Escolar Documentos
Profissional Documentos
Cultura Documentos
CCN 2012
Enviado por
szakaDescrição original:
Título original
Direitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
CCN 2012
Enviado por
szakaDireitos autorais:
Formatos disponíveis
CONTENTS
Lab Session No. 1. Object Installing network card in Windows environment, and performing following configurations:TCP/IP, IP and default gateway Making the following kinds of UTP cables:Straight through and cross Practicing some basic commands to interact with the Cisco IOS (Internetwork Operating System) CLI Software Copying IOS image and configuration to and from CISCO router. Configuring static routes on Cisco routers. Configuring RIP(Routing Information Protocol). Configuring RIP Version 2 Configuring OSPF (Open Shortest Path First) Single Area Configuring IGRP (Interior Gateway Routing Protocol). ConfiguringEIGRP Protocol) (Enhanced Interior Gateway Routing Page No. 1
2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15.
10 17 23 28 31 34 36 41 45 50 54 57 60 66
Recovering lost router password. Studying and configuring Access Lists Studyingbasic LAN switch operation. Learning Loop Avoidance with Spanning Tree. Configuring Virtual LANs
Computer Communication Networks Lab Session 1
NED University of Engineering & Technology - Department of Computer & Information Systems Engineering
Lab Session 01
OBJECT
Installing network card in Windows environment, and performing following configurations: TCP/IP IP configuration Default Gateway
EQUIPMENT AND APPARATUS
Network Interface Cards Ethernet hub or switch UTP cables
THEORY
Networking in Windows NT and later versions allows computers running the Windows operating system to participate in a domain or peer-to-peer network and share resources with other computers, running Windows NT, 9x, 2000, XP or some other operating system. It also allows you to connect to the Internet using dial-up connection or LAN. Windows network can use a variety of protocols. NetBEUI is a protocol most suitable for smaller networks, as a rule of thumb, not exceeding 10 hosts. TCP/IP is a protocol suite well suited for larger networks, but it can also be used on smaller networks. It is the protocol that the Internet uses. As you know TCP/IP is a collection of many different protocols, with IP being the protocol that runs on the network layer. Among other things, IP defines addressing requirements for the hosts. An IP (Internet Protocol) address uniquely identifies a node or host connection to an IP network. System administrators or network designers assign IP addresses to nodes. IP addresses are configured by software and are not hardware specific. An IP address is a 32 bit binary number usually represented as four fields each representing 8 bit numbers in the range 0 to 255 (sometimes called octets) separated by decimal points. For example: 150.215.17.9 It is sometimes useful to view the values in their binary form. 150.215.17.9 10010110.11010111.00010001.00001001 An IP address consists of two parts, one identifying the network and one identifying the node. The class of the address determines which part belongs to the network address which part belongs to the node address.
ter Commun nication Net tworks Lab Session 1 b
versity of Engin neering & Tech hnology - Depa artment of Com mputer & Infor rmation System Engineering ms g
CEDURE
Windows X CD into the CD RO and fol XP OM llow the ste to insta the prod eps all duct onto stem. tion procedu you wi be asked to configur the netwo settings. Choose ure, ill re ork . the installat m settings:
Figure 1 1.1:Configur ring Custom Networking Settings g
working Com mponents d dialog box will appear Make sur that all t compon r. re the nents are d, as shown: :
Figur 1.2:Selecti the netwo re ing orking comp ponents
ter Commun nication Net tworks Lab Session 1 b
versity of Engin neering & Tech hnology - Depa artment of Com mputer & Infor rmation System Engineering ms g
dialogue will appear allowing con w nfiguration o TCP/IP p of properties.
Figure 1.3: G F General TCP propertie P/IP es
ure the IP ad ddress, subn mask, de net efault gatew and DN server se way NS ettings for yo our as shown:
Fig gure 1.4:Spe ecifying IP ad ddress, subne mask and default gatew et way
ter Commun nication Net tworks Lab Session 1 b
versity of Engin neering & Tech hnology - Depa artment of Com mputer & Infor rmation System Engineering ms g
OK and selec if you wa to make the comput a part of Computer Domain or ct ant ter f D roup, as sho own:
Figure 1 Specifyi path to ne 1.5: ing etwork adapt driver ter
e done with the TCP/IP configurat P tions. Wait f the insta for allation proc to com cess mplete. figure TCP/ settings on SUSE 11.4 Linux, y must fir logon as administra /IP you rst s ator. YAST from the applica ations menu Again you will be ask for a pa u. u ked assword. he root passw word:
Figure 1.6: Enter root password t
ter Commun nication Net tworks Lab Session 1 b
versity of Engin neering & Tech hnology - Depa artment of Com mputer & Infor rmation System Engineering ms g
pen YaST C Control Cen and clic on Netwo Devices nter ck ork s:
Figure 1.7 Click netw 7: work devices in YaST con ntrol center
Network Set ttings from the Networ Devices w rk window:
Figure 1.8: Click netw work settings
ter Commun nication Net tworks Lab Session 1 b
versity of Engin neering & Tech hnology - Depa artment of Com mputer & Infor rmation System Engineering ms g
r the networ configurations to ini rk itialize:
Figure 1.9: Initia alizing netwo configura ork ations
xt dialogue w give yo an overview of netw will ou work settings.
Fig gure 1.10: Overview of n O network setti ings
ter Commun nication Net tworks Lab Session 1 b
versity of Engin neering & Tech hnology - Depa artment of Com mputer & Infor rmation System Engineering ms g
network car setup and select sta rd d atically assi IP addr ign ress. Enter the IP add dress, the mask of you subnet an a hostnam as shown and click Next: ur nd me n
Figure 1.11: Assigning I address, su F : IP ubnet mask a hostnam and me
Hostname/D DNS tab to s the requi set ired hostnam domain and DNS s me, n servers IP a address.
Figure 1.12: Network Settings k
ter Commun nication Net tworks Lab Session 1 b
versity of Engin neering & Tech hnology - Depa artment of Com mputer & Infor rmation System Engineering ms g
n the routing tab and sp pecify the d default gatew for you network a shown: way ur as
Figure 1.13: Sp pecifying the default gate e eway
OK. You are now done w TCP/IP configura with P ations on SU Linux. USE
RCISES
the paramete that mus be config ers st gured when configuring TCP/IP on a host. g n __________ __________ __________ __________ __________ __________ __________ _______ __________ __________ __________ __________ __________ __________ __________ _______ __________ __________ __________ __________ __________ __________ __________ _______ __________ __________ __________ __________ __________ __________ __________ _______ __________ __________ __________ __________ __________ __________ __________ _______ __________ __________ __________ __________ __________ __________ __________ _______
would you find out th IP addres of a mach u he ss hine from c command lin in Wind ne dows and x? __________ __________ _________ __________ __________ __________ __________ _______ __________ __________ _________ __________ __________ __________ __________ _______ __________ __________ _________ __________ __________ __________ __________ _______
Computer Communication Networks Lab Session 1
NED University of Engineering & Technology - Department of Computer & Information Systems Engineering
________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ 3. Using the same command as in exercise 2, give a detailed view of network settings. Also give commands to release and renew the leases if the IP address is obtained from a DHCP server. _________________________________________________________________________ _________________________________________________________________________ _________________________________________________________________________ _________________________________________________________________________ _________________________________________________________________________ _________________________________________________________________________ _________________________________________________________________________ _________________________________________________________________________
Comput Commun ter nication Net tworks
Lab S Session 2
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
Lab Sessio 02 b on
OBJECT
Mak king the fol llowing kind of UTP c ds cables: 1. 2. Stra aight throug cable gh Cro cable oss
THEO ORY
There are several cla assifications of twisted pair cable. Lets skip right over s d . d for them and state that well use Category 5 (or CAT 5) cable fo all new installatio ons. Likewise, there are several fire code classificatio for the c ons outer insu ulation of CA 5 cable. Well use CMR cable or riser cable, for AT e, most of th wiring w do. You should als be awar of CMP or plenum he we u so re cable (a p plenum is us to distri sed ibute air in a building) you may b required ) be by local o national codes to use the more e or c e expensive plenum-jack p keted cable if it runs t through sus spended cei ilings, ducts or other a s, areas, if the are used ey to circula air or ac as an air passage f ate ct r from one ro oom to ano other. If in doubt, use plenum. C e CMR cable is generall acceptable for all ap ly pplications not requir ring plenum cable. m able is available in ree el-in-box pa ackaging. T This is very handy for CAT 5 ca pulling the wire with hout putting twists in it. Without th kind of p his package or ulling wire i a two-per is rson job. Be efore the adv of the vent a cable reel stand, pu ox, el on pull reel-in-bo we used to put a ree of wire o a broom handle to p it. One person wo ould hold th broom ha he andle and th other wou pull bro he uld oom handle to pull it. You will pr roduce a tan ngled mess, if your pull the wire o the end , off of the reel al lone.
Figure 2 2.1: UTP cab ble
re bles en egments run nning form Standard wir patch cab are ofte specified for cable se a wall ja to a PC and for pa C atch panels. They are m more flexibl than solid core wire. However, le d . ack the ratio onale for using it is that t constant flexing of patch cabl may wear-out solid core cable and break it. This is the t f les d e k not a rea concern i the avera small ne al in age etwork. f g mply connect computer directly t other com ts rs to mputers or h hubs. Solid Most of the wiring we do sim core cab is quite suitable for this purpos and for m ble r se many home and small business net b twork. It is also qui acceptab for use a patch cab ite ble as bles. You m might consid a stranded wire pat cable if der tch you hav a noteboo computer you are co ve ok r onstantly mo oving aroun nd. our re al ndividually insulated w wires. Each CAT 5 cable has fo twisted pairs of wir for a tota of eight in color coded with one wire havin solid col (blue, orange, gree or brow twisted d ng lor o en, wn) pair is c around a second wire with a white backg w ground and a stripe of the same c d f color. The solid color ave white stripe in s some cable Cable c es. colors are commonly described using the may ha backgro ound color f followed by the color of the strip e.g; whi y pe; ite-orange is a wire wi a white ith backgro ound and an orange stri n ipe.
10
Comput Commun ter nication Net tworks
Lab S Session 2
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
ctors Connec
aight throug and cro gh oss-over pat cables are discuss in this tch sed The stra article w which are t terminated with CAT 5 RJ-45 modular plu m ugs. RJ-45 plugs ar similar to those you see on the end of your teleph re o ull hone cable except th have ei hey ight as oppo osed to four or six cont r tacts on the end of the plug and they are about twice as big. Mak sure they are rated for CAT 5 d a ke y wiring. (RJ stands for Regis stered Jack). Also, th here are RJ J-45 plugs Figure 2 RJ-45 2.2: d solid core w and str wire randed wire Others are designed e. e designed for both s Connecto or specifica ally for one kind of w e wire or the other. Be sure you buy plugs e e appropr riate for the wire you a going to use. We no are ormally use plugs desig e gned to acc commodate both kin of wire. nds rk t Networ cabling tools dular Plug Crimp Too ol 1. Mod ill modular crimp tool. This is very T y You wi need a m similar to the ones which hav been use for many s ve ed y or s w it Figure 2.3:Modular plug crimp tool years fo all kinds of telephone cable work and i r works ju fine for Ethernet ca ust ables. You d dont need a lot of b bells and whistles, ju a tool which wil ust ll securely crimp RJ-45 connecto Some crimpers hav cutters w y ors. c ve which can be used to cu the cable e ut and indi ividual wire and poss es, sibly stripping the outer jacket. r
2. Uni iversal UTP Stripping Tool (Ecli P g ipse)
It make a much n es neater cut. It is highly r t recommend ding for anyo who will make a lo of cables. one ot .
gonal Cutters 3. Diag
Figure 2. Eclipse .4:
sier diagonal cu utters (diag or dike gs es) It is eas to use d to cut th cable off at the reel and to finehe f -tune the ca able ends du uring assem mbly. Also if you dont have a o, e stripper you can strip the cab by using a small kn Figure 2.5 Diagonal Cutters r, ble g nife to carefu slice th outer jack longitud fully he ket dinally and use the diag to cut it o around th circumfe gs off he erence.
Figure 2.5: Diagon cutters nal
asics UTP ba 0BASE-T and 100BASE-TX E Ethernet consist of two transm mission lin nes. Each The 10 transmis ssion line is a pair of twisted wi i f ires. One pair receives data signa and the other pair s als transmit data sign ts nals. A bala anced line d driver or tra ansmitter is at one end of one of these lines d and a lin receiver is at the ot ne ther end. A (much) sim mplified schematic for o of these lines and one e its trans smitter and r receiver fol llows:
11
Comput Commun ter nication Net tworks
Lab S Session 2
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
Figure 2.6: Schem matic diagram of transmis m ssion line
wn nsmission line at about the spee of light (186,000 ed t Pulses of energy travel dow the tran econd). The principal c e components of these p s pulses of en nergy are th potential difference he miles/se between the wires and the cur n rrent flowin near the s ng surface of t wires.Th energy c also be the his can considered as resid ding in the magnetic field which surrounds the wires and the ele h ectric field between the wires. In other w n words, an e electromagn netic wave which is g guided by, a travels and down th wires. he ain nsient magn netic fields which surro ound the w wires and the magnetic e The ma concern are the tran fields g generated ex xternally by the other transmissio lines in the cable, o y on other netwo cables, ork electric motors, flu uorescent li ights, teleph hone and electric lines lightning which ma literally s, g, ay bury the Ethernet p e pulses, the c conveyor of the informa f ation being sent down the line. isted-pair Et thernet emp ploys two principal me eans for com mbating nois The first is the use se. t The twi of balan nced transm mitters and receivers. A signal p pulse actually consists of two sim multaneous pulses r relative to g ground: a n negative pul on one line and a positive pu on the other. The lse ulse receiver detects th total diff r he ference betw ween these two pules. Since a p . pulse of noi usually ise produce pulses of the same p es f polarity on both lines, it is essenti b ially cancele out at th receiver. ed he Also, th magnetic field surro he c ounding one wire from a signal pu is a mirror of the one on the e m ulse other wire. At a ver short dist ry tance from the two wir the magn res netic fields are opposit and have te ncy cel This reduce the lines impact on the other es s n a tenden to canc the effect of each other out. T pairs of wires and t rest of th world. f the he cond and th primary means of r he reducing cro oss-talk (the term cros ss-talk came from the e The sec ability t overhear conversatio on other lines on yo phone) between th pairs in th cable, is to ons r our he he the dou uble helix configuratio produced by twisti the wir togethe This con c on ing res er. nfiguration produce symmetri (dentinal) noise sig es ical gnals in eac wire. Ide ch eally, their difference a detected d as at the re eceiver, is zero. In actu uality it is m much reduced d. ht and over cable Straigh through a cross o the background may have white strip and may be denote that way ds e pes y ed Again, t wire with colored b in diagr rams found elsewhere. For examp the gre wire ma be label Green-W d . ple, een ay led White. The backgro ound color is always sp pecified first t.
12
Comput Commun ter nication Net tworks
Lab S Session 2
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
Fi igure 2.7: St traight throu and cross ugh sover cable w scheme wire
ght-through cable has i h identical end whereas a Crossove cable has different en ds, s er s nds. A Straig IA nd andards EIA/TI 568A an 568B sta
Figure 2.8: C F Cable conne ector standard ordering d
es onal differe ence which standard yo use ou It make no functio for a st traight-throu cable. Your can start a cros ugh ssover cable w either s with standard as long as the other end is the e other st tandard. It makes no f functional difference w d which end is w which. Desp what yo may have read elsew pite ou e where, a 568A patch cable will wor in a netw A rk work with 568B wiring and 568B patch cab will w ble work in a 568A k. rons couldn care less. nt network The electr
PROC CEDURE
To Mak Cable ke
Figure 2.9: EIA/TIA 568A and 5 2 A 568B
1. Pull the cable off the reel to the des l l sired length and cut th total len h he ngth of wire segments e betw ween a PC and a hub o between two PCs cannot excee 100 Met (328 fee or about a or t ed ters et the l length of a football fiel for 100B ld) BASE-TX a 300 Met for 100 and ters 0BASE-T. p of ripper or a k knife and di iags. If you are using th stripper, he 2. Strip one end o the cable with the str plac the cable in the groo on the blade (left) side of the stripper an align the end of the ce ove b nd cabl with the right side o the stripp This wi strip abou of the jacket off the cable. le of per. ill ut f
13
Comput Commun ter nication Net tworks
Lab S Session 2
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
Turn the stripp about 1 turn and pull. If yo turn it more, you w probabl nick the n per d ou m will ly wire If you are using kn and dia carefull slit the cable for about an inch or so and es. a nife ags, ly h neat trim arou the circ tly und cumference of the cable with diags to remove the jacket. e s pect res s. he i a may 3. Insp the wir for nicks Cut off th end and start over if you see any. You m have to adju the blade with the s ust e screw at the front strip e pper. Cable diameters and jacket t a thicknesses vary y. ead ange the pai roughly in the order of the desi irs r ired cable en nd. 4. Spre and arra wist irs nge res rder of the d desired cabl end. Flatt the end le ten 5. Untw the pai and arran the wir in the or betw ween your t thumb and forefinger. Trim the e ends of the wires so th are even with one hey n anot ther. It is very impor rtant that th unstrippe (untwiste end be s he ed ed) slightly less than s han will -of-spec an susceptib to nd ble long. If it is longer th it w be outsstalk. If it is less than it will not be pro n operly clinch when RJ-45 hed R cros plug is crimped on. Flatten again. The should b little or no space bet g d n ere be n tween the w wires. 6. Hold the RJ-45 plug with the clip fac d 5 cing down o away fro you. Pus the or om sh wire firmly int the plug. Now, insp e to pect before crimping and wastin the e ng plug g!Looking t through the bottom of the plug, t wire on the far-left side e f the ft will have a wh backgro hite ound. The w wires should alternativ light and dark d ve d m ht. thest right wire is brow The wire should al end w wn. es ll from left to righ The furt even at the fr nly ront of the p plug. The ja acket shoul end just about where you ld a e see it in the dia agram-right on the line.
Figur 2.10: re Pr reparing the RJ-45 Connector e
BOUT CR RIMPING ALL AB
d near -45 th down and fi irmly 7. Hold the wire n the RJ- plug wit the clip d push it into the left side o the front of the Crim h e of mper (it wil only go i one way) Hold the ll in ). wire in place an squeeze the crimper handles qu firmly. This is wha will happe e nd r uite T at en:
Figur 2.11:Crim re mping
imp it once) The crimp pushes t plunger down on the RJ-45 p ). per two rs plug. One fo orces, what (Cri amo ounts to, a cleverly de esigned plas plug/we stic edge onto the cable ja t acket and v very firmly clinc ches it. The other seats the pins each with two teeth at its end, through the insulation e s , h t e and into the con nductors of their respec f ctive wires.
14
Comput Commun ter nication Net tworks
Lab S Session 2
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
8. Test the crimp, if done pr t , roperly an average pers will no be able to pull the plug off the a son ot o cabl with his or her bare hands. An that quite simply, be le e nd e esides lowe cost, is th primary er he adva antage of tw wisted-pair cables over the older t r thin wire, co oaxial cable In fact, t ease of es. the insta allation and the modular RJ-45 plug is the m reason c d main coaxial cable is no lon nger widely used for small Ethernet. B dont pu that hard on the plu It could stretch the cable and d But, ull d ug. d e chan its char nge racteristics. Look at th side of th plug and see if it lo he he d ooks like th diagram he and give it a fai firm tug to make su it is crim irly g ure mped well. pare her he it esired end a crimp. and 9. Prep the oth end of th cable so i has the de oth are each, hold th next to each other and with R hem o r RJ-45 clips 10. If bo ends of the cable a within re facin away. Lo through the bottom of the plu If the pl ng ook h m ugs. lugs are wir correctly and they red y, are i identical, it is a straigh t ht-through c cable. If the are wired correctly a they are different, ey d and e it is a crossover cable. r
PREC CAUTION NS
1. Try to avoid running cable parallel to power cab es o bles. ou her ble ot 2. If yo bundle a group of cables togeth with cab ties (zip ties), do no over-clinch them. It is ok to snug them toge kay g ether firmly but dont tighten the so much that you d y; t em h deform the cabl les. ep way devices whi can intr ich roduce nois into them Heres a short list: se m. 3. Kee cables aw from d elec ctric heaters, loud sp peakers, pri inters, TV sets, fluo orescent lig ght, copiers welding s, mac chines, mic crowave ov vens, teleph hones, fans elevator motors, el s, lectric oven dryers, ns, washing machin and sho equipme nes, op ent. oid ng les ce ot 4 4. Avo stretchin UTP cabl (the forc should no exceed 24 LBS). n s ecure UTP cables. Use telephone w hanger which are available c wire rs, 5. Don not use a stapler to se at m hardwa stores. most are
EXER RCISES
e on is end c e 1. Give the reaso why it i not advisable to be UTP cables more than four times the diam meter of the cable. ____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________
y dvisable to r UTP ca outside of a buildin run able ng? 2. Why is it not ad ____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________
15
Comput Commun ter nication Net tworks
Lab S Session 2
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________
fine ommended m maximum c cable length for UTP an cite a rea h nd ason for it. 3. Defi the reco ____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________ ____ __________ __________ _________ __________ __________ __________ __________ _________
16
Comput Commun ter nication Net tworks
Lab Sessio 3 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Lab Session 03 b
OBJECT
Practi icing some basic comm b mands to int teract with the Cisco I IOS (Internetwork Ope erating System CLI Sof m) ftware
THEO ORY
me g. duce you to Cisco route and ers Welcom to hands on routing The goal of this lab is to introd other eq quipment th you will be using thr hat roughout th semester. In order to do well in the he . o n labs, we need to un e nderstand th basic set- of the la he -up ab. The lab has one rack, whic is connec to a PC You will be using the PC as a terminal e ch cted C. to ta to the ro alk outers. The routers are labeled alp phanumerica (Examp R1, R2, etc). ally ple Each rack has t patch pa h two anels. One of them has RJ-45 conn o s nectors and the other h serial d has conn nectors. Et thernet port are pre-connected to the RJ-45 patch pane Serial p ts o 5 el. ports are pre-connected to the serial patch pane The port are labele on their left. t l el. ts ed To c connect the PC to a sp e pecific route connect the PCs co er, onsole cable to the app e propriate cons port on the patch p sole n panel in the rack. You w find the console ca as a UT cable will e able TP with one of its ends connec through small dev h cted vices to a serial port on the PC.
Cisco ro outers suppo different modes of operation. When you a ort t o access a rou uter, it will typically be in the u mode. User mode gives a use access to simple sho command y user e er o ow ds. From us mode th next step is Privilege Mode. In the privileg mode a user can ha full ser he ed n ged ave access t all the dat to tabases mai intained by the router. Cisco route use man other mod but ers ny des, let us ke it simpl for now. eep le
Config guration mod de
Privileged m mode
User mode
17
Comput Commun ter nication Net tworks
Lab Sessio 3 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
PROC CEDURE
me un: It is tim to have fu nnect the PC to R1. C 1. Con 2. Pres enter a few time and you s ss es should get a prompt tha looks like router> at e: > u n mode. 3. You are now in the user m 4. Typ ?. Que pe estion mark lists comm mands that ca be used in a certain context. an i ype First ty help Try T typing these comm t mands: p? p pi? p omplete com mmands for you with th help of t TAB key r he the y. 5. The IOS will co Type sh<T T TAB> Finish the c F command w a ? to see what c with o commands y can use with show. you . (show?) u e complete command for the IOS to execute it. You only n Y need to 6. You dont have to type a c type enough of a command to differen e f d ntiate it from all other c m commands. o n de d ompt ending in >), now we g w 7. We have been operating in User Mod (identified by the pro nt ged wan to go into the Privileg Mode: Type enable or e T en The T prompt should end with a # (R t d Router#) Type ? to see all the commands possible fr T o e s rom this mo ode 8. One of the mos useful com e st mmands in the Cisco IOS is sho ow. Try th hese variatio ons: show show show show show show show show co onfigurat tion sh hows saved router confi figuration ve ersion - s shows IOS statistics st tartup-co onfigura ation sh hows the co onfiguration during star n rtup ru unning co onfigura ation sh hows the dy ynamic conf figuration fl lash giv details of flash mem ves o mory where IOS is stor e red pr rotocols shows p protocol and interface statistics d in nterface gives de etailed statis stics on each interface h in nterface s0 - Try this comma with som other in and me nterfaces as well.
w e uration mod Type the following commands: de. e : 9. Now lets move to configu
18
Comput Commun ter nication Net tworks
Lab Sessio 3 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
configur termin c re nal This will take you to confi s y iguration mo ode. The pr rompt endsw with routerco r onfig)#? ; to see the available command ds xt hange the na of rout to R1 ame ter 10. Nex we will ch into configu uration mod (if you ha followe the step 6 then you a already i the de ave ed are in Go i conf mode) a type the following c fig and commands: h hostname R1 e ctrl+Z c wr w m ;thi command will chang name. is d ge ;thi is to come out of priv is vilegemode e ;wri to the me ite emory.
ow an IP 11. No we want to set up a interface for a TCP/I network. T Type these commands: : c config t A After this you will be in config mo same as you did in step 6. ode s n i interfac Ethern ce net 0 T puts yo in interfa mode. N you ca configure interface Ethernet0. This ou ace Now an e E i addre ip ess 130.1 10.20.5 255.255. .255.0 T gives the interface an IP addr and sub mask. This t e ress bnet n shutd no down B default a interface are admini By all e istratively d down. This c command will bring th up. w hem c ctrl+Z T is to co out of p This ome privilege mode. Now ty the foll m ype lowing com mmand: s inter sh rface e0 O Observe and record car d refully wha you see. at N connect a cable fr Now rom router R Ethern e0 inte R1`s net erface to a h or switch. hub A Again type this comma and: s inter sh rface e0 A Again obser and reco carefull what you see. rve ord ly u N Note: Cisco commands are not cas o s se-sensitive e.
19
Comput Commun ter nication Net tworks
Lab Sessio 3 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
EXER RCISES
1. D Determine w which mode you opera in when you first ac e ate ccess the rou uter. __________ _ __________ _________ __________ __________ __________ __________ _______ Local acce to the router is done via ________ ess ____ ports. (serial, E . Ethernet, 2. L asynchrono a ous) An et ___ 3. A Etherne cable has _________ pins. nfiguration is stored in RAM(true or false). 4. Start-up con 5. R Running-co onfiguration is stored in ________ n n _______.
6. T comma used to save chan The and o nges made in the run nning config guration to start-up configuratio is: c on __________ _ __________ _________ __________ __________ __________ __________ _______
The n co d __________ ____. 7. T version of the Cisc IOS used on R1 is _ Hubs are us in _____ sed _______ an MAUs ar used in __ nd re _________ networks. __ 8. H You t es e sing two 8-ports hubs (shown s 9. Y have to connect 14 machine on same LAN. Us below), sho the neces b ow ssary conne ections. Hub1 1 8 1 Hub b2 8
10. L the int List terfaces on three route of your choice. B sure to indicate th router ers r Be he number. n __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ ______ 11. E Elaborate on the inform o mation prese ented by the command show ve e d ersion. __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______
20
Comput Commun ter nication Net tworks
Lab Sessio 3 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
__________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______
Ethernet is used to con nnect to___ __________ whereas serial port is used to connect ___ s t 12. E to t _______ ________ an Token ring is used t connect t ________ nd to to ______. (Choose from the fol f llowing: ISD WAN, LAN, FDD DN, , DI) 13. E Elaborate on the cascad o ding of two or more hu o ubs. __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ 14. Specify the difference in output when you g e e gave the co ommand s shint e0 before and a after co onnecting th cable in s 11. he step __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ 15. W Which of th condition are poss he n(s) sible for an interface: a. b. c. d. adm ministratively down, lin protocol d y ne down adm ministratively down, lin protocol u y ne up adm ministratively up, line protocol up y adm ministratively up, line protocol dow y wn
Can al to f rial ce? 16. C you connect a DTE of a seria interface t a DTE of another ser interfac Will it i work? __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ 17. E Explain the possibility and effect of giving the clock rate comman on a DT serial e y t nd TE interface. i
21
Comput Commun ter nication Net tworks
Lab Sessio 3 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
__________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______ __________ _ __________ _________ __________ __________ __________ __________ _______
22
Comput Commun ter nication Net tworks
Lab Sessio 4 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Lab Session 04 b
OBJECT
Copyi IOS ima and con ing age nfiguration to and from CISCO r n m router.
THEO ORY
S f outer can be upgraded or replaced for additio e d onal compa atibilities The IOS image of a Cisco ro and sup pport as wel as bug fix The IOS image can be upgrad by mean of a flash card or ll xes. S n ded ns h through TFTP file transfer. Not all routers have slots for flash cards. So, TFTP is the h e f P dominan means of IOS upgr nt rade. Not on can an IOS image be downlo nly oaded from a TFTP server, i can also be backup u to a TFT server. T utility w it b up TP The would be to save an im o mage for later use in case so e, omething go wrong. oes tion to the IOS image, the running configurat g tion of the r router can a be back up to also ked In addit or resto ored from a TFTP serv You ca setup a T ver. an TFTP serve on a Cisc router, w IOS er co with image o running c or configuratio data file in memory, or on a PC with a TFTP server s on i , C software. In our la we have setup a TF server on the PC th acts as a console for the router rack. ab, e FTP o hat
PROC CEDURE
al lab ain IOS image and config guration on CISCO The goa of this l is to tra you to copy the I routers. In this lab you will be introduc to the u b ced utility on which all ne w etworking engineers thrive i.e. ping. 1. Con nnect to ro outer R1 an copy th IOS im nd he mage from the TFTP server at address 130.10.10.1. low owing steps s: Foll the follo the Step 1: Establish a console session with t router n done with a direct cons connec sole ction or virtu telnet co ual onnection. A direct This can either be d console connection is preferre over a te n ed elnet conne ection becau a telnet connection will be use n oot f are ion. lost during the rebo phase of the softwa installati Step 2: Configure the Router ure ernet interfa of the ro ace outer with t IP address 130.10.10.34 with a 24-bit the Configu the Ethe subnet m mask (255.2 255.255.0). Connect th Ethernet interface of the router and that of the PC he r onto the same hub. e t server has IP connectiv to the ro vity outer Step 3: Verify that the TFTP s red TFTP server Double cl r. lick the TFT server icon on the Desktop TP The PC is configur as the T he he onfigured w the IP address with to start the TFTP server. Th Ethernet card on th PC is co
23
Comput Commun ter nication Net tworks
Lab Sessio 4 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
130.10.10.1/24. P Ping the PC from the router console and make sure the ping i 100% C e is successf ful. Router r#ping 1 130.10.10 0.1 Type e escape s sequence to abor rt. Sendin 5, 100-byte ICMP Ec ng choes to 130.10 o 0.10.1, timeout is 2 second ds: !!!!! Succes rate is 100 percen (5/5) round ss 0 nt ), d-trip m min/avg/max = 1/2/4 ms Step 4: Begin the process of copying th new soft e f he tware image from the TFTP serve to the e er router Router enabl r> le Router r# Router copy tftp fla r# ash Step 5:S Specify the IP address of the TFTP server. P When p prompted, en the IP a nter address of th TFTP se he erver as in th following example: he g Addres or na ss ame of re emote ho ost [255.255.255 5.255]? 130.10.1 10.1 Step 6:S Specify the filename of the new C Cisco IOS so oftware ima age The IOS images ar stored in the directo c:\temp\ S re n ory \ios_images You can use any of the files s. under th directory for this la All the images are the same e his y ab. e except that their filena ames are differen nt. When p prompted, en the file nter ename of th Cisco IOS software image to be installed a in the he as followin example: ng Source file n e name? ios s_image1 1.bin Step 7: Specify the destination image file e n ename This is t name th new softw image will have o the he ware once it is loa aded onto th router. he Destin nation f file name [80180 e 0812.bin]? ios_i image1.b bin Step 8: Clear flash for new im h mage When p prompted, en "yes" to erase the existing sof nter ftware imag resident i the route Flash ge in er's memory before cop y pying the ne one: ew Erase flash d device be efore wr riting? [confirm m]y
24
Comput Commun ter nication Net tworks
Lab Sessio 4 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Flash contai ins [confi irm]y
fil les.
Are e
you
sure
you y
want t
to
erase? e
The rou asks you to confirm the copy process agai this time specifying what exact it is uter u m p in, e g tly going to do. o Copy 'ios_im mage1.bin n' from m Flash WITH er rase? [ye es/no]y server r as 'i ios_imag ge1.bin' into
The rou reloads after this p uter point using the emergency IOS sto ored in the ROM. It er rases the flash fil system a then con le and ntinues load ding the IO image fr OS rom the TFTP Server onto the flash. T entire co The opying proc cess takes several minu and dif utes ffers from n network to n network. During the transfer process, m r messages in ndicate if th specified file has b he d been accesse The ed. exclama ation point (!) indicate that the c es copy proces is taking place. Each exclamation point ss h (!) indic cates that te packets h en have been transferred successfull A check t ly. ksum verific cation of the imag occurs after the ima is writte to Flash m ge age en memory. Th router wi reload its with he ill self the new image once the softwa upgrade has been c w are e completed. Step 9:V Verify new software im mage has be loaded een eload is com mplete, the r router shou be runnin the desir Cisco IO image. Use the uld ng red OS After re "show version command to verify. n" ing creen shot du uring the co process. opy Followi is the sc r#ping 1 130.10.10 0.1 Router Type e escape s sequence to abor rt. Sendin 5, 100-byte ICMP Ec ng choes to 130.10 o 0.10.1, timeout is 2 second ds: !!!!! Succes rate is 100 percen (5/5) round ss 0 nt ), d-trip m min/avg/max = 1/2/4 ms Router r#copytf ftp flash h *** ** NOTICE **** * Flash load he elper v1. .0 This p process will acc cept the copy options a e and then termina n ate the c current system image to use t o the ROM based image fo the i or copy. Routin funct ng tionality will not be available during that ti y n e g ime. If you are logged in v d via teln net, th his conn nection will termin nate. Users with console access can see the results of the copy c r operat tion. --- ******** ----Procee ed? [con nfirm]y
25
Comput Commun ter nication Net tworks
Lab Sessio 4 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
System flash director m ry: File Length Name/s status 5435532 igs-in 1 2 nr-l.111 1-15.bin [54355 596 byte used, 2953012 available, 838 es 2 88608 total] Addres or na ss ame of re emote ho ost [130.10.10.1 1]? Source file n e name? ios s_image1 1.bin Destin nation f file name [ios_i e image1.bin]? Access sing fil 'ios_i le image1.b bin' on 130.10.1 10.1... Loadin ng ios_ _image1.b bin fro om 130.1 10.10.1 (via E Ethernet0 0): [OK] Erase flash d device be efore wr riting? [confirm m]y Flash contai ins fil les. Are you sure you e y [confi irm]y
want t
to
erase? e
Copy ' 'ios_ima age1.bin' from server ' s as ' 'ios_ima age1.bin' into Flash WITH erase [yes/no]y ' F e? %SYS-5 5-RELOAD Reload reques D: d sted %FLH: ios_ima age1.bin from 13 30.10.10.1 to fl lash ... System flash director m ry: File Length Name/s status 5435532 igs-in 1 2 nr-l.111 1-15.bin [54355 596 byte used, 2953012 available, 838 es 2 88608 total] Access sing fil 'ios_i le image1.b bin' on 130.10.1 10.1... Loadin ng ios_ _image1.b bin .fro om 130.10.10.1 (via E Ethernet0 0): [OK]
Erasin devic ng ce......e erased Loadin ng ios_ _image1. .bin fr rom 130 0.10.10.1 (via Ethern 1 net0): !!!!!! !!!!!!!! !!!!!!!!! !!! !!!!!! !!!!!!!! !!!!!!!!! !!!!!!!! !!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!! !!!!! !!!!!! !!!!!!!! !!!!!! [OK - 543553 32/838860 bytes 08 s] Verify ying che ecksum... OK (0 . 0x9E40) Flash copy to ook 0:03: :05 [hh: :mm:ss] %FLH: Re-boot ting syst tem afte download er 2. Now copy the c w configuratio from the same TFTP server at address 13 on 30.10.10.1. C Copying configu uration is mu easier th copying the IOS im uch han g mage. The con nfiguration f R1 is sto for ored in the f R1conf file fig.
Begin th process of copying the configuratio from the T he f e on TFTP server to the router runningrs configur ration.
26
Comput Commun ter nication Net tworks
Lab Sessio 4 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Router copy tftp run r# nning-co onfig uration filen name Specify the configu Addres of re ss emote hos st[255.2 255.255.255]? he as 0.1 Enter th address a 130.10.10 prompted, en the con nter nfiguration f filename loa aded as in th followin example: he ng When p Source file n e name? R1c config.t txt ok nfiguration o router R1 of 1. 3. Loo at the con
EXER RCISES
ermine the interface st tates after the configu t uration file has been lo oaded to th router he 1. Dete from the TFTP server. Rea m ason why th states are that way. he e ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
2. Backup the run nning config guration of the router to the TFTP server. t o __________ __________ _________ __________ __________ __________ __________ _______ ____ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
27
Comput Commun ter nication Net tworks
Lab Sessio 5 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Lab Session 05 b
OBJECT
Conf figuring sta routes o Cisco rou atic on uters.
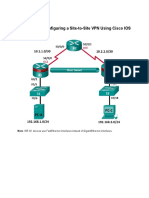
Figure 5.1: Scenario for static routes r s
THEO ORY
mplest metho to route packets on a network i static rou od is utes. Although dynamic routing c The sim protocols are flexib and adjust to netw ble work change they do have associa es, h ated networ traffic rk competes for network b bandwidth w the user data traffic. with r which c routes spec cify a fixed route for a certain destination network. They nee to be d r n ed Static r configu ured on any router that n needs to rea a netwo that it is not directly connected to. The ach ork s y d IOS com mmand used to configu static rou is ip route. Th syntax is: d ure utes he ip ro outedest tination-address ssubnet-m mask{ip-address | outg goinginterf face} [d distance] [tagta ] ag] [per rmanent] where: destinationd -address is the destina ation address prefix fo the netw or work that w would we like l the rou to reach uter h subnet-mask is the su s ubnet mask to be us on the address pr k sed refix to m match for destination addresses. Multiple ne d etworks ma be combined such t ay that the destinationaddress and subnet-ma combina a d ask ation matches all hosts on those ne etworks. ip-address specifies wh ip addre to forwa a packet to if an IP packet arrives with i hat ess ard t a destinatio address t on that matche the destin es nation-addre subnet-m ess mask pair s specified in i this comm mand. Alternativel outgoing A ly g-interface specifies w which interf face the pac cket should be sent d out o of. Add ding a static route to an Ethernet o other bro c n or oadcast inte erface (for e example, ip i route 0.0.0. 0.0.0 e .0 0.0 Ethe ernet 1/2) will cau the rou to be use ute inserted into the routin table onl when the interface i up. This c i ng ly e is configuratio is not on generally re g ecommende When th next hop of a static r ed. he route points to an interface, the s router consi r iders each o the hosts within the r of range of the route to be directly co e e onnected through tha interface and there t at e, efore it wil send AR requests to any des ll RP stination addresses th route thr a hat rough the st tatic route.
28
Comput Commun ter nication Net tworks
Lab Sessio 5 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
distance is the optiona administr d al rative distan value fo the route If unspecified the nce or e. default valu is 1. d ue tag t value ca be used a a "match" value for controlling redistributi via route maps. an as ion e permanent specifies th the rou will not be remove even if the interface shuts p hat ute t ed down. d
DTE/D DCE
DCE an DTE are the interfac nd ces.The DCE E-DTE con nnection bet tween router is referre to as a rs ed null seri cable DC ial CE(data com mmunicatio equipmen and DTE (Data term on nt) E minal equipm ment). DCE is located at t service p the provider end while the DTE is atta d ached device. rvices that are given t the DTE is often a to E accessed via modems or channel service l The ser unit/dat service un ta nit(CSU/DS SU). DCE provides cloc cking and D receive the clock DTE es k
PROC CEDURE
Connect the network a shown in the network diagram. e as k 1. C Configure a appropriate ip addresse and clock rates(if ne es k eeded) on t router in the nterfaces 2. C as a specified in the netw d work diagram m. For wing static routes 3. F R1, enter the follow ip ro oute 172. .16.20.0 255.255.255.0 192.168.10.2 0 ip rou ute 192. .168.20.0 255.25 55.255.0 192.168 8.10.2 On 4. O R2 enter: ip rou ute 172. .16.10.0 255.255 5.255.0 192.168. .10.1 ip route 17 72.16.20 0.0 255.255.255. 192.168.20.2 .0 On 5. O R3 enter: oute 172. .16.10.0 255.255.255.0 192.168.20.1 0 ip ro ip rou ute 192. .168.10.0 255.25 55.255.0 192.168 8.20.1 After that v verify the st tatic routes by entering the follow g wing comma ands in the p privilege 6. A mode: m rou uter# shi route ip e
EXER RCISES
1. Run t comman show IP route and w the nd write its outp put.
29
Comput Commun ter nication Net tworks
Lab Sessio 5 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
2. What is the defa adminis t ault strative dist tance of sta route? W atic Write the IP route com P mmand to modi the same ify e.
e ack nd n ss Now add 3.Create a loop ba interface on R3 an assign an IP addres 10.1.0.1 /16 to it. N stati routes to each of th other ro ic o he outers to re each this in nterface. Ve erify your w work by ping ging the new created interface fr wly rom routers R1 and R2 respectively. ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______
30
Comput Commun ter nication Net tworks
Lab Sessio 6 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Lab Session 06 b
OBJECT
Configu uring RIP(R Routing Inf formation Protocol). P
Figure 6 Scenario for RIP 6.1: o
THEO ORY
Routing Informatio Protocol is an Interio Gateway Protocol (I g on or y IGP), meani it is use within ing ed an autonomous sy ystem. An a autonomous system is a collectio of netwo s on orks under a single stration, sha aring a com mmon rout ting strateg A distan gy. nce-vector protocol, R was RIP adminis designed to work w small to medium-s with o sized networks. The ori iginal versi ion of RIP is based on the pro P ogram route (pronou ed unced "rout dee"), te distribu uted with th 4.3 Berk he keley Softw ware Distrib bution. RIP was in w P widespread u as a use efore it was formally defined in R s d RFC 1058. R Version 2, defined in RFC RIP n d routing protocol be dded some additional features and functiona d ality to the o original ver rsion. Both versions 2453, ad of RIP are discuss in this module. RF 2091 sp sed FC pecified add ditional ext tensions for RIP to r upport for d demand circ cuits (Trigg gered RIP). Support fo Triggered RIP was a or d added in allow su 12.0(1)T and will n be discu T not ussed here. Some a advantages of using R RIP, especially in small network is that there is ve little ks, ery overhea in terms of bandwi ad, s idth used an configur nd ration and m managemen time. RIP is also nt P easy to implement, compared to newer IGPs, and h been imp I has mplemented in networks around s the world. es ate rmance and to help pre d event routin loops. Al routers ng ll RIP use timers both to regula its perfor that use RIP send an update message to all of their neigh e d e hbors appro oximately e every 30 seconds this proce is terme advertisin The RFC specifies that advert s; ess ed ng. tisements sh hould be random mized by up to +/ five seconds in order to pr revent synch hronization of routing updates. The Cis implem sco mentation se ends update every 30 seconds m es minus up to 15 percent or 4.5 t, seconds s. If a neig ghbor has n respond in 180 s not ded seconds, it is assumed that the ne d eighboring r router is unavaila able or the network connecting it to the router has become un e nusable. W When the neighbo has not re or esponded fo 180 secon the rou is marke invalid; 180 seconds is long or nds, ute ed
31
Comput Commun ter nication Net tworks
Lab Sessio 6 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
enough that a route won't be i e invalidated by a single missed update message. The nei e ighbor is to sending a no ormal upda message with a met of "infi ate tric inity;" in shown t be unreachable by s the case of RIP, th number is 16. If an advertisement is rec e his n ceived from a neighbo with a m or metric o infinity, then the rou is place into hold of ute ed ddown state advertised with a dis e, d stance of 16, and kept in th routing ta d he able. No up pdates from other neig m ghbors for the same r route are accepted while the route is in h d holddown state. If othe neighbors are still ad s er s dvertising th same he route w when the hol lddown tim expires, then their updates will then be accepted. T route mer a The will be advertised with an inf finity metric for a peri of time after the ho c iod olddown sta if no ate e alternate paths are found. The act tual timers used to acc complish th above ta he asks are a r routing-upd date timer, a routeinvalid timer, a rou ute-holddow timer, an a route-f wn nd flush timer. The RIP ro outing-upda timer ate rally set to 30 second ensuring that each router will send a co ds, g l omplete cop of its py is gener routing table to all neighbors e every 30 seconds. The route-inval timer det lid termines ho much ow time mu expire w ust without a ro outer havin heard abo a partic ng out cular route before that route is considered invalid. When a ro oute is mar rked invalid or put in holddown s d state, neigh hbors are d ct. ification mu occur pr to expir ust rior ration of th route-flus timer. he sh notified of this fac This noti When t route fl the lush-timer e expires, the route is r e removed fro the rou om uting table. Typical initial v values for th hese timers a 180 seco are onds for the route-inva and rou e alid ute-holddow timers wn and 240 seconds fo the route0 or -flush timer The value for each o these tim can be adjusted r. es of mers with the timers ba e asic router configurat r tion command. ust d opology cha anges, RIP specifies n numerous st tability featu that ures To adju for rapid network-to are com mmon to man routing p ny protocols. R implem RIP ments split ho orizon with poison-rev h verse and holddow mechani wn isms to prev vent incorre routing information from bein propagated. Split ect n ng horizon prevents in n ncorrect me essages from being pro m opagated by not adverti ising routes over an s r h nting split h horizon help avoid ps interface that the router is using to reach the route. Implemen operates by advertising routes that are unreac y g t chable with a metric routing loops. Poison reverse o al f Holddown is a method of markin routes d ng of infinity back to the origina source of the route. H A d o om eighbors for the same r r route are invalid (expired). As discussed above, no updates fro other ne d holddown state. s accepted while the route is in h ed s ed ence and stability feature. Upd s dates are Triggere updates are also an include converge triggere whenever a metric for a route changes. T ed e Triggered u updates may also contain only y informa ation regard ding routes that have changed, unlike sc s e cheduled up pdates. The is a ere minimu delay of five second between triggered up um ds t pdates to pr revent updat storms. te
PROC CEDURE
Cable up th network a shown in the diagram he as n m. 1. C Assign the IP address as shown in the diagr i ram to the a appropriate interfaces. For the 2. A , used to indic a DCE port. cate serial links, has been u Issue RIP ro outing comm mands on a the router starting from the glo config m all rs fr obal mode. 3. I
32
Comput Commun ter nication Net tworks
Lab Sessio 6 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
4. O R1: On uter rip rou net twork 172 2.16.10. .0 net twork 192 2.168.10 0.0 On O R2 uter rip rou net twork 192 2.168.10 0.0 net twork 192 2.168.20 0.0 On O R3 router r r rip net twork 10. .0.0.0 net twork 192 2.168.20 0.0 wo nds the p IP. These tw comman enable t routing protocol RI 5. Ping the ho from R1. ost
escape s sequence to abor rt. Type e Sendin 5, 10 ng 00-byte I ICMP Ech hos to 10.0.0.1, timeou is 2 , ut second ds: !!!!! Succes rate is 100 p ss percent (5/5), round-tr rip min/avg/max = 1/2/4 ms
EXER RCISES
1. Conf figure RIP version 1 on two route Run De v n ers. ebug ip rip a note th address o which and he on upda are sent. ates ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______
e s y t d n 2. Write commands to modify the default update and hold-down timers for RIP v1. ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______
33
Comput Commun ter nication Net tworks
Lab Se ession7
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Lab Session 07 b
OBJECT
Configu uring RIP V Version 2
Figure 7. Scenario for RIPv2 .1:
THEO ORY
RIPv2 i almost the same as th RIP vers is e he sion 1. RipV also send its complete routing table to V2 ds g its active interfac ces at peri iodictime i intervals.Th timers,lo he oop avoida ance schem mes and strative dist tance are th same as Rip versi 1.But RIPv2 is c he s ion R considered c classless adminis routing protocol because it a also sends s subnet infor rmations w each ro with outer.It also allows o ication usin MD5 enc ng cryption sch heme. And it also suppo disconti orts iguous netw works. authenti Configu uring router with RIP v r version 2 is very simp Just add the comm s ple. d mand version 2under n the (co onfig-rou uter) # prompt and the route is running RIPv2. a er rou uter rip ver rsion 2 net twork 172 2.16.10. .0 net twork 192 2.168.10 0.0
EXER RCISES
outing table for Router R1. e r 1. Note down the ro __________ __________ __________ __________ __________ __________ __________ _______ ____ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______
34
Comput Commun ter nication Net tworks
Lab Se ession7
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
2. Run t comman debug rip and note d the nd p down the m multicast add dress on wh RIPv2 f hich forwards the u updates. ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______
3. Write down the s e source IP ad ddress for th ping pac he ckets when y ping H1 from R1. you 1 ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______
le w u H1 ch pback interf face? In 4. Whil working on R1, how could you check if H can reac the loop other words, how can you v r w verify if a pi from H1 to loopbac of R1 is successful? ing ck ? ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ __________ __________ __________ __________ __________ _______
35
Comput Commun ter nication Net tworks
Lab Se ession8
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Lab Session 08 b
OBJECT
Co onfiguring OSPF (Open Shortest Path First Single Ar t t) rea
THEO ORY
Open S Shortest Pat First (OSPF) was developed by the Inte th ernet Engin neering Tas Force sk (IETF) as a replace ement for th problem he matic RIP an is now th IETF-rec nd he commended Interior d ay SPF is a li ink state protocol tha as the n at, name impli ies, uses Gatewa Protocol (IGP). OS Dijkstra Shortest Path First ( a's (SPF) algori ithm. It is a open stan an ndards proto ocolthat is, it isn't propriet tary to any vendor or organization v n Like all link state protocols, O l p OSPF's major advantag over dis ges stance vecto protocols are fast or s reconve ergence, sup pport for m much larger internetwor and les susceptib rks, ss bility to bad routing d informa ation. Other features of OSPF are: f
The use of area which re as, educes the protocol's im p mpact on C CPU and me emory, cont tains the w ng nd possible the construction of hier e rarchical flow of routin protocol traffic, an makes p inter rnetwork to opologies Full classless behavior, eliminatingsuch classful problems as discontig ly guous subne ets Support of classless route table look e kups, VLSM and sup M, pernetting fo efficient address or nagement man A di imensionles arbitrary metric ss, y Equ ual-cost load balancing for more ef d fficient use of multiple paths. The use of res served mul lticast addre esses to reduce the im mpact on n non-OSPF-s speaking ices devi Support of auth hentication f more secure routing for g The use of rout tagging fo the tracki of exter routes te or ing rnal
eristics of OSPF Table 8.1 Characte Characterist tic VLSM support OSP PF Yes s
Manual summariza ation
Yes s
Type of protocol f
Link st tate
Classles support ss
Yes s
36
Comput Commun ter nication Net tworks
Lab Se ession8
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Auto-su ummarizatio on
No N
Discont tiguous supp port
Yes Y
Route p propagation
Multicast on change M n
Hop cou limit unt
None N
Converg gence
Fast F
Peer aut thentication n
Yes Y
Hierarch hical network kUpdates/ Route R computa ation
Event trigge E ered/ Dijkstra D
nd DR an BDR
DR (De esignated Ro outers): The DR has the fol R llowing duti ies:
To represent the multi-a t access netw work and i attached routers t the rest of the its d to t rnetwork inter To m manage the flooding pr rocess on th multi-acc network he cess k
The con ncept behin the DR is that the network it nd tself is con nsidered a "pseudonod " de," or a virtual r router. Each routeron the network forms an adjacency with the DR which re h k epresents the pseu udonode. On the DR will send L nly LSAs to the rest of the i internetwork k. Note: r router might be a DR o one of its attached m on s multi-access networks, and it migh not be s ht the DR on another of its attached multi-a access netwo orks. In other words, th DR is a p he property uter's interfa not the entire route ace, er. of a rou BDR(Backup Desi ignated Rou uter): A Back kup Design nated Route (BDR) is a hot sta er andby for t DR on the nmulti-acces links. ss TheBDR receives all routing updates fr R g rom OSPF adjacent ro outers but doesnt flo LSA ood updates.
37
Comput Commun ter nication Net tworks
Lab Se ession8
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Note: if the router interface p f priority valu is set to z ue zero then th router wont partic hat w cipate in the DR or BDR ele ections on th interface hat e.
Lo 0 11.1.1.1/24 172.16.68.1/ /21 Fa0/0 P=2 Cisco 2801 Fa0/1 10.1.1.1/24 E0 1.2/24 10.1.1
P=1
P=1 R1
Configu urations for cisco 2801
First form the physical top p pology as ab bove Ente interface configurati mode for fa0/0 an assign th given ip address and subnet er ion f nd he d mas sk In th interface configurati mode gi the com he ion ive mmand ipos spf prio ority 2 Exit from fa0/ and ente interface configurati mode o fa0/1. A t /0 er ion of Assign the g given IP addr and sub mask. A ress bnet Assign prio ority is in the previous s e step. Note As the given priori value is 1, which is default, therefore t e: g ity s there is no need of expl licit assignm ment Quit the interfa configur t ace ration mode e Now start confi w figuring the interfaces of R1 o
urations for R1 Configu
Ente the interf er face configu uration mod of R1 fo e0 and en the IP address and subnet de or nter d mas sk Quit from int t terface con nfiguration of e0 and type int d terface lo 0 in global n conf figuration mode m Now as you hav entered i w ve interface co onfiguration of loop bac 0 interfa assign th given n ck ace, he IP a address and subnet mas sk Quit from inter t rface config guration mo and inv ode voke router configurat r tion mode on both rout simultan ters neously
aneous configurations on both ro s outers Simulta
Ente the follo er owing com mmands on both rout n ters simulta aneously ( one route to be er conf figured by the student and the ot t ther one by the demo y onstrator) an press en after nd nter sync chronization of each co n ommand router rospf 1
Ente each of network com er n mmands on both routers simultaneo b s ously
38
Comput Commun ter nication Net tworks
Lab Se ession8
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
networ rk<netwo ork add dress of o interfaces swi itch><wil ldcard m mask> area 0
attach hed
to
the
Checkin the outc ng come of the election e
First check the routing ta e able by issu uing show ip rou w ute comm mand on pr rivileged mod or ping fr de rom cisco28 to the lo 801 oopback int terface of R1 R Now to check the state o your rout issue s w of ter, show ipospf inte erface co ommand from priviledge mode an note dow 1) your router ID, 2) your sta 3) Router ID of m ed nd wn ate desi ignated rout ter Issu show ip ue pospf ne eighbors command t further co to onfirm the status of adj s jacency Now type ipo w ospf database to find out wh hich LSAs have been exchanged and to s n d note their respe e ective seque ence numbers
RCISES EXER
ange the rou priority for Cisco 2801s fa0 interface to your r number and for uter y 0/1 roll r 1. Cha R1s e0 interfac to the pr ce resent year. Write the c configuratio command in the spa given on d ace belo ow._______ __________ __________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __
ntinuing exe ercise 1, res start the ospf process and reconf figure the networks. N n Now note 2. Con dow the route IDs of th designat router a backup designated router in th space wn er he ted and he give below. Also note down the defa value of Hello time en A ault f er ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
39
Comput Commun ter nication Net tworks
Lab Se ession8
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
3. Give command to change the default value of H e ds e Hello timer to your roll number an router l nd dead interval = 5 times the Hello inter d e rval. ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
40
Computer Communic cation Netwo orks
Lab Session 9 b
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
Lab Session 09 S
OBJEC CT
Configuring IGRP (Inte C erior Gatewa Routing P ay Protocol).
4
.1: mplementatio on Fig 9. Scenario for IGRP im
THEOR RY
In this la we will introduce you to your second rou ab, y uting protoco Interior G ol Gateway Ro outing Protocol (IGRP). Int terior Gatew Routing Protocol (IG way GRP) is a ro outing proto ocol develop in ped the mid-1 1980s by Cis Systems, Inc. In crea sco ating IGRP, Cisco had th principal goal to prov a he vide robust pr rotocol for routing with an auton r hin nomous syst tem (AS) ha 1 an arb aving bitrarily com mplex topology, and consist ting of medi with diver bandwid and delay characteris ia rse dth y stics. When I IGRP was deve eloped, the most popular intra-AS ro m r outing protoc was the R col Routing Info ormation Pro otocol (RIP). Th small hop he p-count limi (16) of RI restricted the size of internetwor and its s it IP rks, single metric (h count) di not allow for much routing flexibi hop id ility in comp plex environ nments. To provide additiona flexibility IGRP permits multipa routing. Dual equal al y, ath l-bandwidth lines may run a single st tream of tra affic in roun nd-robin fas shion, with automatic s switchover t the to second li if one lin goes dow Also, mu ine ne wn. ultiple paths can be used even if th metrics fo the s d, he or paths are different. For example, if one path is three tim better tha another b F , h mes an because its m metric t p times as oft ten. Only rou with m utes metrics is three times lower, the better path will be used three t that are within a certa range of the best rout are used a multiple p w ain te as paths. IGRP is a distance-vector protocol. Distance e-vector rout ting protocol call for ea router to send ls ach o all or a portion of its routing tab in a routi update m p s ble ing message at re egular interv to each of its vals neighbori ing routers. As routing informati ion prolifera ates through the netw h work, routers can s calculate distances to all nodes within the internetwork. o w IGRP use a combina es ation of adm ministrative distance and route metric to aid in r d cs routing decis sions. The dista ance value is the relative believability of a route, and the metric is the re s , elative desira ability of the rou In IGRP distance al ute. P, lways takes precedence over the me etric. The me etric is used when routes ha an equal distance. ave
41
Computer Communic cation Netwo orks
Lab Session 9 b
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
Administrative Dist tance Every rou uting protocol supported by Cisco ro d outers has a default-dista ance value a associated w it. with This valu is used to determine the relative believabili of a rout If the router has mu ue o e ity te. ultiple entries in its routing table to the same desti n e ination netw work, it will "believe" th route wit the he th lowest di istance value over routes with highe distance v e er values. It wi then choo the route with ill ose e the shorte distance value. Conn est nected and st tatic routes a have dis also stances associated with t them. RIP has an administrative distanc of 120 wh a ce hereas IGRP has an adm P ministrative d distance of 10 00. Distance is a factor when a route is running two differe routing p w er g ent protocols and learns abou the d ut same netw work from both protoco The prot b ols. tocol that ha a lower di as istance assoc ciated with i will it be the on whose en is install in the ro ne ntry led outing table of the route For exam er. mple, a netwo is ork running both RIP and IGRP. Fro the above table, you can see that the distance of IGRP is 100, b d om e t e s whereas the distance of RIP is 120. In this case, the IGR routes w be install in the ro t c RP will led outing table of th router. Be he ecause runni more tha one proto col is comm ing an mon, distance will always play e s a part in routing dec cisions. Dist tance is loca to the rou al uter. It is no advertised by any ro ot d outing s. protocols Metrics IGRP use a combination of met es trics. Interne etwork delay bandwidth reliability, and load can all y, h, be factore into the ro ed outing decision:
Intern network dela ayDelay measures the time it take an interfa to seriali the maxi m e es ace ize imum size for a packet that an inter f t rface can acc onto the physical m cept e media. The IG GRP internet twork delay is the speed of the med in units of 10 micros y d dia o seconds. To find the del in a path add lay h, all the delays from the outgoi interface and divide this numbe by 10. (Th delay is in tens e m ing es e er he n of microseconds). Slowe links have higher dela and fast links hav lower dela Delay c be config er e ays, ter ve ays. can gured by a network adm n ministrator, or you can use the Cisco default. W a Cisco router, the delay o u With seen with the show inte erface co ommand is in units of microsecon nds. The de elay comm mand, which allows us to change the default del for an int h o e lay terface, spec cifies the del in lay tens of microseco o onds.
Band dwidthBan ndwidth is th measure of the speed of the phys he o sical network connected to an k interf face. Bandw width is usu ually express in units of kilobits per secon (Kbps). I sed s s nd IGRP 7 bandw width is the inverse of the media bandwidth scaled by a factor of 10 . To fin the e f nd bandw width in a path, find th smallest of all the ba p he o andwidths f from outgoin interfaces and ng divide 10,000,000 by that nu e umber. (The bandwidth is scaled b 10,000,00 in kilobit per e h by 00 ts secon nd.) Cisco uses a facto of 1000 when using the bandwi o or w t idth comma and. A 64K serial conne ection has a bandwidth of 64,000 bits per se h econd. With a Cisco r h router, if yo configur the ou re band dwidth 64 command on a serial in 4 nterface, the result is a 6 bandwid e 64K dth.
42
Computer Communic cation Netwo orks
Lab Session 9 b
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
ReliabilityIGR reliability reflects the stability of the link, g RP y e f given as a fr raction of 25 A 55. value of 255 indi e icates a 100-percent stab link. This value is ba ble ased upon re eceived keep palive inform mation for th link. Reliability also incorporate how often the link tra he es n ansitions fro an om up sta to a down state, as well as the err rate of frames arrivin on the link ate n ror ng k. Load IGRP loa reflects th saturation of the link given as a fraction of 255. A val of ad he n k, f lue 255 indicates tha the link is 100-percen saturated. A value of 1 indicates that there is no i at s nt . f s traffic on the link Load reflec the utiliz c k. cts zation of a lin nk.
These me etric compon nents are co ombined in a user-defina able algorith with the result know as hm, e wn the comp posite metri By defau IGRP uses only b ic. ult, u bandwidth an delay in determinin its nd n ng composit metric. te To calcu ulate the co omposite metric, IGRP adds toge m P ether the w weighted val lues of diff fferent character ristics of the link to th network in question These va he n. alues (bandw width, bandw width divided by load, and delay) are weighted with the co b d e onstants K1, K2, K3, K and K5. The , K4, formula follows: f Metric = K1 * Bandw width + (K2 * Bandwidth h)/(256 Lo oad) + K3 * Delay The defau constant values are K1 = K3 = 1 and K2 = 0, so, when using the d ult K n default value the es, metric va can be simplified to: alue s Metric = Bandwidth + Delay Additiona ally, K4 and K5 default to 0. If K5 does not equ 0, an addi d d ual itional opera ation is done e: Metric = Metric * [K K5/(Reliabilit + K4)] ty w allest metric is the best p path. Remember, the path with the sma
PROCE EDURE
1. Use a /16 mask on all the inte erfaces. he 0.0.0-130.13. for all th links. .0.0 he 2. Use th address range 130.10 3. Use a bandwidth of 64000 bp for serial links. ps l o Scenario 1 me nk R bps ne ou 1. Assum that the ethernet lin between R1 and R3 is a 100Mb back bon link. Yo are asked not to have any broad d dcast traffic on this link But only unicast pac k. ckets are allo owed.
43
Computer Communic cation Netwo orks
Lab Session 9 b
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
Using the networ (a)10.0.0 for R1-fa g rks 0.0 a0/0 (b)11.0 0.0.0 for R1-s0/0 and R2 s0/0 (c)12.0.0.0 2 for R2 s0/1 and R3 s0/0 (d) 13.0.0.0 for R3 fa0/0.Con 2 R R nfigure IGRP appropriat P tely. 2. Change the mask on the R1-R R2serial link from /16 to /24. Check for network connectivi k o k k ity. If you have any pro h oblems with full connectivity, use th command that you h he ds have learnt s far so in this course to get full connectivity. g
Scenario 2 o 1. Change the mask on R1-R3 serial link ba to /24. ack 2. Confi igure IGRP on R3 such that R3 equ ually load ba alances betw ween the ethe ernet link an the nd serial link to reach the loopba interface on R1. l ack e 3. The serial link be s etween R3 and R1 is bei provided by a new I ing d ISP. It has been seen tha this at link is highly unr i reliable and a decision has been tak to use it only when the link bet h ken t tween R2 an R3 goes down. Make suitable ch nd hanges to yo IGRP co our onfiguration on R3 to r n reflect this. o Scenario 3 The seria link betwe R3 and R1 is now being provide by a diffe al een R ed erent ISP an has been f nd found to have a very high re eliability. Also the link between R3 and R2 has been upgrad to T3 an the b ded nd link betw ween R2 and R1 is a T1. Make neces ssary change to your IG es GRP configu uration on R and R3 R2 so tha it correctly reflects the bandwidths and delays. Also IGRP should load balance. at y e s P d
EXERC CISES
ement the ab bove given sc cenarios and write down the configu d n uration comm mands for ea of ach 1. Imple them, using Cisco routers. , o _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____
44
Computer Communic cation Netwo orks
Lab S Session 10
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
Lab Session 10 S
OBJEC CT
Config guringEIGR (Enhance Interior G RP ed Gateway Rou uting Protoc col)
THEOR RY
EIGRP is a proprieta Cisco pr s ary rotocol that runs on Cis routers. It is importa to under sco ant rstand EIGRP because it is probably on of the tw most popu routing protocols in use today. Like b ne wo ular n . IGRP, EI IGRP uses th concept of an autono he o omous system to describ a set of contiguous ro m be outers that run the same ro outing proto ocol and share routing information But unlik IGRP, EI n. ke IGRP includes the subnet mask in its ro updates. t m oute . Why pre EIGRP? efer EIGRP is sometimes referred to as a hybrid routing proto s a r ocol because it has chara e acteristics of both f distance vector and link state pro l otocols. For example, E r EIGRP doesn send link nt k-state packe as ets oes; instead it sends tra aditional dis stance vecto updates c or containing in nformation about OSPF do networks plus the co of reach s ost hing them from the per fr rspective of the adverti f ising router. And . EIGRP has link state characteristics as well it synchro h e onizes routin tables bet ng tween neigh hbours at startup and then se p ends specific updates onl when topo c ly ology chang occur. Th makes EI ges his IGRP suitable for very larg networks EIGRP ha a maximum hop coun of 255 (the default is set to f ge s. as um nt 100). EIGRP metric calcu m ulation: EIGRP unlike many other protoc that vuse a single fac to comp u cols e ctor pare routes a select the best and e possible path, EIGRP can use a combination of four: p P c 1) Bandw width ay 2) Dela 3) Load 4) Relia ability ring EIGRP P Configur Consider the topology:
Router r1
Router2 R PC2
PC1
172.16.3 32.2/24
172.16.16.2/2 24
Fig 10. .1:Scenario for EIGRP i implementat tion Following are the IP addresses as ssigned to th interfaces he
45
Computer Communic cation Netwo orks
Lab S Session 10
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
Router2 2#sh ipint brief ace Interfa Pr rotocol FastEth hernet0/0 FastEth hernet1/0 Serial2 2/0 Serial3 3/0 down FastEth hernet4/0 down FastEth hernet5/0 down Modem6/ /0 down Modem7/ /0 down /0 Modem8/ down Address IP-A unassigned 172.16.32.1 172.16.64.2 unas ssigned una assigned una assigned YES YES YES YES YES OK? ? Method d Stat tus
do m manual up own up m manual u up up m manual u up m manual ad dministra atively d down m manual ad dministra atively d down
YES m manual ad dministra atively d down YES YES YES m manual manual m m manual d down d down d down
igned unassi unassi igned unassi igned
Router1 1#sh ipint brief ace Interfa IP-AddressOK? Method Status s Protoc col
172.16.32.1YES man Fa0/0 nual up up p u YES manual adminis strativel down d ly down Fa1/0 unassigned manual up Serial2 2/0 172.16.64.1 YES up p Serial3 3/0 unassigned YES d manual administ tratively down d y down Fa4/0 unassigned u YES manu ual admin nistrativ vely down down n YES Fa5/0 unassigned u manu ual admin nistrativ vely down down n Tostart EIGRP proce on both ro E ess outers the fo ollowing con nfigurations w be done will e. Router1 1(config)#router eigrp 1 Router1 1(config-router)#network 172.16. 64.0 0.0 k 0.0.255 Router1 1(config-router)#network 172.16. 32.0 0.0 k 0.0.255 Router1 1(config-router)#exit Router2 2(config)#router eigrp 1 Router2 2(config-router)#network 172.16. 64.0 0.0 k 0.0.255 Router2 2(config-router)#network 172.16. 64.0 0.0 k 0.0.255 Router2 2(config-router)#network 172.16. 16.0 0.0 k 0.0.255 Router2 2(config-router)#exit
46
Computer Communic cation Netwo orks
Lab S Session 10
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
Now veri ifying the routing tables. . Router2 2#sh ip route Codes: C - con nnected, S - stat tic, I - IGRP, R - RIP, M - mobi ile, B - BGP P D - EIG GRP, EX - EIGRP external, O - OS e , SPF, IA - OSPF in nter area N1 - OS SPF NSSA externa type 1 N2 - OSPF NS al 1, SSA exter rnal type 2 E1 - OS SPF exter rnal type 1, E2 - OSPF e e external type 2, E EGP i - IS-IS, L1 - IS-IS level-1, L2 - I , IS-IS level-2, i ia i IS-IS inter area * - candidate default, U - perd -user sta atic rout te, o - O ODR P - periodic downloaded static route d y Gateway of last resort is not set 17 72.16.0.0/24 is subnetted, 3 sub bnets C 172.16.16.0 is directly connec cted, Fas stEtherne et0/0 D 172 2.16.32.0 [90/205 0 514560] via 172.16.64.1 00:01: 1, :36, Serial2 2/0 C 172.16.64.0 is directly connec cted, Ser rial2/0 Router1 1#sh ip route Codes: C - con nnected, S - stat tic, I - IGRP, R - RIP, M - mobi ile, B - BGP P D - EIG GRP, EX - EIGRP external, O - OS e , SPF, IA - OSPF in nter area N1 - OS SPF NSSA externa type 1 N2 - OSPF NS al 1, SSA exter rnal type 2 E1 - OS SPF exter rnal type 1, E2 - OSPF e e external type 2, E EGP i - IS-IS, L1 - IS-IS level-1, L2 - I , IS-IS level-2, i ia i IS-IS inter area * - candidate default, U - perd -user sta atic rout te, o - O ODR P - periodic downloaded static route d y Gateway of last resort is not set 72.16.0.0/24 is subnetted, 3 sub bnets 17 D 2.16.16.0 [90/205 0 514560] via 172.16.64.2, 00:01: :53, 172 Serial2 2/0 C 172.16.32.0 is directly connec cted, Fas stEtherne et0/0 C 172.16.64.0 is directly connec cted, Ser rial2/0
47
Computer Communic cation Netwo orks
Lab S Session 10
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
Now we will check end to end co e onnectivity from PCs. f PC2>pin 172.16.32.2 ng g ytes of d data: Pinging 172.16.32.2 with 32 by Reply Reply Reply Reply from f from f from f from f 172.16.32.2: 172.16.32.2: 172.16.32.2: 172.16.32.2: bytes= =32 bytes= =32 bytes= =32 bytes= =32 time= =156ms time= =125ms time= =127ms time= =141ms TT TL=126 TT TL=126 TT TL=126 TT TL=126
Ping st tatistics for 172.16.32.2: Pac ckets: Sent = 4, Received = 4, L Lost = 0 (0% loss s), Approxi imate round trip times in milli-seconds: Min nimum = 125ms, Maximum = 156ms, Average = 137ms M PC1>pin 172.16.16.2 ng Pinging 172.16.16.2 with 32 by g ytes of d data: Reply Reply Reply Reply from f from f from f from f 172.16.16.2: 172.16.16.2: 172.16.16.2: 172.16.16.2: bytes= =32 bytes= =32 bytes= =32 bytes= =32 time= =140ms time= =156ms time= =125ms time= =141ms TT TL=126 TT TL=126 TT TL=126 TT TL=126
Ping st tatistics for 172.16.16.2: Pac ckets: Sent = 4, Received = 4, L Lost = 0 (0% loss s), Approxi imate round trip times in milli-seconds: Min nimum = 125ms, Maximum = 156ms, Average = 140ms M Now disp playing EIGR topology on R2 only RP y y Router2 2#sh ipeigrp topology IP-EIGR Topology Table for AS 1 RP Codes: P - Passive, A - Active, U - Up pdate, Q - Query, R - Reply, p r - Reply status P 172.1 16.64.0/24, 1 successors, FD is 20512000 0 via Connected Serial2/0 d, 16.16.0/24, 1 successors, FD is 28160 P 172.1 via Connected FastEthernet0/ d, /0 P 172.1 16.4.0/24, 1 successors, FD is 2 20512000 via Connected Serial3/0 d, P 172.1 16.32.0/24, 1 successors, FD is 20514560 0
48
Computer Communic cation Netwo orks
Lab S Session 10
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
via 172.16.64.1 (20514560/281 160), Ser rial2/0 16.8.0/24, 2 successors, FD is 2 21024000 P 172.1 via 172.16.64.1 (21024000/205 512000), Serial2/ /0 via 172.16.4.1 (21024000/2051 12000), S Serial3/0 0 Router2 2#sh ipeigrp neighbors
RP IP-EIGR neighbors for process 1 H Ad ddress In nterface Seq CntNum 0 172.16.64.1 20 1 172.16.4.1 24
Hol Uptim ld me (se ec)
SRT TT
RTO
Q ( (ms)
Se e2/0 Se e3/0
12 10
00:02 2:50 00:02 2:50
40 40
1000 0 1000 0
0 0
EXERC CISES
1. What four routed protocols ar supported by EIGRP? t re d ? _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____
2. When is redistribution require for EIGR n ed RP? _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____
49
Computer Communic cation Netwo orks
Lab Session 11 n
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
Lab Session 11 S
OBJEC CT
Recovering lost router p R l password.
RY THEOR
In this lab you will le b earn the proc cedures requ uired to reco over a lost lo ogin or enabl password. The le . procedure differs de es epending on the platform and the s n m software use but in all cases, pass ed, l sword recovery requires tha the router be taken out of operation and power down. Note: at b t n red 1. Please use cisco as the passw a word where necessary. n 2. Please be prepare to do pass ed sword recove right awa The gro before yo might hav set ery ay. oup ou ve a pass sword other than cisco. 3. Use show ver s rsion comm mand to de etermine the platform b e before you t the pass try sword recov very. nfiguration register as pa of this lab The conf r art b. fig-register is a 16 s You will be working with the con bit regist ter. Look up informatio about the config-regi p on e ister on docu umentation CD, CISCO web O site, or an other reso ny ources availa to you. able Software Configura e ation Registe Bits (Wh do they m er hat mean) Bit Number 0 to 3 6 8 13 Valu ue 0x00 to 0x000 000 0F 0x00 (setting bit 6 to 1) 040 b 0x0100 0x20 000 Me eaning Boo field ot Cau uses system software to ignore m o NV VRAM conte ents Bre disabled eak d Boo default Flash soft ot tware if netw fails work boot fa
Explanat tion of Boot Field t Boot Fiel ld 0x0000 0xXXX1 0xXXX2 2 0xXXXF F Meaning M St tays at the sy ystem bootstr prompt rap Bo the first system ima in onboar Flash mem oots t age ard mory If you set the boot field value to 0x2 through 0xF and there is a valid v F bo system command sto oot c ored in the c onfiguration file, the rou boots n uter the system so oftware as directed by that value. If there is no boot d s sy ystem command, the rou forms a d uter default boot filename fo booting t or fro a networ server. If there is no network ser om rk f rver configu ured, as is the case in our lab, the standard setup dialogue is started. r
50
Computer Communic cation Netwo orks
Lab Session 11 n
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
PROCE EDURE
Assume you have been locked ou of the rou y ut uter. You ha access on to the us mode. Fo ave nly ser ollow the instru uctions below from the user mode. Do not get in privilege mode. w u D nto ed show vers sion and re ecord the value of the co onfiguration register. 1. Types 2. Using the power switch, turn off the route and then t g er turn it on. 3. Press CTRL+Bre on the te eak erminal key yboard within 60 second of the po n ds owerup to pu the ut router into ROMM r MON mode. . 4. This is where the procedure differs depen i d nding on the platform. For 25XX and 40 2 000:
Type o/r 0x2142or0x42at the > prompt t boot from flash wit 0 to m thout loadin the ng co onfiguration. Typeiorrese etat the > prompt. The router reboo but ignor its saved configuratio p ots res d on.
For 2600, 3600, 4500, 4700: 2 4
Type confre 0x2142 at the rom eg mmon 1> pro ompt to boo from Flash without loading ot h th configurat he tion. Type reset at the rom t mmon 2> prompt. Th router re p he eboots but i ignores its saved co onfiguration.
5. Type no after eac setup ques ch stion or press Ctrl-C to s skip the initial setup proc cedure. > Y enable mode and see the Router# pro e e ompt. 6. Type enable at the Router> prompt. You'll be in e emorcopy start run s nningto co the nonv opy volatile RAM (NVRAM into M M) 7. Type configme memo ory. Do not type config term. 8. Type config termand ma the chang t ake ges. The pro ompt is now hostname(c w config)#. 9. Type enable password <passwor to set th password to the new v p rd> he d value or issu the ue comm mand no en nable pas ssword. register 0x2102, or the value y recorded in step 1. o you d 10. Type config-r emorcopy running startup to commit the changes. r s o e 11. Type write me 12. Type show ver rsion and observe the configuration register se o c n etting careful lly.
51
Computer Communic cation Netwo orks
Lab Session 11 n
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
EXERC CISES
ain ng on-register is set to 0x254 s 42. 1. Expla the settin when the configuratio _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____
2. There are many different way to access a router. Wr down the ways. e d ys rite ese _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____
3. Expla the need for step 7 in password re ain n ecovery proc cedure. _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____
4. Write down the difference between enable p e e password and enable sec d cret pass sword. _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____
52
Computer Communic cation Netwo orks
Lab Session 11 n
NED University of Enginee ering & Technol logy Departme of Computer & Information Systems Engin ent r n neering
_____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ 5. What happens if enable password and en t f nable sec cret pas ssword ar the re same? ? _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____
6. When you config n gure enable password an issue the c p nd command sh how running you can se the g, ee passw word set for the privilege mode. Is there a meth to preve it from be t ed hod ent eing visible? ? _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____
7. Set th configura he ation-register to 0x2542. Reload the router. Do the break sequence w r e oes k work? Cross check with configurati s h ion-register settings and see if it m d matches with the settings s. there any differen nce? Explain n. _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ _____ __________ ___________ __________ ___________ __________ ___________ __________ _____ Is
53
Compute Communic er cation Netwo orks
Lab Sessio 12 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Lab Session 12 b
OBJECT
Stu udying and configurin Access Lists d ng
THEO ORY
An acce list is e ess essentially a list of co onditions th categor hat rize packets One of t most s. the common and easie to under n est rstand uses of access lists is filt s tering unwa anted packe when ets implem menting secu urity polici ies. Access lists can even be used in sit s u tuations tha dont at necessa arily involve blocking p e packets. There ar a few im re mportant rule that a pac follows when its being comp es cket s pared with a anaccess list: Rule#1 Its always compar with eac line of th access lis in sequen red ch he st ntial order that is, itl always ll start wit the first line of the a th l access list, th go to line 2, then li 3, and s on. hen ine so Rule#2 mpared with lines of the access list only u h until a mat is made Once the packet tch e. e Its com matches the condit s tion on a li of the access list, the packet is acted u ine a t upon and no further o compari isons take p place. Rule#3 s it t f ss t t There is an implici deny at the end of each acces listthis means that if a packet doesnt match th condition on any of the lines in the access list, the pa he n f n s acket will be discarded e d.Each of these ru has som powerful implication when filt ules me l ns tering IP pa ackets with a access lists, so keep , in mind that creatin effective access lists truly takes some prac d ng e s s ctice. There ar two main types of ac re n ccess lists: ccess lists 1. Standard ac 2. E Extended ac ccess lists rd ists Standar access li use e ket ondition tes All decis st. sions are These u only the source IP address in an IP pack as the co made ba ased on the source IP a address. Thi means tha standard access lists basically p is at s permit or deny an entire suite of protoco They do disting n e ols. ont guish betwee any of th many typ of IP en he pes traffic such as web, Telnet, UD and so o DP, on.
54
Compute Communic er cation Netwo orks
Lab Sessio 12 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Its comm mand synta is ax
-list<numb ber> {perm mit| deny} <destination> [log] access-
Fig 12.1 Standard Access list to allowmy network 1: A y Comma ands on rout will be ter R1(con nfig)#ac ccess-lis 1 per st rmit 172.16.0.0 0.0.255.255 R1(con nfig)#in nterface etherne 0 et R1(con nfig)#ip accessp -group 1 out R1(con nfig)#in nterface etherne 1 et R1(con nfig)#ip accessp -group 1 out The abo comma ove ands will pe ermit the ne etwork 172.16.0.0 only and will b y block other network through the router o its ethern interface in its out h on net es tside directions Extended access li ists Extende access lis can evalu many o the other fields in th ed sts uate of r helayer 3 and layer 4 he eaders of an IP pa acket. They can evalua source a destinat y ate and tion IPaddr resses, the p protocol fiel in the ld Network layer head and the port numb at the Tr k der, e ber ransport lay header. T gives e yer This extended access l lists the abil to make much more granular d lity e decisions wh control hen lling traffic. mand synta is ax Its comm s-list<n number> { {permit| deny} | access <proto ocol><so ource>[<p ports>]< <destination>[po orts][<options>] ]
55
Compute Communic er cation Netwo orks
Lab Sessio 12 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Fig 12.2: Extended a : access list ands on the r router will b be: Comma s-list 1 101 deny tcp 172 2.16.4.0 0.0.0.2 255 any eq 23 access access s-list 1 101 permi ip an any it ny interf face eth hernet 0 ip acc cess-gro oup 101 o out The abo comman will den only the telnet from subnet 172 ove nds ny 2.16.40.0 ou of E0 and will ut d permit a other traf all ffic.
EXER RCISES
Give co ommands to enable logg ging for the given acce list and t show the entries that have e ess to t been blo ocked.
________ ____________ ___________ ____________ ____________ ____________ ___________ ____________ ________ ________ ____________ ___________ ____________ ____________ ____________ ___________ ____________ ________ ________ ____________ ___________ ____________ ____________ ____________ ___________ ____________ ________ ________ ____________ ___________ ____________ ____________ ____________ ___________ ____________ ________ ________ ____________ ___________ ____________ ____________ ____________ ___________ ____________ ________ ________ ____________ ___________ ____________ ____________ ____________ ___________ ____________ ________ ________ ____________ ___________ ____________ ____________ ____________ ___________ ____________ ________
56
Compute Communic er cation Netwo orks
Lab Sessio 13 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Lab Session 13 b
OBJECT
St tudyingbasi LAN swit operatio ic tch on.
THEO ORY
LAN sw witch perfor 3 operat rms tions
Add dress learnin ng Forw ward filter decision d Loo avoidance op e
plore how a Ethernet s an switch learn addresses of the atta ns s ached In this lab session, we will exp hosts. Addres learning ss A new switch has empty MA address t AC table. As ea frame t ach transits swit tch, it learn source ns address aga ainst the so ource port. As the sw witch does not know to which port the MAC a destinat tion is attac ched, it ini itially trans smits the fr rame to all ports. Thi process i called is is flooding As the responses are received, the MAC ad g. e ddress table is further populated. p
PROC CEDURE
er wing scenar rio: Conside the follow
mainCSDsw
Cisco3560
Fig 13.1: Scenar for LAN switch ope rio N eration y d f Initially the MAC database of Cisco3560 will be h#sh mac c-address s-table Switch
Mac Ad ddress Ta able ------------------------------------------Vlan V Mac Addr ress Type
57
Ports
Compute Communic er cation Netwo orks
Lab Sessio 13 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
---1 Switch h#
----------0006.2a7 75.100c DYNA AMIC
-------Fa0/1
-----
at SDsw is And tha of mainCS ISDsw#sh mac-add h dress-ta able mainCI Mac Ad ddress Ta able ------------------------------------------Vlan V ---1 mainCI ISDsw# ping for any of the rem y maining comp puters, the M MAC Now as any of the computers generates p g address table will grow h#sh mac c-address s-table Switch Mac Addr M ress Tabl le ------------------------------------------Vlan V ---1 1 1 Switch h# r Also for mainCSDsw ISDsw#sh mac-add h dress-ta able mainCI Mac Add dress Tab ble ------------------------------------------Vlan V ---1 1 1 mainCI ISDsw# Mac Addr ress ----------0040.0ba a5.183a 0060.471 1b.ae01 00e0.f7a a4.475c Type -------DYNA AMIC DYNA AMIC DYNA AMIC Ports ----Eth1/1 Eth0/1 Eth0/1 Mac Addr ress ----------0006.2a7 75.100c 0040.0ba a5.183a 00e0.f7a a4.475c Type -------DYNA AMIC DYNA AMIC DYNA AMIC Ports ----Fa0/1 Fa0/1 Fa0/2 Mac Addr ress ----------0060.471 1b.ae01 Type -------DYNA AMIC Ports ----Eth0/1
58
Compute Communic er cation Netwo orks
Lab Sessio 13 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
EXER RCISES
1. If a destination MAC add n dress is not in the forw ward/filter t table, what will the sw witch do h ? with the frame? ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
h e dress is no in the ot 2. If a frame is received on a switch port and the source MAC add forw ward/filter ta able, what w the swit do? will tch ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
59
Compute Communic er cation Netwo orks
Lab Sessio 14 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Lab Session 14 b
OBJECT
Learnin Loop Av ng voidance wi Spannin Tree. ith ng
THEO ORY
The Spa anning Tree Protocol (STP) is a link layern e network pro otocol that ensures a loop-free topology for any sw witched LA Thus, th basic function of STP is to prev switchin loops AN. he vent ng uing broadc radiatio cast on. and ensu In the O model f compute networkin STP fall under the OSI layer-2. It is stand OSI for er ng, ls dardized as 802.1D. As the name sug e ggests, it c creates a sp panning tre within a mesh network of ee ted ypically Eth hernetswitch hes), and disables thos links that are not se t connect layer-2 switches (ty part of t spanning tree, leavi a single active path between an two netw the g ing h ny work nodes. . Spannin tree allow a networ design to include spa (redund ng ws rk o are dant) links to provide au o utomatic backup paths if an active link fails, witho the dang of switch loops, or the need for manual out ger h t r g/disabling of these ba ackup links. Switch loo must be avoided be ops ecause they result in enabling flooding the local n g network. STP is based on an algorit thm invent ted by Rad Perlman while w dia n working for Digital r ment ation. Equipm Corpora
col ation Protoc Opera
The col llection of s switches in a LAN can be conside n ered a graph whose no h odes are the bridges e and the LAN segm ments (or cab bles), and whose edges are the int w s terfaces con nnecting the bridges e To ops LAN while maintaining access to all LAN se g egments, to the segments. T break loo in the L dges collect tively comp pute a span nning tree. The spann ning tree is not neces s ssarily a the brid minimu cost span um nning tree. A network administrat can redu the cost of a spann tor uce t ning tree, if neces ssary, by alt tering some of the con e nfiguration p parameters in such a way as to a w affect the choice o the root o the spann of of ning tree. The spa anning tree that the bridges co e ompute usin the Spa ng anning Tree Protocol can be determined using th followin rules. he ng Select a root brid dge. The ro bridge of the span oot o nning tree is the bridge with the smallest s (lowest) bridge ID Each bri ) D. idge has a unique ide entifier (ID and a co D) onfigurable priority number the bridge ID contai both nu r; e ins umbers. To compare tw bridge IDs, the pr wo riority is compare first. If t bridges have equal priority, th the MAC addresses are compa ed two l hen s ared. For example if switche A (MAC e, es C=0200.000 00.1111) and B (MAC= d =0200.0000 0.2222) both have a h priority of 10, then switch A w be selected as the root bridge If the netw n will e. work admin nistrators e s n would like switch B to become the root bridge, they must set its priority to be less than 10.
60
Compute Communic er cation Netwo orks
Lab Sessio 14 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Determ mine the least cost path to the ro bridge. The compu spannin tree has t hs oot uted ng the property that messa y ages from a connecte device to the root br any ed o ridge traver a least co path, rse ost i.e., a pa from the device to t root tha has minim ath e the at mum cost am mong all pat from the device ths e to the ro The cos of travers oot. st sing a path is the sum o the costs o the segm i of of ments on the path. Differen technolog have di nt gies ifferent defa costs fo network s ault or segments. An administr A rator can con nfigure the c of trave cost ersing a part ticular netw work segmen nt. The pro operty that messages a m always trave erse least-co paths to the root is guaranteed by the ost o s followin two rules ng s. Least c cost path from each bridge. Aft the roo bridge h been ch fr fter ot has hosen, each bridge h determines the cost of each po t ossible path from itself to the root From thes it picks o with h f t. se, one allest cost (a least-cost path). The port conne a t e ecting to th path bec hat comes the r root port the sma (RP) of the bridge. f ost om ment. The br ridges on a network se egment coll lectively Least co path fro each network segm determine which br ridge has th least-cost path from the network segment to the root. T port he t k t The ting this br ridge to the network segment is then the designated port (DP) for the e s connect segmen nt. oot Any s t designated p is a port Disable all other ro paths. A active port that is not a root port or a d d blocked port (BP). Bridge Protocol Data Units ( D (BPDUs) ove escribe one way of dete ermining wh spannin tree will b compute by the hat ng be ed The abo rules de algorith but the rules as wri hm, r itten require knowledg of the ent network The bridg have e ge tire k. ges to deter rmine the ro bridge and compu the port roles (root, designated or blocke with oot ute d, ed) only the informatio that they have. To ensure that each bridg has enou informa e on y ge ugh ation, the bridges use specia data fram called B al mes Bridge Pro otocol Data Units (BP a PDUs) to e exchange ation about b bridge IDs a root pat costs. and th informa A bridg sends a B ge BPDU fram using the unique M me e MAC address of the por itself as a source rt address, and a desti ination addr of the S multica address 01:80:C2:00:00:00. ress STP ast re pes Us: There ar three typ of BPDU
Con nfiguration B BPDU (CBP PDU), used for Spanni Tree com d ing mputation Top pology Chan Notifica nge ation (TCN) BPDU, used to annou ) unce change in the net es twork topo ology Top pology Chan Notifica nge ation Ackno owledgment (TCA) t
BPDUs are exchan nged regula arly (every 2 seconds by default) and enabl switches to keep ) le f hanges and to start and stop forwa arding at por as requir rts red. track of network ch When a device is f first attache to a switc port, it w not imm ed ch will mediately st to forwa data. tart ard It will i instead go t through a n number of s states while it processe BPDUs and determ e es mines the topology of the net twork. When a host is a attached suc as a com ch mputer, printer or server the port r
61
Compute Communic er cation Netwo orks
Lab Sessio 14 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
will alw ways go into the forwar o rding state, albeit after a delay of about 30 se econds while it goes through the listeni and lea h ing arning states (see belo ow). The tim spent in the listen me n ning and learning states is d g determined b a value known as th forward delay (defa 15 seco by k he ault onds and set by th root brid he dge). Howev if inste another switch is co ver, ead onnected, th port may remain he y in block king mode if it is determined that it would cause a lo in the network. T d oop Topology Change Notificatio (TCN) B on BPDUs are u used to info other sw orm witches of port change TCNs p es. he gated to the root. Upon receipt e n are injected into th network by a non-root switch and propag CN, ot ill pology Chan flag in i normal B nge its BPDUs. Thi flag is is ofthe TC the roo switch wi set a Top propaga ated to all o other switches to instr ruct them t rapidly a out the forwarding table to age eir entries. Spannin Tree po states: ng ort
Bloc cking - A po that wou cause a switching loop, no use data is sen or receiv but it ort uld er nt ved may go into fo y orwarding m mode if the other links in use wer to fail an the spann re nd ning tree algo orithm deter rmines the port may tr ransition to the forwar o rding state. BPDU dat is still ta rece eived in bloc cking state. Liste ening - The switch pro e ocesses BPD and aw DUs waits possib new info ble ormation tha would at caus it to retur to the blo se rn ocking state e. Lear rning - Wh the por does not yet forwar frames ( hile rt t rd (packets) it does learn source t n addr resses from frames r m received an adds the to the filtering database (sw nd em d witching data abase) Forw warding - A port rece eiving and sending da normal operation. STP still m ata, monitors inco oming BPD that wo DUs ould indicat it should return to t blocking state to p te the g prevent a loop p. Disa abled - Not strictly part of STP, a network ad t dministrator can manua disable a port ally
onsider the f following to opology: Now co
mainCSDsw
Cisco3560
Fig 14.1 1:Scenario f impleme for enting spann ning tree physical loo can be ob op bserved Here a p bserve the sp panning tree calculations for main e nCSDsw fir rst Now ob ISDsw#sh spannin h ng-tree mainCI VLAN00 001
62
Compute Communic er cation Netwo orks
Lab Sessio 14 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Span nning tr ree enabl led prot tocol ieee Root ID t Priority y 327 769 Address 001 10.1100.58CE This bri idge is the root Hello Ti ime 2 sec Max Age 20 sec s 15 sec c Brid dge ID Priority y Address Hello Ti ime Aging Ti ime Interf face ---------------Et3/1 Et2/1 Et0/1 Et1/1 Role e ---Desg g Desg g Desg g Desg g Sts --FWD FWD FWD FWD
Forward De elay
327 769 (priority 3 32768 sy ys-id-ext 1) t 001 10.1100.58CE 2 sec Max Age 20 sec Forward De s elay 20 Co ost --------10 00 10 00 10 00 10 00 Prio.Nb br -------128.4 128.3 128.1 128.2 Type ----------------P2p P2p P2p P2p
15 sec c
For ci isco3560 the cal 0 lculatio ons will be Switch h#sh spa anning-tr ree VLAN00 001 Span nning tr ree enabl led prot tocol ieee Root ID t Priority y 327 769 Address 001 10.1100.58CE Cost 100 0 Port 1(F FastEthernet0/1) ) Hello Ti ime 2 sec Max Age 20 sec s 15 sec c Brid dge ID Priority y Address Hello Ti ime Aging Ti ime Interf face ---------------Fa0/1 Fa0/3 Fa0/2 Role e ---Root t Altn n Desg g Sts --FWD BLK FWD
Forward De elay
327 769 (priority 3 32768 sy ys-id-ext 1) t 00E E0.B02B.5EA0 2 sec Max Age 20 sec Forward De s elay 20 Co ost --------10 00 10 00 19 9 Prio.Nb br -------128.1 128.3 128.2 Type ----------------P2p P2p P2p
15 sec c
Modify ying priorities and oth parame her eters nge priority one can use the following command. e e g To chan default p
mainCIS SDsw(confi ig)#spanni ing-tree vlan 1 priority 36864
63
Compute Communic er cation Netwo orks
Lab Sessio 14 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
Now see what happ pens to the r root bridge. . mainCI ISDsw#sh spannin h ng-tree VLAN00 001 Span nning tr ree enabl led prot tocol ieee Root ID t Priority y 327 769 Address 00E E0.B02B.5EA0 Cost 100 0 Port 1(E Ethernet0/1) Hello Ti ime 2 sec Max Age 20 sec s 15 sec c Brid dge ID Priority y Address Hello Ti ime Aging Ti ime Interf face ---------------Et3/1 Et2/1 Et0/1 Et1/1 Role e ---Altn n Desg g Root t Desg g Sts --BLK FWD FWD FWD
Forward De elay
368 865 (priority 3 36864 sy ys-id-ext 1) t 001 10.1100.58CE 2 sec Max Age 20 sec Forward De s elay 20 Co ost --------10 00 10 00 10 00 10 00 br Prio.Nb -------128.4 128.3 128.1 128.2 Type ----------------P2p P2p P2p P2p
15 sec c
Other details on ST can be ob TP bserved thro ough the following set of comman under sp nds panning tree. h#sh spa anning-tr ree ? Switch acti ive Report o activ interfaces on on ve nly deta ail Detailed inform d mation inte erface Spanning Tree interface status and configurat g i s tion summ mary Summary of port states t VL vlan LAN Switc Spann ch ning Trees <cr>
EXER RCISES
at o witching loo in a netw ops work with re edundant sw witched path hs? 1. Wha is used to prevent sw ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
64
Compute Communic er cation Netwo orks
Lab Sessio 14 on
NEDUniv versity of Engin neering & Tech hnology Depa artment of Com mputer & Inform mation Systems Engineering s
2. Whe is STP co en onsidered said to be co onverged? ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
65
Comput Commun ter nication Net tworks
Lab Session 15 n
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
Lab Session 15 b
OBJECT
Configu uring Virtua LANs al
THEO ORY
A virtual LAN, co ommonly kn nown as a VLAN, is a group of hosts with a commo set of f h on ments that communica as if th were a ate hey attached to the same broadcast domain, requirem regardle of their physical loc ess cation. A VLAN has th same att V he tributes as a physical L LAN, but it allow for end s ws stations to b grouped together e be d even if they are not lo y ocated on th same he network switch. Ne k etwork reco onfiguration can be done through software in n nstead of ph hysically relocatin devices. ng To phys sically repli icate the fun nctions of a VLAN, it would be n t necessary to install a s separate, parallel collection of network cables an switches k nd s/hubs whic are kept separate f ch t from the y physically separate network, VLANs must share n V primary network. However unlike a p bandwid two se dth; eparate one-gigabit VL LANs using a single on ne-gigabit i interconnec ction can both suffer reduced throughpu and cong ut gestion. It v virtualizes VLAN beh V haviors (con nfiguring ports, taggin frames w ng when enterin VLAN, lookup MA table to switch/flood frames ng AC s d switch p to trunk links, and u k untagging w when exit fr rom VLAN.)
Implem mentation n
A basic switch not configured for VLAN will eith have VL c t d Ns her LAN functionality disa abled, or will hav it perm ve manently ena abled with what is kn nown as a default VL LAN which simply h contains all ports on the device as membe s o e ers. Configu uration of th first custom VLAN port group usually in he N p nvolves sub btracting po from orts the defa VLAN such that the first cu ault N, ustom grou of VLAN ports is a up N actually the second e VLAN on the device, apart fro the defa VLAN. The defaul VLAN typ om ault lt pically has an ID of 1. AN o t e l If a VLA port group were to only exist on the one device, all ports that are members of the VLAN group only need to b "untagge y be ed". It is on when the port gro is to ex nly oup xtend to t s ations to oc ccur from switch to sw witch, an another device that tagging is used. For communica port to ged r VLAN on th switch th uses tha uplink he hat at uplink p needs t be a tagg member of every V port, inc cluding the default VLA AN. Some switches eith allow o require a name be c her or created for the VLAN but it is only the N, ber mportant fro one swi to the next. om itch n VLAN group numb that is im Where a VLAN gr roup is to si imply pass t through an intermediat switch vi two passte ia -through ports, only the two ports need to be a me o d ember of th VLAN, a are tagg to pass both the he and ged d nd n mediate swit tch. required VLAN an the default VLAN on the interm Manage ement of the switch req e quires that the manage t ement funct tions be associated with one of h the conf figured VLA ANs. If the default VL LAN were d deleted or re enumbered without mo w oving the
66
Comput Commun ter nication Net tworks
Lab Session 15 n
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
ement to a different VLAN firs it is po st, ossible to be locked out of the switch b e manage configu uration, requ uiring a forc clearing of the devi configur ced g ice ration to reg control. gain es y built-in met thod to ind dicate VLA port me AN embers to s someone Switche typically have no b working in a wirin closet. It is necessar for a tech g ng ry hnician to either have m e managemen access nt to the d device to vie its config ew guration, or for VLAN port assign r N nment chart or diagram to be ts ms xt witches in ea wiring closet. Thes charts mu be manu ach c se ust ually update by the ed kept nex to the sw technica staff whe al enever port m membership changes a made to the VLANs p are s. Remote configura e ation of V VLANs pre esents seve eral opport tunities for a techni r ician to acciden ntally cut o commun off nications and lock th a hemselves out of the devices t e they are ing figure. Actio such as subdividin the defa VLAN by splitting off the ons s ng ault g attempti to conf switch uplink po orts into a separate new VLA can su AN uddenly cu off all remote ut nication, re equiring the technician to physically visit the device in the distant location e commun to contin the con nue nfiguration p process. When in nside the wo of VLA there a two type of links. These links allow us to orld ANs are es s o connect multiple sw t witches toge ether or just simple net t twork devic e.g PC, t will acc the ces that cess VLAN n network. Depending on their conf n figuration, th are call Access Links, or Tr hey led L runk Links. Access Links he mmon type of links on any VLAN switch. All network hosts N l Access Links are th most com t s rder to gain access to th local net n he twork. Thes links se connect to the switch's Access Links in or are your ordinary p r ports found on every sw witch, but co onfigured in a special way, so you are n w u able to p plug a comp puter into th and acc your ne hem cess etwork. Link Trunk L A Trunk Link, or 'T k Trunk' is a p configu port ured to carry packets fo any VLA These ty of y or AN. ype ports are usually fo ound in conn nections bet tween switc ches. These links requir the abilit to re ty ackets from all availabl VLANs because VL le b LANs span o over multipl switches. le . carry pa
PROC CEDURE
VLAN 1 is the defa fault Switch #shint h tvlan 1 Vlan1 is admi inistrati ively do own, line protoc col is d down Hard dware is CPU Int s terface, address is 00e , e0.b02b.5ea0 (bi ia 00e0.b b02b.5ea a0) MTU 1500 by ytes, BW 100000 Kbit, DLY 10000 000 usec c, reliabil r lity 255/ /255, tx xload 1/255, rxl load 1/255 Configu uring IP on default VLAN n Switch h(config g)#intvla 1 an Switch h(config g-if)#ip address 172.16.68.2 25 s 55.255.248.0
67
Comput Commun ter nication Net tworks
Lab Session 15 n
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
Creatin VLANs ng Switch h(config g)#intvla 2 an Assigni ports to vlans ing o Switch h(config g)#intfa 0/2 Switch h(config g-if)#swi itchport mode access t Switch h(config g-if)#swi itchport access vlan 2 t Configu uring trunk link k Conside the follow er wing topology
mainCSDsw
Cisco3560
Fig 1 15.1:Scenari for imple io ementing VL LANs Suppose mainCSD has two VLANs co e Dsw onfigured V VLAN1 and VLAN2, w whereas cisco o3560 has only VLAN1. N both sw y Now witched mu have at l ust least one common trunk link conne k ecting the two switches, so that the P which a in VLAN may com PCs are N1 mmunicate. Here we ha ave h d er. ation would be interface fa 0/1 on each switch connected to the othe Hence the configura Switch h(config g)#intfa 0/1 Switch h(config g-if)#swi itchport mode trunk t Verifica ation of con nfiguration ns Switch h#show i interface switch e hport Name: Fa0/1 Switch hport: E Enabled Admini istrativ Mode: trunk ve Operat tional M Mode: tru unk Admini istrativ Trunki ve ing Enca apsulation: dot1 1q Operat tional T Trunking Encapsu ulation: dot1q Negoti iation o Trunki of ing: On Access Mode V s VLAN: 1 ( (default t) Trunki ing Nati ive Mode VLAN: 1 (default) Voice VLAN: n none Admini istrativ privat ve te-vlan host-associatio on: none Admini istrativ privat ve te-vlan mapping: none
68
Comput Commun ter nication Net tworks
Lab Session 15 n
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
istrativ privat ve te-vlan trunk native VL LAN: non ne Admini Admini istrativ privat ve te-vlan trunk encapsula ation: d dot1q Admini istrativ privat ve te-vlan trunk normal VL LANs: none Admini istrativ privat ve te-vlan trunk private V VLANs: n none Operat tional p private-v vlan: no one Trunki ing VLAN Enable Ns ed: All Prunin VLANs Enabled 2-100 ng s d: 01 Captur Mode Disabled re d Captur VLANs Allowed ALL re s d: Protec cted: fa alse Unknow unica wn ast block ked: dis sabled Unknow multi wn icast blo ocked: disabled d d Applia ance tru ust: none e Name: Fa0/2 Switch hport: E Enabled Admini istrativ Mode: static access ve Operat tional M Mode: sta atic acc cess Admini istrativ Trunki ve ing Enca apsulation: dot1 1q Operat tional T Trunking Encapsu ulation: native Negoti iation o Trunki of ing: Off f Access Mode V s VLAN: 1 ( (default t) Trunki ing Nati ive Mode VLAN: 1 (default) Voice VLAN: n none Admini istrativ privat ve te-vlan host-associatio on: none Admini istrativ privat ve te-vlan mapping: none Admini istrativ privat ve te-vlan trunk native VL LAN: non ne Admini istrativ privat ve te-vlan trunk encapsula ation: d dot1q Admini istrativ privat ve te-vlan trunk normal VL LANs: none Admini istrativ privat ve te-vlan trunk private V VLANs: n none Operat tional p private-v vlan: no one Trunki ing VLAN Enable Ns ed: All A more handy way of verifyin VLAN m y ng memberships would be s mainCI ISDsw#sh hvlan bri ief VLAN N Name ---- -------------------------------1 default d Eth3/1 Eth4/ 1, /1 2 VLAN0002 V 2 1002 f fddi-def fault 1003 t token-ri ing-defau ult 1004 f fddinet-default 1005 t trnet-de efault Statu us Ports --------- -------------activ ve Eth2/1, activ ve activ ve activ ve activ ve activ ve Eth1/1
69
Comput Commun ter nication Net tworks
Lab Session 15 n
NED Univ versity of Engin neering & Tech hnology Depa artment of Com mputer & Infor rmation System Engineering ms
EXER RCISES
at nking provid de? 1. Wha does trun ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
2. Wha type of li is only part of one VLAN an is referre to as the native VL at ink e nd ed LAN of the p port? ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______ ____ __________ __________ _________ __________ __________ __________ __________ _______
70
Você também pode gostar
- Ethernet CablingDocumento8 páginasEthernet CablingOctav EnachiAinda não há avaliações
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkAinda não há avaliações
- 2.3.3.4 Lab - Building A Simple Network - ILMDocumento18 páginas2.3.3.4 Lab - Building A Simple Network - ILMcisocsyAinda não há avaliações
- CCNASv1 1 Chp08 Lab B RMT Acc VPN Instructor PDFDocumento33 páginasCCNASv1 1 Chp08 Lab B RMT Acc VPN Instructor PDFAhmadHijaziAinda não há avaliações
- Ccnasv1.1 Chp04 Lab-A Cbac-Zbf InstructorDocumento43 páginasCcnasv1.1 Chp04 Lab-A Cbac-Zbf Instructorclearmoon247Ainda não há avaliações
- Lab6 - 2 CiscoDocumento8 páginasLab6 - 2 CiscoMoussa MarAinda não há avaliações
- Module4 (LAB) - Serial ConfigurationDocumento15 páginasModule4 (LAB) - Serial ConfigurationJoyce Ann Rufino100% (1)
- 2.3.3.4 Lab - Building A Simple NetworkDocumento14 páginas2.3.3.4 Lab - Building A Simple NetworkMaria Tudosa50% (2)
- Csc261 CCN Lab ManualDocumento125 páginasCsc261 CCN Lab ManualasadhppyAinda não há avaliações
- 2.3.3.3 Lab - Building A Simple Network PDFDocumento13 páginas2.3.3.3 Lab - Building A Simple Network PDFPetra Miyag-aw100% (1)
- 8.3.3.3 Lab - Collecting and Analyzing NetFlow Data - ILM PDFDocumento13 páginas8.3.3.3 Lab - Collecting and Analyzing NetFlow Data - ILM PDFDominguez Ronald100% (2)
- Sem1 Batch1 PDFDocumento73 páginasSem1 Batch1 PDFMustapha OulcaidAinda não há avaliações
- 5.1.3.6 Lab - Viewing Network Device MAC AddressesDocumento7 páginas5.1.3.6 Lab - Viewing Network Device MAC Addressesbekirm10% (3)
- CN Labsheet 1Documento8 páginasCN Labsheet 1Nu YangAinda não há avaliações
- 6.5.1.2 Lab - Building A Switch and Router NetworkDocumento8 páginas6.5.1.2 Lab - Building A Switch and Router NetworkParthPatel100% (8)
- CCNA Lab ManualDocumento127 páginasCCNA Lab ManualMuhammad Kashif Iqbal100% (1)
- CN-lab, Hina Gul (17pwele5108)Documento53 páginasCN-lab, Hina Gul (17pwele5108)Wajid AliAinda não há avaliações
- CCN LAB ASSIGNMENT 1 - (VLANS AND TRUNKING LAB) - 26feb2020Documento4 páginasCCN LAB ASSIGNMENT 1 - (VLANS AND TRUNKING LAB) - 26feb2020luhoni jonaAinda não há avaliações
- 6.4.3.5 Lab - Building A Switch and Router NetworkDocumento11 páginas6.4.3.5 Lab - Building A Switch and Router NetworkfutjulyAinda não há avaliações
- CNE Tutorial 02 - Real - LAN and LAN With Packet TracerDocumento18 páginasCNE Tutorial 02 - Real - LAN and LAN With Packet TracerThơm VũAinda não há avaliações
- How To Configure Your Router To Allow Fast Bit Torrent DownloadsDocumento10 páginasHow To Configure Your Router To Allow Fast Bit Torrent DownloadsRam Sagar Mourya0% (1)
- Lab - Configuring A Site-to-Site VPN Using Cisco IOS and CCPDocumento30 páginasLab - Configuring A Site-to-Site VPN Using Cisco IOS and CCPVasan Suryaßoyzz100% (1)
- Network Devices & Packet Tracer Objectives:: A Router Also IncludesDocumento27 páginasNetwork Devices & Packet Tracer Objectives:: A Router Also IncludesHunter BunterAinda não há avaliações
- Updated Computer NetworkDocumento27 páginasUpdated Computer NetworkAryan SinghAinda não há avaliações
- Lesson 9.2.1Documento11 páginasLesson 9.2.1Rye Rye LasorAinda não há avaliações
- 2.3.3.3 Lab - Building A Simple Network - ILMDocumento18 páginas2.3.3.3 Lab - Building A Simple Network - ILMshm2hotmail.comAinda não há avaliações
- Erras LindiardaMahentar - LAM+4Documento10 páginasErras LindiardaMahentar - LAM+4Erras LmAinda não há avaliações
- Experiment 3Documento34 páginasExperiment 3dundundunzAinda não há avaliações
- CCN 2010Documento98 páginasCCN 2010abbass512Ainda não há avaliações
- Lab 2 HandoutDocumento7 páginasLab 2 Handouthassaan tanveerAinda não há avaliações
- 8.7.1.1 Lab - Configuring A Site-To-Site VPN Using Cisco IOS and CCP - InstructorDocumento47 páginas8.7.1.1 Lab - Configuring A Site-To-Site VPN Using Cisco IOS and CCP - InstructorSalem TrabelsiAinda não há avaliações
- Lab Reports: Department of Electrical Engineering, University of Engineering and Technology, PeshawarDocumento30 páginasLab Reports: Department of Electrical Engineering, University of Engineering and Technology, PeshawarWajid AliAinda não há avaliações
- 5 It344 CNDocumento28 páginas5 It344 CNrashmi mAinda não há avaliações
- 11.3.4.6 Lab - Using The CLI To Gather Network DeviDocumento11 páginas11.3.4.6 Lab - Using The CLI To Gather Network DeviRichardWhitley20% (5)
- 2.3.3.3 Lab - Building A Simple NetworkDocumento13 páginas2.3.3.3 Lab - Building A Simple NetworkDaisy Galvan33% (3)
- Lab Assignment 2018-2019Documento15 páginasLab Assignment 2018-2019tuyambaze jean claudeAinda não há avaliações
- DC Rec RemainingDocumento25 páginasDC Rec Remainingbilnot9Ainda não há avaliações
- 8.3.3.3 Lab - Collecting and Analyzing NetFlow Data PDFDocumento7 páginas8.3.3.3 Lab - Collecting and Analyzing NetFlow Data PDFbeef22Ainda não há avaliações
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationDocumento8 páginas11.3.4.6 Lab - Using The CLI To Gather Network Device InformationSuen Clarke0% (1)
- 8.7.1.2 Lab - Configuring A Remote Access VPN Server and Client - InstructorDocumento37 páginas8.7.1.2 Lab - Configuring A Remote Access VPN Server and Client - InstructorSalem TrabelsiAinda não há avaliações
- ESwitching Lab 1 3 1Documento12 páginasESwitching Lab 1 3 1Derek Ang Yew PinAinda não há avaliações
- Configuring Devices For Use With Cisco Configuration Professional (CCP) 2.5Documento8 páginasConfiguring Devices For Use With Cisco Configuration Professional (CCP) 2.5Irfee100% (1)
- Lab 1.3.1Documento12 páginasLab 1.3.1Alondra CarmonaAinda não há avaliações
- Cisco Lab :building A Simple Network With AnswersDocumento14 páginasCisco Lab :building A Simple Network With AnswersEmzy Soriano50% (2)
- 2.3.3.4 Lab - Building A Simple NetworkDocumento14 páginas2.3.3.4 Lab - Building A Simple Networkroberto002Ainda não há avaliações
- Router Troubleshooting Guide: DefinitionsDocumento9 páginasRouter Troubleshooting Guide: Definitionsebossé_1Ainda não há avaliações
- PT 8.2.5.4 Stadium Redundancy Test Plan StudentDocumento14 páginasPT 8.2.5.4 Stadium Redundancy Test Plan Studentonlycisco.tkAinda não há avaliações
- CCN-Lab No. 01 Title:: Packet TraceDocumento18 páginasCCN-Lab No. 01 Title:: Packet TraceNaveed LatifAinda não há avaliações
- T BOX ManualDocumento26 páginasT BOX ManualVlady TeoAinda não há avaliações
- Diorey Practice ExamDocumento22 páginasDiorey Practice ExamYeroid Diorey PotestasAinda não há avaliações
- ACN FileDocumento19 páginasACN FileSalil BansalAinda não há avaliações
- 2.3.3.5 Lab - Configuring A Switch Management AddressDocumento8 páginas2.3.3.5 Lab - Configuring A Switch Management AddressNicolas Bonina33% (3)
- 8 4 1 3 Lab Configure Site To Site VPN Using CLI InstructorDocumento15 páginas8 4 1 3 Lab Configure Site To Site VPN Using CLI InstructorMujeeb Rahman DostAinda não há avaliações
- Lab ManualDocumento82 páginasLab ManualSafa MAinda não há avaliações
- DCN Exp 1-2022Documento6 páginasDCN Exp 1-2022Soham SawantAinda não há avaliações
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationAinda não há avaliações
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNo EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksAinda não há avaliações
- Computer Networking: An introductory guide for complete beginners: Computer Networking, #1No EverandComputer Networking: An introductory guide for complete beginners: Computer Networking, #1Nota: 4.5 de 5 estrelas4.5/5 (2)
- CompTIA A+ Complete Review Guide: Core 1 Exam 220-1101 and Core 2 Exam 220-1102No EverandCompTIA A+ Complete Review Guide: Core 1 Exam 220-1101 and Core 2 Exam 220-1102Nota: 5 de 5 estrelas5/5 (2)
- Infilink Evolution: Product DatasheetDocumento5 páginasInfilink Evolution: Product DatasheethithamAinda não há avaliações
- TMA LTE BTS (R05) Configuration Guide PDFDocumento24 páginasTMA LTE BTS (R05) Configuration Guide PDFgopizizou100% (2)
- What Is That?Documento15 páginasWhat Is That?ajipurnomoAinda não há avaliações
- Global AcceleratorDocumento1 páginaGlobal AcceleratorMadhav PandaAinda não há avaliações
- Setup For UniFi HyppTV - MikroTik Support MalaysiaDocumento20 páginasSetup For UniFi HyppTV - MikroTik Support Malaysiahangtuah79Ainda não há avaliações
- Multidatagram Messaging MeghdutDocumento6 páginasMultidatagram Messaging MeghdutMeghdut BakaleAinda não há avaliações
- Communications and Network SecurityDocumento43 páginasCommunications and Network SecurityEL MAMOUN ABDELLAHAinda não há avaliações
- 802.15.4 and Zigbee Routing Simulation: at Samsung/CunyDocumento22 páginas802.15.4 and Zigbee Routing Simulation: at Samsung/CunyEng. Abdalla sheik Aden RaageAinda não há avaliações
- Veritas Netbackup™ Network Ports Reference Guide: Release 9.1Documento23 páginasVeritas Netbackup™ Network Ports Reference Guide: Release 9.1黃國峯Ainda não há avaliações
- 3a Reflector AntennasDocumento60 páginas3a Reflector AntennasEncep Rahmat FadillahteaAinda não há avaliações
- MFC-T4500DW - Brother PhilippinesDocumento1 páginaMFC-T4500DW - Brother PhilippinesArvin ColladoAinda não há avaliações
- Frequency BandsDocumento6 páginasFrequency BandsAaron HongreiAinda não há avaliações
- SWU ConfigDocumento6 páginasSWU ConfigharyantojogjaboyAinda não há avaliações
- 32PFL3605 Tpm4.1e - LaDocumento64 páginas32PFL3605 Tpm4.1e - Laismosch100% (1)
- VX-1700 Owners ManualDocumento32 páginasVX-1700 Owners ManualVan ThaoAinda não há avaliações
- Mapping Physical To Logical Address: RARP, BOOTP, and DHCPDocumento2 páginasMapping Physical To Logical Address: RARP, BOOTP, and DHCPWasim firujAinda não há avaliações
- Bluetooth® Digital Alarm Clock: With Usb Port For Phone ChargingDocumento2 páginasBluetooth® Digital Alarm Clock: With Usb Port For Phone ChargingAlin MarcuAinda não há avaliações
- Intel Thunderbolt: James Coddington Ed MackowiakDocumento28 páginasIntel Thunderbolt: James Coddington Ed MackowiakAkalatronic TunezAinda não há avaliações
- Open Lab Quiz 1 (10 - 2 - 21) (1-22)Documento7 páginasOpen Lab Quiz 1 (10 - 2 - 21) (1-22)Poorna RenjithAinda não há avaliações
- BiTs ElectronicsDocumento3 páginasBiTs ElectronicselectronicartAinda não há avaliações
- Low RF-Complexity Technologies To Enable Millimeter-Wave MIMO With Large Antenna Array For 5G Wireless CommunicationsDocumento7 páginasLow RF-Complexity Technologies To Enable Millimeter-Wave MIMO With Large Antenna Array For 5G Wireless CommunicationsAhmet Sacit SümerAinda não há avaliações
- How - To - Present - Cyber - Security - To - Senior - Management - Complete - Deck - Slide07 (7 Files Merged)Documento7 páginasHow - To - Present - Cyber - Security - To - Senior - Management - Complete - Deck - Slide07 (7 Files Merged)tcAinda não há avaliações
- DMX Usb Pro Api SpecDocumento9 páginasDMX Usb Pro Api SpecPinguins Aire LibreAinda não há avaliações
- Intelligent Cell ConceptDocumento28 páginasIntelligent Cell ConceptMohammed AbdallahAinda não há avaliações
- Marantz SR-8002 Service ManualDocumento203 páginasMarantz SR-8002 Service ManualManoel CesarAinda não há avaliações
- ICT Vietnam White Book 2010 - Eng (MIC)Documento75 páginasICT Vietnam White Book 2010 - Eng (MIC)Tuan NguyenAinda não há avaliações
- C406-N Product Manual 570-5060RDocumento90 páginasC406-N Product Manual 570-5060RAlexAinda não há avaliações
- DekTec DTE-3137Documento7 páginasDekTec DTE-3137Alexander WieseAinda não há avaliações
- DC LAB Hand Book For Every ExperimentDocumento11 páginasDC LAB Hand Book For Every ExperimentSivagopiGopisetty0% (1)
- Philadelphia 5G Summit AgendaDocumento3 páginasPhiladelphia 5G Summit AgendaMRousstiaAinda não há avaliações