Escolar Documentos
Profissional Documentos
Cultura Documentos
Design Analysis of Algorithms
Enviado por
JanPatrik GuarinDescrição original:
Direitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
Design Analysis of Algorithms
Enviado por
JanPatrik GuarinDireitos autorais:
Formatos disponíveis
GREEDY
ALGORITHMS
Greedy algorithms are often employed in optimization problems where it can be proved that a greedy choice selection results in an optimal solution to the given problem. An optimization problem is one in which you want to find, not just a solution, but the best solution. Greedy algorithms do not always yield optimal solutions, but for many problems they do. A greedy algorithm always makes the choice that looks best at the moment. It works in phases. At each phase: You take the best you can get right now, without regard for future consequences. You hope that by choosing a local optimum at each step, you will end up at a global optimum. Example 1: Counting Money - Suppose you want to count out a certain amount of money, using the fewest possible bills and coins. E.g. A: For US money, the greedy algorithm always gives the optimum solution. At each step, take the largest possible bill or coin that does not overshoot: To make $6.39, you can choose: a $5 bill + a $1 bill (to make $6) + a 25 coin (to make $6.25) + a 10 coin (to make $6.35) + four 1 coins (to make $6.39) E.g. B: Failure of Greedy Algorithm in Counting Money - In some (fictional) monetary system, krons come in 1 kron, 7 kron, and 10 kron coins. Using a greedy algorithm to count out 15 krons, you would get: a 10 kron piece and five 1 kron pieces, for a total of 15 krons. This requires six coins.
1|Design Analysis of Algorithms
A better solution would be to use two 7 kron pieces and one 1 kron piece. This only requires three coins. The greedy algorithm results in a solution, but not in an optimal solution.
Greedy Algorithms: o o Huffman Encoding Algorithm Dijkstras algorithm for finding the shortest path in a graph o o Always takes the shortest edge connecting a known node to an unknown node Kruskals algorithm for finding a minimum-cost spanning tree Always tries the lowest-cost remaining edge Always takes the lowest-cost edge between nodes in the spanning tree and nodes not yet in the spanning tree Prims algorithm for finding a minimum-cost spanning tree
Example 2: Job Scheduling We want to schedule given n jobs. Job i requires running time ti Find the best order to execute the jobs to minimize the average completion time Sample input: (J1, 10), (J2, 4), (J3, 5), (J4, 12), (J5, 7) One possible schedule: J3, J2, J1, J5, J4. Total completion time = 5+9+19+26+38= 97 Optimal schedule: J2, J3, J5, J1, J4 Total completion time = 4+9+16+26+38 = 93
2|Design Analysis of Algorithms
Greedy Scheduling Algorithm Schedule the job with smallest running time first. Schedule jobs in increasing order of running times. Correctness: Suppose scheduling order is i1, , in. If tij > tij+1, then swap jobs ij and ij+1: Completion times for jobs before ij and ij+1 do not change Time of job ij increases by tij+1 Time of job ij+1 decreases by tij So total completion time decreases by tij- tij+1
Thus, optimal completion time can happen only if the list i1, , in is sorted.
Multiprocessor Case Suppose that jobs can be scheduled on k processors. Same intuition: since running times of earlier jobs contribute to completion times of latter jobs, schedule shorter jobs first. Algorithm: Sort jobs in increasing order of running times: i1, , in. Schedule i1 on processor P1, i2 on Pi2, , ik on Pk, ik+1 on Pk+1, and so on in a cycle Sample input: (J1, 10), (J2, 4), (J3, 5), (J4, 12), (J5, 7) and 2 processors Solution: J2, J5, J4 on P1; J3, J1 on P2 Total completion time: (4+11+23)+(5+15)=58
3|Design Analysis of Algorithms
Final Completion Time Suppose we want to minimize the maximum completion time instead of total (or average) completion time makes sense only in multiprocessor case
Scheduling shorter job first does not seem to have any advantage In fact, previous greedy algorithm does not give optimal solution Optimal solution: J1, J2, J3 on P1; J4, J5 on P2. Final completion time =19 In fact, no greedy strategy works. We may be forced to try out all possible ways to split jobs among processors. This is an NP-complete problem!
guarin
4|Design Analysis of Algorithms
BINARY
SEARCH
TREES
Introduction: Binary Tree o o o An Abstract Data Type (ADT) that is hierarchical in nature. Collection of nodes which are either empty or consists of a root and two disjoint binary trees called the left and the right subtrees. A binary tree could be empty or could only have one node (the root).
Terms: Root - special parent node, i.e. Parent - immediate node of a node or nodes, i.e. is the parent of nodes and ; is the parent of node Child - any node that has a parent node, i.e. and are the children of node . If two nodes have the same parents, they are said to be siblings. Degree - number of non-null subtrees of a node. If a node has degree zero, it is classified as a leaf or a terminal node. Level of a node - distance of the node from the root. The root of the tree has level 0, its subtrees at level 1 and so on.
5|Design Analysis of Algorithms
Height or depth of a tree - level of the bottommost nodes; length of the longest path from the root to any leaf. The height of the example tree is 3.
External node - node w/o children, i.e. nodes , , , and ; internal otherwise.
Types of Binary Tree A right ( left ) skewed binary tree is a tree in which every node has no left (right) subtrees. For a given number of nodes, a left or right-skewed binary tree has the greatest depth.
A strictly binary tree is a tree in which every node has either two subtrees or none at all.
6|Design Analysis of Algorithms
A full binary tree is a strictly binary tree in which all terminal nodes lie at the bottommost level. For a given depth, this tree has the maximum number of nodes.
A complete binary tree is a tree which results when zero or more nodes are deleted from a full binary tree in reverse-level order, i.e. from right to left, bottom to top.
Binary Tree Traversals Computations in binary trees often involve traversals. Traversal is a procedure that visits the nodes of the binary tree in a linear fashion such that each node is visited exactly once, where visit is defined as performing computations local to the node. There are three ways to traverse a tree: preorder, inorder, postorder. The prefix (pre, in and post) refers to the order in which the root of every subtree is visited.
7|Design Analysis of Algorithms
Preorder Traversal In preorder traversal of a binary tree, the root is visited first. Then the children are traversed recursively in the same manner. This traversal algorithm is useful for applications requiring listing of elements where the parents must always come before their children. The Method: If the binary tree is empty, do nothing (traversal done) Otherwise: Visit the root. Traverse the left subtree in preorder. Traverse the right subtree in preorder.
Inorder Traversal The inorder traversal of a binary tree can be informally defined as the left-to-right traversal of a binary tree. That is, the left subtree is recursively traversed in inorder, followed by a visit to its parent, then finished with recursive traversal of the right subtree also in inorder. The Method: If the binary tree is empty, do nothing (traversal done) Otherwise: Traverse the left subtree in inorder. Visit the root. Traverse the right subtree in inorder.
8|Design Analysis of Algorithms
Postorder Traversal Postorder traversal is the opposite of preorder, that is, it recursively traverses the children first before their parents. The Method: If the binary tree is empty, do nothing (traversal done) Otherwise: Traverse the left subtree in postorder. Traverse the right subtree in postorder. Visit the root.
9|Design Analysis of Algorithms
Main: Searching o An application of the ADT Binary Tree. By enforcing certain rules on the values of the elements stored in a binary tree, it could be used to search and sort. Consider the sample binary tree shown below:
The value of each node in the tree is greater than the value of the node in its left (if it exists) and it is less than the value in its right child (also, if it exists). In binary search tree, this property must always be satisfied.
Operations on Binary Search Trees o The most common operations on BSTs are insertion of a new key, deletion of an existing key, searching for a key and getting the data in sorted order. o In the first three operations, it is an assumption that the binary search tree is not empty and it does not store multiple values. Also, the node structure BSTNode(left, info, right), as illustrated below, is used:
Searching In searching for a value, say k, three conditions are possible: k = value at the node (successful search) k < value at the node (search the left subtree) k > value at the node (search the right subtree)
10 | D e s i g n A n a l y s i s o f A l g o r i t h m s
The same process is repeated until a match is found or the farthest leaf is reached but no match is found. In the case of the latter, the search is unsuccessful. Insertion In inserting a value, searching is performed in finding its proper location in the tree. However, if during the search process the key is found, the insertion will not be performed. The following is the algorithm: 1. Start the search at the root node. Declare a node p and make it point to the root. 2. Do the comparison: if (k == p.info) return false // if key found, insertion not allowed else if (k < p.info) p = p.left // go left else p = p.right // if (k > p.info) go right 3. Insert the node (p now points to the new parent of node to insert): newNode.info = k newNode.left = null newNode.right = null if (k < p.info) p.left = newNode else p.right = newNode Deletion Deleting a key from the binary search tree is a bit more complex than the other two operations just discussed. The operation starts by finding the key to delete. If not found, the algorithm simply returns to tell that deletion fails. If the search returns a node, then there is a need to delete the node that contains the key that we searched for. However, deletion is not as simple as removing the node found since it has a parent pointing to it. It is also a big possibility that it is the parent of some other nodes in the binary search tree. In this case, there is a need to have its children adopted by some other node, and the pointers pointing to it should also be adjusted. And in the process of reassigning pointers, the BST property of the order of the key values has to be maintained. 11 | D e s i g n A n a l y s i s o f A l g o r i t h m s
There are two general cases to consider in deleting a node d: 1. Node d is an external node(leaf): Action: update the child pointer of the parent p: if d is a left child, set p.left = null otherwise, set p.right = null
Deletion of a leaf node
2. Node is internal (there are two subcases): Case 1: If d has a left subtree, 1. Get the inorder predecessor, ip. Inorder predecessor is defined as the rightmost node in the left subtree of the current node, which in this case is d. It contains the preceding key if the BST is traversed in inorder. 2. Get the parent of ip, say p_ip. 3. Replace d with ip. 4. Remove ip from its old location by adjusting the pointers: a. If ip is not a leaf node: 1. Set the right child of p_ip to point to the left child of ip 2. Set the left child of ip to point to the left child of d b. Set the right child of ip to point to the right child of d
12 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Deletion of an internal node with a left subtree
Case 2: If d has no left son but with a right subtree 1. Get the inorder successor, is. Inorder successor is defined as the leftmost node in the right subtree of the current node. It contains the succeeding key if the BST is traversed in inorder. 2. Get the parent of is, say p_is. 3. Replace d with is. 4. Remove is from its old location by adjusting the pointers: a. If is is not a leaf node: 3. Set the left child of p_is to point to the right child of is 4. Set the right child of is to point to the right child of d b. Set the left child of is to point to the left child of d
Deletion of an internal node with no left subtree
13 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Balanced Binary Search Tree o o A tree is balanced if, at each node, the heights of the left and right subtrees differ by at most one. One of the most commonly used balanced BST is the AVL tree. It was created by G. Adelson-Velskii and E. Landis, hence the name AVL. An AVL tree is a height-balanced tree wherein the height difference between the subtrees of a node, for every node in the tree, is at most 1. o Consider the binary search trees below where the nodes are labelled with the balance factors:
Binary search trees A, C and D all have nodes with balances in the range [-1, 1], i.e., -1,0 and +1. Therefore, they are all AVL trees. BST B has a node with a balance of +2, and since it is beyond the range, it is not an AVL tree. Tree Balancing: In maintaining the balance of an AVL tree, rotations have to be performed during insertion and deletion. The following are the rotations used: o Simple right rotation (RR) used when the new item C is in the left subtree of the left child B of the nearest ancestor A with balance factor +2
14 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Simple left rotation (LR) used when the new item C is in the right subtree of the right child B of the nearest ancestor A with balance factor -2
Left-right rotation (LRR) used when the new item C is in the right subtree of the left child B of the nearest ancestor A with balance factor +2
Right-left rotation (RLR) used when the new item C is in the left subtree of the right child B of the nearest ancestor A with balance factor -2
15 | D e s i g n A n a l y s i s o f A l g o r i t h m s
MORE... Example 1:
16 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Insertion into an AVL Tree
17 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Example 2: Insert the following keys in an AVL tree, based on the order given: ARFGEYBXCSTIOPLV
18 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Example 3: guarin A Binary Tree A
C E F
N Application of Traversals Preorder: Inorder: Postorder: ABDGJKEHCFILNM JGKDBHEAFLNIMC JKGDHEBNLMIFCA
Balancing: 1 6 7 4 2 5 8 9 0 3 Insert 1 1 Insert 6 1 6 1 Insert 7 6 7
19 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Insert 4 6 1 7 1
Insert 2 6 2 7
Insert 5 4 2 6
Insert 8 4 2 6
20 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Insert 9 4 2 6
Insert 0 4
7 Insert 3 4
21 | D e s i g n A n a l y s i s o f A l g o r i t h m s
KRUSKALS
ALGORITHM
Introduction: Graphs o A graph, G = ( V, E ), consists of a finite, non-empty set of vertices (or nodes), V, and a set of edges, E. The following are examples of graph:
An undirected graph is a graph in which the pair of vertices representing an edge is unordered, i.e.,( i,j ) and (j,i) represent the same edge.
Two vertices i and j are adjacent if (i, j) is an edge in E. The edge (i, j) is said to be incident on vertices i and j.
22 | D e s i g n A n a l y s i s o f A l g o r i t h m s
A complete undirected graph is a graph in which an edge connects every pair of vertices. If a complete undirected graph has n vertices, there are n(n -1)/2 edges in it.
A directed graph or digraph is a graph in which each edge is represented by an ordered pair <i, j>, where i is the head and j is the tail of the edge. The edges <i,j> and <j,i> are two distinct edges.
A complete directed graph is a graph in which every pair of vertices i and j are connected by two edges <i,j> and <j,i>. There are n(n-1) edges in it.
23 | D e s i g n A n a l y s i s o f A l g o r i t h m s
A subgraph of an undirected (directed) graph G = (V,E) is an undirected (directed) graph G = (V,E) such that V V and E E.
A weighted graph is a graph with weights or costs assigned to its edges.
Minimum Cost Spanning Tree (MST) o A subgraph of a given graph G, in which all the vertices are connected and has the lowest cost. This is particularly useful in finding the cheapest way to connect computers in a network, and in similar applications. MST Theorem o Let G = (V,E) be a connected, weighted, undirected graph. Let U be some proper subset of V and (u, v) be an edge of least cost such that u U and v (V U). There exists a minimum cost spanning tree T such that (u, v) is an edge in T. A Greedy Approach: Kruskals Algorithm 24 | D e s i g n A n a l y s i s o f A l g o r i t h m s
A greedy algorithm that is used to find the MST was developed by Kruskal. In this algorithm, the vertices are listed in non-decreasing order of the weights. The first edge to be added to T, which is the MST, is the one that has the lowest cost. An edge is considered if at least one of the vertices is not in the tree found so far.
Now the algorithm: Let G = (V, E) be a connected, weighted, undirected graph on n
vertices. The minimum cost spanning tree, T, is built edge by edge, with the edges considered in non-decreasing order of their cost. 1. Choose the edge with the least cost as the initial edge. 2. The edge of least cost among the remaining edges in E is considered for inclusion in T. If cycle will be created, the edge in T is rejected. EXAMPLE 1:
The following shows the execution of Kruskal's algorithm in solving the MST problem of the graph above:
25 | D e s i g n A n a l y s i s o f A l g o r i t h m s
26 | D e s i g n A n a l y s i s o f A l g o r i t h m s
27 | D e s i g n A n a l y s i s o f A l g o r i t h m s
The result of applying Ruskals Algorithm: Since all the vertices are already in U, MST has been obtained. The algorithm resulted to MST of cost 33. In this algorithm, one major factor in the computational cost is sorting the edges in nondecreasing order. 28 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Example 2: Find the minimum cost spanning tree of the following graphs using Kruskals algorithm. Give the cost of the MST.
Edges (c,d) 1 (b,e) 2 (e-d) 3 (e,c) 4 (b,f) 5 (b-d) 6 (f-d) 6 (c,b) 8 (a,b) 9 (a,c) 10 (c,d) 1 Accept (b,e) 2 (e-d) 3 (e,c) 4 (b,f) 5 (b-d) 6 (f-d) 6 (c,b) 8 (a,b) 9 (a,c) 10 (c,d) 1 * (b,e) 2 (e-d) 3 Accept (e,c) 4 (b,f) 5 (b-d) 6 (f-d) 6 (c,b) 8 (a,b) 9 (a,c) 10 (c,d) 1
MST ---
V-U a, b, c, d, e, f
c, d
b, a, e, f
1 a (c,d) 1 (e,d) 3 3 a c, d, e b, a, f
1 a
29 | D e s i g n A n a l y s i s o f A l g o r i t h m s
(c,d) 1 * (b,e) 2 Accept (e-d) 3 * (e,c) 4 (b,f) 5 (b-d) 6 (f-d) 6 (c,b) 8 (a,b) 9 (a,c) 10
(c,d) 1 (e,d) 3 (b,e) 2 b 2 c e 3 a d
c, d, e, b
a, f
(c,d) 1 * (b,e) 2 * (e-d) 3 * (e,c) 4 Reject (b,f) 5 Accept (b-d) 6 (f-d) 6 (c,b) 8 (a,b) 9 (a,c) 10
(c,d) 1 (e,d) 3 (b,e) 2 (b,f) 5
1 a
c, d, e, b, f 5 a
b 2 c e
3 a
(c,d) 1 * (b,e) 2 * (e-d) 3 * (e,c) 4 Reject (b,f) 5 * (b-d) 6 Reject (f-d) 6 Reject (c,b) 8 Reject (a,b) 9 Accept (a,c) 10 Reject
(c,d) 1 (e,d) 3 (b,e) 2 (b,f) 5 (a,b) 9 a 9
1 a
c, d, e, b, f, a
---
b 2
5 a
3 a
1 a guarin
30 | D e s i g n A n a l y s i s o f A l g o r i t h m s
Você também pode gostar
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNo EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryNota: 3.5 de 5 estrelas3.5/5 (231)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)No EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Nota: 4.5 de 5 estrelas4.5/5 (121)
- Never Split the Difference: Negotiating As If Your Life Depended On ItNo EverandNever Split the Difference: Negotiating As If Your Life Depended On ItNota: 4.5 de 5 estrelas4.5/5 (838)
- The Little Book of Hygge: Danish Secrets to Happy LivingNo EverandThe Little Book of Hygge: Danish Secrets to Happy LivingNota: 3.5 de 5 estrelas3.5/5 (400)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNo EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaNota: 4.5 de 5 estrelas4.5/5 (266)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNo EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeNota: 4 de 5 estrelas4/5 (5794)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNo EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreNota: 4 de 5 estrelas4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyNo EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyNota: 3.5 de 5 estrelas3.5/5 (2259)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNo EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersNota: 4.5 de 5 estrelas4.5/5 (345)
- The Emperor of All Maladies: A Biography of CancerNo EverandThe Emperor of All Maladies: A Biography of CancerNota: 4.5 de 5 estrelas4.5/5 (271)
- Team of Rivals: The Political Genius of Abraham LincolnNo EverandTeam of Rivals: The Political Genius of Abraham LincolnNota: 4.5 de 5 estrelas4.5/5 (234)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNo EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceNota: 4 de 5 estrelas4/5 (895)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNo EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureNota: 4.5 de 5 estrelas4.5/5 (474)
- The Yellow House: A Memoir (2019 National Book Award Winner)No EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Nota: 4 de 5 estrelas4/5 (98)
- The Unwinding: An Inner History of the New AmericaNo EverandThe Unwinding: An Inner History of the New AmericaNota: 4 de 5 estrelas4/5 (45)
- Linear and Nonlinear ProgrammingDocumento7 páginasLinear and Nonlinear ProgrammingLogan J. RabuogiAinda não há avaliações
- Quiz - Weekly Quiz 2 PDFDocumento5 páginasQuiz - Weekly Quiz 2 PDFanswer2myqueries100% (1)
- RS 1Documento15 páginasRS 1AbdallahAinda não há avaliações
- A Novel Hybrid PSO-PS Optimized Fuzzy PI Controller For AGC SeeDocumento14 páginasA Novel Hybrid PSO-PS Optimized Fuzzy PI Controller For AGC SeeMushtaq Najeeb AhmedAinda não há avaliações
- Turbo Codes For Multi-Hop Wireless Sensor Networks With Dandf MechanismDocumento30 páginasTurbo Codes For Multi-Hop Wireless Sensor Networks With Dandf Mechanismjeya1990Ainda não há avaliações
- Algebra Treasure HuntDocumento4 páginasAlgebra Treasure HuntKazi Rafshan HasinAinda não há avaliações
- Quantitative Methods AssignmentDocumento9 páginasQuantitative Methods AssignmentnadineAinda não há avaliações
- Math 2311: Introduction To Probability and Statistics Course SyllabusDocumento3 páginasMath 2311: Introduction To Probability and Statistics Course SyllabusRaymond RamirezAinda não há avaliações
- Automata Final PDFDocumento12 páginasAutomata Final PDFAfn TariqAinda não há avaliações
- Huawei CE Utilization GuidelineDocumento3 páginasHuawei CE Utilization Guidelinerizal011188412Ainda não há avaliações
- Learning of Alphabets Using Kohonen's Self Organized Featured MapDocumento5 páginasLearning of Alphabets Using Kohonen's Self Organized Featured MapInternational Journal of Application or Innovation in Engineering & ManagementAinda não há avaliações
- Class Imbalance NotesDocumento6 páginasClass Imbalance NotesGokul RajendranAinda não há avaliações
- Design of Decoupled Pi Controllers For Two-Input Two-Output Networked Control Systems With Intrinsic and Network-Induced Time DelaysDocumento8 páginasDesign of Decoupled Pi Controllers For Two-Input Two-Output Networked Control Systems With Intrinsic and Network-Induced Time DelaysAnuj ShahaneAinda não há avaliações
- Artificial Intelligence Lecture No. 5Documento42 páginasArtificial Intelligence Lecture No. 5Sarmad RehanAinda não há avaliações
- Forecasting Dengue Fever Using Machine Learning Regression TechniquesDocumento8 páginasForecasting Dengue Fever Using Machine Learning Regression TechniquesCorina Erika Navarrete MacedoAinda não há avaliações
- Portfolio Data CleaningDocumento39 páginasPortfolio Data CleaningShaurya JainAinda não há avaliações
- 4.2.7 DictionariesDocumento16 páginas4.2.7 DictionariesarchiehankeyAinda não há avaliações
- Data Structure Lab-222Documento13 páginasData Structure Lab-222Rahul SinghAinda não há avaliações
- An Efficient Incremental Clustering AlgorithmDocumento3 páginasAn Efficient Incremental Clustering AlgorithmWorld of Computer Science and Information Technology JournalAinda não há avaliações
- International Journal of Science and Research (IJSR) ISSN (Online) 2319-7064Documento4 páginasInternational Journal of Science and Research (IJSR) ISSN (Online) 2319-7064agha wijayaAinda não há avaliações
- VU-Assignment CS101Documento3 páginasVU-Assignment CS101mc220203866 JAWAD SARWARAinda não há avaliações
- 4985.practical Optimization. Algorithms and Engineering Applications by Andreas AntoniouDocumento2 páginas4985.practical Optimization. Algorithms and Engineering Applications by Andreas AntoniouRuby ChanAinda não há avaliações
- Navo Minority Over-Sampling Technique (Nmote) : A Consistent Performance Booster On Imbalanced DatasetsDocumento42 páginasNavo Minority Over-Sampling Technique (Nmote) : A Consistent Performance Booster On Imbalanced DatasetsHeri SetiawanAinda não há avaliações
- ISOM 2600: Introduction To Business AnalyticsDocumento2 páginasISOM 2600: Introduction To Business AnalyticsHo Ming ChoAinda não há avaliações
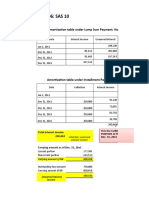
- Acc 106 P3 LessonDocumento6 páginasAcc 106 P3 LessonRowella Mae VillenaAinda não há avaliações
- Integer Multiplication and AccumulationDocumento5 páginasInteger Multiplication and Accumulationue06037Ainda não há avaliações
- UEMK3313 Chemical Process Control and InstrumentationDocumento4 páginasUEMK3313 Chemical Process Control and InstrumentationRama KrishnaAinda não há avaliações
- Midterm Exam 2 SPRING 2020Documento7 páginasMidterm Exam 2 SPRING 2020AbdulazizAinda não há avaliações
- Spoiler Detection & Early Spoiler AvoidanceDocumento7 páginasSpoiler Detection & Early Spoiler AvoidanceIJRASETPublicationsAinda não há avaliações