Escolar Documentos
Profissional Documentos
Cultura Documentos
CSDA: Sample Test Questions: Home About Help Browse by Topic Sitemap Contact Login
Enviado por
Munini K. PierreDescrição original:
Título original
Direitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
CSDA: Sample Test Questions: Home About Help Browse by Topic Sitemap Contact Login
Enviado por
Munini K. PierreDireitos autorais:
Formatos disponíveis
The world's leading membership organization for computing professionals Home | About | Help | Browse By Topic | Sitemap | Contact
| Login Search Advanced
Publicati ons Conferen ces Digital Library Build Your Career e-Learning Campus Certification & Training Commun ities Sto re
CSDA Home CSDP Home Certification Home Education and Training FAQ and Resources Why Certify? Press Room Admin
CSDA: Sample Test Questions
The following questions were developed to offer examples of the style and content of the type of questions that will appear in the exam for the Certified Software Development Associate. They are classified as (I) or (C) questions as follows:
Introductory (I) level is intended to represent someone who has basic capability to perform in a knowledge area, but needs help, supervision, and review to do so -- like an apprentice. Competency (C) level is expected of a typical, experienced, professional -- they work largely on their own. One would certainly expect someone at the Competency level to be able to answer more specific, detailed, and difficult questions.
I. Software Requirements A. Software Requirements Fundamentals (I) 1. For which of the following practices does requirements engineering provide appropriate mechanisms and tools? a. Analyzing need b. Unambiguous specification of the solution c. Validating the specification
d. All of the above Answer Answer: D Rationale: Pressman states Requirements engineering provides appropriate mechanism for understanding what the customer wants, analyzing need, assessing feasibility, negotiating a reasonable solution, specifying the solution unambiguously, validating the specification, and managing the requirements as they are transformed into an operational system Reference: Pressman, R, S, Software Engineering: A Practitioners Approach, 6th Ed., Prentice-Hall, 2000.
B. Requirements Process (I) 1. Are requirements validation and analysis distinct requirements activities? a. Yes, because requirements validation needs a complete draft of the requirements document while the requirements analysis works with incomplete requirements. b. Yes, because requirements validation works with incomplete requirements while the requirements analysis needs a complete draft of the requirements document. c. Yes, because validation can only be done with testing while analysis can be done with prototyping. d. No, they are not distinct activities as they both work on requirements and aid in their elicitation.
Answer Answer: A Rationale: Answer A contains the rationale. Reference: Sommerville, I, Software Engineering, 6th Ed., Prentice-Hall, 2000, Page 137.
C. Requirements Elicitation (I) 1. Which of the following is a common method of requirements elicitation? a. Transactional Analysis b. Risk Assessment c. Implementing the System d. Observation Answer Answer: D Rationale: Most common methods of requirements elicitation include use of interviews, questionnaires, scenarios, brainstorming, facilitation, observation, social analysis, requirements reuse, study of documents, and software systems. References: - Sommerville, I, Software Engineering, 6th Ed., Prentice-Hall, 2000. - Pressman, R.S., Software Engineering: A Practitioners Approach, 6th edition, McGrawHill, 2005.
D. Requirements Analysis (C)
E. Requirements Specification (I)
F. Requirements Validation (C)
G. Practical Considerations (I)
II. Software Design
A. Software Design Fundamentals (C) 1. Suppose a team is developing a web-based ticket distribution system. Which of the following decisions was most likely made during system design? a. The ticket distributor will include a user interface subsystem. b. The ticket distributor will follow web-accessibility standards. c. The ticket distributor will provide the traveler with on-line help. d. The ticket distributor requirements have been met and satisfy customer needs. Answer Answer: A Rationale: a) is typically done in system design phase. b) is typically done in requirement phase (non-functional requirement) c) is typically done in requirement phase (functional requirement). d) is typically done in acceptance testing phase. Reference: Sommerville, Software Engineering, 8th Ed, Addison Wesley, 2007, Pages: 80, 81, 342-344.
B. Key Issues in Software Design (C)
C. Software Structure and Architecture (C) 1. In designing an object-oriented class hierarchy to represent binary expressions, which structural pattern and behavioral pattern could be used most effectively? a. Composite and Interpreter b. Decorator and Command c. Flyweight and Strategy
d. Proxy and Visitor Answer Answer: A Rationale: a) A Composite OperatorExpression class can inherit from an abstract BinaryExpression class. Classes PlusExpression, MinusExpression, etc., (which can inherit from OperatorExpression) together with an OperandExpression class can implement the grammar rules of the Interpreter pattern. b) A Decorator attaches responsibilities dynamically. This hierarchy is static. c) A Flyweight uses sharing to support large numbers of fine-grained objects; Strategy defines a family of interchangeable algorithms. Neither is particularly applicable. d) A Proxy is a placeholder, generally to defer the cost of creating an expensive object. There are no such heavy objects in this hierarchy. Reference: Gamma et. al., Design Patterns, Addison-Wesley, 1995, pp. 163, 175, 195, 207, 233, 243, 315, 331
2. To support the reuse of component systems, which of the following mechanisms is often used to insulate client code from the specific details of the components by exporting only the portion of a components interfaces that are needed by the client system? a. Abstract Class b. Faade c. Parameterized Classes d. Publisher-Subscriber Answer Answer: B Rationale: a) Abstract Classes define common interfaces for its subclasses. They have no mechanism that is suitable for isolating or encapsulating interfaces to component. b) A Faade is a high-level interface that provides a simpler interface to a subsystem. This high-level interface can shield the clients from the complexities of the standard subsystem
interfaces while still allowing other clients access to the lower level, more complex interfaces. c) Parameterized Classes have no mechanism that is capable of isolating or encapsulating interfaces to components. Parameterized classes allow their functionality to be reused by a bound class, thus transforming the bound class. d) Publisher-Subscriber pattern has no mechanism that is capable of isolating or encapsulating interfaces to components, it is used for the selective notifications of events. Reference: Gamma et. al., Design Patterns, Addison-Wesley, 1995, pp 15, 21-22, 185-193, 293-299.
D. Human Computer Interface Design (C)
E. Software Design Quality Analysis and Evaluation (C)
F. Software Design Notations (C)
G. Software Design Strategies and Methods (C) 1. Using a structural model to represent an architectural design has which of the following characteristics? a. A structural model allows identifying repeatable architectural design frameworks that are encountered in similar applications b. A structural model addresses behavioral aspects which indicate how the system changes as a function of external events c. A structural model represents the architecture as an organized collection of program modules and components d. A structural model focuses on the business or technical processes that a system must accommodate Answer Answer: C
Rationale: a is a framework model, b dynamic model, d is a process model. Reference: Pressman, R.S., Software Engineering: A Practitioners Approach, 6th edition, McGraw-Hill, 2005, page 234.
III. Software Construction
IV. Software Testing
A. Software Testing Fundamentals (I) 1. An incorrect step, process, or data definition in a computer program is a a. Failure b. Mistake c. Fault d. Consequence Answer Answer: C Rationale: The word consequence does not typically refer to an incorrect element, but rather the results of an action. IEEE Std 610.12-1990 states; Fault: An incorrect step, process, or data definition in a computer program Failure: The [incorrect] result of a fault Mistake: A human action that produces an incorrect result Reference: - SWEBOK, Chapter 11, Section 3.2 - IEEE Std 610.12-1990 IEEE Standard Glossary of Software Engineering Terminology
B. Test Levels (C)
C. Test Techniques (C) 1. What is the Cyclomatic Complexity of the following flow graph for a program?
a. 3 b. 4 c. 9 d. 11 Answer Answer: B Rationale: V(G) = Number of Edges Number of Nodes + 2 V(G) = 10 8 + 2 = 4 Reference: Pressman, R.S., Software Engineering: A Practitioners Approach, 6th edition, McGraw-Hill, 2005, section 14.4.
2. Equivalence Partitioning is a testing technique used in the following a. White box testing b. Black box testing c. Stress testing d. Usability testing Answer Answer: B Rationale: Equivalence partitioning is concerned with a units performance based on the specification for the unit or the black box operation of the unit, while white box testing is determined by the unit code. Usability testing is concerned with ease-of-use, issues such as the understandability, learnability, and operability of the software. Stress testing is concern with the softwares performance under stress or heavy load. Reference: Pressman, R.S., Software Engineering: A Practitioners Approach, 6th edition, McGraw-Hill, 2005, section 13.6, 14.2, 14.6, 20.4.
D. Human Computer User Interface Testing and Evaluation (C)
E. Test-Related Measures (C)
F. Test Process (C)
V. Software Maintenance
A. Software Maintenance Fundamentals (I) 1. Why are requirements errors generally among the most expensive errors to repair? a. Because repairing requirements errors is likely to lead to extensive system redesign.
b. Because repairing requirements errors forces adaptations to the system to cope with environmental changes. c. Because the need to repair requirements errors usually comes about due to organizational or business changes. d. Because repairing requirements errors involves keeping the functionality of the system unchanged while improving the internal structure and overall performance. Answer Answer: A Rationale: Answer a is the correct answer. Repairs due to specification errors can be very expensive because they are likely to involve fundamental changes that affect every part of a system. This is a type of corrective maintenance. Answer b describes adaptive maintenance, where a system is adapted to a different environment. This type of maintenance is not considered to be corrective maintenance (that is, the work is generally not due to the discovery of an error). Answer c describes a type of perfective maintenance. This type of maintenance may introduce new requirements because the business has changed in some way. This type of maintenance is generally not considered to be corrective because the task is to incorporate newer requirements that did not exist when the earlier version of the system was released, rather to correct errors in the original requirements. Answer d describes another type of perfective maintenance. Leaving the functionality unchanged implies that no errors had been discovered in system behavior. It may be desirable, however, to improve the maintainability of a system or its performance, even if its overall operation is acceptable. Reference: Sommerville, Software Engineering, 8th Ed, Addison Wesley, 2007, Chapter 21, p. 493.
2. Lehman's laws regarding program evolution dynamics describe the principles behind system change. Lehman's Laws of Large Program Evolution and Organizational Stability suggest that program evolution for large systems is largely independent of management decisions. This has the following consequence: a. Structural factors have little effect on the evolution process for large systems. b. Making major changes, rather than smaller changes, is a reasonable strategy for large systems. c. Large software development teams are not overly affected by the overhead of communication.
d. Changes to resources or staffing have largely imperceptible effects on the long-term evolution of large systems. Answer Answer: D Rationale: Answer a is incorrect because the structure of a system determines the maintenance dynamic of that system. Structural factors influence and constrain system change. Answer b is incorrect because in a large, complex system, the system is harder to understand and programmers are more likely to maker errors and introduce faults into the system. A major change is likely to introduce many new faults, while smaller changes are likely to lead to fewer faults that are easier to catch. Answer c is incorrect because communication overhead can dominate the work of a large team, leading to reduced productivity. Answer d is the correct answer because the maintenance dynamics for large systems appear to be established early in the development process. Early decisions about system structure appear to determine the gross trends for the system's maintenance process. Reference: Somerville, I. , Software Engineering, 8th Ed, Addison Wesley, 2007, Chapter 21, pp. 491-492.
B. Key Issues in Software Maintenace (I)
C. Maintenance Process (C)
D. Techniques for Maintenance (C)
VI. Software Configuration Management
A. Management of the SCM Process (I) 1. Identification and selection of a version control tool is a part of which software configuration management activity? a. Release Management and Delivery b. Management and Planning c. Configuration Auditing d. Configuration Control Answer Answer: B Rationale: Tool selection is part of planning for SCM. Reference: SWEBOK, Chapter 7, Section 1.3.3 Tool Selection and Implementation, page 74.
B. Software Configuration Identification (C) 1. Which of the following best describes a software library? a. baseline documentation and code b. collection of software configuration items c. controlled collection of software and related documentation designed to aid in software development, use, and maintenance d. all minutes of a configuration control board (CCB) and related audits Answer Answer: C Rationale: This the only description that encompasses the long-term use of software library by the software engineering community as well as addressing the breadth and practicality of its meaning. Reference: SWEBOK, Chapter 7, Section 2.2 Software Library, page 7-7.
C. Software Configuration Control (C) 1. A configuration control board (CCB) handles which of the following? a. tool selection b. software change requests c. software configuration audits d. software release documentation Answer Answer: B Rationale: The rationale is that the primary purpose for the CCB is to handle SCRs. Reference: SWEBOK, Chapter 7, Section 3.1.1 Software Configuration Control Board, pages 7-7 to 7-8.
D. Software Configuration Status Accounting (C)
E. Software Configuration Auditing (I)
F. Software Release Management and Delivery (I) 1. In order to perform daily integration of the software system, which of the following activity must be performed? a. daily configuration board meeting b. daily change requests processing c. daily build d. daily auditing
Answer Answer: C Rationale: Software building is the only way that the latest executable program can be delivered for testing or other purposes. Reference: SWEBOK, Chapter 7, Section 6.1 Software Building, page 7-9.
VII. Software Engineering Management
A. Initiation and Scope Definition (I) B. Software Project Planning (I) 1. Identifying and managing risks are an important part of effective management of the software engineering effort. Risks are documented: a. In a concise statement of what went wrong and when they occurred in the project lifecycle b. As clearly defined tasks in the project schedule c. In a concise statement that includes the context, conditions, and consequences of risk occurrence d. As clearly defined line-items in the project budget Answer Answer: C Rationale: Direct quote from the CMMI Reference: Chrissis, Mary Beth, et. Al, CMMI Second Edition, Guidelines for Process Integration and Product Improvement, Addison Wesley, 2007, Part Two, Risk Management, SP 2.1, page 505.
C. Software Project Enactment (I)
D. Review and Evaluation (I)
E. Closure (I)
F. Software Engineering Measurement (I)
G. Software Management Tools (I)
VIII. Software Engineering Process
A. Process Implementation and Change (I) 1. The success rate for software projects is very low. Although viewed form different perspectives, studies in the 1990s by Caper Jones, The Standish Group and the Defense Science Board conclude that the success rate for software projects is very low and that the high level of software scrap and rework is mostly indicative of: a. Lack of software development skills b. Immature process c. Lack of adequate schedule d. Lack of adequate budget
Answer Answer: B Rationale: In the mid-1990s, at least three important analyses of the state of the software engineering industry were published by Capers Jones in 1996, The Standish Group in 1995, and the Defense Science Board in 1994, that all came to the same general conclusion Reference: Royce, Walker, Software Project Management A Unified Framework, Addison Wesley, 1998, Chapter 1, page 5.
B. Process Definition (C)
C. Process Assessment (I)
D. Measurement (I)
E. Software Process Tools (I)
IX. Software Engineering Methods
A. Modeling (C) 1. Systems that are built from a functional viewpoint would typically use which of the following methods: a. structural methods b. object-oriented methods c. constructive methods
d. data-oriented methods Answer Answer: A Rationale: structural methods are focused on a functional view of the system Reference: SWEBOK, Chapter 10, Section 2 Software Engineering Methods, page 10-3.
B. Types of Models (C)
C. Analysis (C) 1. The formal methods technique of refinement: a. refers to tools that structurally format a formal specification b. is an automatic theorem-proving technique. c. transforms a formal specification into a design or implementation component. d. checks the semantics of a formal specification Answer Answer: C Rationale: This topic deals with how the method refines (or transforms) the specification into a form which is closer to the desired final form of an executable program. Reference: SWEBOK, Chapter 10.
E. Development Methods (C)
X. Software Quality
A. Software Quality Fundamentals (I)
B. Software Quality Management Processes (C) 1. Which of the following represents the most complete process for Fagan Inspection a. Planning, overview, preparation, inspection, rework, brain storming, follow up b. Planning, overview, brain storming, preparation, inspection, rework, follow up c. Planning, preparation, inspection, rework d. Planning, overview, preparation, inspection, rework, follow up Answer Answer: D Rationale: There is no brainstorming step in the official Fagan Inspection, therefore, a & b are eliminated. Follow up is a major component of the Fagan Inspection, which is missing from choice c. Reference: Tian, J., Software Quality Engineering: Testing, Quality Assurance, and Quantifiable Improvement, Wiley, 2005, chapter 14.
C. Software Quality Practical Considerations (C)
XI. Software Engineering Economics
A. Software Engineering Economy Fundamentals (C) 1. If $15,000 is invested at 5% compounded annually, what is the value of the investment after 6 years? a. 15000 x 6 x 0.05 b. 15000 x 1.056 c. 15000 + 6 x (0.05x15000) d. (0.05 + 15000)6 Answer Answer: B Rationale: Using the compound interest formula, P(1+i)n, the result is answer b. Reference: Tockey, S., Return on Software, Addison-Wesley, 2004.
B. For-profit Decision-making (C) 1. A company is evaluating a proposal for developing a new internet product. The company has established the Minimum Attractive Rate of Return (MARR) for such products. Suppose the Internal Rate of Return (IRR) for the new proposal has been determined. Which of the following conditions would most likely cause rejection of the proposal? a. IRR < MARR b. IRR > MARR c. 90% of IRR > MARR d. IRR = MARR Answer Answer: A Rationale: IRR < MARR implies the new product is not economically attractive and may involve financial loss.
Reference: Tockey, S., Return on Software, Addison-Wesley, 2004.
C. Non For-pofit Decision-making (C)
D. Present Economy (C)
E. Estimation, Risk, and Uncertainty (C)
F. Multiple Attribute Decisions (C)
XII. Software Engineering Professional Practice
A. Professionalism
B. Codes of Ethics (C) 1. A software developer who adheres to the Software Engineering Code of Ethics and Professional Practices must: a. Always practice according to IEEE standards b. Assist colleagues in professional development c. Be a member of the IEEE Computer Society d. Avoid all issues related to finance and profitability Answer
Answer: B Rationale: Section 7.02 of the Software Engineering Code of Ethics and Professional Practices states 7.02. that a software engineer must Assist colleagues in professional development. Although answers a and c would be supported by the Code, it does not include statements with this level of specificity. Answer d is clearly false; in fact, software engineer managers and leaders are required to Ensure realistic quantitative estimates of cost, (statement 5.05). Reference: Software Engineering Code of Ethics and Professional Practice
2. A software engineer is employed by the company that designs and manufactures voting machines. She is employed to develop an archival system for retaining voting information and results. Which of the following actions would most likely be a violation of the Software Engineering Code of Ethics and Professional Practice? a. She failed to keep adequate documentation of her work on the project. b. She has not previously worked on a voting machine project. c. She has registered as a voter in the state in which the machines will be used. d. She discovered significant number defects in her design for the archival system. Answer Answer: A Rationale: Section 3.11 of the Software Engineering Code of Ethics and Professional Practices states that a software engineer must Ensure adequate documentation, including significant problems discovered and solutions adopted, for any project on which they work. For answers b and c, the engineer should inform her employer about her lack of experience and her current voting status, these are not in themselves violations of the Code. For answer d, she would only have code problems if she were h not using accepted practices or if she failed to fix the defects discovered. Reference: Software Engineering Code of Ethics and Professional Practice
C. Group Dynamics / Psychology (C) 1. In forming a software team, it is decided to organize the team so that team members
can work on pieces of the problem with little communication between each other. Which organizational paradigm is being used? a. Closed Paradigm b. Open Paradigm c. Random Paradigm d. Synchronous Paradigm Answer Answer: D Rationale: Constantine [Pressman 2005, p. 602] defined four team organization paradigms: Closed Open, Random and Synchronous. According to [Pressman 2005, p. 602] the synchronous paradigm relies on the natural compartmentalization of a problem and organized team members to work on pieces of the problem with little active communication between themselves. Reference: - [Constantine 1993] Constantine, L.L., Work Organization: Paradigms for Project Management and organization, Communications of the ACM, Volume 36 , Issue 10, October 1993. - [Pressman 2005] Pressman, R.S., Software Engineering: A Practitioners Approach, 6th edition, McGraw-Hill, 2005.
D. Communication Skills
E. Intellectual Property, Confidentiality, Security
XIII. Computing Foundations
A. Programming Fundamentals (C) 1. Consider a recursive function "recurr" that calculates and returns a value based on
input n, a positive integer. function recurr(n) // purpose: ? // input: a positive integer n // output: a number x equal to the value of recurr(n) x := 1 if n > 10 , then x := 2*recurr(n-10) if n < 10, then x := x*3 return x What is the value of recurr(55) ? a. 165 b. 96 c. 1 d. 48 Answer Answer: B Rationale: x = 2*recurr(45) = 2*2*recur(35) = 2*2*2*recur(25) = 2*2*2*2*recur(15) = 2*2*2*2*2*recur(5) = 2*2*2*2*2*3 = 32*3 = 96 Reference: Applications Programming in C++ by Johsonbaugh and Kalin.
B. Algorithms, Data Structures/Representation (static & dynamic), Complexity (C) 1. The following pseudocode defines a sorting algorithm SORT for sorting numbers: algorithm SORT(A) // purpose: sorts the array A in ascending order //input: an array A[0,...,n-1] of orderable elements //output: an array A[0,...,n-1] sorted in ascending order. for i = 0 to n-2 do min := i for j = i+1 to n-1 do if A[j] < A[min], then min := j swap A[i] and A[min]
Which of the following statements concerning SORT are true: a. The number of comparisons is given by sum b. The number of comparisons is given by n(n+1)/4. c. The number of comparisons is O(nlogn). d. The number of swaps is n + 2. Answer Answer: A Rationale: The inner for loop has (n-1) (i+1) +1 = n-i+1 comparisons. For the outer for loop, (n-i+1) comparisons are performed from i=0 to i=n-2. So a is true, and b and c are false. The number of swaps is n-2+1=n-1; hence, d is also false. Reference: Leviin, A., The Design and Analysis of Algorithms, Addison Wesley.
2. The BNF grammar for a language is given as: ::= | ::= 1|2|3|4|5|6|7|8|9|0 ::= $ | ! | # | @ Which of the following statements is true about the above grammar? a. The operators are left-associative. b. The $ operator has higher precedence than the @ operator c. The operators are right-associative d. The @ operator has higher precedence than the # operator Answer Answer: C Rationale: By definition, the expression 9 $ 3 ! 7 = 9 $ (3 ! 7); hence, the BNF is right associative. The operators do not have an specified precedence. Reference: Sebesta, R., Concepts of Programming Languages, Addison Wesley Longman Inc., 2002.
C. Problem Solving Techniques(C)
D. Abstraction -- use and support for (encapsulation, hierarchy, and so on) (C)
E. Computer Organization (C)
F. Basic concept of a system (C)
G. Basic user human factors (I/O, error messages, robustness) (C)
H. Basic developer human factors (comments, structure, readability) (C)
I. Operating system basics (C)
J. Database Basics and Data Management (C)
K. Network communication basics (C)
L. Distributed and Parallel Computing (C)
M. Concepts of programming languages (C) 1. "Report" class inherits from "Document" class. Document class defines a print()
method. Assume polymorphic behavior. Which of the following scenarios would not result in the client calling Document.print() on a Report object called TermReport? a. Report.print() does not refer to Document.print() b. Report class does not define print() method. c. Report.print() calls Document.print() and does nothing else d. Client casts the TermReport object to Document class before calling print. Answer Answer: A Rationale: By the usual understanding of polymorphism in OO inheritance, for answers b, c and d, Document.print() would be called; and for answer a, Document.print() would not be called Reference: Deitel and Deitel, C++: How to Program, 5th Ed. , Prentice Hall, 2005.
N. Debugging Tools and Techniques (C)
O. Secure Coding (C)
XIV. Mathematical Foundations
A. Functions, Relations and Sets (C) B. Basic Logic (prepositional and predicate) (C) C. Proof Techniques (direct, contradiction, inductive) (C) D. Basic Counting (C) E. Graphs and Trees C)
F. Discrete Probability (C) G. Finite State Machines, regular expressions (C) H. Grammars (C) I. Numerical precision, accuracy, and errors (C) J. Number Theory (C) K. Algebraic Structures (C)
XV. Engineering Foundations
A. Empirical methods and experimental techniques (such as computer-related measuring techniques for CPU and memory usage) (C)
B. Statistical analysis (including simple hypothesis testing, estimating, regression, and correlation) (C) 1. A software engineer is asked to analyze the relationship between the number of lines of source code (LOC) produced for a set of projects versus the effort (in Hours) required to produce the code. He is using linear regression to compare LOC and effort in Hours. He submits a report to management showing that the set of data analyzed has a correlation coefficient of r = 0.05. What can one conclude?
a. LOC and effort are not linearly correlated. b. There is a direct linear correlation between LOC and effort. c. The correlation between LOC and effort is nonlinear. d. Conclusions depend on the number of data elements in the set analyzed. Answer Answer: A Rationale: A low coefficient of correlation means that LOC shows no linear relationship to effort. It is possible that the data have a nonlinear correlation, but this has to be tested. If the
few pieces of data d would be correct if r was closed to +1 or -1, but not for an r close to zero. Reference: Spiegel, M.R., Statistics, 2nd Edition, Schaums Outlines, McGraw-Hill, 1996, p. 297.
C. Measurement (I)
D. Systems development (security, safety, performance, effects of scaling, feature interaction, and so on) (I)
E. Engineering design (problem forumulation, alternative solutions, feasibility, and so on) (C)
F. Theory of measurement (for example, criteria for valid measurement) (C) 1. A software engineer is measuring the quality of a software system. She is concerned with the reliability and the validity of her measurements. Which of the following is true? a. Reliability refers to the extent to which the measurement represents the actual quality of the system and validity refers to the consistency of her quality measurements b. Reliability refers to the consistency of her quality measurements and validity refers to the extent to which the measurement represents the actual quality of the system. c. Reliability refers to the accuracy of her quality measurements and validity refers to the extent to which the measurement follows a quality standard. d. Reliability refers to the concurrency of her quality measurements and validity refers to the extent to which the measurements are consistent with established norms. Answer Answer: B Rationale: Reliability refers to the consistency of a number of measurements taken using the same measurement method on the subject. Validity refers to whether the measurement really measures what is intended.
Reference: Kan, S. H., Metrics and Models in software Quality Engineering, 2nd Edition, Addison-Wesley, 2003, pp. 70, 71.
G. Simulation, Modeling, and Conceptual Prototyping (C)
H. GQM Paradigm (I)
I. Standards (identify, evaluate, select, adapt) (I)
J. Tool and platform selection (I)
K. Root cause analysis (C)
About Conta Membe Volunte For More Us ct Us r er Informati Resourc Center on Mission, Customer Vision & Service es Goals Key Staff Member & Press Room
History Awards and Fellows Volunteer Leadership Contacts Advertising Office Locations & Directions Renew Membership Access eLearning Geographic Activities Educational Activities Professional Member Resource Guide (PDF) Author Information Request Information
Staff Leadership Nondiscrimina tion Policy Browser Support Policy
Report Website Issue
Courses Access Safari Books Online Access Books 24x7 Discounted Subscriptions Discounted Conference Registration Chapter Contacts Username / Password Issues
Activities Standards Activities Technical Activities Volunteer Resource Center
This site and all contents (unless otherwise noted) are Copyright 2011 IEEE. All rights reserved.
Você também pode gostar
- 650-177 SMB Select Bootcamp AMDocumento74 páginas650-177 SMB Select Bootcamp AMbcoxtoshAinda não há avaliações
- Ha400 PDFDocumento1 páginaHa400 PDFZacharias Pavlos50% (2)
- My Edit Draft 166 QDocumento33 páginasMy Edit Draft 166 QDilsenAinda não há avaliações
- Number: 220-1001 Passing Score: 800 Time Limit: 120 Min: Website: VCE To PDF Converter: Facebook: TwitterDocumento40 páginasNumber: 220-1001 Passing Score: 800 Time Limit: 120 Min: Website: VCE To PDF Converter: Facebook: TwitterJavier Jesús ParionaAinda não há avaliações
- DOC1 Users GuideDocumento453 páginasDOC1 Users GuideEzra Gutierrez0% (1)
- FCBADocumento5 páginasFCBATwilightAinda não há avaliações
- Okta Developer Exam - Study Guide - 0Documento17 páginasOkta Developer Exam - Study Guide - 0gunda prashanthAinda não há avaliações
- 62-193.examcollection - Premium.exam.41q: Number: 62-193 Passing Score: 800 Time Limit: 120 Min File Version: 4.0Documento26 páginas62-193.examcollection - Premium.exam.41q: Number: 62-193 Passing Score: 800 Time Limit: 120 Min File Version: 4.0Ruben Dario Pinzón ErasoAinda não há avaliações
- Official Google Cloud Certified Professional Data Engineer Study Guide - Dan SullivanDocumento5 páginasOfficial Google Cloud Certified Professional Data Engineer Study Guide - Dan SullivanpudocowuAinda não há avaliações
- 5 - WQU - 622 CTSP - M5 - CompiledContentDocumento34 páginas5 - WQU - 622 CTSP - M5 - CompiledContentJoe NgAinda não há avaliações
- 1z0-900.prepaway - Exam.69q: Number: 1z0-900 Passing Score: 800 Time Limit: 120 Min File Version: 1Documento46 páginas1z0-900.prepaway - Exam.69q: Number: 1z0-900 Passing Score: 800 Time Limit: 120 Min File Version: 1Leonardo Gabriel WeingaudAinda não há avaliações
- Cisco Certified Network Professional CyberOps A Complete Guide - 2019 EditionNo EverandCisco Certified Network Professional CyberOps A Complete Guide - 2019 EditionAinda não há avaliações
- Exam Az 900 Microsoft Azure Fundamentals Skills MeasuredDocumento8 páginasExam Az 900 Microsoft Azure Fundamentals Skills Measuredrody692Ainda não há avaliações
- Ai Powered SearchDocumento9 páginasAi Powered SearchStoica AlexandruAinda não há avaliações
- Dotnet SyllabusDocumento2 páginasDotnet Syllabuskkumar_876069Ainda não há avaliações
- iSQI Selftestengine CTFL - Foundation v2019-06-15 by Laura 119q PDFDocumento58 páginasiSQI Selftestengine CTFL - Foundation v2019-06-15 by Laura 119q PDFميميAinda não há avaliações
- Oracle Actualtests 1z0-900 v2018-11-28 by Eric 41qDocumento27 páginasOracle Actualtests 1z0-900 v2018-11-28 by Eric 41qcveta21Ainda não há avaliações
- 210 260Documento271 páginas210 260mkashifmohiAinda não há avaliações
- Study Guide: Exam AI-900: Microsoft Azure AI FundamentalsDocumento7 páginasStudy Guide: Exam AI-900: Microsoft Azure AI FundamentalsAman C. KapseAinda não há avaliações
- Formal Description of A System, or A Detailed Plan of The System at Component Level, To Guide Its ImplementationDocumento2 páginasFormal Description of A System, or A Detailed Plan of The System at Component Level, To Guide Its ImplementationMelissa Indah FiantyAinda não há avaliações
- ScribdDocumento6 páginasScribdZaihisma_Che_C_2828Ainda não há avaliações
- Microsegmentation Architectures A Complete Guide - 2019 EditionNo EverandMicrosegmentation Architectures A Complete Guide - 2019 EditionAinda não há avaliações
- SAP HANA Development Exam Guide and QuesDocumento7 páginasSAP HANA Development Exam Guide and QuesJaya SankarAinda não há avaliações
- NWT AssignmentDocumento81 páginasNWT AssignmentShavin Avin50% (4)
- AWS Certified Advanced Networking Speciality Exam Guide v1.1 FINALDocumento3 páginasAWS Certified Advanced Networking Speciality Exam Guide v1.1 FINALakAinda não há avaliações
- Oracle Banking Digital Experience Installation GuideDocumento91 páginasOracle Banking Digital Experience Installation GuideAlem MezgeboAinda não há avaliações
- Az-900 AdDocumento175 páginasAz-900 AdSAMIR MOHANTYAinda não há avaliações
- Itil - Premium.itilfnd V4.by - Vceplus.293qDocumento117 páginasItil - Premium.itilfnd V4.by - Vceplus.293qŁukasz IwanowskiAinda não há avaliações
- AWS Certified Cloud Practitioner - Exam Guide - C02Documento22 páginasAWS Certified Cloud Practitioner - Exam Guide - C02Sonal GuptaAinda não há avaliações
- SaaS Platform Security Management A Complete Guide - 2020 EditionNo EverandSaaS Platform Security Management A Complete Guide - 2020 EditionAinda não há avaliações
- 98 364 Study GuideDocumento65 páginas98 364 Study GuideBob Mulumba100% (1)
- Professional Cloud DevOps Engineer - enDocumento93 páginasProfessional Cloud DevOps Engineer - enSimon Yeswa Mukavana100% (1)
- Key Management System A Complete Guide - 2020 EditionNo EverandKey Management System A Complete Guide - 2020 EditionAinda não há avaliações
- Reporting Services 2014 PDFDocumento130 páginasReporting Services 2014 PDFAna B. Lima L.Ainda não há avaliações
- Exam Aws ListDocumento2 páginasExam Aws Listfox_8809Ainda não há avaliações
- HPE Aruba 2540 Quick Setup Guide enDocumento14 páginasHPE Aruba 2540 Quick Setup Guide enLuis Yefferson Tica QuispeAinda não há avaliações
- Microservices with Azure A Complete Guide - 2019 EditionNo EverandMicroservices with Azure A Complete Guide - 2019 EditionAinda não há avaliações
- Az 900Documento16 páginasAz 900durgasatyahansithAinda não há avaliações
- 010-160 Exam QuestionsDocumento3 páginas010-160 Exam QuestionspollymcelroyAinda não há avaliações
- The Real MCTS/MCITP Exam 70-647 Prep Kit: Independent and Complete Self-Paced SolutionsNo EverandThe Real MCTS/MCITP Exam 70-647 Prep Kit: Independent and Complete Self-Paced SolutionsNota: 1 de 5 estrelas1/5 (1)
- AWS Certified Solutions Architect Professional Exam GuideDocumento3 páginasAWS Certified Solutions Architect Professional Exam GuideJhon HuamanchumoAinda não há avaliações
- Exam AZ 900: Azure Fundamental Study Guide-2: Explore Azure Fundamental guide and Get certified AZ 900 examNo EverandExam AZ 900: Azure Fundamental Study Guide-2: Explore Azure Fundamental guide and Get certified AZ 900 examAinda não há avaliações
- Storage area network The Ultimate Step-By-Step GuideNo EverandStorage area network The Ultimate Step-By-Step GuideAinda não há avaliações
- Example: Questions 1-4Documento5 páginasExample: Questions 1-4Vitória Rodovalho100% (1)
- Cisco - Certleader.700 150.PDF.2020 Aug 26.by - Alston.96q.vceDocumento9 páginasCisco - Certleader.700 150.PDF.2020 Aug 26.by - Alston.96q.vceDmitrii DaniliukAinda não há avaliações
- Amazon Web Services for Mobile Developers: Building Apps with AWSNo EverandAmazon Web Services for Mobile Developers: Building Apps with AWSAinda não há avaliações
- SAP CRM Campaign Management - CRM and ECC Middleware IntegrationDocumento8 páginasSAP CRM Campaign Management - CRM and ECC Middleware IntegrationPrasun Roy ChowdhuryAinda não há avaliações
- Pass4Sure ACMP - 6.4 Braindumps QuestionsDocumento20 páginasPass4Sure ACMP - 6.4 Braindumps QuestionsPass4SuresAinda não há avaliações
- MCS-034 Solved AssignmentsDocumento30 páginasMCS-034 Solved AssignmentsAbhinand Rajeev SAinda não há avaliações
- What Is GenocideDocumento46 páginasWhat Is GenocideMunini K. PierreAinda não há avaliações
- Explanation (Describe Your Relationship With The Institution and Add Further Information You Wish To Share Concerning This Complaint.)Documento1 páginaExplanation (Describe Your Relationship With The Institution and Add Further Information You Wish To Share Concerning This Complaint.)Munini K. PierreAinda não há avaliações
- Application Form English ToDocumento5 páginasApplication Form English ToMunini K. PierreAinda não há avaliações
- I.2. Problem StatementDocumento1 páginaI.2. Problem StatementMunini K. PierreAinda não há avaliações
- Igrp - : IGRP (Interior Gateway Routing Protocol)Documento9 páginasIgrp - : IGRP (Interior Gateway Routing Protocol)Munini K. PierreAinda não há avaliações
- Configuring Ethernet Switches: Switch Port Numbering and NamingDocumento12 páginasConfiguring Ethernet Switches: Switch Port Numbering and NamingMunini K. Pierre100% (1)
- Vehicle Management System For Tenaga Nasional Berhad Kelantan - Noor Aidah Bt. Ahmed - QA76.76.D47.N66 2006Documento27 páginasVehicle Management System For Tenaga Nasional Berhad Kelantan - Noor Aidah Bt. Ahmed - QA76.76.D47.N66 2006Munini K. PierreAinda não há avaliações
- Week 2: Conversions: InputDocumento2 páginasWeek 2: Conversions: InputMunini K. PierreAinda não há avaliações
- The Intellectual and Political Legacies of Kwame Nkrumah: Ama BineyDocumento16 páginasThe Intellectual and Political Legacies of Kwame Nkrumah: Ama BineyMunini K. PierreAinda não há avaliações
- Rwanda - UniversityDocumento6 páginasRwanda - UniversityMunini K. PierreAinda não há avaliações
- International Boundary Study: Democratic Republic of The Congo - Rwanda BoundaryDocumento9 páginasInternational Boundary Study: Democratic Republic of The Congo - Rwanda BoundaryMunini K. PierreAinda não há avaliações
- Timeline of Democratic Republic of Congo History & Key EventsDocumento2 páginasTimeline of Democratic Republic of Congo History & Key EventsMunini K. PierreAinda não há avaliações
- Zimbabwe CongoDocumento23 páginasZimbabwe CongoMunini K. PierreAinda não há avaliações
- Williams ZaireDocumento5 páginasWilliams ZaireMunini K. PierreAinda não há avaliações
- VentilationDocumento3 páginasVentilationasdasaAinda não há avaliações
- Function Modules Available in MM & EWMDocumento3 páginasFunction Modules Available in MM & EWMgopalaaraoAinda não há avaliações
- Art Appreciation Learning ModulesDocumento32 páginasArt Appreciation Learning ModulesJonah ChoiAinda não há avaliações
- Spiking Into Aqueous Samples: Standard Guide ForDocumento6 páginasSpiking Into Aqueous Samples: Standard Guide Formohdhafizmdali100% (1)
- Design Data (No Longer Current But Cited in The Building Regulations)Documento290 páginasDesign Data (No Longer Current But Cited in The Building Regulations)ferdinand bataraAinda não há avaliações
- Invers Transf LaplaceDocumento13 páginasInvers Transf LaplaceMeriska AhmadAinda não há avaliações
- TS1620 TechstarDocumento12 páginasTS1620 TechstarMahdiiiiii83Ainda não há avaliações
- WS-Problems Solved by Quadratic EquationsDocumento1 páginaWS-Problems Solved by Quadratic EquationsNorul AzimAinda não há avaliações
- Conic SectionDocumento9 páginasConic SectionJomana MacalnasAinda não há avaliações
- Data StructuresDocumento2 páginasData StructuresRavi PalAinda não há avaliações
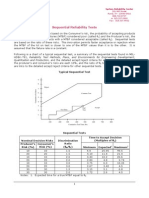
- Sequential Reliability TestsDocumento2 páginasSequential Reliability Teststanpreet_makkadAinda não há avaliações
- Nps 5638Documento8 páginasNps 5638vamsi_1990Ainda não há avaliações
- Sag 38 2 12 0709 2Documento7 páginasSag 38 2 12 0709 2Yoselin GomezAinda não há avaliações
- Siegel57Nonparametric PDFDocumento8 páginasSiegel57Nonparametric PDFTarisna AryantiAinda não há avaliações
- Velocity Analysis-Instantaneous Center MDocumento7 páginasVelocity Analysis-Instantaneous Center MSuman_SamadderAinda não há avaliações
- Certification of eVTOL AircraftDocumento19 páginasCertification of eVTOL AircraftrlwersalAinda não há avaliações
- Software Development Kit 2.1 Programmer's Guide 2.1: Cell Broadband EngineDocumento82 páginasSoftware Development Kit 2.1 Programmer's Guide 2.1: Cell Broadband EnginemathurvaibhavAinda não há avaliações
- Lutron / Trane Bacnet Integration: QuantumDocumento7 páginasLutron / Trane Bacnet Integration: QuantumthomasAinda não há avaliações
- Transition Elements Final 1Documento44 páginasTransition Elements Final 1Venkatesh MishraAinda não há avaliações
- QP NTSE Stage 1 2016 17 AndhraPradeshDocumento27 páginasQP NTSE Stage 1 2016 17 AndhraPradeshsudhir_narang_3Ainda não há avaliações
- 07 Drawer RunnersDocumento20 páginas07 Drawer RunnersngotiensiAinda não há avaliações
- Diego 1Documento22 páginasDiego 1acs_spAinda não há avaliações
- DC and AC Machines Lab ManualDocumento68 páginasDC and AC Machines Lab ManualGhilman HabibAinda não há avaliações
- CR EstimateDocumento307 páginasCR EstimateGani AnosaAinda não há avaliações
- Unit QuestionsDocumento155 páginasUnit QuestionsSanya KhanAinda não há avaliações
- Dam From: Safety Valve For A DamDocumento28 páginasDam From: Safety Valve For A DamRashmi SahooAinda não há avaliações
- ABB Timers and Controls, Express ProductsDocumento89 páginasABB Timers and Controls, Express ProductsElias100% (1)
- Smart Four Channel Highside Power Switch: BTS711L1Documento17 páginasSmart Four Channel Highside Power Switch: BTS711L1Giapy Phuc TranAinda não há avaliações