginaChallan PDFPINAKI BISWASAinda não há avaliações
- McMillen v. Hummingbird Speedway, Inc. (Pa. Ct. of Common Pleas Sept. 9, 2010)Documento8 páginasMcMillen v. Hummingbird Speedway, Inc. (Pa. Ct. of Common Pleas Sept. 9, 2010)Venkat BalasubramaniAinda não há avaliações
- Guide Renewal PDFDocumento103 páginasGuide Renewal PDFka baraAinda não há avaliações
- Appendix A: Introduction To Cryptographic Algorithms and ProtocolsDocumento80 páginasAppendix A: Introduction To Cryptographic Algorithms and ProtocolsDipesh ShresthaAinda não há avaliações
- Principles of Information Security, Fifth Edition: Security Technology: Firewalls and VpnsDocumento65 páginasPrinciples of Information Security, Fifth Edition: Security Technology: Firewalls and VpnsCharlito MikolliAinda não há avaliações
- Shibboleth2 IdP Setup CentOSDocumento17 páginasShibboleth2 IdP Setup CentOSir5an458Ainda não há avaliações
- Using GSKit Tool and IHS-WebSphere Certification ProcessDocumento8 páginasUsing GSKit Tool and IHS-WebSphere Certification ProcessvaraAinda não há avaliações
- 025 - TRA - Grouting Works - Rev 1Documento3 páginas025 - TRA - Grouting Works - Rev 1Rachel Flores100% (2)
- 004 Electrical ClydeDocumento182 páginas004 Electrical ClydeSaurabh Kumar ThakurAinda não há avaliações
- Triumph & Despair - Starship Layout (Firespray)Documento1 páginaTriumph & Despair - Starship Layout (Firespray)CrazyCaseyAinda não há avaliações
- Pfleeger Security in ComputingDocumento87 páginasPfleeger Security in ComputingMuhammed Shafi K PAinda não há avaliações
- Navodaya Vidyalaya Samiti: NVS1997M09382 Employee Id: App No. 590409Documento2 páginasNavodaya Vidyalaya Samiti: NVS1997M09382 Employee Id: App No. 590409Nandkishor LanjewarAinda não há avaliações