Escolar Documentos
Profissional Documentos
Cultura Documentos
Full Text
Enviado por
kak0f0nieDescrição original:
Direitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
Full Text
Enviado por
kak0f0nieDireitos autorais:
Formatos disponíveis
Ethics Inf Technol (2009) 11:163174 DOI 10.
1007/s10676-009-9201-2
ORIGINAL PAPER
The importance of privacy revisited
Norman Mooradian
Published online: 14 July 2009 Springer Science+Business Media B.V. 2009
Abstract James Rachels seminal paper Why Privacy Is Important (1975) remains one of the most inuential statements on the topic. It offers a general theory that explains why privacy is important in relation to mundane personal information and situations. According to the theory, privacy is important because it allows us to selectively disclose personal information and to engage in behaviors appropriate to and necessary for creating and maintaining diverse personal relationships. Without this control, it is implied, the diversity of relationships would diminish; relationships would atten out, we might say. The aspect of the paper that addresses information ows (what I refer to as his information privacy theory) has been of particular interest to computer information privacy theorists. Despite its continued importance to computer privacy theorists, however, the information privacy theory appears to be contradicted by recent developments in computing. In particular, since the publication of Rachels paper we have seen an extensive amount of personal information collected. Further, recent developments in computing falling under the heading of social computing have brought about a new wave of personal information creation and collection. This paper will reassess and resituate Rachels information privacy theory in light of these developments. I will argue that the increasing collection of personal data will not atten relationships as the information privacy theory predicts because such data lack contextual factors important to Rachels general theory. The paper will conclude by pointing to some areas where Rachels general
theory and where his information privacy theory will continue to be relevant. Keywords Personal information Privacy Personal relationships Social computing Friendship Abbreviations IPI Institution specic personal information SPI Socially sensitive personal information BPI Biographical personal information FERPA Family educational rights and privacy act VPPA Video privacy protection act HIPAA Health insurance portability and accountability act GLBA Gramm leach bliley act
Introduction James Rachels seminal paper Why Privacy Is Important remains one of the most inuential statements on the topic. While the paper addresses privacy in general, it has been widely anthologized in texts on computer information ethics, thus giving it the status of a starting point in the study of computer information privacy.1 The central claim of Rachels paper is that privacy is a precondition for maintaining the diversity of personal relationships that people value. Personal relationships, Rachels argues, are constituted by certain kinds of behaviors and certain kinds of exchanges of information. Individuals need to be able (a) to control or restrict access to themselves and (b)
1 For example, Quinn (2009), Johnson (2001), Ermann et al. (1997), Johnson and Nissenbaum (1995).
N. Mooradian (&) Information Management and Compliance, CookArthur Inc., 575 N. Central Avenue, Upland, CA 91786, USA e-mail: nmooradian@cookarthur.com
123
164
N. Mooradian
restrict and control access to information about themselves in order to cultivate and maintain personal relationships. Rachels theory can be broken down into two parts. Part (a) can be described as theory about personal access and space privacy, while Part (b) can be described as a theory about personal information. (When referring to part (a), I will use the label, access privacy theory, and when referring to part (b), I will use the phrase information privacy theory.)2 For writers in the area of computer information privacy, Rachels information privacy theory, has been important because it has been interpreted as offering a way to explain why the accelerated collection of mundane personal information by computer information systems should be viewed with concern. In the case of certain kinds of information, such as medical and nancial information, there has been considerable agreement that their unrestricted collection, processing and dissemination threaten a number of strong interests and rights. However, in the case of non-sensitive, ordinary personal information, no such agreement exists and arguments for restrictions on data collection and sharing have been harder to make. In the computer information privacy literature, Rachels information privacy theory has been seen, along with political autonomy and Fourth Amendment considerations, as a way to ground arguments for greater restrictions over data collection and sharing. (See, Johnson 2001) Because computer information systems collect, store, process and distribute such information, Rachels information privacy theory has appeared particularly relevant to information privacy in the context of computer information systems. The basic idea is that, if control over personal information is essential to maintaining a diversity of personal relationships, loss of control should lead to a reduction of this diversity; it should atten out the different types of relationships or reduce their number. The objective of this paper is to reconsider the role Rachels information privacy theory has had in the literature on computer information privacy. What prompts this reconsideration is the fact that, in the three decades since Why Privacy Is Important was published, we have seen an explosion in information systems, personal computing, and the creation of the World Wide Web. Further, in recent
Rachels does not make these distinctions himself, as they have been identied in the computer information privacy literature by subsequent. Further, these two broad categories of privacy have been further elaborated by such writers as Solove (2008), Nissenbaum (2004), and De George (2003). For our purposes it is sufcient to note that Rachels theory does have a component that address information privacy and that it can be isolated by his intent to explain the importance of privacy in relation to ordinary information as opposed to medical and nancial information. Further, it is this element of the theory that has interested writers in the area of computer information privacy.
2
years, we have seen the emergence of social computing sites and applications such as Facebook, MySpace, YouTube, and uncountable blogging pages. Once conned to government computer systems, personal information now lives ubiquitously in traditional business systems, Web pages, and personal computers. One would have expected, therefore, that concern about personal relationships, and, specically, concern about maintaining a diversity of kinds of personal relationships, would be in evidence in many quarters. However, this has not come to pass. There is, as of yet, no widespread concern about the threat to diversity in relationships. In fact, users of social networking sites often express the belief that such systems have expanded the kinds and numbers of relationships they are now able to pursue. This raises the question whether Rachels theory of information privacy should continue to be given the centrality it has been given in the computer information privacy literature.
Structure of the paper In this paper, I will reassess the relevance of Rachels information theory in light of current developments in information systems and their uses, focusing especially on the rise of Web 2.0 technologies and uses. I will begin by reviewing Rachels general theory, though the focus will be on the aspects of the theory that concern the value of personal information. Rachels theory should, I will contend, predict that diversity in relationships will be threatened by increases in the collection and distribution of personal information. Having laid out his theory, I will then consider a challenge to it that claims that its prediction of attening personal relationships has not been borne out; that the continued existence of diverse relationships in the face of massive amounts of data creation and collection shows that Rachels information privacy theory has been refuted or at least denuded of much of its force. In light of this argument, I will consider how the explosion in Web 2.0 technologies bears on Rachels information privacy theory. In particular, I will look at social computing, broken down into the areas of and social networking and blogging. After summarizing recent developments in these areas, I will turn to another trend in computing, namely, the aggregation of data, and consider how it, in combination with social computing, poses increased privacy risks. With these recent developments documented, I will turn to a reassessment of Rachels information privacy theory. I will argue that despite the explosion of personal information creation and collections, as well as the increasing aggregation of data, we should not expect to see a decrease in our ability to maintain diverse relationships. My argument will be based on the
123
The importance of privacy revisited
165
importance of contextual and modal factors, in relation to personal information, and the importance of physical presence. The paper will come to a close with a re-situating of Rachels general theory, as well as his personal information privacy theory. I will argue that, even though Rachels seminal paper fails to account for the problems that arise from data collection and aggregation, it still has application to current information practices in two areas. First, his insight into the connection between control over access to oneself and ones spaces and personal relationships is relevant to the problem of surveillance. Second, his information privacy theory has application to certain aspects of social computing in relation to their architecture and feature sets. I will suggest that his theory sheds light on how privacy issues related to these architectures are connected to creating and maintaining personal relationships within social computing environments.
Rachels theory The goal of Rachels paper is to answer the question posed in its title, i.e., why is privacy important. More precisely, he attempts to explain our sense of privacy and its importance in normal, everyday circumstances where nothing of great importance seems to be at stake if a particular piece of personal information is disclosed to a person or entity that does not have a legitimate interest in that information or a particular person is observed carrying out his or her private life during its most quotidian moments. By explaining the importance of privacy with respect to mundane information and situations, Rachels believes he will have provided an account of the importance of privacy not derivative from independently speciable and familiar rights or interests such as a right to or interest in receiving healthcare or in gaining and maintaining employment.3 To clarify his thesis, Rachels provides a few examples of the kinds of information and situations he is not concerned with. His examples of non-mundane information, where an independently speciable right or interest is at stake, include medical and nancial and information, as well as socially embarrassing situations and information.4 The problems with disclosure of such information, Rachels notes, are easy to explain in terms of the relevant interest or right (325). Disclosure of medical information can lead to exclusion from a medical plan or loss of an opportunity for
3
Whether his account, which appeals to the enabling role privacy plays in forming diverse relationships, succeeds in providing a more independent footing for privacy than those that appeal to health, nancial need, and other interests, is a topic for another discussion. 4 Pages 324325.
employment. Disclosure of nancial information may have similar consequences. Disclosure of potentially embarrassing information about, for example, ones sexual practices, can injure the persons reputation or social standing, (even if these practices are considered acceptable or normal by the rest of society). Rachels account of the importance of privacy in relation to mundane information and situations is well known, so I will summarize it briey. Control over access to ourselves and information about ourselves is justied by virtue of the enabling role this control plays in our ability to create and maintain the diversity of social relations that we count as part of a good life. Such social relationships include that of being a father, mother, daughter, son, wife, husband, friend, business associate, teammate, etc. These relationships are dened by characteristic behaviors, attitudes, and certain kinds of exchanges of information. Different types of relationships call for (and are in part dened by) the giving and withholding of certain kinds and amounts of personal information. Friendship requires disclosures about ourselves that, say, a business relationship does not. Disclosing our hopes, dreams or disappointments to a friend is appropriate and expected in the case of friendship, but not in the case of a business relationship (unless it has evolved into a friendship). A putative friend to whom such information was not disclosed, where it had been disclosed to others, could justiably question whether he or she was really considered a friend by the other. In order for persons to have and sustain such relationships, intrusions or invasions of privacy that undermine our ability to engage in behaviors constitutive of or critical to these relationships need to be prohibited or limited. Also, disclosures and information exchanges need to be restricted to the parties participating relationship. In the case of behaviors, individuals need to be able control or restrict access to themselves and the spaces in which they conduct their relationships. If they do not have such control, they may be unable to engage in the behaviors constitutive of the specic kind of relationship. There are two reasons why such behaviors might be constrained by a lack of access privacy. First, they may, for emotional reasons, be inhibited with respect to the behavior in a certain way if access privacy is not provided. Second, the behavior may, in itself or derivatively, provide knowledge of the person, which knowledge would normally be reserved to parties of the relationship. Some of this knowledge will be knowledge by acquaintance. Some of it will be convertible into knowledge by description.5 Still, some of it will be an integral part of the experience of the mutually engaged in behavior. For all these reasons,
5
For a detailed discussion of descriptions and personal information, see Van Der Hoven (2008, pp. 307310).
123
166
N. Mooradian
individuals need control over access to themselves and their spaces. This is the part of Rachels theory that I labeled above as his access privacy theory. Individuals also need to be able control the ow of information about themselves. The reason is that relationships are based on the exclusive and selective exchange of information between parties to the relationship. If individuals lose control over their personal information, it will undermine their ability to make the appropriate selective disclosures or communications. Of course, it will not prevent them from actually engaging in the relevant communicative act. However, loss of control over personal information will undermine their ability to selectively and exclusively communicate information about themselves. Once disclosed to third parties or published to the general public, the individual loses the ability to tell a friend (for example) something about himself or herself the friend does not know but, in the role of friend, should know, and what others outside of the role of friend should not know, but, in fact, do know. The information thus loses its value to the individual with respect to the information exchanges that constitute the relationship in question. This is the part of Rachels theory that I labeled as his information privacy theory. Rachels thus provides an account of different aspects of privacy that can be broken into at least two broad categories: (a) control over access to oneself and ones spaces and (b) control over access to ones information. It is the latter part of the theory, the information privacy theory, that has wielded such inuence in the computer privacy literature. For further terminological convenience, I will introduce some general labels meant to cover the different kinds of information discussed in the paper.6 The labels are not exclusive, but should manage to capture a central feature of the information in question.7 First, it has been widely noted that certain kinds of information are at the heart of institutional relationships (Johnson, p. 123). Some of Rachels examples above of non-mundane information, namely, medical and nancial information, fall into this category. Such information is created and managed for the sake of the activities of their respective elds. How that information is controlled affects the ability of the individual to receive services within the given area and sometimes outside of it. I will call this institution specic personal information (IPI).
The other kind of non-mundane information that Rachels wants to set aside, embarrassing information, I will simply label socially sensitive personal information (SPI). The two broad categories of IPI and SPI account for a good deal of the information about which there are privacy concerns. They are not exclusive, however, as, for example, certain medical information might carry a stigma per se or by implication to its causes. Also, certain kinds of SPI might (by being disclosed) lead to disadvantages vis a vis a particular institution. What is important for our purposes is that these two kinds of information are not relevant to Rachels thesis. The importance of IPI and SPI are explainable in terms of their institutional and social implications. Rachels, by contrast, is interested in what I will call biographical personal information (BPI). BPI consists of any mundane facts about you that tell something about who you are, what you do or have done, where you have been, etc. Of course, so dened, this broadest class of information includes the others. So, to make this category useful it is necessary to dene it as including all mundane facts about a person, less those facts contained in the other two categories.8 Using this terminology, we can frame the issue of this paper more clearly. Rachels information privacy theory has played a central role in the computer information privacy literature. The reason is that is it precisely the kind of information that I labeled BPI that computer information systems collect, store, process, and distribute and it is precisely these activities that have generated such controversy. In the United States, legal structures exist for some important classes of IPI (FERPA, VPPA, HIPAA, GLBA, etc.), but BPI remains particularly problematic because of its disparate, pervasive, and (taken in isolation) seemingly innocuous character. It remains relatively unregulated in the United States, especially in the private sector.9 Civil law also offers spotty protection.10 With this in mind, let us turn to a challenge posed to Rachels information privacy theory.
Rachels does not offer a classication of types of personal information. Rather, he offers a number of suggestive examples, as indicated above, to help frame his concerns. 7 These labels are meant to apply to the kinds of information Rachels discusses, though of course, he does not use them himself.
This denition is not a mere contrivance. Most of the debate about personal information privacy concerns mundane information such as is generated by purchase transactions, mobile phone records, including GPS positioning, Web pages browsed, etc. I use the term biographical for all of this diverse data because, taken together, it can be used to tell a story about ones life history or segments of it. 9 The situation in Europe is different. The EU Data Directive 95/46 does in fact encompass BPI, as does the Safe Harbor agreement between the EU and United States. 10 Solove (2007, 2008).
123
The importance of privacy revisited
167
A challenge to Rachels: the coexistence of masses of BPI with diversity in relationships Writing in the late 1990s, Deborah Johnson observed that vast amounts of personal information existed in databases and computer information systems and yet despite this fact people seemed to be able to maintain a diversity of personal relations in a way that Rachels theory predicted they could not. She says: Rachels seems right about the way information affects relationships. We control relationships by controlling the information that others have about us. When we lose control over information, we lose signicant control over how others perceive and treat us. However, while Rachels seems right about this, his analysis does not quite get at what is worrisome about all the information gathering that is facilitated by computer technology. That is, the information gathering and exchange that goes on via computer technology does not seem, on the face of it, to threaten the diversity of personal relationships each of us has. For example, huge quantities of data now exist about my purchases, phone calls, medical condition, work history, and so on, I am able to maintain a diversity of personal relationships. (pp. 121122) Johnsons challenge should be of concern. Since the time of her writing, data collection has intensied and diversied, and it has done so with respect to the type of personal information I labeled BPI. In-store transactions are increasingly tracked using store cards and other collection methods. More and more consumer transactions are carried out online, which means that even more and richer transactional data is being collected. Cell phones now incorporate GPS tracking in order to locate cell phone users in emergency situations. Surveillance cameras exist in more and more places and, being linked with recognition software, are capable of recognizing license plate numbers and letters (for example) and linking them back to computer databases, thus identifying our comings and goings in certain locations. Despite all this, there is no evidence that people are unable to maintain the diversity of personal relationships that Rachels wrote about. In addition, Johnson seems correct to say that the worry that such information collection has engendered concerns problems of control and harms that come from lack of control. It is not the diversity of relationships, in general, that is threatened by this lack of control. Rather, it is the existence or health of particular relationships that is at risk. Disclosure and dissemination of various kinds of personal information can easily injure a persons reputation and spoil some of his or her important relationships. Further, this information might be precisely the kind of information
that a given person would have preferred to keep to himself or herself and would have therefore not disclosed within the context of any of his or her personal relationships. The fact of increased ows and stores of personal information, especially BPI, should cause us to revaluate the relevance of Rachels information privacy theory to the concerns of computer information privacy theorists. To do so properly, however, we should consider not just recent history in the realm of data collection and processing but also current trends and near term possibilities. In particular, the very rapid rise of social computing in the context of Web 2.0 environments has opened the channels to massive amounts of new, personal information that was hitherto far out of the reach of traditional information systems. The information collected and exchanged via social network sites such as Facebook and MySpace should surely be relevant to Rachels theory and we would be remiss not to consider it. Also, while available in sporadic and nascent form, the aggregation of BPI is still in its early stages. While one can Google a person (that is, search the Web by entering their name in a search engine) and collect an impressive scattering of BPI tidbits, the real aggregation is still in the ofng as far as the average person is concerned. But aggregation is a signicant area of concern in respect of privacy as Daniel Solove has indicated by identifying it as one of the central problem areas in privacy law.11 Hence, we should look carefully at how increased and improved aggregation of BPI might affect, one way or another, the relevance of Rachels theory to information privacy theorists. The next two sections of this paper will describe these recent developments in information systems and computing. The next section will discuss social computing, and, in particular, social networks and blogging. The following section will take up the issue of aggregation.
Social computing The rise of social computing in the context of Web 2.0 environments has dramatically altered the information privacy landscape. While the designation, Web 2.0 may be part marketing aspiration and part technical, it suggests the idea of a changed from static Web pages, portals and Web interfaced database applications to a new form of interactive, personal Web computing that allows internet users to engage in various forms of self-publishing. Two central components of the Web 2.0 experience are blogging and social networking sites. Blogging is a source for various forms of self expression. While political opinion makes up the lions share of blogging, very personal information is also a common theme, with many blogs
11
Solove (2008, p. 117).
123
168
N. Mooradian
being the equivalent of digital diaries. Social networking sites provide for liking of personal proles and pages among ends. Blogging and posting of images and videos comprise a large part of the content of social networking sites, as does messaging of various sorts. Unique to social computing, however, are the linkages of friends, which linkages are informational and functional. That is, they display the structure of relationships and they propagate information across these structures. Daniel Soloves recent book, The Future of Reputation: Gossip, Rumor and Privacy on the Internet, is an excellent guide to this new privacy terrain. I will take a few examples from it by way of illustration. Blogging Blogging is a channel for self disclosure for many people. It serves as a digital diary for many persons, with the difference that in many cases it is available to anyone with internet access. Solove recounts the story of a blog called the Washingtonienne, in which a young woman working on the Hill in Washington D.C. posted regularly about the personal details of her daily life, including her work and her attitude towards it, as well as her intimate relationships. Having started up a relationship with an attorney, she blogged about the intimate details of their sexual encounters and some of his preferred practices. When he became aware of this, he angrily broke off the relationship.12 Second, blogging is often an avenue for third party revelation, often by strangers, of selective personal information. Often, a person is captured in an embarrassing or shameful moment by a digital camera. Sometimes a persons actions or alleged actions are blogged about by others. Another story recounted by Solove concerns a Korean girl who allowed her dog to defecate on a subway and did not clean up after it. This act (or omission, as the case may be) was captured by a digital camera and a picture of her was posted on the Web. She became the object of scorn by a multitude of bloggers and suffered psychological trauma as a result.13 Blogging is on the rise. There were about 50 blogs in 1999, a few thousand more in 2000, more than 10 million in 2004, and more than 30 million in 2005. By the end of July 2006 there were approximately 50 million blogs. (p. 21) Presumably most bloggers understand that their postings are public and that they are accessible by millions of internet users. However, some may not and most, one may
12 13
speculate, have not fully realized how available and lasting their disclosures will be and how out of their control they will remain. They may also be unaware of the extent and limitations of the existing legal protections of such information, especially given the recent legal immunities provided to internet access, service and content providers. (In particular, section 230 of the CDA.) Social networks The second leg of social computing is social networks. There were only a few social networking sites in the mid 1990s, while now there are a few hundred, with MySpace, Facebook, and a few others being the most well known (Solove 2007, p. 24). Social networks are venues for extensive and rich personal information ows and disclosures. Registered users are given a set of pages in which they can list prole information (e.g., name, gender, education, residence, marital status, sexual preference, political afliation, and religious identication), post photos and links, blog, send messages to friends, chat, etc. Most signicantly, users pages often list the users friends (individuals whom the user explicitly added as a friend). On some sites, by clicking on a given friend, a user can see that persons list of friends. Another feature indicates that a friend is held in common with another friend. (Examples from Facebook.) Social networking sites provide some privacy protections that generic blogging lacks. Blogging is an act of publication to an audience. The audience can consist of the entire Web or a group formed around a common interest. Social networking sites provide a set of privacy controls (which vary from site to site) that allow users to restrict their pages to friends and to restrict what is displayed to friends. However, these sites, because of their architecture and nomenclature (take the name MySpace) offer a false sense of security to many. Neophyte users are often unaware of the privacy controls and may commit some eradicable faux paux before gaining mastery of them. Most users remain unaware or think little about the fact that all their personal information is housed on servers, often owned by corporations, and that these corporations are only bound (if that is not too strong a word) by their privacy policies. Since many sites are commercial enterprises that have a business model based on harvesting personal information for marketing purposes, many users half cogitated belief that what happens on these sites stays on these sites is, to put it mildly, naive. Finally, social networking sites pose a unique risk that, tre, should be because it is related to their raison de obvious to their users, but most likely is not fully considered. The purpose of social networking sites is to create communication channels and linkages between users.
Solove (2007, pp. 5054). Solove (2007, pp. 14).
123
The importance of privacy revisited
169
Many sites make these linkages visible to users with the result that it is easy to see with whom a given user associates. Also, as personal information is communicated across social network channels, it will often nd its way to unintended recipients. Now, one might point out that this happens in the physical social world, where gossip passes from person to person. But as Solove notes, in the physical social world, our social circles tend not to intersect and for the most part information stays within circles.14 Social networking sites typically do not replicate these semi exclusive circles but rather expand the circumference of the users one circle. This architectural fact has privacy implications that many users surely fail consider, not least of which is that messages and information available within the protected canals of the social network site can always be thrown over the fence into the ocean of the World Wide Web. One therefore has to be concerned that users of social networking sites may be inclined to volunteer much more information about themselves than they otherwise would if they understood the technical architecture, business model, and legal context that characterize most of these sites.
Aggregation The other more recent, though less developed, trend in computing that is of relevance to Rachel information privacy theory is the aggregation of data. Aggregation is the bringing together into a single data structure or interface data produced from a variety of different sources. Linking data such as names and social security numbers allows personal data to be aggregated. At its best, aggregation does more than just collect personal information. It brings it into a usable structure that eliminates duplication, lters out irrelevant information, calculates statistics, and summarizes data to allow for relatively quick comprehension. As mentioned above, anyone Googling a persons name for the rst time gets a shocking glimpse into the future of aggregated personal data. However, it is only a glimpse. What is collected typically consists of highly selective, mainly self published comments from a person or relatively public facts about that person. Much of it is of little interest to anyone, including the data subject him or herself.15 If aggregation techniques improve, however, this could change the privacy picture with respect to BPI quite dramatically. Taken by themselves, certain pieces of
14 15
information do not communicate much about a person. Taken together, however, they could communicate a great deal. Given all the BPI now available thanks to the increasing quantities of transactional data harvested by commercial applications and now the increasingly massive amounts of personal information produced through blogging and social networking sites, it is easy to imagine that not far off in the future we will see more and more successful data aggregations. There are challenges to this, as data is produced by diverse sources and largely unstructured. But as the commercial value of this data becomes apparent, we can expect that serious efforts will be made to harvest and process it with the goal of producing useful personal data aggregates or digital dossiers. Technical challenges can be addressed with data mining programs, human intervention, and improved front end structuring using XML and other data formats. Further, existing legal structures do not offer much protection to BPI, so it is not implausible to believe that entrepreneurial information technology companies will 1 day offer very comprehensive digital dossiers at a reasonable price. These dossiers might be constructed on the y as the product of a search, delivered by order after human intervention is added to produce a more accurate and readable result, or delivered from a massive, repository of constantly updated dossiers. Such a service would save people quite a lot of time that they would otherwise spend Googling names and shing around social networking sites, and it would likely deliver far more information in a more comprehensible form. In the next section of this paper, we turn to reassessing the relevance of Rachels information privacy theory to computer information privacy issues.
Reassessing the theory As is evident from above, the sort of information divulged through a great deal of blogging in and outside of the context of social networking sites is the sort of personal information that is at the center of Rachels information privacy theory, which information I have labeled BPI. If this sort of information were to be captured and aggregated into a useable form so that comprehensive personal proles for just about everyone were to be easily accessible to just about anyone, Rachels theory concerning the value of BPI would lead us to expect that diversity in personal relationships would disappear. Persons without any deep relationship with each other would have access to a detailed, current biography lled with the most important facts and events in the persons life. But this is just the kind of information that, according to Rachels, must be meted out with caution in order to avoid its devaluation as the
Solove (2007, pp. 176181). For example, among the things turned up by a Google search on my name is a question I asked about what turned out to be a timing problem with a Visual Basic script I wrote to access an Oracle database. It is not embarrassing information, but not at all interesting to anyone.
123
170
N. Mooradian
exchange currency of personal relationships. To quote Rachels: Suppose I believe that someone is my close friend, then I discover that he is worried about his job and is afraid of being red. But, while he has discussed this situation with several other people, he has not mentioned it at all to me. And then I learn that he writes poetry, and that this is an important part of his life; but while he has shown his poems to many other people, he has not shown them to me. (p. 328) Any good digital prole worthy of the name would surely contain facts such as this, as well as other biographical information such as past relationships, current behaviors etc. that might help explain why the friends job is in peril and why he writes poetry. To engage in hyperbole for a moment, everyone would be an open book to everyone else. If the importance given to Rachels information privacy theory is justied, then, we should expect that the complex structure of relationships would be attened as a kind of personal information egalitarianism emerged. Acquaintances with sufcient motivation to know a person could ramp up quite quickly through diligent study and join his or her ever widening circle of friends and condents. It is doubtful, however, that this comprehensive digital dossier, whose specter I have raised, will undermine diversity. It can certainly be expected to harm relationships as Johnson predicted and Solove has documented. Already, one can hear anecdotal stories about how third parties have found out things about others that they were not intended to know; parents have logged onto social networking sites to learn about their childrens friends and employers have done the same to learn about their prospective employees. Rumor and gossip are magnied on the internet as Solove contends and a variety of information types such as digital video capture people during importune moments and infelicitous acts. Relationships of various sorts can be greatly harmed if the concerned party becomes apprised of such information, as it is becoming increasingly likely he or she will. The problem of contextual and modal variables It is doubtful, however, that relationships will atten out in the manner described above even as more BPI becomes available and even if aggregation rises to the level of making digital dossiers pervasive. The reason, I believe, is that Rachels general theory, which attempts to address a number of kinds of intrusions, presupposes certain contextual and modal variables that do not extend to the masses of BPI stored in computer information systems. These include caring, affection, trust, concern, and other
such emotional factors. This, in the end, undermines his theorys usefulness as a theory of information privacy, even if he might have hoped that it would have this application as some of his key examples suggested he did.16 Privacy theorists such as Reiman17 raised the question of contextual and modal variables early on. While Reimans criticism may be uncharitable to Rachels broader account, it does capture the key weakness of the information privacy theory. A brief summary of Reimans criticism should put the issue in perspective. In his 1976 paper Privacy, Intimacy, and Personhood, Reiman criticized Rachels theory on the grounds that it left out the essential contextual variable of caring. For Reiman, it is this contextual variable of caring that gives meaning to the exchange, not the information per se. Caring is the primary determinant of the relationshipcreating character of the exchanged, with the information content being secondary (though not unimportant, one would assume). Thus, the most intimate details of a persons life could be told to a psychoanalyst without creating an intimate friendship. And this is not because the exchange is asymmetrical. Reiman imagines two psychoanalysts analyzing each other in their role as professionals. What is missing in the information exchange between analyst and patient is caring, and not just caring simpliciter, but the sort of caring that denes friendships. (Certainly a psychoanalyst would show and feel professional care and concern for a patient, but this is not the same as the caring that characterizes friendship.)18 There are modal variables as well. The information privacy theory does not give proper emphasis to the fact that the exchanges are communication acts with modal characteristics. What is important is that I tell you something, not that you acquire that particular information about me.19 Hence, to return to Rachels example quoted above, I might be miffed that you did not tell me about your poetry. What miffs me, however, is not that the information is out there and I dont have it, but rather, you did not communicate it to me with the intent of doing so. If I learned from some posting on a blog site that you write poetry and it is clear from the posting that the information was gained through observing or surveilling you, but you later tell me that you write poetry, I would still be quite glad to learn this from you and our relationship would proceed nicely.
16 17
Pages 324325. Reiman (1976). 18 To be fair to Rachels, his general theory does, I believe, have room for the emotional context that Reiman believes is missing. However, Reimans criticism does apply to the information privacy theory, which is the part of his theory that has been seen as so important to computer information privacy theorists. 19 I owe this point to Laurie Schrage from a discussion of an earlier draft of this paper.
123
The importance of privacy revisited
171
Likewise, if you told me you were gaining weight, I would also be glad that you conded in me, even though the fact conded may be available to public observation. The importance of these contextual and modal variables gives us reason to believe that the continued collection of BPI will not, in fact, atten out relationships, as Rachels information theory would predict. These variables are an integral part of the relationship building process. They are constituent factors in the behaviors and communicative acts that dene different types of personal relationships. But it is precisely these factors that are absent in relation to the masses of BPI collected, stored, and processed. The extension of Rachels general theory to BPI thus fails for reasons that ground its plausibility in relation to privacy claims for certain kinds of behaviors, communicative acts, and personal situations.20 A similar problem can be raised by examining the role of shared space and physical presence in the creation of friendships. The next section of the paper will address this issue. The problem of physical presence In addition the sort of contextual and modal factors of information exchanges discussed above, there is another reason why the existence of the digital dossier should not be expected to atten out relationships. The reason is that much of the relationship building information that is exchanged between persons in a friendship or some other type of intimate relationship requires physical presence. The parties to the relationship must share physical spaces for appropriate amounts of time to share personal information critical to their relationships. This is accounted for in Rachels space privacy theory, but as with the contextual and modal factors described above, it is absent from BPI and its absence undermines the Rachelean information privacy theory. To explain and support this claim, I will draw on a paper by Dean Cocking and Steve Matthews on a different topic, virtual friendship. In their paper, Unreal Friends (2001), they argue that computer mediated personal relationships will lack features essential to friendship. Their argument focuses on text based communications, but its claims and justications are applicable (in varying degrees) to richer multimedia communications. While their argument is meant to cast doubt
20
One might object that too much available BPI might still undermine personal relationships because it might deate the value of an important element in the exchanges, namely, the content. If ends know a good deal of biographical information about each other, they might just run out of things to talk about. This objection fails to take into account that there is always much to talk about, that one can convey ones feelings about any of the known biographical facts and that friends can speak about their shared experiences as they happen, among other things.
on the possibility of pure cyber friendships, it has implications for our understanding of how personal information exchanges contribute to constructing diverse relationships and what aspects of privacy are critically related to this process. As a preliminary to their argument, Cocking and Matthews survey different theories of friendship. Theses include Aristotles Mirror Theory, which they interpret as basing friendship in nding similar traits in another. Also included is an account they call the Secrets View, according to which mutual self-disclosure is the basis of friendship. The third theory they call the Drawing View. On this theory, the basis of friendship is a dynamic, identity forming relation between two persons. Friendship not only allows sharing of information and experience. It is a relationship that shapes and alters the individuals conception of self. As presented, the three theories do not have to be mutually exclusive. The different features and aspects of friendship that they emphasize might be combined into a more comprehensive theory. Further, as the authors note, all three theories require self disclosure of some form, though the Secrets View places self disclosure at its center. The centerpiece of their argument revolves around the idea of interpretation. Whichever view of friendship one takes, the contextual interaction and interpretation of the friends character is essential to the relationship. Friends learn about each other through their mutual involvement and engagement in situations and their reactions to and within these situations. For example, one might be at a party with a friend. His ex-partner arrives. Upon her arrival, the friend begins to look nervous, agitated or depressed. You learn something about his relationship to her from his non-verbal reactions, intonation, or even direct, in context comments. Earlier that night, you might have noticed three pad locks on his door, and on your way to the party you may have observed his reactions to trafc conditions or news on the radio. From this you glean something about his attitudes toward safety, inconvenience brought on by other people, and politics. The important point here is that much if not most of what you learn about a friend comes through his or her in contextually embedded responses, many semi-voluntary or involuntary, to a myriad of events and situations in the physical world. Given the above, we can see that the self-revelation critical to friendship requires physical presence. The friend is invited to share space and time with the other friend. This includes sharing presence in public spaces but also, and more importantly, sharing private spaces. In such spaces friends reveal much about themselves, and much of this revelation is simply in their reaction to things, and is therefore not under their voluntary control. By contrast, Cocking and Matthews argue that Net or cyber friends are excluded from the kind of physical presence that permits
123
172
N. Mooradian
this essential form of self-revelation. Cyber relations, mediated by, for example, messaging, are controlled and ltered. Each person attempts to represent himself or herself in a way that he or she chooses. People select their words carefully and take time to respond to communications so that a controlled and deliberate representation is maintained. Further, even if they wished to disclose much or all of themselves, they could not. First, there is much that they do not know about themselves. The friend described in the example above may not know that he carries feelings for his ex-partner, that he is a bit paranoid about personal safety, and that he is impatient with people. It is only by being with him in the right circumstances that his verbal and non-verbal behavior would clue one in to this. Second, even if the friend were aware of many such aspects of himself, giving expression to them in writing would prove to be too tedious and laborious to be practicable. For these reasons, Cocking and Matthews conclude that cyber friendships are not possible.21 If Cocking and Matthews are correct,22 the sorts of information exchanges that build and maintain personal relationships are not, in the case of intimate relationships, exhausted by those that can be represented by linguistically expressed information. The reasons for this are largely practical. Individuals are simply limited in how much information they can disclose verbally by a variety of constraints. This nding has direct relevance to the question whether the increased capture and aggregation of personal information will undermine diversity in relationships. If BPI does not contain much of the critical information required to build and maintain relationships, we can expect that its existence in massive quantities that it will not bring about an end to this diversity.
data being produced through traditional business transactions, e-commerce, and social computing. There are some aspects of the general theory, and even of the information privacy theory, however, that may have continued relevance as these and new trends continue. Rachels general theory does have something to say about surveillance. Also, the information privacy theory has something to say about social computing, though not what was originally thought important. I will conclude with a discussion issues. Surveillance As mentioned throughout the paper, Rachels offered an explanation of the value of personal access and space privacy, in addition to an explanation of the value of information privacy. (Different privacy theorists will categorize his concerns differently; e.g., De George, Nissenbaum23) Rachels concern with personal access and space privacy is evident in many of his examples. Physical presence and observation loom large in these examples, as does his concern with the sorts of behaviors that are appropriate and necessary for relationships. To take just one example: Again, consider the differences between the way that a husband and wife behave (italics mine) when they are alone and the way they behave in the company of third parties. Alone, they may be affectionate, sexually intimate, have their ghts and quarrels, and so on; but with others, a more public face is in order. If they could never be alone together, they would either have to abandon the relationship that they would otherwise have as husband and wife or else behave in front of others in ways they now deem inappropriate. (330) This aspect of Rachels theory that is concerned with control over access to oneself will have continued relevance as electronic surveillance becomes more pervasive. Digital cameras already pervade private commercial spaces where people shop and spend much of their leisure time. They are also increasingly found in public spaces such as government buildings and even public streets and parks. As people carry out much of their lives in these commercial and public spaces, and therefore undertake to form, build and maintain relationships in these spaces, Rachels theory will have relevance to debates about surveillance. It will not, however, be the only or dominate consideration, as numerous theorists have advanced powerful arguments against surveillance based on conceptions of
23 For example, De Georges (2003) distinctions between space privacy, body/mental privacy, and communication privacy are directly relevant. Also relevant are Nissenbaums Principle 1 concerning government intrusions and Principle 3 concerning intrusions into spaces and spheres deemed private or personal.
Re-situating Rachels theory If my arguments are correct, Rachels theory of personal information privacy fails to capture what is important about BPI and hence cannot be expected to be borne out or vindicated by the ever increasing collections of personal
21
In her paper, Friends, Friendsters, and Top 8: Writing community into being on social network sites, discussed later in this paper, danah boyd, explores the concept of friending within social networking sites. She argues against the belief that friending someone on a social networking site is the equivalent of becoming friends and explores the many purposes and implication of friending within this context. Her ndings, at least initially, are consistent with Cocking and Matthews thesis, and their thesis, in turn, is likely to provide an explanation of some of underlying causes of these ndings. 22 See two recent, separately written papers for further exploration of their thesis, Plural Selves and Relational Identity (Cocking) and Identity and Information Technology (Matthews) in Information Technology and Moral Philosophy.
123
The importance of privacy revisited
173
political and moral autonomy,24 self development, contextual appropriateness25 and other factors. Further, in Western democracies, counter balancing legal structures and institutions such as constitutional restraints on governmental intrusion and strong property rights ensure that many people will have control over their own private spaces and will be able to carry out their relationships there without inhibition, even if public and private spaces prove inhospitable. Still, Rachels insights about the importance of restricted access to the self and its spaces to personal relationships will add another important consideration to the many that have and will be advanced against the encroachments of electronic surveillance technologies. Social networking As mentioned in the discussion of social networking above, social networking sites are distinguished from other Web 2.0 applications in that they make explicit a persons networks of friends and their structures, and they communicate personal information through these structures. They therefore capture new information and pose new risks. While I have argued that the collection and aggregation of this information will not vindicate Rachels theory of personal information privacy, it may be that it has application to some aspects of social computing itself. More specically, it may be that Rachels information privacy theory can be used to illuminate privacy issues that arise within social networks and may help guide architects of those sites.26 As danah boyd has documented, social networking sites are highly mediated environments with architectures that constrain and shape the relationships and norms that arise in association with them. They provide technical affordances that allow users to create site specic relationships that depend upon these affordances. Conversely, they may lack affordances that support a variety of ofine relationships. Her discussion of friending is of particular relevance. As boyd describes: When people login to a social network site, they are required to craft a Prole. This Prole includes information about their demographics and tastes, a self-description Once a user nds a Prole of a friend (or anyone else), they can add them The Friends list typically includes a list of photos or handles with links to that persons Prole. Thus,
24
when users are surng social network sites, they can hop from one Prole to another through a chain of Friendship. Beyond this general description, the details of how Friendship works are site-specic.27 The creation of these friendship links are thus mediated by and structured by the architecture and functionality of the site. Typically, this means that one can easily make a request of another user that your prole be added to his or her list of friends and he or she can easily accept your request. As boyd notes, the reasons for making and accepting friend-add requests vary, some resembling the reasons and motives that people seek out off-line friendships, some unique to social networking environments, and some related to off-line social relations distinct from close personal relations. So, a person might want to add a realworld friend to his or her list; he or she may simply want to connect to other proles to share and learn about various postings and techniques used; he or she may want to attract fans, clients, or create some kind of following for business, political or other purposes. The problem that social networking sites present is that they use the broad category of friend to represent links between user proles. This means that social networking sites offer very crude tools for creating and maintaining diverse relationships. The category of friend does not represent the many kinds of off-line relationships that people would like to represent in social networking sites. Also, to the extent that the linkages between friends creates linkages between their friends lists, channels of communication are extended and hence control of personal information in relation to its intended audience is weakened. As mentioned above, ones circle of friends grows as friends are added, and added to it are their circles of friends. Rachels theory of personal information privacy should have application to this new context. It offers insights into how information ows within social networking sites are related to the creation and maintenance of personal relationships. Since the purpose of such sites is to provide new and enabling venues for social interaction, a theory connecting the value of personal information to relationships should be of interest to theorists and to the developers of such sites (as should the work of other theorists such as Nissenbaum who deal with the relation of the social norms governing information ows). Further, as Rachels notes, his theory is meant to address not only the relationships familiar to a given cultural context, but other cultural contexts and, importantly, new relationships that will arise in new contexts. Social networking sites in particular and Web 2.0 computing and its successors are likely to form a
27
For example, Johnson (2001), Nissenbaum (2004), and Solove (2003), Garnkel (2000), Rosen (2001), and many others. 25 Nissenbaum (2004). 26 Also, to the extent that social networking sites support real time communication and video meetings, surveillance concerns will arise as they do for physical spaces.
Boyd (2006).
123
174
N. Mooradian
new context for social interaction and create new relationships. These relationships will be information based and will consist, in large part, of information exchanges. Some of these relationships may be judged by their participants in terms of the content and quantity of information provided to members of the relationship to the exclusion of persons outside of it. It can therefore be expected that Rachels personal information theory will be of relevance in understanding how privacy is important to the functioning of these sites and the relationships in them, even if it is seen to lose relevance in explaining how information privacy is important to our relationships generally.
References
Boyd, D. (2006). Friends, friendsters, and myspace top 8: Writing community into being on social network sites. First Monday 11:12, December. http://www.rstmonday.org/issues/issue11_ 12/boyd/index.html. Cocking, D. (2008). Plural selves and relational identity. In J. Van Den Hoven & J. Weckert (Eds.), Information technology and moral philosophy. Cambridge: Cambridge University Press. Cocking, D., & Matthews, S. (2001). Unreal friends. In Ethics and Information Technology (Vol. 2). Netherlands: Kluwer Academic Publishers. De George, R. (2003). The ethics of information technology and business. Oxford: Blackwell. Den Hoven, J. (2008). Information Technology privacy and the protection of personal date. In J. Van Den Hoven & J. Weckert (Eds.) Information Technology and Moral philosophy. Cambridge: Cambridge University Press. Ermann, D., Williams, M., & Shauf, M. (1997). Computers, ethics, and society. Oxford: Oxford University Press. Garnkel, S. (2000). Database nation: The death of privacy in the 21st century. Sebastopol: OReilly and Associates. Johnson, D. (2001). Computer ethics. Upper Saddle River: Prentice Hall. Johnson, D., & Nissenbaum, H. (1995). Computers, ethics and social values. Englewood Cliffs: Prentice Hall. Matthews, S. (2008). Identity and information technology. In J. Van Den Hoven & J. Weckert (Eds.), Information technology and moral philosophy. Cambridge: Cambridge University Press. Nissenbaum, H. (2004). Privacy as contextual integrity. Wash Law Rev, 79(1), 119158. Quinn, M. (2009). Ethics for the information age. Boston: Pearson Education. Rachels, J. (1975). Why privacy is important. Philos Public Aff, 4(4), 323333. Reiman, J. (1976). Privacy, intimacy, and personhood. Philos Public Aff, 6(1), 2644. Rosen, J. (2001). The unwanted gaze: The destruction of privacy in America. New York: Vintage Books. Solove, D. J. & Rotenberg M. (2003). Information privacy law. New York: Aspen Publisher. Solove, D. J. (2007). The future of reputation: Gossip, rumor, and privacy on the internet. New Haven: Yale University Press. Solove, D. J. (2008). Understanding privacy. Cambridge: Harvard University Press.
Conclusion If the above arguments are correct, the advent of increased personal data capture and aggregation will not bring about the elimination of or weaken diversity in personal relationships. The reason is that the relationship building characteristics of personal information exchanges include more than the static content of the information. They include contextual and modal variables such as caring, intent, source, and others. Also, they depend upon contextual variables limited to the physical world. Consequently, to the extent that the interest that information theorists have taken in Rachels paper has depended on his theory of the value of BPI, we can expect this interest to wane in the coming years, despite the vast increases in BPI harvesting and processing that are sure to come. Still, the theory does have something to say about social networking and may see revived interest in that respect. Also, Rachels paper did anticipate concerns about the inhibiting effects of surveillance in relation to an important aspect of our lives. We should not be surprised, therefore, to see his paper cited well into the future.
123
Você também pode gostar
- Cybertext Chapter 1 - AarsethDocumento13 páginasCybertext Chapter 1 - AarsethsehomohoAinda não há avaliações
- Cecilia ÅsbergDocumento2 páginasCecilia Åsbergkak0f0nieAinda não há avaliações
- Animation 2006 Manovich 25 44Documento21 páginasAnimation 2006 Manovich 25 44kak0f0nieAinda não há avaliações
- Danger MouseDocumento15 páginasDanger Mousekak0f0nieAinda não há avaliações
- HaroldDocumento23 páginasHaroldkak0f0nieAinda não há avaliações
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNo EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNota: 4 de 5 estrelas4/5 (5783)
- The Yellow House: A Memoir (2019 National Book Award Winner)No EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Nota: 4 de 5 estrelas4/5 (98)
- Never Split the Difference: Negotiating As If Your Life Depended On ItNo EverandNever Split the Difference: Negotiating As If Your Life Depended On ItNota: 4.5 de 5 estrelas4.5/5 (838)
- The Emperor of All Maladies: A Biography of CancerNo EverandThe Emperor of All Maladies: A Biography of CancerNota: 4.5 de 5 estrelas4.5/5 (271)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNo EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNota: 4 de 5 estrelas4/5 (890)
- The Little Book of Hygge: Danish Secrets to Happy LivingNo EverandThe Little Book of Hygge: Danish Secrets to Happy LivingNota: 3.5 de 5 estrelas3.5/5 (399)
- Team of Rivals: The Political Genius of Abraham LincolnNo EverandTeam of Rivals: The Political Genius of Abraham LincolnNota: 4.5 de 5 estrelas4.5/5 (234)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNo EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNota: 4.5 de 5 estrelas4.5/5 (265)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNo EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNota: 3.5 de 5 estrelas3.5/5 (231)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNo EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNota: 4.5 de 5 estrelas4.5/5 (474)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNo EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNota: 4.5 de 5 estrelas4.5/5 (344)
- The Unwinding: An Inner History of the New AmericaNo EverandThe Unwinding: An Inner History of the New AmericaNota: 4 de 5 estrelas4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyNo EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyNota: 3.5 de 5 estrelas3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNo EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNota: 4 de 5 estrelas4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)No EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Nota: 4.5 de 5 estrelas4.5/5 (119)
- Upsc Admit Card 19Documento1 páginaUpsc Admit Card 19KUMAR GAURAVAinda não há avaliações
- ISXXX IT Helpdesk Issue Management Process V1.1Documento7 páginasISXXX IT Helpdesk Issue Management Process V1.1Vivi LimAinda não há avaliações
- QSP 7.1-02. Control of Monitoring and Measuring Resources (Preview)Documento4 páginasQSP 7.1-02. Control of Monitoring and Measuring Resources (Preview)Centauri Business Group Inc.100% (1)
- Serangan CyberDocumento20 páginasSerangan CyberballerinnaAinda não há avaliações
- E-mail Security SolutionsDocumento76 páginasE-mail Security SolutionsPapithaAinda não há avaliações
- Selection Table Type 2 CoordinationDocumento7 páginasSelection Table Type 2 CoordinationVishal Patel100% (1)
- IT Infrastructure Questionnaire GuideDocumento9 páginasIT Infrastructure Questionnaire Guideمحمد يوسف100% (1)
- 3.7.C - Third Wave WarDocumento16 páginas3.7.C - Third Wave Warjjamppong09Ainda não há avaliações
- Sree Dattha Institute of Engineering & Science: Ec851Pe: Network Security and CryptographyDocumento13 páginasSree Dattha Institute of Engineering & Science: Ec851Pe: Network Security and Cryptographyyuvaraaj aletiAinda não há avaliações
- Advertisement ICT 2016 of BUPDocumento1 páginaAdvertisement ICT 2016 of BUPSaif UzZolAinda não há avaliações
- Wordpress For Beginners Free Ebook Wp35Documento85 páginasWordpress For Beginners Free Ebook Wp35Daniel Martinz100% (3)
- 3 Cost Distribution Execution of Distribution CycleDocumento5 páginas3 Cost Distribution Execution of Distribution CycleMohammad AarifAinda não há avaliações
- OmniVista 8770 Brochure EN PDFDocumento6 páginasOmniVista 8770 Brochure EN PDFcarbonAinda não há avaliações
- Truck Body Mounting Directives 01-09-2006Documento362 páginasTruck Body Mounting Directives 01-09-2006George JabbourAinda não há avaliações
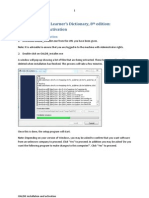
- Oxford Advanced Learner's Dictionary, 8 Edition: Installation and ActivationDocumento9 páginasOxford Advanced Learner's Dictionary, 8 Edition: Installation and ActivationsouvikdoluiAinda não há avaliações
- MOP TemplateDocumento5 páginasMOP TemplateJamsheed Ali Khan100% (1)
- ESE 2020 Notes Basics of Energy and EnvironmentDocumento133 páginasESE 2020 Notes Basics of Energy and EnvironmentsubhajitAinda não há avaliações
- JEEMAINJAN AdmitCard PDFDocumento1 páginaJEEMAINJAN AdmitCard PDFMehraan Ali KhanAinda não há avaliações
- Outlook2007 Guide PDFDocumento2 páginasOutlook2007 Guide PDFChris SalcidoAinda não há avaliações
- Pitch Music & Arts: Event Details Billing DetailsDocumento1 páginaPitch Music & Arts: Event Details Billing DetailsFinn HurleyAinda não há avaliações
- Ds Esprimo Mobile v6535Documento4 páginasDs Esprimo Mobile v6535kasem_beAinda não há avaliações
- Prisma Cloud Onboarding - AssessmentDocumento6 páginasPrisma Cloud Onboarding - Assessmentkya1005Ainda não há avaliações
- ITS Technologies for Improving Transportation SafetyDocumento21 páginasITS Technologies for Improving Transportation SafetySumanth BsAinda não há avaliações
- 6 1Documento2 páginas6 1Nazrul Ali MondalAinda não há avaliações
- Netapp CfstatusDocumento36 páginasNetapp Cfstatusmanas199Ainda não há avaliações
- Image Steganography Using Mid Position Value TechniqueDocumento7 páginasImage Steganography Using Mid Position Value TechniqueIhsan SabahAinda não há avaliações
- Ccnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 AmDocumento52 páginasCcnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 Amclearmoon247Ainda não há avaliações
- Quality Assurance ProcessDocumento130 páginasQuality Assurance Processbrijeshcoco100% (1)
- Tatweer Petroleum Contractor ID Badge RequestDocumento1 páginaTatweer Petroleum Contractor ID Badge RequestFishy09100% (1)
- BMA Innothon SFIMAR Barclays SrudentsDocumento2 páginasBMA Innothon SFIMAR Barclays SrudentsMovil MathiasAinda não há avaliações