Escolar Documentos
Profissional Documentos
Cultura Documentos
Abi Research Utm Vendor Ranking
Enviado por
oracleidmDescrição original:
Direitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
Abi Research Utm Vendor Ranking
Enviado por
oracleidmDireitos autorais:
Formatos disponíveis
ABIresearch
(Vendor Matrix)
Enterprise Security: Unified Threat Management Vendor Matrix: Excerpt
Subha Rama
Senior Analyst, Enterprise Communications
Juniper Networks Company Profile
The SRX series services gateways of Juniper Networks Inc, along with the J-series routers and the SSG Secure Services Gateways (SSG), offer multiple security functions such as anti-virus, anti-spam, web filtering, and IDS deep inspection/IPS. While all of these products have high visibility in the large enterprise and carrier markets, the SSG product line has considerable presence among the SMBs as well. Junipers secure firewall/VPN appliances and routers incorporate UTM features that are delivered in partnership with niche vendors. Junipers integrated anti-virus solution, comprising anti-spyware, antiadware, and anti-phishing, is from Kaspersky Lab, with web filtering from Websense and the integrated anti-spam solution from Sophos. Junipers Adaptive Threat Management (ATM) solutions offer a highly modular deployment model and risk mitigation capabilities in an open and standards-based environment, features that have found a high level of acceptance among key verticals such as Government, Education, and Healthcare. Though network infrastructure vendors tend to bundle security with infrastructure sales, Juniper also has achieved considerable visibility among non-network customers, who are increasingly evaluating its security solutions independent of their infrastructure buying decisions. (continued page 2)
Innovation: Implementation:
78 76
Juniper Networks places in the 100th percentile of those 9 companies examined. This company is highest rated company along the Innovation scale. This company is highest rated company along the Implementation scale.
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
Section 1.
1.1
COMPANY PROFILE (CONTINUED FROM PAGE 1)
IMPLEMENTATION
A key feature of Junipers ATM solutions is that they support a pay-as-you-grow model, allowing significant flexibility in customer deployments while simultaneously helping them reduce Total Cost of Ownership (TCO). The SSG line of products delivers a rich set of UTM features specifically designed for branch office security. A simple built-in feature allows easy update of firmware and the latest signatures, facilitating easy management. The products ensure granular control over zones, policies, objects, users, groups, protocols, services, source and destination IP addresses with advanced screening, profile, and filtering options that help to protect both the endpoints and the networks. Juniper scores well on Implementation, especially for the following parameters: Product Integration and Support The UTM products integrate a complete suite of security features that include a stateful firewall, IPS, application security, anti-virus, anti-spam, antiphishing, anti-adware, and anti-spyware. Centralized management software simplifies deployment and updates. Quick deployment features of Auto Connect VPN and Dynamic VPN help administrators overcome the bottlenecks associated with IPSec implementations. Seamless integration of IPS functionality across all products with in-depth analysis of application protocol, context, state, and behavior help mitigate zero-day attacks.
Total Solutions Quotient Approach to total solutions enablement through partner ecosystem development, and alliances with key vendors: Juniper has extensive relationships with multiple partners and solutions vendors for both channel and technology capabilities. Juniper has a longstanding relationship with Symantec for developing and delivering best-in-class UTM solutions that are standards-based. Junipers J-Security Team and Symantec's Global Intelligence Network collaborate to deliver security and threat research to their customers. Juniper also provides integrated file-based anti-virus remediation from Kaspersky Lab on the Juniper Networks SSG series and the SRX series Services Gateways for branches.
Market Leadership, Strength, and Experience Level of penetration/share in key vertical and application markets: Juniper has seen consistent high growth in its UTM revenues largely due to exceptional performance, and mature products that have helped the vendor emerge as a value differentiator in a highly competitive market which is displaying a fair degree of price sensitivity. Juniper also has been winning a substantial number of deals in environments running non-Juniper network gear, indicative of the unique mindshare it commands for its security portfolio.
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
1.2
INNOVATION
Juniper has consistently nurtured innovation across its security products portfolio through in-house product development as well as through strategic acquisitions. The latest addition to the SSG product line, the SRX1400 gateway, is scalable to suit a variety of environments, from a small business to a carrier data center. Juniper scores well on the Innovation axis along the following parameters: Industry Leadership, Influence Factor, and Knowledge Transfer Junipers core network infrastructure and security solutions are behind the most demanding networks in the world, including the New York Stock Exchange and Facebook. Through a number of industry partnerships, Juniper is promoting innovation, interoperability, and open standards. Junos OS, a single operating system that runs across the switching, routing, and security solutions, has been key in streamlining network operations and lower TCO for enterprises as well as service providers. The Junos One family of processors has been consistently raising the bar on network performance, setting new industry standards. Juniper has also announced interoperability of its IP networking solutions with Lync, the Microsoft UC platform, ensuring optimal performance of the UC solution in Juniper network environments. Juniper has developed a number of new application areas, including Junos Pulse, an integrated network client that enables network security, access, and application acceleration for both mobile and non-mobile devices. This, coupled with the acquisition of SMobile Systems, a mobile security applications provider, has helped Juniper to offer a more unified solution for mobile endpoints. Junipers entry into the mobile device security market addresses the growing need for device security among enterprise end users. Junos Pulse will also help wireless carriers offer a set of mobile security solutions and result in higher value-add to their revenue streams.
New Application Enablement
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
Innovation 78 76 74 73 72 70 70 61 61 Implementation 76 75 74 69 68 67 67 55 53
(Source: ABI Research)
Section 2.
Rank 1 2 3 4 5 6 7 8 9
RANKINGS
Company Juniper Networks Inc. Fortinet Cicso Systems Inc. Check Point Software Technologies Inc. SonicWALL, Inc. WatchGuard Technologies McAfee Inc Cyberoam NetASQ
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
Section 3.
3.1
METHODOLOGY
Introduction
The rapid growth in the Unified Threat Management (UTM) appliances market is driven by the need for enterprises to consolidate their network security infrastructure, realize cost savings and achieve better operational and management efficiencies. UTM devices are those that offer a set of security features built around a hardened (out-of-the box) Operating System (OS). Many of these devices combine security and policy management features, along with quality of service and load-balancing attributes. Adoption of UTM devices is on the rise as security threats diversify in nature and companies are forced to deploy multiple countermeasures. UTM devices that comprise diverse security applications such as anti-virus, firewalls, intrusion detection, and spam filters coupled with management features have driven adoption among both large enterprises and small and medium businesses (SMB). UTM device vendors have introduced a number of common differentiators that focus on: Form factor. Ease and simplicity of installation. Advanced predictive functionality that anticipates emerging market needs. Many of these devices have features for network security (firewalls, IDS/IPS, VPN), web security (anti-virus, URL filters) and e-mail security (spam filter, anti-virus and IM controls, and security). Local storage. Modularity, allowing users to turn on specific features and multiple throughput options with varying price points. Attractive bundled pricing.
However, some vendors are known to brand their advanced firewall systems as UTM devices though these may differ significantly from what is outlined above. UTM devices have evolved over time and some vendors are increasingly incorporating identity management, Voice over IP (VoIP). and Unified Communications (UC) security, and Network Access Control (NAC) functions, especially for branch office deployments. VoIP and UC applications present unique challenges as security features designed for these applications should be designed in such a way that they do not inject packet loss and jitter in the network, which may adversely impact the delivery of real-time media. There is a confusing array of pricing in the market today and this is largely due to the expanding functionality of these devices. Customers demand network IPS sensors with wireline speed performance since inline security controls can negatively affect network performance.
3.1.1
UTM Market Growth
In 2010, the UTM market saw a 10.6% growth in revenue, largely due to the fact that the increasing number of threats to enterprise networks makes it impossible to deploy a dedicated device to address each one of them. The UTM concept resonated well in the SMB market in its early days, as these businesses did not have the resources to manage security infrastructure sprawl. Though large enterprises with best-of-breed equipment did not see any value in deploying UTM devices at first, this is changing as vendors have added advanced firewall and IPS functionality to these devices. Given that UTMs, with their lower pricing and modular design, can significantly reduce
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
CAPEX, they are being deployed as dedicated appliances (for a single functionality) by large enterprises. UTM products have had a long gestation period and need some unique skills in their design and implementation. Symantec, which was one of the first security vendors to introduce a UTM-type product, ended support for its UTM appliances in 2006 and transferred the customer base to Juniper. Enterprises predominantly opt for best-of-breed technologies when implementing security. This not only escalates cost but also creates management challenges with multiple devices and solution sets at headquarters and branches. For enterprise deployments, vendors tend to stress Total Cost of Ownership (TCO) benefits. However, unified management is fast emerging as a critical influence. A single management system that can deliver information across multiple UTM devices coupled with a high degree of intuitiveness and full life-cycle management functions that range from configuration to monitoring and troubleshooting, is considered invaluable in the enterprise scenario. For example, the Cisco Adaptive Security Appliance, the ASA 5500 series IPS Editions, offers a Cisco management and monitoring suite that facilitates large-scale deployment and operation. The Cisco Adaptive Security Device Manager (ASDM) provides browser-based management and monitoring interfaces for individual devices. The Fortinet FortiManager and FortiAnalyzer appliances offer a centralized management solution for enterprises, regardless of the number of branch offices or remote locations they may have.
3.2
DESCRIPTION OF CRITERIA
Criteria used to develop this UTM Vendor Matrix are related to product and company characteristics that serve as proxies for vendor performance in the areas of Innovation and Implementation. Numerical scores are aggregated, weighted, and analyzed to provide overall rankings that are assigned to each vendor on the Innovation and Implementation axes.
3.3
Innovation
The eight Innovation scoring criteria and their associated weightings are: 1. Scope of the UTM offering (10% weight) Evaluates the breadth of UTM solution offerings and capabilities (narrow, partial, or complete) Evaluates breadth of application support (broad or limited)
2. Product Innovation I Offering (25% weight) Evaluates degree of specialization (narrow or broad) Evaluates product considerations (number of security features, bundling) Evaluates UTM architectures, performance features such as throughput, performance resilience (when multiple features are turned on), and scalability Availability of load-balancing features to accommodate the processor needs of different security applications
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
Availability of applications for managing enterprise-wide UTM deployments, and ability of the management software to work across third-party solutions as well Additional consideration for awards/recognition for product excellence Slow product launches or upgrades and inadequate QoS considerations have negative impact on ratings
3. Product Innovation II Partner and VAR Enablement (15% weight) Evaluates ability to offer a complete suite of solutions that addresses many of the network and content security needs of enterprises Evaluates ability to allow third-party solution integration with the core UTM platform
4. Scalability and Flexibility (10% weight) Evaluates level of robustness and the ability of the product to scale Evaluates demonstrating flexibility, extendibility, and ability to scale in realworld environments (proof points/use cases are critical considerations) Additional consideration for strong vendor core competencies and skill sets
5. Application and Vertical Market Leadership, Alignment, and Innovation (20% weight) Evaluates leadership within verticals and applications; depth and breadth of application focus and specialization; and innovation across multiple products and vertical markets (weak, moderate, or strong)
6. Overall Vendor Strategy, Vision, and Approach (5% weight) Evaluates strategies for the deployment of UTM devices comprising multiple, key security features Additional consideration for clear vision and strength of management team Additional consideration for clear vision and product alignment with market needs Additional consideration for synergy between expressed vision and offered products
7. Industry Leadership, Influence Factor, and Knowledge Transfer (10% weight) Evaluates involvement in leading trials and deployments Evaluates involvement in industry groups/associations (both security and end-user) Evaluates participation in UTM education and awareness campaigns Evaluates length of time in the UTM and network security space Evaluates perceived level of influence in the space
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
8. New Application Enablement (5% weight) Evaluates focus on developing/enabling new application areas Evaluates capabilities to enable turnkey solutions for new applications Evaluates development tools/programs available to partners to enable new applications
3.4
Implementation
The nine Implementation scoring criteria and their associated weightings are: 1. Breadth and Strength of Vertical Markets Served/Targeted (10% weight) Evaluates vendor specialization within vertical markets as well as number of vertical markets served/targeted Evaluates strength/leadership position within those verticals Additional consideration for alliances with key vertically aligned industry associations, regulatory bodies, and so forth.
2. Breadth and Strength of Solutions in the Markets Served/Targeted (10% weight) Evaluates vendor specialization within specific application markets as well as number of applications served/targeted Evaluates strength/leadership position within those applications Additional consideration for strong ability to shift seamlessly vertically or horizontally targeted product offerings Additional consideration for alliances with key industry associations, regulatory bodies, and so on.
3. Product Integration and Support Capabilities (25% weight) Evaluates service integration capabilities and ability to support customers (weak, moderate, or strong)
4. Installed Base/Customer Deployments (25% weight) Evaluates strength of customer base and customer mix Evaluates types of deployments Evaluates typical size of deployments Evaluates visibility in deals/end-user proposals
5. Geographic Presence and Penetration (5% weight) Evaluates vendor presence and penetration in key regional markets, local support, and partner ecosystem (weak, moderate, or strong)
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
6. Total Solutions Quotient (5% weight) Evaluates approach to total solutions enablement through partner ecosystem development, and alliances with key security vendors Number of subscription services offered Additional consideration for providing customer support, security information, and event management through management software and dashboards
7. Partner Collaboration Quotient (5% weight) Evaluates overall partnering strategy and approach, including partner friendliness (approachability and receptivity) Evaluates overall diversity of channels Evaluates partner collaboration efforts such as cross-marketing and bringing partners into deals Additional consideration for partner/potential partner opinions shared with ABI Research
8. Partner Ecosystem Vendors, VARs, Integrators, Managed Security Service Providers (MSSP) (5% weight) Evaluates breadth and strength of vendor, VAR, integrator and MSSP partner network Evaluates depth and strength of those relationships considerations include vertical/horizontal and application specialization and synergy among partners Additional consideration for cross-marketing and messaging efforts
9. Overall Perceived Market Leadership, Strength, and Experience (5% weight) Evaluates level of market penetration and leadership through subjective and objective considerations such as: 1. Perceived level of penetration/share in key vertical/horizontal and application markets 2. Product support (professional and consulting services, break-fix and maintenance) 3. Perceived position in market relative to competition 4. Revenue growth (historical and forecast) 5. Financial strength, health, and backing 6. Company size 7. Positive word-of-mouth/momentum in industry
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
3.5
Scoring
Vendors receive a rating score for each ABI Research-defined criterion under Implementation and Innovation. These scores range from 0 to 9 and are based on available information as well as ABI Research assumptions. Points are awarded in 0.25 increments. For example, a score of 8.75 is possible within a given criterion. Each criterion (and its score) is weighted based on ABI Researchs opinion of each criterions level of influence on and importance to the overall assessment of Innovation and Implementation. The number of criteria for Implementation and Innovation may vary; however, this does not impact service provider ranking. Vendors receiving higher scores in higher weighted criteria will benefit in terms of better overall position. Lower scores in higher weighted categories will result in weaker overall placement due to the impact of the weighting. The rating scores assigned to each criterion are added to determine a raw total score for Implementation and Innovation. A mathematical formula is then applied to adjust for the 0 to 9 rating system and the number of criteria so that vendors can be positioned along the x- and y-axes (with a maximum score of 100 for Implementation and Innovation). The mathematical formula does not impact vendor ranking. It is ABI Researchs policy not to publicly disclose individual scores for each criterion for each vendor. However, we will accept requests to discuss a vendor's individual scores with that same provider.
3.6
Rankings
After individual scores are established for Innovation and Implementation using the above criteria, an overall company score is established using the Root Mean Square (RMS) method:
The resulting overall scores are then ranked and used for percentile comparisons. The RMS method, in comparison with a straight summation or average of individual innovation and implementation values, rewards companies for standout performance. For example, using this method a company with an innovation score of 9 and an implementation score of 1 would score considerably higher than a company with a score of 5 in both areas, despite the mean score being the same. ABI Research believes this is appropriate as the goal of these matrices is to highlight those companies that stand out from the others.
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
10
The Passive UHF RFID Reader Vendor Matrix
ABIresearch
Published March 17, 2011 2011 ABI Research PO Box 452 249 South Street Oyster Bay, NY 11771 USA Tel: +1 516-624-2500 Fax: +1 516-624-2501 http://www.abiresearch.com/analystinquiry.jsp
2011 ABI Research. Used by permission. Disclaimer: Permission granted to reference, reprint or reissue ABI Research products is expressly not an endorsement of any kind for any company, product, or strategy. ABI Research is an independent producer of market analysis and insight and this ABI Research product is the result of objective research by ABI Research staff at the time of data collection. ABI Research was not compensated in any way to produce this information and the opinions of ABI Research or its analysts on any subject are continually revised based on the most current data available. The information contained herein has been obtained from sources believed to be reliable. ABI Research shall have no liability for errors, omissions, or inadequacies in the information contained herein or for interpretations thereof. ABI Research disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. ALL RIGHTS RESERVED. No part of this document may be reproduced, recorded, photocopied, entered into a spreadsheet or information storage and/or retrieval system of any kind by any means, electronic, mechanical, or otherwise without the expressed written permission of the publisher. Exceptions: Government data and other data obtained from public sources found in this report are not protected by copyright or intellectual property claims. The owners of this data may or may not be so noted where this data appears. Electronic intellectual property licenses are available for site use. ABI Research to find out about a site license. Please call
2011 ABI Research abiresearch.com The material contained herein is for the individual use of the purchasing Licensee and may not be distributed to any other person or entity by such Licensee including, without limitation, to persons within the same corporate or other entity as such Licensee, without the express written permission of Licensor.
11
Você também pode gostar
- Industrial Network Security: Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control SystemsNo EverandIndustrial Network Security: Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control SystemsNota: 4.5 de 5 estrelas4.5/5 (5)
- Firewall-Features-Palo AltoDocumento6 páginasFirewall-Features-Palo AltojoseAinda não há avaliações
- Security Operations Center - Analyst Guide: SIEM Technology, Use Cases and PracticesNo EverandSecurity Operations Center - Analyst Guide: SIEM Technology, Use Cases and PracticesNota: 4 de 5 estrelas4/5 (1)
- Critical Capabilities For High-Security Mobility Management - Gartner - 24aug2017 PDFDocumento59 páginasCritical Capabilities For High-Security Mobility Management - Gartner - 24aug2017 PDFDJ JAMAinda não há avaliações
- Juniper(r) Networks Secure Access SSL VPN Configuration GuideNo EverandJuniper(r) Networks Secure Access SSL VPN Configuration GuideNota: 5 de 5 estrelas5/5 (1)
- Extremecontrol Data SheetDocumento5 páginasExtremecontrol Data Sheets9789144140Ainda não há avaliações
- CYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookNo EverandCYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookAinda não há avaliações
- Ericsson Network SecurityDocumento14 páginasEricsson Network SecuritytousifaslamAinda não há avaliações
- Securing You: SecuringyouDocumento4 páginasSecuring You: SecuringyouSorachut ChaithaneeAinda não há avaliações
- Firewall Features OverviewDocumento6 páginasFirewall Features OverviewRDNFO TIAinda não há avaliações
- FortiGate High End - Combined - LiteUpdate - 20210326Documento35 páginasFortiGate High End - Combined - LiteUpdate - 20210326Mohamed KalkoulAinda não há avaliações
- Securing The Virtual World: VirtualizationDocumento8 páginasSecuring The Virtual World: Virtualizationlinuxer6Ainda não há avaliações
- Genx CyberoamDocumento7 páginasGenx CyberoamVignesh RajendranAinda não há avaliações
- Unified Threat Management: International Research Journal of Engineering and Technology (IRJET)Documento5 páginasUnified Threat Management: International Research Journal of Engineering and Technology (IRJET)samir taydeAinda não há avaliações
- (R023C00) HUAWEI HiSecEngine USG6500F Series Firewalls DatasheetDocumento16 páginas(R023C00) HUAWEI HiSecEngine USG6500F Series Firewalls Datasheetalnavarr2Ainda não há avaliações
- FortiGuard Security ServicesDocumento8 páginasFortiGuard Security Servicesdoris marcaAinda não há avaliações
- CyberoAm UTMDocumento7 páginasCyberoAm UTMksibinpaulAinda não há avaliações
- Cellusys Signalling Firewall v6.7Documento4 páginasCellusys Signalling Firewall v6.7Lucky AmaanAinda não há avaliações
- ForeScout Company OverviewDocumento2 páginasForeScout Company OverviewIchwan SetiawanAinda não há avaliações
- Transforming Your Security: A New Era in Enterprise FirewallsDocumento14 páginasTransforming Your Security: A New Era in Enterprise Firewallsnirushan456Ainda não há avaliações
- Executive Summary: Beecham Research September 2014Documento3 páginasExecutive Summary: Beecham Research September 2014Rahul MoreAinda não há avaliações
- Endpoint Security - Best PracticeDocumento13 páginasEndpoint Security - Best PracticeRazafindrabeAinda não há avaliações
- Cellusys Signalling Firewall PDFDocumento4 páginasCellusys Signalling Firewall PDFWasim AliAinda não há avaliações
- Fortinet Enterprise Partner Sales GuideDocumento64 páginasFortinet Enterprise Partner Sales GuideFelipe Gabriel Nieto ConchaAinda não há avaliações
- Cyber o Am BrochureDocumento7 páginasCyber o Am BrochureRamzi Hicham ErreurAinda não há avaliações
- Sourcefire Next-Generation IPS (NGIPS) White PaperDocumento10 páginasSourcefire Next-Generation IPS (NGIPS) White PapergfbAinda não há avaliações
- ForeScout Company OverviewDocumento2 páginasForeScout Company Overviewshahidul0Ainda não há avaliações
- Complete Protection On Digital surface-PHD InterviewDocumento15 páginasComplete Protection On Digital surface-PHD InterviewAnju ElzabethAinda não há avaliações
- Integrated Security, Visibility, and Control For Next-Generation Network ProtectionDocumento5 páginasIntegrated Security, Visibility, and Control For Next-Generation Network ProtectionMdMehediHasanAinda não há avaliações
- 22855.magic Quadrant For Endpoint Protection PlatformsDocumento35 páginas22855.magic Quadrant For Endpoint Protection PlatformsJavier Javier MLAinda não há avaliações
- The Network Is Changing How Does Cybersecurity Keep PaceDocumento3 páginasThe Network Is Changing How Does Cybersecurity Keep PaceAshu BhallaAinda não há avaliações
- Utm PDFDocumento5 páginasUtm PDFiyan rahdianAinda não há avaliações
- Service Provider Guide enDocumento6 páginasService Provider Guide enZehra X AdilovicAinda não há avaliações
- Eb Seven Major Challenges Impeding Digital AccelerationDocumento3 páginasEb Seven Major Challenges Impeding Digital AccelerationGokhan GULENAinda não há avaliações
- Wurldtech Overview Brochure-2Documento12 páginasWurldtech Overview Brochure-2Tarek KhafagaAinda não há avaliações
- IJIRET Sapna HD Network Security Issues Measures and Tools For Intruder AttacksDocumento4 páginasIJIRET Sapna HD Network Security Issues Measures and Tools For Intruder AttacksInternational Journal of Innovatory Research (IJIR), (IJIRET) & (IJIRSM).Ainda não há avaliações
- Idp Series Intrusion Detection and Prevention Appliances: Product Category BrochureDocumento6 páginasIdp Series Intrusion Detection and Prevention Appliances: Product Category BrochureAri AnandaprajaAinda não há avaliações
- Atos Trustway - HSM - En2-WebDocumento8 páginasAtos Trustway - HSM - En2-Websantosa2dAinda não há avaliações
- Iotsm: An End-To-End Security Model For Iot Ecosystems: Submitted By: Anubha Kabra (2K16/Co/51)Documento3 páginasIotsm: An End-To-End Security Model For Iot Ecosystems: Submitted By: Anubha Kabra (2K16/Co/51)Anubha KabraAinda não há avaliações
- Simplified Security HND BKDocumento23 páginasSimplified Security HND BKlotos27Ainda não há avaliações
- Ebook Securing Digital AccelerationDocumento19 páginasEbook Securing Digital AccelerationGokhan GULENAinda não há avaliações
- Visionary Innovation Leadership: Frost & Sullivan Best Practices AwardDocumento10 páginasVisionary Innovation Leadership: Frost & Sullivan Best Practices AwardAparnaAinda não há avaliações
- Protection Service For: BusinessDocumento16 páginasProtection Service For: BusinessGuadalupe PasiónAinda não há avaliações
- Arm Trust Zone White PaperDocumento10 páginasArm Trust Zone White PaperDayabaran GangatharanAinda não há avaliações
- Eb Protecting Every EdgeDocumento12 páginasEb Protecting Every EdgeGokhan GULENAinda não há avaliações
- SIEM Nov 22 Gartner ReprintDocumento14 páginasSIEM Nov 22 Gartner ReprintWolf RichardAinda não há avaliações
- Junos Pulse: Mobility Redefined: Juniper's Integrated, Multiservice Client For Security, Access and AccelerationDocumento4 páginasJunos Pulse: Mobility Redefined: Juniper's Integrated, Multiservice Client For Security, Access and AccelerationAditya MehtaAinda não há avaliações
- Competitive Analysis - Fortinet Vs Trend Micro Network VirusWallDocumento8 páginasCompetitive Analysis - Fortinet Vs Trend Micro Network VirusWallo0000oAinda não há avaliações
- Managed Security Services On The Cloud by IBMDocumento18 páginasManaged Security Services On The Cloud by IBMOthon CabreraAinda não há avaliações
- SB Fortisase Cloud Delivered Securtiy To Every UserDocumento5 páginasSB Fortisase Cloud Delivered Securtiy To Every UserpatrickkenAinda não há avaliações
- Zero Trust Solution Brief PDFDocumento11 páginasZero Trust Solution Brief PDFSofiene CHOUCHENEAinda não há avaliações
- Types of FirewallDocumento8 páginasTypes of Firewallyasser waelAinda não há avaliações
- HuaweiiDocumento5 páginasHuaweiiAdrian LugueAinda não há avaliações
- Item 1. BusinessDocumento15 páginasItem 1. BusinessYuk Ngo FongAinda não há avaliações
- Genesys 2 Brochure WebDocumento9 páginasGenesys 2 Brochure WebunstrainAinda não há avaliações
- INSECURE Magazine Issue 19Documento103 páginasINSECURE Magazine Issue 19Marco Antonio Martinez AndradeAinda não há avaliações
- Eudemon200E X1Documento2 páginasEudemon200E X1Sabin DragneaAinda não há avaliações
- Palo Alto Networks ML-Powered Next-Generation Firewall Feature OverviewDocumento6 páginasPalo Alto Networks ML-Powered Next-Generation Firewall Feature OverviewМөнхбаяр НямааAinda não há avaliações
- Byod Brochure 4AA4-0638ENWDocumento8 páginasByod Brochure 4AA4-0638ENWselvakumaran.lAinda não há avaliações
- PovidoneDocumento2 páginasPovidoneElizabeth WalshAinda não há avaliações
- Czech Republic GAAPDocumento25 páginasCzech Republic GAAPFin Cassie Lazy100% (1)
- EC2 406006 001 EFE 0121 - Controgen Generator Excitation System Description - Rev - ADocumento29 páginasEC2 406006 001 EFE 0121 - Controgen Generator Excitation System Description - Rev - AAnonymous bSpP1m8j0n50% (2)
- Chapter 2 A Guide To Using UnixDocumento53 páginasChapter 2 A Guide To Using UnixAntwon KellyAinda não há avaliações
- Hierarchy of The Inchoate Crimes: Conspiracy Substantive CrimeDocumento18 páginasHierarchy of The Inchoate Crimes: Conspiracy Substantive CrimeEmely AlmonteAinda não há avaliações
- MOFPED STRATEGIC PLAN 2016 - 2021 PrintedDocumento102 páginasMOFPED STRATEGIC PLAN 2016 - 2021 PrintedRujumba DukeAinda não há avaliações
- Business Testimony 3Documento14 páginasBusiness Testimony 3Sapan BanerjeeAinda não há avaliações
- Durga Padma Sai SatishDocumento1 páginaDurga Padma Sai SatishBhaskar Siva KumarAinda não há avaliações
- Pilot'S Operating Handbook: Robinson Helicopter CoDocumento200 páginasPilot'S Operating Handbook: Robinson Helicopter CoJoseph BensonAinda não há avaliações
- Leeka Kheifets PrincipleDocumento6 páginasLeeka Kheifets PrincipleAlexandreau del FierroAinda não há avaliações
- Audit Certificate: (On Chartered Accountant Firm's Letter Head)Documento3 páginasAudit Certificate: (On Chartered Accountant Firm's Letter Head)manjeet mishraAinda não há avaliações
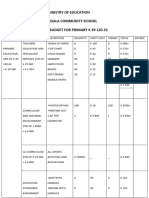
- Ministry of Education Musala SCHDocumento5 páginasMinistry of Education Musala SCHlaonimosesAinda não há avaliações
- Danh Sach Khach Hang VIP Diamond PlazaDocumento9 páginasDanh Sach Khach Hang VIP Diamond PlazaHiệu chuẩn Hiệu chuẩnAinda não há avaliações
- Codex Standard EnglishDocumento4 páginasCodex Standard EnglishTriyaniAinda não há avaliações
- CY8 C95 X 0 ADocumento32 páginasCY8 C95 X 0 AAnonymous 60esBJZIj100% (1)
- Journal of Economic LiteratureDocumento28 páginasJournal of Economic LiteratureEkoKurniadiAinda não há avaliações
- Your Electronic Ticket ReceiptDocumento2 páginasYour Electronic Ticket Receiptjoana12Ainda não há avaliações
- Terms and Conditions 27 06 PDFDocumento4 páginasTerms and Conditions 27 06 PDFShreyash NaikwadiAinda não há avaliações
- Switch CondenserDocumento14 páginasSwitch CondenserKader GüngörAinda não há avaliações
- Guidelines Use of The Word AnzacDocumento28 páginasGuidelines Use of The Word AnzacMichael SmithAinda não há avaliações
- Numerical Transformer Differential RelayDocumento2 páginasNumerical Transformer Differential RelayTariq Mohammed OmarAinda não há avaliações
- SQL Datetime Conversion - String Date Convert Formats - SQLUSA PDFDocumento13 páginasSQL Datetime Conversion - String Date Convert Formats - SQLUSA PDFRaul E CardozoAinda não há avaliações
- Installation and User's Guide For AIX Operating SystemDocumento127 páginasInstallation and User's Guide For AIX Operating SystemPeter KidiavaiAinda não há avaliações
- Research Proposal IntroductionDocumento8 páginasResearch Proposal IntroductionIsaac OmwengaAinda não há avaliações
- Econ 1006 Summary Notes 1Documento24 páginasEcon 1006 Summary Notes 1KulehAinda não há avaliações
- Elliot WaveDocumento11 páginasElliot WavevikramAinda não há avaliações
- PW Unit 8 PDFDocumento4 páginasPW Unit 8 PDFDragana Antic50% (2)
- Kicks: This Brochure Reflects The Product Information For The 2020 Kicks. 2021 Kicks Brochure Coming SoonDocumento8 páginasKicks: This Brochure Reflects The Product Information For The 2020 Kicks. 2021 Kicks Brochure Coming SoonYudyChenAinda não há avaliações
- Soneri Bank Compensation PolicyDocumento20 páginasSoneri Bank Compensation PolicySapii MandhanAinda não há avaliações
- Fascinate: How to Make Your Brand Impossible to ResistNo EverandFascinate: How to Make Your Brand Impossible to ResistNota: 5 de 5 estrelas5/5 (1)
- Summary: $100M Leads: How to Get Strangers to Want to Buy Your Stuff by Alex Hormozi: Key Takeaways, Summary & Analysis IncludedNo EverandSummary: $100M Leads: How to Get Strangers to Want to Buy Your Stuff by Alex Hormozi: Key Takeaways, Summary & Analysis IncludedNota: 3 de 5 estrelas3/5 (6)
- $100M Offers: How to Make Offers So Good People Feel Stupid Saying NoNo Everand$100M Offers: How to Make Offers So Good People Feel Stupid Saying NoNota: 5 de 5 estrelas5/5 (25)
- Summary: Dotcom Secrets: The Underground Playbook for Growing Your Company Online with Sales Funnels by Russell Brunson: Key Takeaways, Summary & Analysis IncludedNo EverandSummary: Dotcom Secrets: The Underground Playbook for Growing Your Company Online with Sales Funnels by Russell Brunson: Key Takeaways, Summary & Analysis IncludedNota: 5 de 5 estrelas5/5 (2)
- $100M Leads: How to Get Strangers to Want to Buy Your StuffNo Everand$100M Leads: How to Get Strangers to Want to Buy Your StuffNota: 5 de 5 estrelas5/5 (19)
- Dealers of Lightning: Xerox PARC and the Dawn of the Computer AgeNo EverandDealers of Lightning: Xerox PARC and the Dawn of the Computer AgeNota: 4 de 5 estrelas4/5 (88)
- Visibility Marketing: The No-Holds-Barred Truth About What It Takes to Grab Attention, Build Your Brand, and Win New BusinessNo EverandVisibility Marketing: The No-Holds-Barred Truth About What It Takes to Grab Attention, Build Your Brand, and Win New BusinessNota: 4.5 de 5 estrelas4.5/5 (7)
- Scientific Advertising: "Master of Effective Advertising"No EverandScientific Advertising: "Master of Effective Advertising"Nota: 4.5 de 5 estrelas4.5/5 (164)
- Obviously Awesome: How to Nail Product Positioning so Customers Get It, Buy It, Love ItNo EverandObviously Awesome: How to Nail Product Positioning so Customers Get It, Buy It, Love ItNota: 4.5 de 5 estrelas4.5/5 (152)
- Yes!: 50 Scientifically Proven Ways to Be PersuasiveNo EverandYes!: 50 Scientifically Proven Ways to Be PersuasiveNota: 4 de 5 estrelas4/5 (154)
- Storytelling: A Guide on How to Tell a Story with Storytelling Techniques and Storytelling SecretsNo EverandStorytelling: A Guide on How to Tell a Story with Storytelling Techniques and Storytelling SecretsNota: 4.5 de 5 estrelas4.5/5 (72)
- Summary: The Intelligent Investor: The Definitive Book on Value Investing by Benjamin Graham: Key Takeaways, Summary & AnalysisNo EverandSummary: The Intelligent Investor: The Definitive Book on Value Investing by Benjamin Graham: Key Takeaways, Summary & AnalysisNota: 4 de 5 estrelas4/5 (4)
- Invisible Influence: The Hidden Forces that Shape BehaviorNo EverandInvisible Influence: The Hidden Forces that Shape BehaviorNota: 4.5 de 5 estrelas4.5/5 (131)
- Understanding Digital Marketing: Marketing Strategies for Engaging the Digital GenerationNo EverandUnderstanding Digital Marketing: Marketing Strategies for Engaging the Digital GenerationNota: 4 de 5 estrelas4/5 (22)
- How to Read People: The Complete Psychology Guide to Analyzing People, Reading Body Language, and Persuading, Manipulating and Understanding How to Influence Human BehaviorNo EverandHow to Read People: The Complete Psychology Guide to Analyzing People, Reading Body Language, and Persuading, Manipulating and Understanding How to Influence Human BehaviorNota: 4.5 de 5 estrelas4.5/5 (33)
- Jab, Jab, Jab, Right Hook: How to Tell Your Story in a Noisy Social WorldNo EverandJab, Jab, Jab, Right Hook: How to Tell Your Story in a Noisy Social WorldNota: 4.5 de 5 estrelas4.5/5 (18)
- Summary: Traction: Get a Grip on Your Business: by Gino Wickman: Key Takeaways, Summary, and AnalysisNo EverandSummary: Traction: Get a Grip on Your Business: by Gino Wickman: Key Takeaways, Summary, and AnalysisNota: 5 de 5 estrelas5/5 (10)
- Pre-Suasion: Channeling Attention for ChangeNo EverandPre-Suasion: Channeling Attention for ChangeNota: 4.5 de 5 estrelas4.5/5 (278)
- Brand Identity Breakthrough: How to Craft Your Company's Unique Story to Make Your Products IrresistibleNo EverandBrand Identity Breakthrough: How to Craft Your Company's Unique Story to Make Your Products IrresistibleNota: 4.5 de 5 estrelas4.5/5 (48)
- Summary: Range: Why Generalists Triumph in a Specialized World by David Epstein: Key Takeaways, Summary & Analysis IncludedNo EverandSummary: Range: Why Generalists Triumph in a Specialized World by David Epstein: Key Takeaways, Summary & Analysis IncludedNota: 4.5 de 5 estrelas4.5/5 (6)
- 46 Consumer Reporting Agencies Investigating YouNo Everand46 Consumer Reporting Agencies Investigating YouNota: 4.5 de 5 estrelas4.5/5 (6)
- Made You Look: How to Use Brain Science to Attract Attention and Persuade OthersNo EverandMade You Look: How to Use Brain Science to Attract Attention and Persuade OthersAinda não há avaliações
- The Myth of the Rational Market: A History of Risk, Reward, and Delusion on Wall StreetNo EverandThe Myth of the Rational Market: A History of Risk, Reward, and Delusion on Wall StreetAinda não há avaliações
- 100M Offers Made Easy: Create Your Own Irresistible Offers by Turning ChatGPT into Alex HormoziNo Everand100M Offers Made Easy: Create Your Own Irresistible Offers by Turning ChatGPT into Alex HormoziAinda não há avaliações
- Ca$hvertising: How to Use More than 100 Secrets of Ad-Agency Psychology to Make Big Money Selling Anything to AnyoneNo EverandCa$hvertising: How to Use More than 100 Secrets of Ad-Agency Psychology to Make Big Money Selling Anything to AnyoneNota: 5 de 5 estrelas5/5 (114)
- Summary: Influence: The Psychology of Persuasion by Robert B. Cialdini Ph.D.: Key Takeaways, Summary & AnalysisNo EverandSummary: Influence: The Psychology of Persuasion by Robert B. Cialdini Ph.D.: Key Takeaways, Summary & AnalysisNota: 5 de 5 estrelas5/5 (4)