Escolar Documentos
Profissional Documentos
Cultura Documentos
Compression II
Enviado por
Jagadeesh NaniDescrição original:
Direitos autorais
Formatos disponíveis
Compartilhar este documento
Compartilhar ou incorporar documento
Você considera este documento útil?
Este conteúdo é inapropriado?
Denunciar este documentoDireitos autorais:
Formatos disponíveis
Compression II
Enviado por
Jagadeesh NaniDireitos autorais:
Formatos disponíveis
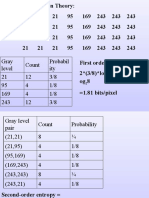
Using Information Theory:
21 21 21 95 169 243 243 243
21 21 21 95 169 243 243 243
21 21 21 95 169 243 243 243
21 21 21 95 169 243 243 243
Gray
level
Count
Probabil
ity
21 12 3/8
95 4 1/8
169 4 1/8
243 12 3/8
First order entropy =
2*(3/8)*log
2
(8/3)+2*(1/8)*l
og
2
8
=1.81 bits/pixel
Gray level
pair
Count Probability
(21,21) 8
(21,95) 4 1/8
(95,169) 4 1/8
(169,243) 4 1/8
(243,243) 8
(243,21) 4 1/8
Second-order entropy =
2*(1/4)*log
2
4+4*(1/8)*log
2
8=1+1.5=2.5 bits/pair = 1.25
bits/pixel.
The fact that the second order entropy (in bits/pixel) is less
than the first order entropy, indicates the presence of inter-
pixel redundancy. Hence variable length coding alone will
not lead to the most optimum compression in this case.
Consider mapping the pixels of the image to create
the following representation:
21 0 0 74 74 74 0 0
21 0 0 74 74 74 0 0
21 0 0 74 74 74 0 0
21 0 0 74 74 74 0 0
Here, we construct a difference array by replicating
the first column of the original image and using the
arithmetic difference between adjacent columns for
the remaining elements.
Gray level
or
difference
Count Probability
0 16
21 4 1/8
74 12 3/8
First order entropy of this difference image = 1.41 bits/pixel
Near optimal variable length codes:
Huffman codes require an enormous
number of computations. For N source symbols,
N-2 source reductions (sorting operations) and N-
2 code assignments must be made. Sometimes we
sacrifice coding efficiency for reducing the
number of computations.
Truncated Huffman code:
A truncated Huffman code is generated by Huffman
coding only the most probable M symbols of the
source, for some integer M (less than the total N
symbols). A prefix code followed by a suitable fixed
length is used to represent all other source symbols. In
the table in the previous slide, M was arbitrarily
selected as 12 and the prefix code was generated as the
13
th
Huffman code word. That is a 13
th
symbol whose
probability is the sum of the probabilities of the
symbols from 13
th
to 21
st
is included in the Huffman
coding along with the first 12 symbols.
B-code:
It is close to optimal when the source symbols
probabilities obey a law of the form:
P(a
j
) = c j
-|
In the B-code, each code word is made up of
continuation bits, denoted C, and information bits,
which are binary numbers. The only purpose of the
continuation bits is to separate individual code words,
so they simply toggle between 0 and 1 for each new
code word. The B-code shown here is called a B
2
code,
because two information bits are used per
continuation bit.
Shift code:
A shift code is generated by
Arranging the source symbols so that their probabilities
are monotonically decreasing
Dividing the total number of symbols into symbol blocks
of equal size.
Coding the individual elements within all blocks
identically, and
Adding special shift-up or shift-down symbols to identify
each block. Each time a shift-up or shift-down symbol is
recognized at the decoder, it moves one block up or down
with respect to a pre-defined reference block.
Arithmetic coding:
Unlike the variable-length codes described previously,
arithmetic coding, generates non-block codes. In arithmetic
coding, a one-to-one correspondence between source
symbols and code words does not exist. Instead, an entire
sequence of source symbols (or message) is assigned a
single arithmetic code word.
The code word itself defines an interval of real
numbers between 0 and 1. As the number of symbols in the
message increases, the interval used to represent it
becomes smaller and the number of information units (say,
bits) required to represent the interval becomes larger.
Each symbol of the message reduces the size of the interval
in accordance with the probability of occurrence. It is
supposed to approach the limit set by entropy.
Arithmetic coding
Let the message to be encoded be a
1
a
2
a
3
a
3
a
4
0.2
0.4
0.8
0.04
0.08
0.16
0.048
0.056
0.072
0.0592
0.0624
0.0688
0.06368
0.06496
So, any number in the interval [0.06752,0.0688) ,
for example 0.068 can be used to represent the
message.
Here 3 decimal digits are used to represent the 5
symbol source message. This translates into 3/5 or
0.6 decimal digits per source symbol and compares
favourably with the entropy of
-(3x0.2log
10
0.2+0.4log
10
0.4) = 0.5786 digits per
symbol
As the length of the sequence increases, the
resulting arithmetic code approaches the bound
set by entropy.
In practice, the length fails to reach the lower
bound, because:
The addition of the end of message indicator that
is needed to separate one message from another
The use of finite precision arithmetic
1.0
0.8
0.4
0.2
0.8
0.72
0.56
0.48
0.4
0.0
0.72
0.688
0.624
0.592
0.592
0.5856
0.5728
0.5664
Therefore, the
message is
a
3
a
3
a
1
a
2
a
4
0.5728
0.57152
056896
0.56768
Decoding:
Decode 0.572.
Since 0.8>code word > 0.4, the first symbol should be a
3
.
0.56 0.56 0.5664
LZW (Dictionary coding)
LZW (Lempel-Ziv-Welch) coding, assigns fixed-length
code words to variable length sequences of source
symbols, but requires no a priori knowledge of the
probability of the source symbols.
The n
th
extension of a source can be coded with fewer
average bits per symbol than the original source.
LZW is used in:
Tagged Image file format (TIFF)
Graphic interchange format (GIF)
Portable document format (PDF)
LZW was formulated in 1984
The Algorithm:
A codebook or dictionary containing the
source symbols is constructed.
For 8-bit monochrome images, the first 256
words of the dictionary are assigned to the gray
levels 0-255
Remaining part of the dictionary is filled with
sequences of the gray levels
Example:
39 39 126 126
39 39 126 126
39 39 126 126
39 39 126 126
Compression ratio = (8 x 16) / (10 x 9 ) = 64 / 45 = 1.4
Important features of LZW:
The dictionary is created while the data are being
encoded. So encoding can be done on the fly
The dictionary need not be transmitted. Dictionary can be
built up at receiving end on the fly
If the dictionary overflows then we have to reinitialize
the dictionary and add a bit to each one of the code words.
Choosing a large dictionary size avoids overflow, but
spoils compressions
Decoding LZW:
Let the bit stream received be:
39 39 126 126 256 258 260 259 257 126
In LZW, the dictionary which was used for
encoding need not be sent with the image. A
separate dictionary is built by the decoder, on
the fly, as it reads the received code words.
Recognized
Encoded
value
pixels Dic.
address
Dic. entry
39 39
39 39 39 256 39-39
39 126 126 257 39-126
126 126 126 258 126-126
126 256 39-39 259 126-39
256 258 126-126 260 39-39-126
258 260 39-39-126 261
126-126-
39
260 259 126-39 262
39-39-126-
126
259 257 39-126 263 126-39-39
257 126 126 264
39-126-126
INTERPIXEL REDUNDANCY
Variable length coding will produce identical
compression ratios for the two images shown on the next
slide, however we can achieve higher compression ratios by
reducing interpixel redundancy.
We can detect the presence of correlation between
pixels (or interpixel redundancy) by computing the auto-
correlation coefficients along a row of pixels
) 0 (
) (
) (
A
n A
n
A
= A
) , ( ) , (
1
) (
1
0
n y x f y x f
n N
n A
where
n N
y
A +
A
= A
A
=
Maximum possible value of (An) is 1 and this value is
approached for this image, both for adjacent pixels and
also for pixels which are separated by 45 pixels (or
multiples of 45).
Chapter 8
Image Compression
RUN-LENGTH CODING (1-D)
Used for binary images
Length of the sequences of ones & zeroes are
detected.
Assume that each row begins with a white(1) run.
Additional compression is achieved by variable length-
coding (Huffman coding) the run-lengths.
Developed in 1950s and has become, along with its 2-D
extensions, the standard approach in facsimile (FAX)
coding.
Problems with run-length and LZW coding:
Imperfect digitizing
Vertical correlations are missed
An m-bit gray scale image can be converted into m
binary images by bit-plane slicing. These individual
images are then encoded using run-length coding.
However, a small difference in the gray level of adjacent
pixels can cause a disruption of the run of zeroes or ones.
Eg: Let us say one pixel has a gray level of 127 and the
next pixel has a gray level of 128.
In binary: 127 = 01111111
& 128 = 10000000
Therefore a small change in gray level has decreased the
run-lengths in all the bit-planes!
GRAY CODE
Gray coded images are free of this problem
which affects images which are in binary format.
In gray code the representation of adjacent gray
levels will differ only in one bit (unlike binary
format where all the bits can change.
Let g
m-1
.g
1
g
0
represent the gray code
representation of a binary number.
Then:
1 1
1
2 0
+
=
s s =
m m
i i i
a g
m i a a g
In gray code:
127 = 01000000
128 = 11000000
Decoding a gray coded image:
The MSB is retained as such,i.e.,
1 1
1
2 0
+
=
s s =
m m
i i i
g a
m i a g a
Lossless Predictive Coding
n n n
f f e
=
Based on eliminating the interpixel redundancy in an
image
We extract and code only the new information in each
pixel
New information is defined as the difference between the
actual (f
n
) and the predicted value, of that pixel.
n
f
n n n
f e f
+ =
Decompression:
(
=
=
m
i
i n i n
f round f
1
o
Most general
form :
Most Simple form
1
=
n n
f f
Example for Lossless Predictive
coding
Lossy compression
Lossless compression usually gives a maximum
compression of 3:1 (for monochrome images)
Lossy compression can give compression upto 100:1 (for
recognizable monochrome images) 50:1 for virtually
indistinguishable images
The popular JPEG (Joint Photographic Experts Group)
format uses lossy transform-based compression.
Lossy predictive Coding
Delta modulation (DM) is a well-known form of lossy
predictive coding in which the predictor and
quantizer are defined as:
1
=
n n
f f
otherwise -
0 e for
n
,
,
=
> + =
n
e
DELTA MODULATION
TRANSFORM CODING
A linear, reversible transform (such as the Fourier
transform) is used to map the image into a set of transform
co-efficients, which are then quantized and coded.
For most natural images, a significant number of (high
frequency) coefficients have small magnitudes and can be
coarsely quantized with little image distortion
Other than the DFT, we have the Discrete Cosine
Transform (used in JPEG) and the Walsh Hadamard
Transform
TRANSFORM CODING
THE JPEG STANDARD FOR LOSSLESS
COMPRESSION
User chooses :
Huffman or Arithmetic code
One out of 8 predictive coding methods
1. Predict the next pixel on the line as having the same
value as the last one.
2. Predict the next pixel on the line as having the same
value as the pixel in this position on the previous line
3. Predict the next pixel on the line as having a value
related to a combination of the previous , above and
previous to the above pixel values.
The JPEG Standard for Lossy Compression
The Lossy compression uses the Discrete Cosine
Transform (DCT), defined as:
=
|
.
|
\
|
+
|
.
|
\
|
+ =
1
0
1
0
) 1 2 (
2
cos ) 1 2 (
2
cos ) , ( 4 ) , (
N
i
M
j
j
M
l
i
N
k
j i y l k Y
t t
In the JPEG image reduction process, the DCT is applied
to 8 by 8 pixel blocks of the image.
The lowest DCT coefficients are trimmed by setting them
to zero.
The remaining coefficients are quantized (rounded off),
some more coarsely than others.
Zig-zag coding is done after the quantization as
shown below
4.32 3.12 3.01 2.41
2.74 2.11 1.92 1.55
2.11 1.33 0.32 0.11
1.62 0.44 0.03 0.02
0 0 0 2
0 0 1 2
2 2 2 3
2 3 3 4
4333222122200000
Você também pode gostar
- Build A 10 Ton Hydraulic PressDocumento10 páginasBuild A 10 Ton Hydraulic PressManuel SterlingAinda não há avaliações
- MCS-011 Solved Assignment 2015-16 IpDocumento12 páginasMCS-011 Solved Assignment 2015-16 IpJigar NanduAinda não há avaliações
- Mastering Microcontrollers Helped by ArduinoDocumento23 páginasMastering Microcontrollers Helped by ArduinoMeri Terihaj100% (2)
- Computer Science (9608)Documento38 páginasComputer Science (9608)Attique RehmanAinda não há avaliações
- Is 15707 2006Documento23 páginasIs 15707 2006anupam789Ainda não há avaliações
- Heat ExchangersDocumento25 páginasHeat ExchangersMohammed Kabiruddin100% (7)
- Image Compression Coding SchemesDocumento96 páginasImage Compression Coding Schemesresmi_ng50% (4)
- Tailless AircraftDocumento17 páginasTailless AircraftVikasVickyAinda não há avaliações
- Modern Introduction to Object Oriented Programming for Prospective DevelopersNo EverandModern Introduction to Object Oriented Programming for Prospective DevelopersAinda não há avaliações
- Gray Level Count Probabil Ity 21 12 3/8 95 4 1/8 169 4 1/8 243 12 3/8Documento51 páginasGray Level Count Probabil Ity 21 12 3/8 95 4 1/8 169 4 1/8 243 12 3/8kamnakhannaAinda não há avaliações
- Image Compression (Chapter 8) : CS474/674 - Prof. BebisDocumento128 páginasImage Compression (Chapter 8) : CS474/674 - Prof. Bebissrc0108Ainda não há avaliações
- Why Needed?: Without Compression, These Applications Would Not Be FeasibleDocumento11 páginasWhy Needed?: Without Compression, These Applications Would Not Be Feasiblesmile00972Ainda não há avaliações
- 3.multimedia Compression AlgorithmsDocumento23 páginas3.multimedia Compression Algorithmsaishu sillAinda não há avaliações
- Mad Unit 3-JntuworldDocumento53 páginasMad Unit 3-JntuworldDilip TheLipAinda não há avaliações
- Chapter Six 6A ICDocumento30 páginasChapter Six 6A ICRobera GetachewAinda não há avaliações
- DIP Image Compression 1.11.2015Documento66 páginasDIP Image Compression 1.11.2015LayaAinda não há avaliações
- Text and Image CompressionDocumento57 páginasText and Image Compressionoureducation.in100% (1)
- Lec6 - Scalar Abnd Vector QuantizationDocumento32 páginasLec6 - Scalar Abnd Vector QuantizationAli AhmedAinda não há avaliações
- Image CompressionDocumento50 páginasImage CompressionVipin SinghAinda não há avaliações
- GROUP 3 Image CompressionDocumento31 páginasGROUP 3 Image CompressionPrayerAinda não há avaliações
- Huffman Coding TechniqueDocumento13 páginasHuffman Coding TechniqueAnchal RathoreAinda não há avaliações
- Image Compression (Chapter 8) : CS474/674 - Prof. BebisDocumento75 páginasImage Compression (Chapter 8) : CS474/674 - Prof. BebisKoushik SupercalifragilisticAinda não há avaliações
- Arithmetic Coding: Implementation Details and ExamplesDocumento11 páginasArithmetic Coding: Implementation Details and ExamplesShunmuga PriyanAinda não há avaliações
- UNIT5 Part 2Documento54 páginasUNIT5 Part 2Venkateswara RajuAinda não há avaliações
- UNIT5 Part 2-1-19Documento19 páginasUNIT5 Part 2-1-19Venkateswara RajuAinda não há avaliações
- UNIT5 Part 2-1-35Documento35 páginasUNIT5 Part 2-1-35Venkateswara RajuAinda não há avaliações
- Image CompressionDocumento133 páginasImage CompressionDeebika KaliyaperumalAinda não há avaliações
- Tornado Codes and Luby Transform Codes PDFDocumento12 páginasTornado Codes and Luby Transform Codes PDFpathmakerpkAinda não há avaliações
- Arithmetic Coding: Presented By: Einat & KimDocumento48 páginasArithmetic Coding: Presented By: Einat & Kimjigar16789Ainda não há avaliações
- CH 3 DatalinkDocumento35 páginasCH 3 DatalinksimayyilmazAinda não há avaliações
- Error-Free Compression: Variable Length CodingDocumento13 páginasError-Free Compression: Variable Length CodingVanithaAinda não há avaliações
- EntropyDocumento10 páginasEntropyRajesh TripathyAinda não há avaliações
- Dip 4 Unit NotesDocumento10 páginasDip 4 Unit NotesMichael MariamAinda não há avaliações
- Channel CodingDocumento45 páginasChannel CodingTu Nguyen NgocAinda não há avaliações
- Data CompressionDocumento22 páginasData CompressionPrachi TrehanAinda não há avaliações
- Notes For Turbo CodesDocumento15 páginasNotes For Turbo CodesMaria AslamAinda não há avaliações
- Design of Convolutional Encoder and Viterbi Decoder Using MATLABDocumento6 páginasDesign of Convolutional Encoder and Viterbi Decoder Using MATLABThu NguyễnAinda não há avaliações
- DC Unit Test 2 Question BankDocumento4 páginasDC Unit Test 2 Question BankSiva KrishnaAinda não há avaliações
- Ece 306L - Experiment 4: Signal QuantizationDocumento10 páginasEce 306L - Experiment 4: Signal QuantizationAndy CaoAinda não há avaliações
- Data CompressionDocumento28 páginasData CompressionKimAinda não há avaliações
- ImageCompression-UNIT-V-students MaterialDocumento88 páginasImageCompression-UNIT-V-students MaterialHarika JangamAinda não há avaliações
- The Data Link LayerDocumento35 páginasThe Data Link Layernitu2012Ainda não há avaliações
- 09 CM0340 Basic Compression AlgorithmsDocumento73 páginas09 CM0340 Basic Compression AlgorithmsShobhit JainAinda não há avaliações
- Fault Tolerant Huffman Coding For JPEG Image Coding SystemDocumento11 páginasFault Tolerant Huffman Coding For JPEG Image Coding SystemMymy SuityAinda não há avaliações
- Low Density Parity Check CodesDocumento21 páginasLow Density Parity Check CodesPrithvi Raj0% (1)
- Chapter 8-Image CompressionDocumento61 páginasChapter 8-Image CompressionAshish GauravAinda não há avaliações
- Convolutional Codes Turbo Codes LDPC CodesDocumento49 páginasConvolutional Codes Turbo Codes LDPC CodesveerutheprinceAinda não há avaliações
- H.264 / MPEG-4 Part 10 White Paper Variable-Length Coding 1Documento7 páginasH.264 / MPEG-4 Part 10 White Paper Variable-Length Coding 1sadsdaAinda não há avaliações
- H.264 / MPEG-4 Part 10 White Paper Variable-Length Coding 1Documento7 páginasH.264 / MPEG-4 Part 10 White Paper Variable-Length Coding 1sadsdaAinda não há avaliações
- Chapter ThreeDocumento30 páginasChapter ThreemekuriaAinda não há avaliações
- Lec8 ConvDocumento28 páginasLec8 ConvYaseen MoAinda não há avaliações
- HasanDocumento8 páginasHasansumeiranAinda não há avaliações
- FALLSEM2022-23 CSE4019 ETH VL2022230104728 2022-10-19 Reference-Material-IDocumento33 páginasFALLSEM2022-23 CSE4019 ETH VL2022230104728 2022-10-19 Reference-Material-ISRISHTI ACHARYYA 20BCE2561Ainda não há avaliações
- 1.1.1 Reed - Solomon Code:: C F (U, U, , U, U)Documento4 páginas1.1.1 Reed - Solomon Code:: C F (U, U, , U, U)Tân ChipAinda não há avaliações
- Arithmetic Code Discussion and ImplementationDocumento11 páginasArithmetic Code Discussion and ImplementationperhackerAinda não há avaliações
- Lempel-Ziv Codes: 5 .1 Lemp El - Ziv P Ar SingDocumento12 páginasLempel-Ziv Codes: 5 .1 Lemp El - Ziv P Ar SingPablo MontalvoAinda não há avaliações
- Convolutional CodeDocumento15 páginasConvolutional CodeDhivya LakshmiAinda não há avaliações
- Development of Wimax Physical Layer Building BlocksDocumento5 páginasDevelopment of Wimax Physical Layer Building BlocksSandeep Kaur BhullarAinda não há avaliações
- Error Control Coding3Documento24 páginasError Control Coding3DuongMinhSOnAinda não há avaliações
- 0742 Clu Ever 2005Documento4 páginas0742 Clu Ever 2005Samir ChouchaneAinda não há avaliações
- VTU Exam Question Paper With Solution of 17EC741 Multimedia Communication Feb-2021-Prof. Aritri DebnathDocumento38 páginasVTU Exam Question Paper With Solution of 17EC741 Multimedia Communication Feb-2021-Prof. Aritri DebnathShreya m YenagiAinda não há avaliações
- Data Compression Data Compression: Chapter FourDocumento22 páginasData Compression Data Compression: Chapter FourDawit BassaAinda não há avaliações
- Error-Correction on Non-Standard Communication ChannelsNo EverandError-Correction on Non-Standard Communication ChannelsAinda não há avaliações
- Line Drawing Algorithm: Mastering Techniques for Precision Image RenderingNo EverandLine Drawing Algorithm: Mastering Techniques for Precision Image RenderingAinda não há avaliações
- VarPlus Can - BLRCH104A125B48Documento2 páginasVarPlus Can - BLRCH104A125B48Achira DasanayakeAinda não há avaliações
- Jun SMSDocumento43 páginasJun SMSgallardo0121Ainda não há avaliações
- Chip DielDocumento45 páginasChip DielJUANCANEXTAinda não há avaliações
- EFR32BG1 Blue Gecko BluetoothDocumento102 páginasEFR32BG1 Blue Gecko BluetoothLullaby summerAinda não há avaliações
- SECTION 1213, 1214, 1215: Report By: Elibado T. MaureenDocumento19 páginasSECTION 1213, 1214, 1215: Report By: Elibado T. MaureenJohnFred CativoAinda não há avaliações
- Recent Developments in Crosslinking Technology For Coating ResinsDocumento14 páginasRecent Developments in Crosslinking Technology For Coating ResinsblpjAinda não há avaliações
- An Overview of Subspace Identification: S. Joe QinDocumento12 páginasAn Overview of Subspace Identification: S. Joe QinGodofredoAinda não há avaliações
- ManpasandDocumento16 páginasManpasandJacob MathewAinda não há avaliações
- Mumbai BylawsDocumento110 páginasMumbai BylawsLokesh SharmaAinda não há avaliações
- Notes Mechanism of Methanol Synthesis From Carbon Monoxide and Hydrogen On Copper CatalystsDocumento4 páginasNotes Mechanism of Methanol Synthesis From Carbon Monoxide and Hydrogen On Copper CatalystsArif HidayatAinda não há avaliações
- VX-1700 Owners ManualDocumento32 páginasVX-1700 Owners ManualVan ThaoAinda não há avaliações
- VAPORISERDocumento62 páginasVAPORISERAshish ChavanAinda não há avaliações
- Ecg Signal Thesis1Documento74 páginasEcg Signal Thesis1McSudul HasanAinda não há avaliações
- Wri Method FigDocumento15 páginasWri Method Figsoumyadeep19478425Ainda não há avaliações
- Raft TheoryDocumento37 páginasRaft Theorymuktha mukuAinda não há avaliações
- Quotation 98665Documento5 páginasQuotation 98665Reda IsmailAinda não há avaliações
- DVMDocumento197 páginasDVMLeonardLapatratAinda não há avaliações
- Misc Forrester SAP Competence CenterDocumento16 páginasMisc Forrester SAP Competence CenterManuel ParradoAinda não há avaliações
- Tutorial Class 1 Questions 1Documento2 páginasTutorial Class 1 Questions 1Bố Quỳnh ChiAinda não há avaliações
- Design Procedure For Journal BearingsDocumento4 páginasDesign Procedure For Journal BearingsSwaminathan100% (1)
- MB m.2 Support Am4Documento2 páginasMB m.2 Support Am4HhhhCaliAinda não há avaliações
- Activation and Deactivation of CatalystsDocumento16 páginasActivation and Deactivation of Catalystsshan0214Ainda não há avaliações
- Paper AeroplaneDocumento19 páginasPaper Aeroplanejkb SudhakarAinda não há avaliações
- Research Papers in Mechanical Engineering Free Download PDFDocumento4 páginasResearch Papers in Mechanical Engineering Free Download PDFtitamyg1p1j2Ainda não há avaliações